Start using Defender Experts for XDR service
Applies to:
After you completed the onboarding steps and readiness checks for Microsoft Defender Experts for XDR, our experts will start monitoring your environment to streamline the service so we can perform comprehensive service on your behalf. During this stage, our experts identify latent threats, sources of risk, and normal activity.
Once our experts begin to perform comprehensive response work on your behalf, you'll start receiving notifications about incidents that require remediation steps and targeted recommendations on critical incidents. You can also chat with our experts or your service delivery managers (SDMs) regarding important queries and regular business and security posture reviews and view real-time reports on the number of incidents we've investigated and resolved on your behalf.
Managed detection and response
Through a combination of automation and human expertise, Defender Experts for XDR triages Microsoft Defender XDR incidents, prioritizes them on your behalf, filters out the noise, carries out detailed investigations, and provides actionable managed response to your security operations center (SOC) teams.
Incident updates
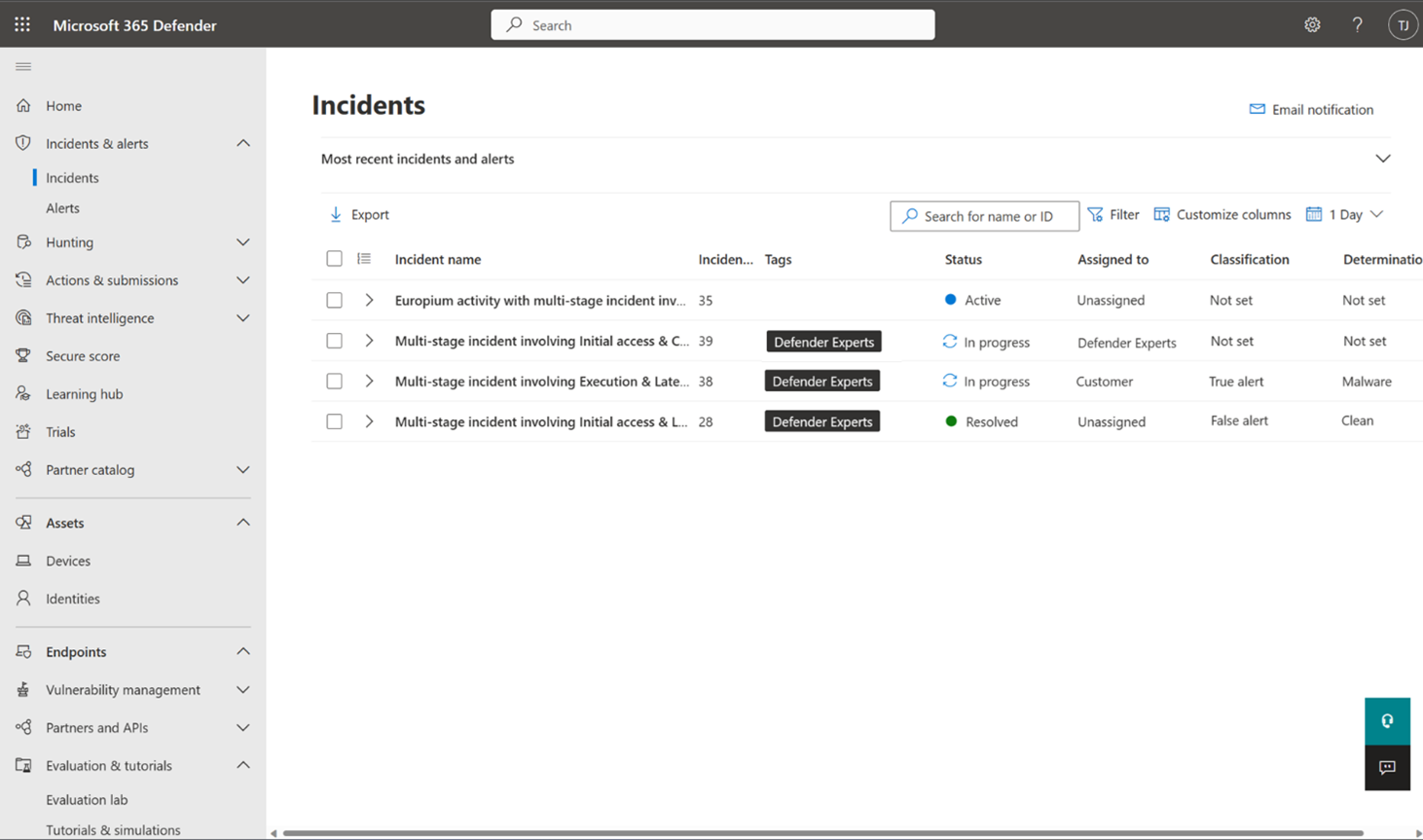
Once our experts start investigating an incident, the incident's Assigned to and Status fields are updated to Defender Experts and In progress, respectively.
