Trial user guide: Microsoft Defender for Business
Welcome to the Defender for Business trial user guide!
This guide will help you set up and use key features of your free trial. Using recommendations in this article from the Microsoft Defender team, learn how Defender for Business can help elevate your security from traditional antivirus protection to next-generation protection, endpoint detection and response, and vulnerability management.
What is Defender for Business?
Defender for Business is a new endpoint security solution designed especially for small and medium-sized businesses with up to 300 employees. With this endpoint security solution, your organization's devices are well-protected from ransomware, malware, phishing, and other threats.
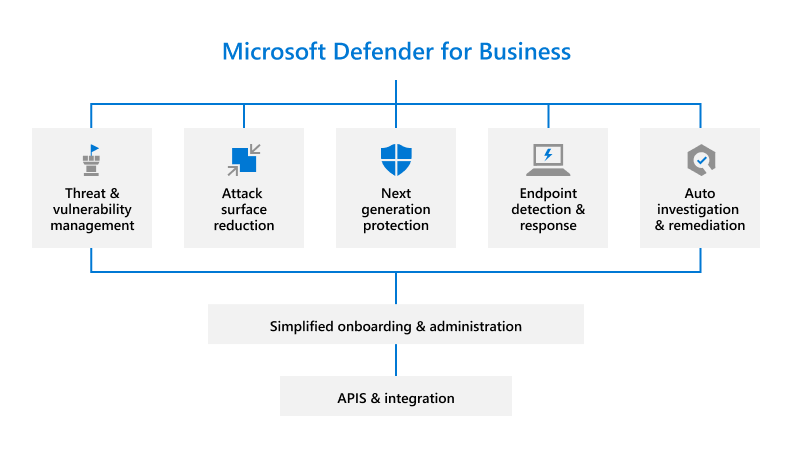
Let's get started!
Set up your trial
Here's how to set up your trial subscription:
- Add users and assign licenses.
- Visit the Microsoft Defender portal.
- Use the setup wizard.
- Set up and configure Defender for Business.
Step 1: Add users and assign licenses
After you sign up for Defender for Business, the first step is to add users and assign licenses.
Step 2: Visit the Microsoft Defender portal
The Microsoft Defender portal (https://security.microsoft.com) is the one-stop shop where you use and manage Defender for Business. It includes callouts to help you get started, cards that surface relevant information, and a navigation bar that provides easy access to the various features and capabilities.
- Visit the Microsoft Defender portal.
- Explore the navigation bar on the left side of the screen to access your incidents, view reports, and manage your security policies and settings.
Step 3: Use the setup wizard in Defender for Business (recommended)
Defender for Business was designed to save small and medium-sized businesses time and effort. You can do initial setup and configuration through a setup wizard. The setup wizard helps you grant access to your security team, set up email notifications for your security team, and onboard your company's Windows devices. Use the setup wizard.
Note
You can only use the setup wizard once.
Setup wizard flow: what to expect
Tip
Using the setup wizard is optional. If you choose not to use the wizard, or if the wizard is closed before your setup process is complete, you can complete the setup and configuration process on your own. See Step 4: Set up and configure Defender for Business.
Assign user permissions. Grant your security team access to the Microsoft Defender portal.
Set up email notifications for your security team.
Onboard and configure Windows devices. Onboarding devices right away helps protect those devices from day one.
Note
When you use the setup wizard, the system detects if you have Windows devices that are already enrolled in Intune. You'll be asked if you want to use automatic onboarding for all or some of those devices. You can onboard all Windows devices at once or select specific devices at first and then add more devices later.
To onboard other devices, see Step 4: Set up and configure Defender for Business.
View and edit your security policies. Defender for Business includes default security policies for next-generation protection and firewall protection that can be applied to your company's devices. These preconfigured security policies use recommended settings, so you're protected as soon as your devices are onboarded to Defender for Business. And you can edit the policies or create new ones.
Step 4: Set up and configure Defender for Business
If you choose not to use the setup wizard, see the following diagram that depicts the overall setup and configuration process for Defender for Business.
If you used the setup wizard but you need to onboard more devices, such as non-Windows devices, go directly to step 4 in the following procedure:
Review the requirements to configure and use Defender for Business.
Assign roles and permissions in the Microsoft Defender portal.
Set up email notifications for your security team.
Onboard devices. To onboard Windows and Mac clients, you can use a local script.
View and configure your security policies. After you onboard your company's devices to Defender for Business, the next step is to view and edit your security policies and settings.
Defender for Business includes pre-configured security policies that use recommended settings. But you can edit the settings to suit your business needs.
Security policies to review and configure include:
- Next-generation protection policies which determine antivirus and antimalware protection for your company's devices
- Firewall protection and rules which determine what network traffic is allowed to flow to and from your company's devices
- Web content filtering which prevents people from visiting certain websites (URLs) based on categories, such as adult content or legal liability
- Advanced features such as automated investigation and response and endpoint detection and response (EDR) in block mode
Start using Defender for Business
For the next 30 days, here's guidance from the product team on key features to try:
1. Use the Defender Vulnerability Management dashboard
Defender for Business includes a Defender Vulnerability Management dashboard that's designed to save your security team time and effort. Learn how to use your Defender Vulnerability Management dashboard.
- View your exposure score, which is associated with devices in your organization.
- View your top security recommendations, such as address impaired communications with devices, turn on firewall protection, or update Microsoft Defender Antivirus definitions.
- View remediation activities, such as any files that were sent to quarantine, or vulnerabilities found on devices.
2. View and respond to detected threats
As threats are detected and alerts are triggered, incidents are created. Your organization's security team can view and manage incidents in the Microsoft Defender portal. Learn how to view and respond to detected threats.
- View and manage incidents.
- Respond to and mitigate threats.
- Review mediation actions in the Action Center.
- View and use reports.
3. Review security policies
In Defender for Business, security settings are configured through policies that are applied to devices. Defender for Business includes pre-configured policies to help protect your company's devices as soon as they are onboarded, safeguarding your organization against identity, device, application, and document security threats.
Learn how to review security policies.
4. Prepare for ongoing security management
New security events, such as threat detection on a device, adding new devices, and employees joining or leaving the organization, will require you to manage security. In Defender for Business, there are many ways for you to manage device security.
- View a list of onboarded devices to see their risk level, exposure level, and health state.
- Take action on a device that has threat detections.
- Onboard a device to Defender for Business.
- Offboard a device from Defender for Business.
