Azure Chaos Studio に関する問題のトラブルシューティング
[アーティクル] 2024/10/15
13 人の共同作成者
フィードバック
この記事の内容
一般的なトラブルシューティングのヒント
リソースを追加するときの問題
前提条件の問題
実験を作成または設計するときの問題
実験を実行するときの問題
マネージド ID を設定するときの問題
さらに 2 個を表示
Azure Chaos Studio を使っていると、時には問題が発生することがあります。 この記事では、一般的な問題とトラブルシューティングの手順を説明します。
次のソースは、Chaos Studio に関する問題のトラブルシューティングを行うときに役立ちます。
アクティビティ ログ : Azure アクティビティ ログ には、サブスクリプション内の作成、更新、削除の操作がすべて記録されています。 この記録には Chaos Studio の操作 (ターゲットまたは機能の有効化、エージェントのインストール、実験の作成または実行など) も含まれています。 アクティビティ ログの中の障害は、Chaos Studio を使用するために必要なユーザー アクションを完了できなかった可能性があることを示します。 ほとんどのサービス直接フォールトでは、Azure Resource Manager 操作を実行するという方法でのフォールト挿入も行われるため、アクティビティ ログにはサービス直接フォールトの実験中に挿入されたフォールトの記録も含まれます。実験の詳細 : 実験実行の詳細には、個々の実験実行の状態とエラーが表示されます。 実験の詳細の中の特定のフォールトを開くと、障害が発生したリソースと障害に関するエラー メッセージが表示されます。 実験の詳細にアクセスする 方法の詳細を参照してください。エージェント ログ : エージェントベースのフォールトを使用する場合は、エージェントがフォールトを実行できなかった理由を理解するために仮想マシン (VM) に RDP または SSH で接続することが必要になる可能性があります。 エージェント ログにアクセスするための手順は、オペレーティング システムによって異なります。
Chaos Windows エージェント : エージェントのログは、Windows イベント ログの "アプリケーション" カテゴリにソース AzureChaosAgent で記録されています。 エージェントにより、このログにフォールト アクティビティと通常の正常性チェック (認証を行い、Chaos Studio エージェント サービスと通信する機能) イベントが追加されます。Chaos Linux エージェント : Linux エージェントでは systemd を使用して、エージェント プロセスを Linux サービスとして管理します。 エージェントの systemd ジャーナル (エージェント サービスによってログに記録されるイベント) を表示するには、コマンド journalctl -u azure-chaos-agent を実行します。
VM 拡張機能の状態 : エージェントベースのフォールトを使用する場合は、VM 拡張機能がインストール済みで正常であることを確認してください。 Azure portal で、お使いの VM に移動して [拡張機能] または [拡張機能とアプリケーション] に移動します。 ChaosAgent という拡張機能を選択し、次のフィールドを見つけます。
[状態] には "プロビジョニング成功" と表示されるはずです。システム要件 をすべて満たしていることを確認してください。 エージェントを再インストールしてみてください。[ハンドラーの状態] には "準備完了" と表示されるはずです。ネットワーク要件 をすべて満たしていることと、ユーザー割り当てマネージド ID が VM に追加されたことを確認してください。 再起動してみてください。
リソースを追加するときに、次の問題が発生することがあります。
リソースが Azure portal のターゲット リストに表示されない 有効にしたいリソースが Chaos Studio のターゲット リストに表示されない場合は、原因として次の問題が考えられます。
ターゲットまたは機能の有効化に失敗する、またはターゲット リストに正しく表示されない ターゲットまたは機能を有効にするときにエラーが発生した場合は、次の手順を試してください。
追加するリソースに対する適切なアクセス許可があることを確認します。 ターゲットまたは機能を有効にするには、そのリソースのスコープでの Microsoft.Chaos/* アクセス許可が必要です。 "共同作成者" などの組み込みロールには、ワイルドカードの読み取りと書き込みのアクセス許可が付与されており、これにはすべての Microsoft.Chaos 操作に対するアクセス許可が含まれています。
ターゲットおよび機能リストが更新されるまで数分待ちます。 Azure portal では、ターゲットと機能の追加に関する情報が Azure Resource Graph を使用して収集されます。 更新が反映されるまでに最大 5 分ほどかかることがあります。
それでもリソースが "無効" と表示される場合は、次の手順を試してください。
リソースをもう一度有効にしてみます。