When our experts conclude their investigation on an incident, the incident's Classification field is updated to one of the following, depending on the experts' findings:
- True Positive
- False Positive
- Informational, Expected Activity
The Determination field corresponding to each classification is also updated to provide more insights on the findings that led our experts to determine the said classification.
If an incident is classified as False Positive or Informational, Expected Activity, then the incident's Status field gets updated to Resolved. Our experts then conclude their work on this incident and the Assigned to field gets updated to Unassigned. Our experts may share updates from their investigation and their conclusion when resolving an incident. These updates are posted in the incident's Comments and history flyout panel.
Note
Incident comments are one-way posts. Defender Experts can't respond to any comments or questions you add in the Comments and history panel. For more information about how to correspond with our experts, see Communicating with experts in the Microsoft Defender Experts for XDR service.
Otherwise, if an incident is classified as True Positive, our experts then identify the required response actions that need to be performed. The method in which the actions are performed depends on the permissions and access levels you have given the Defender Experts for XDR service. Learn more about granting permissions to our experts.
If you have granted Defender Experts for XDR the recommended Security Operator access permissions, our experts could perform the required response actions on the incident on your behalf. These actions, along with an Investigation summary, show up in the incident's Managed response flyout panel in your Microsoft Defender portal for you or your SOC team to review. All actions that are completed by Defender Experts for XDR appear under the Completed actions section. Any pending actions that require you or you SOC team to complete are listed under the Pending actions section. For more information, see the Actions section. Once our experts have taken all the necessary actions on the incident, its Status field is then updated to Resolved and the Assigned to field is updated to Unassigned.
If you have granted Defender Experts for XDR the default Security Reader access, then the required response actions, along with an Investigation summary, show up in the incident's Managed response flyout panel under the Pending actions section in your Microsoft Defender portal for you or your SOC team to perform. For more information, see the Actions section. To identify this handover, the incident's Status field is updated to Awaiting Customer Action and the Assigned to field is updated to Customer.
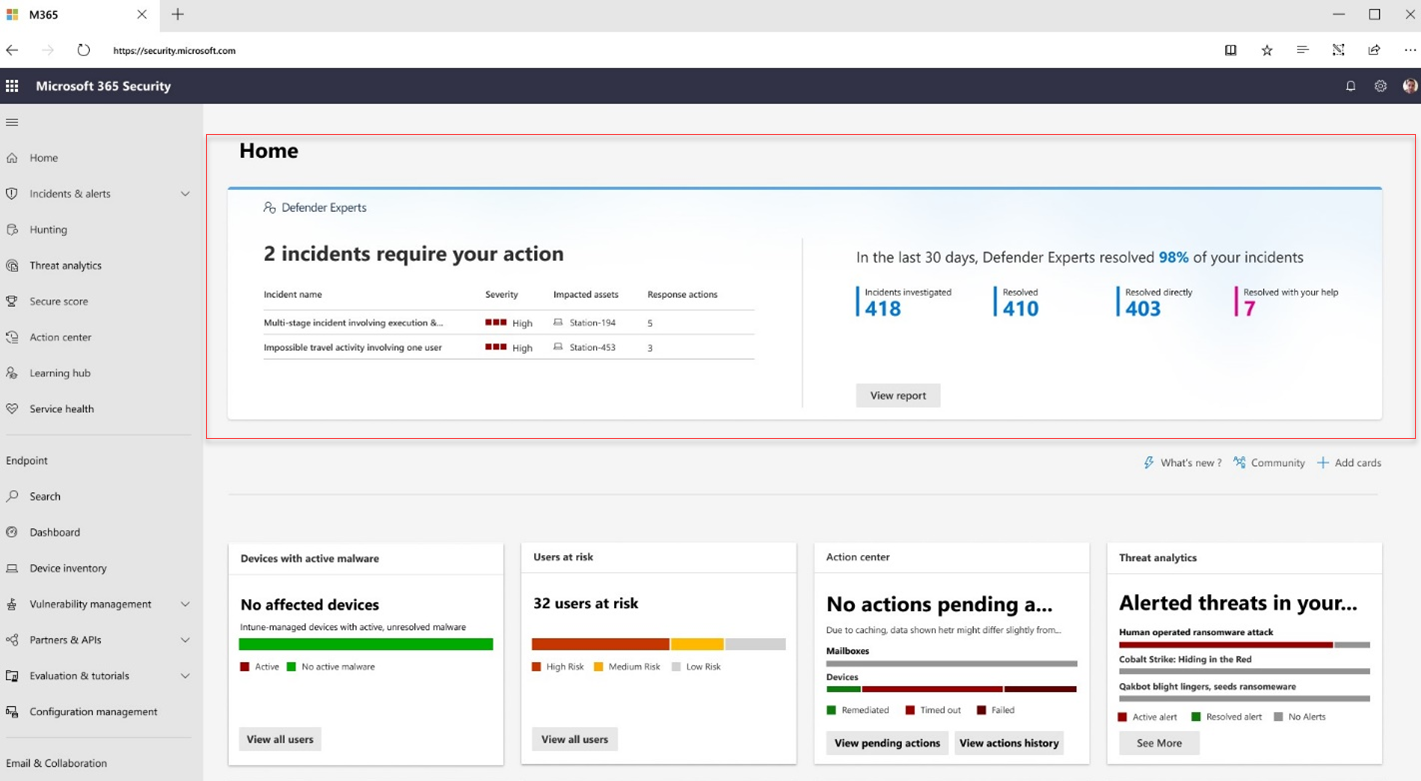
You can check the number of incidents that require your action in the Defender Experts banner at the top of the Microsoft Defender homepage.
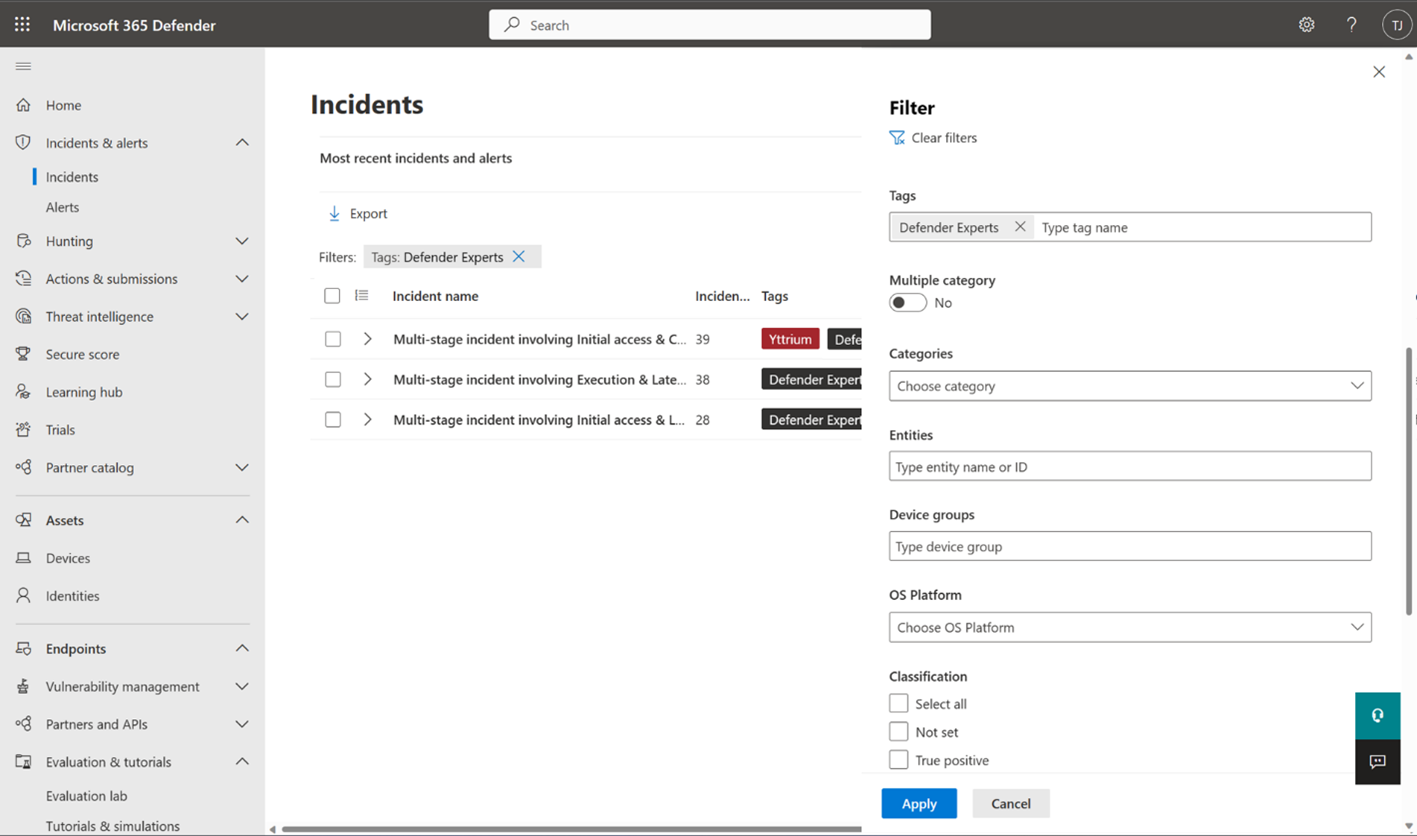
To view the incidents our experts have investigated or are currently investigating, filter the incident queue in your Microsoft Defender portal using the Defender Experts tag.
How to use managed response in Microsoft Defender XDR
In the Microsoft Defender portal, an incident that requires your attention using managed response has the Assigned to field set to Customer and a task card on top of the Incidents pane. Your designated incident contacts also receives a corresponding email notification with a link to the Defender portal to view the incident. Learn more about notification contacts.
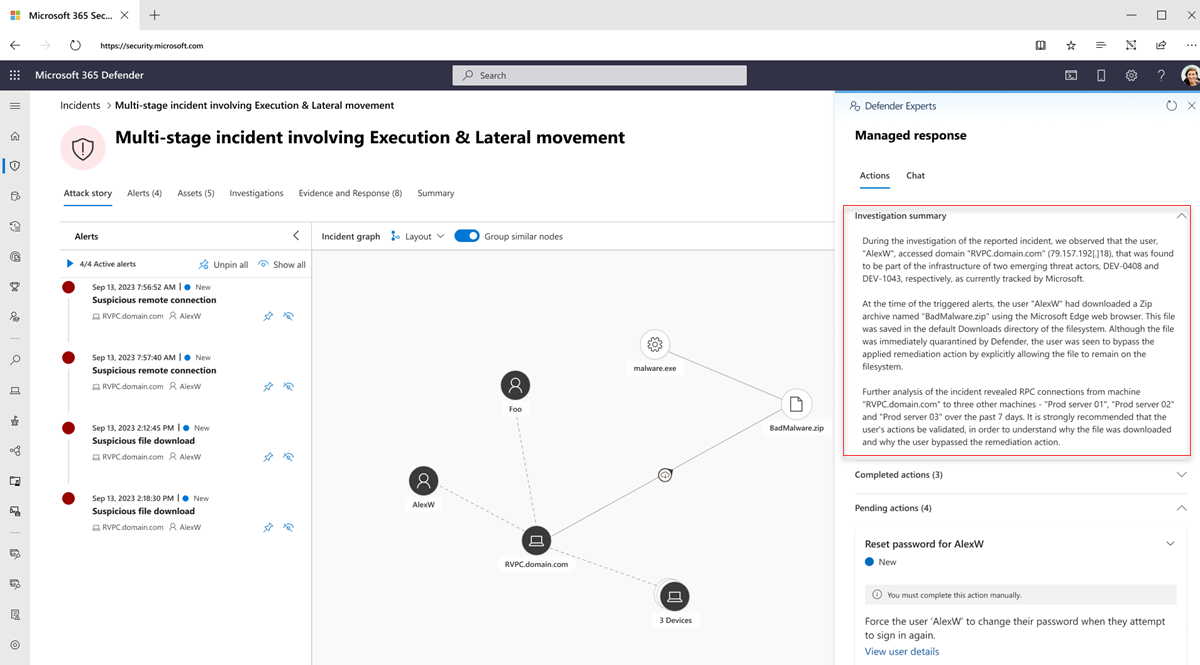
Select View managed response on the task card or on the top of the portal page (Managed response tab) to open a flyout panel where you can read our experts' investigation summary, complete pending actions identified by our experts, or engage with them through chat.
Investigation summary
The Investigation summary section provides you with more context about the incident analyzed by our experts to provide you with visibility about its severity and potential impact if not addressed immediately. It could include the device timeline, indicators of attack, and indicators of compromise (IOCs) observed, and other details.
Actions
The Actions tab displays task cards that contain response actions recommended by our experts.
Defender Experts for XDR currently supports the following one-click managed response actions:
| Action | Description |
|---|---|
| Isolate device | Isolates a device, which helps prevent an attacker from controlling it and performing further activities such as data exfiltration and lateral movement. The isolated device will still be connected to Microsoft Defender for Endpoint. |
| Quarantine file | Stops running processes, quarantines the files, and deletes persistent data such as registry keys. |
| Restrict app execution | Restricts the execution of potentially malicious programs and locks down the device to prevent further attempts. |
| Release from isolation | Undoes isolation of a device. |
| Remove app restriction | Undoes release from isolation. |
Apart from these one-click actions, you can also receive managed responses from our experts that you need to perform manually.
Note
Before performing any of the recommended managed response actions, make sure that they are not already being addressed by your automated investigation and response configurations. Learn more about automated investigation and response capabilities in Microsoft Defender XDR.
To view and perform the managed response actions:
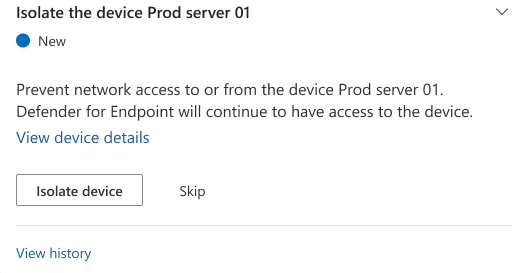
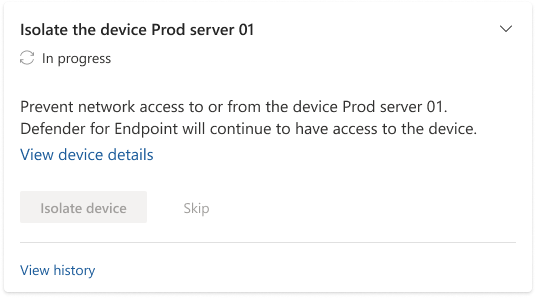
Select the arrow buttons in an action card to expand it and read more information about the required action.
For cards with one-click response actions, select the required action. The Action status in the card changes to In progress, then to Failed or Completed, depending on the action's outcome.
Tip
You can also monitor the status of in-portal response actions in the Action center. If a response action fails, try doing it again from the View device details page or initiate a chat with Defender Experts.
For cards with required actions that you need to perform manually, select I've completed this action once you've performed them, then select Yes, I've done it in the confirmation dialog box that appears.
If you don't want to complete a required action right away, select Skip, then select Yes, skip this action in the confirmation dialog box that appears.
Important
If you notice that any of the buttons on the action cards are grayed out, it could indicate that you don't have the necessary permissions to perform the action. Make sure that you're signed into the Microsoft Defender XDR portal with the appropriate permissions. Most managed response actions require that you have at least the Security Operator access.
If you still encounter this issue even with the appropriate permissions, navigate to View device details and complete the steps from there.
Get visibility to Defender Experts investigations in your SIEM or ITSM application
As Defender Experts for XDR investigate incidents and come up with remediation actions, you can have visibility to their work on incidents in your security information and event management (SIEM) and IT service management (ITSM) applications, including applications that are available out of the box.
Microsoft Sentinel
You can get incident visibility in Microsoft Sentinel by turning on its out-of-the-box Microsoft Defender XDR data connector. Learn more.
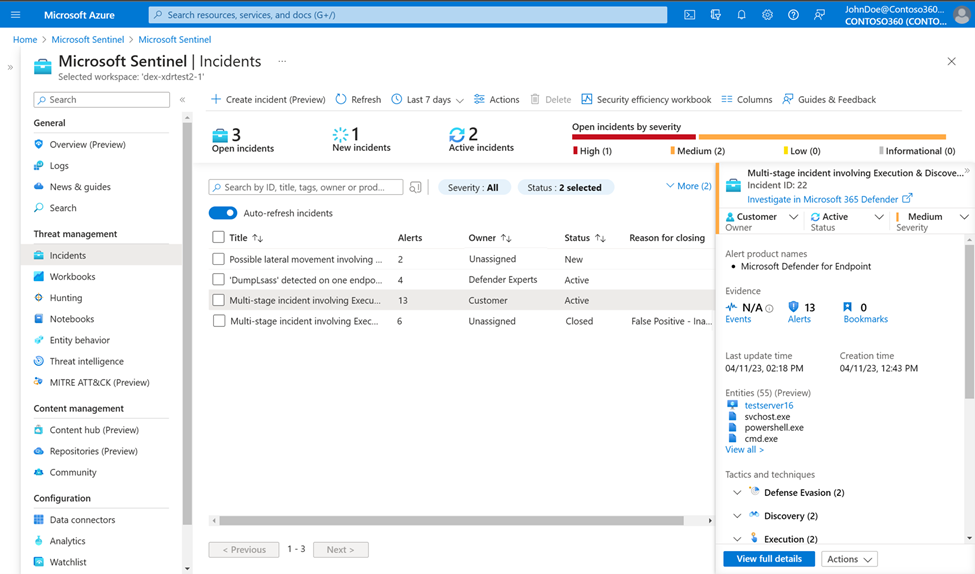
Once you have turned on the connector, updates by Defender Experts to the Status, Assigned to, Classification, and Determination fields in Microsoft Defender XDR will show up in the corresponding Status, Owner, and Reason for closing fields in Sentinel.
Note
The status of incidents investigated by Defender Experts in Microsoft Defender XDR typically transitions from Active to In progress to Awaiting Customer Action to Resolved, while in Sentinel, it follows the New to Active to Resolved path. The Microsoft Defender XDR Status Awaiting Customer Action doesn't have an equivalent field in Sentinel; instead, it's displayed as a tag in an incident in Sentinel.
The following section describes how an incident handled by our experts is updated in Sentinel as it progresses through the investigation journey:
- An incident being investigated by our experts has the Status listed as Active and the Owner listed as Defender Experts.
- An incident that our experts have confirmed as a True Positive has a managed response posted in Microsoft Defender XDR, and a Tag Awaiting Customer Action and the Owner is listed as Customer. You need to act on the incident based on using the provided managed response.
- Once our experts have concluded their investigation and closed an incident as False Positive or Informational, Expected Activity, the incident's Status is updated to Resolved, the Owner is updated to Unassigned, and a Reason for closing is provided.
Other applications
You could obtain visibility into incidents in your SIEM or ITSM application by using the Microsoft Defender XDR API or connectors in Sentinel.
After configuring a connector, the updates by Defender Experts to an incident's Status, Assigned to, Classification, and Determination fields in Microsoft Defender XDR can be synchronized with the third-party SIEM or ITSM applications, depending on how the field mapping has been implemented. To illustrate, you can take a look at the connector available from Sentinel to ServiceNow.
Get real-time visibility with Defender Experts for XDR reports
Defender Experts for XDR includes an interactive, on-demand report that provides a clear summary of the work our expert analysts are doing on your behalf, aggregate information about your incident landscape, and granular details about specific incidents. Your service delivery manager (SDM) also uses the report to provide you with more context regarding the service during a monthly business review.
Each section of the report is designed to provide more insights about the incidents our experts investigated and resolved in your environment in real time. You can also select the Date range to get detailed information about incidents based on severity, category, and understand the time taken to investigate and resolve an incident during a specific period.
Understand the Defender Experts for XDR report
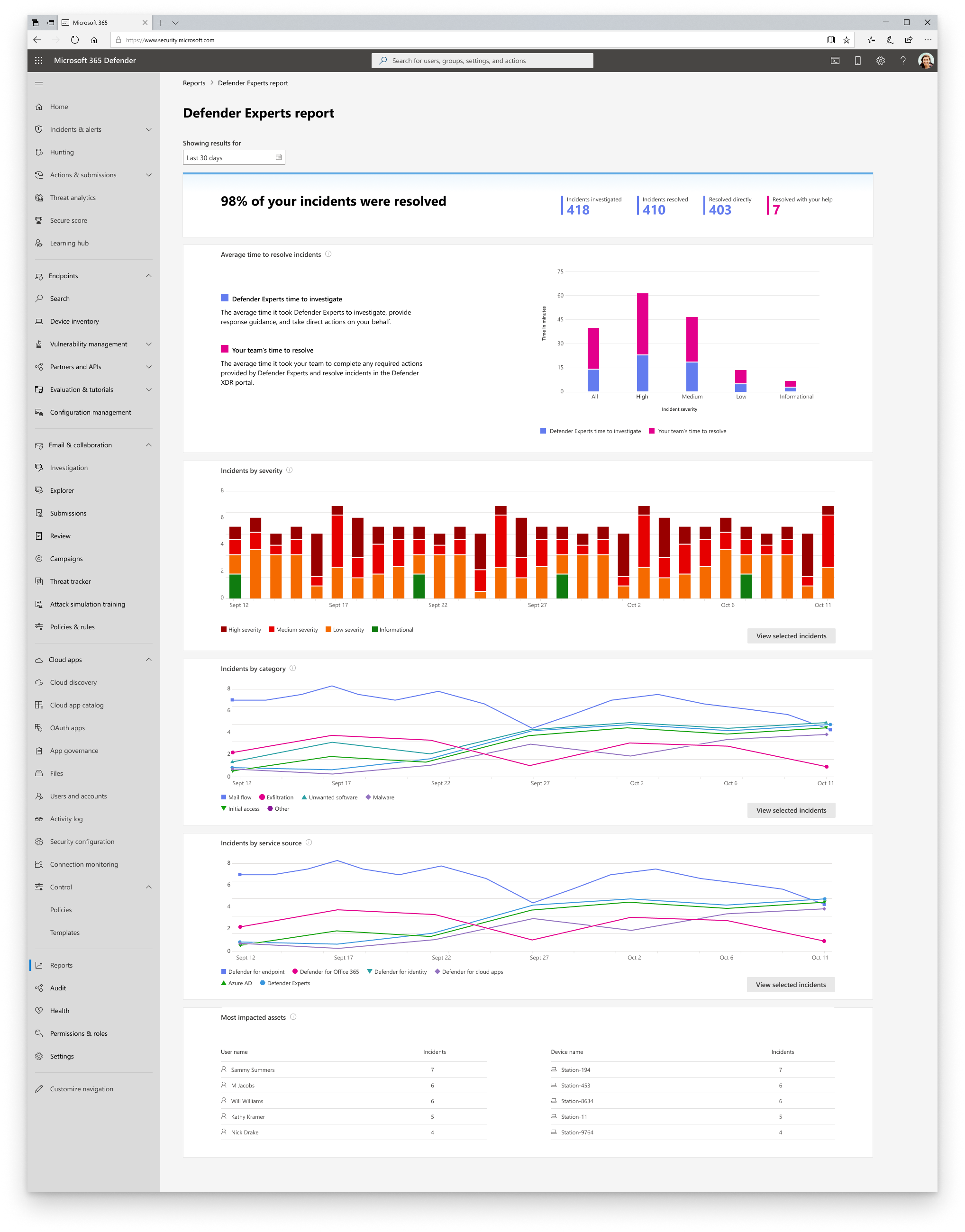
The topmost section of the Defender Experts for XDR report provides the percentage of incidents we resolved in your environment, providing you with transparency in our operations. This percentage is derived from the following figures, which are also presented in the report:
- Investigated – The number of active threats and other incidents from your incident queue that we triaged, investigated, or currently investigating within our scope.
- Resolved – The total number of investigated incidents that were closed.
- Resolved directly – The number of investigated incidents that we were able to close directly on your behalf.
- Resolved with your help – The number of investigated incidents that were resolved because of your action on one or more managed response tasks.
The Average time to resolve incidents section displays a bar chart of the average time, in minutes, our experts spent investigating and closing incidents in your environment and the average time you spent performing the required managed response actions.
The Incidents by severity, Incidents by category, and Incidents by service source sections break down resolved incidents by severity, attack technique, and Microsoft security service source, respectively. These sections let you identify potential attack entry points and types of threats detected in your environment, assess their impact, and develop strategies to mitigate and prevent them. Select View incidents to get a filtered view of the incident queue based on the selections you made in each of the two sections.
The Most impacted assets section shows the users and devices in your environment that were involved in the most number of incidents during your selected date range. You can see the volume of incidents each asset was involved in. Select an asset to get a filtered view of the incident queue based on the incidents that included the said asset.
Proactive managed hunting
Defender Experts for XDR also includes proactive threat hunting offered by Microsoft Defender Experts for Hunting. Defender Experts for Hunting was created for customers who have a robust security operations center but want Microsoft to help them proactively hunt threats using Microsoft Defender data. This proactive threat hunting service goes beyond the endpoint to hunt across endpoints, Office 365, cloud applications, and identity. Our experts investigate anything they find, then hand off the contextual alert information along with remediation instructions, so you can quickly respond.
Request advanced threat expertise on demand
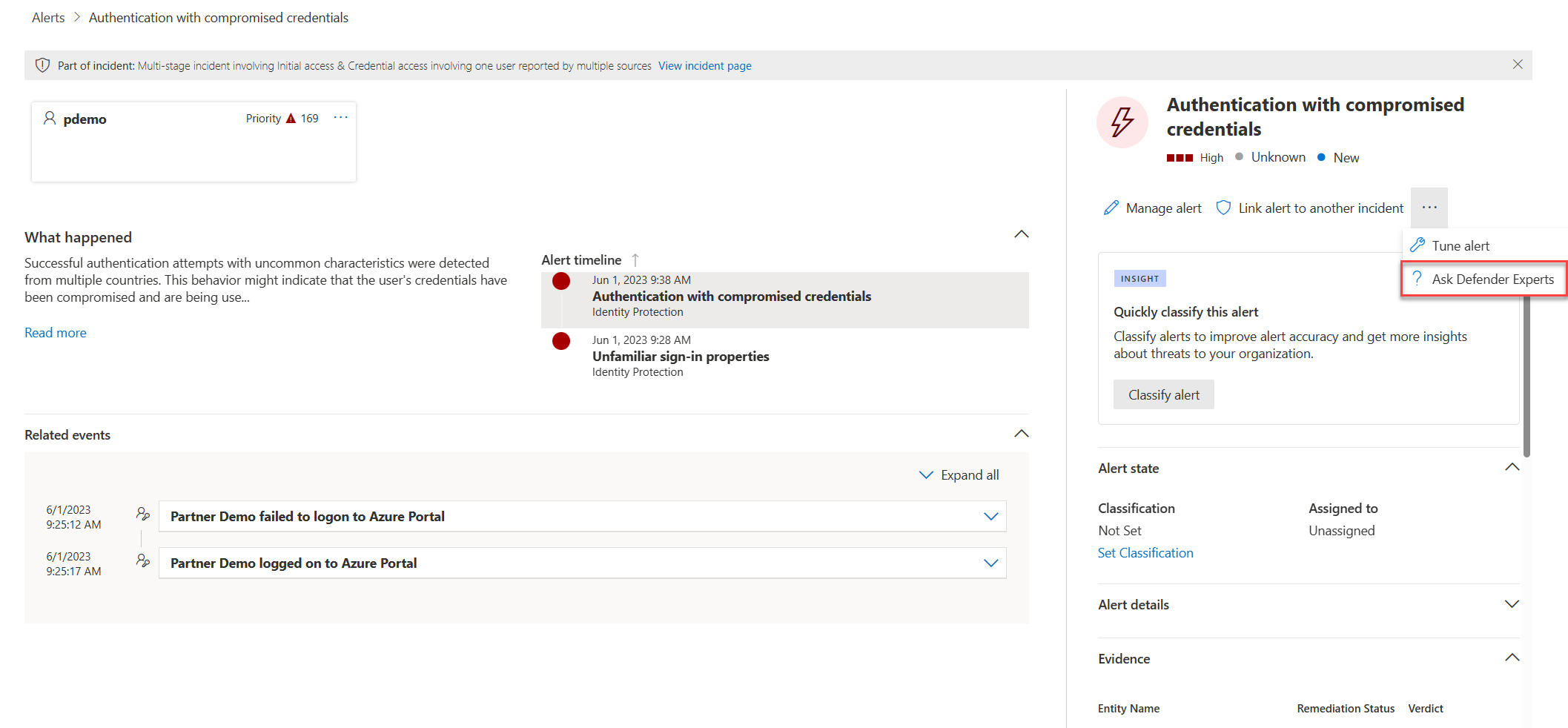
Select Ask Defender Experts directly inside the Microsoft Defender XDR portal to get swift and accurate responses to all your threat questions. Experts can provide insights to better understand the complex threats your organization might face. Consult an expert to:
- Gather additional information on alerts and incidents, including root causes and scope.
- Gain clarity into suspicious devices, alerts, or incidents and get the next steps if faced with an advanced attacker.
- Determine risks and available protections related to activity groups, campaigns, or emerging attacker techniques.
Note
Ask Defender Experts is not a security incident response service. It's intended to provide a better understanding of complex threats affecting your organization. Engage with your own security incident response team to address urgent security incident response issues. If you don't have your own security incident response team and would like Microsoft's help, create a support request in the Premier Services Hub.
The option to Ask Defender Experts is available in the incidents and alerts pages for you to ask contextual questions about a specific incident or alert:
- Alerts page flyout menu:
- Incidents page actions menu:
See also
- Search audit logs for actions performed by Defender Experts
- Additional information
- General information on Defender Experts for XDR service
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.