それでもリソースの有効化に失敗する場合は、アクティビティ ログに移動し、失敗したターゲット作成操作を見つけて詳細なエラー情報を確認してください。
リソースが "有効" と表示されているけれども機能の追加に失敗した場合は、次の手順を試してください。
ターゲット リストで、リソースの [アクションの管理] を選択します。 チェックボックスがオフだった機能がある場合はオンにして、[保存] をクリックします。
それでも機能の有効化に失敗する場合は、アクティビティ ログに移動し、失敗したターゲット作成操作を見つけて詳細なエラー情報を確認してください。
前提条件が満たされていないことが原因で発生する問題もあります。
仮想マシンでエージェントベースのフォールトが失敗する エージェントベースのフォールトは、前提条件が満たされていないことに関連するさまざまな理由で失敗することがあります。
Linux VM では、CPU 負荷 、物理メモリ負荷 、ディスク I/O 負荷 、および任意の stress-ng ストレス のどのフォールトについても、stress-ng ユーティリティ が VM にインストールされている必要があります。 stress-ng をインストールする方法の詳細については、フォールトの前提条件に関するセクションを参照してください。
Linux と Windows のどちらの VM でも、エージェントベースのターゲットの有効化の際に指定されたユーザー割り当てマネージド ID がその VM にも追加されている必要があります。
Linux と Windows のどちらの VM でも、実験のシステム割り当てマネージド ID にその VM での閲覧者ロールが付与されている必要があります。 ("仮想マシン共同作成者" のような、一見昇格されたロールには、Chaos Studio エージェントが VM 上の microsoft-agent ターゲット プロキシ リソースを読み取るために必要な */Read 操作は含まれていません。)
Chaos エージェントが仮想マシン スケール セットにインストールされない 仮想マシン スケール セットのアップグレード ポリシーが [手動] に設定されている場合は、その仮想マシン スケール セットへの Chaos エージェントのインストールがエラーを示すことなく失敗することがあります。 仮想マシン スケール セットのアップグレード ポリシーを確認する方法は次のとおりです。
Azure portal にサインインします。
[仮想マシン スケール セット] を選択します。左側のペインで、[アップグレード ポリシー] を選択します。
[アップグレード モード] が [手動 - 既存のインスタンスは手動でアップグレードする必要があります] に設定されているかどうかを調べます。
アップグレード ポリシーが [手動] に設定されている場合は、Chaos エージェントのインストールを完了できるようにするために Azure Virtual Machine Scale Sets のインスタンスをアップグレードする必要があります。
Azure portal からインスタンスをアップグレードする 次の手順で Azure portal から Virtual Machine Scale Sets のインスタンスをアップグレードできます。
Azure portal にサインインします。
[仮想マシン スケール セット] を選択します。左側のペインで、[インスタンス] を選択します。
すべてのインスタンスを選択して [アップグレード] を選択します。
Azure CLI を使用してインスタンスをアップグレードする 次の手順で Azure CLI を使用して Virtual Machine Scale Sets のインスタンスをアップグレードできます。
詳細については、最新のスケール セット モデルで VM を最新の状態にする方法 の説明を参照してください。
Azure Kubernetes Service (AKS) Chaos Mesh のフォールトは、前提条件が満たされていないことに関連するさまざまな理由で失敗することがあります。
AKS Chaos Mesh フォールトを使用する前に、まず AKS クラスターに Chaos Mesh をインストールする必要があります。 手順については、AKS に対する Chaos Mesh フォールトのチュートリアル に関するページを参照してください。
Chaos Mesh はバージョン 2.0.4 以上である必要があります。 AKS クラスターに接続し、helm version chaos-mesh を実行することで、Chaos Mesh のバージョンを取得することができます。
Chaos Mesh は名前空間 chaos-testing と共にインストールする必要があります。 Chaos Mesh のその他の名前空間名はサポートされていません。
AKS クラスター管理者ロールがカオス実験用のシステム割り当てマネージド ID に割り当てられている必要があります。
実験を作成または設計するときに問題が発生することがあります。
フォールトの追加時に、リソースが [ターゲット リソース] リストに表示されない フォールトを追加するときに、フォールトのターゲットとなるリソースが[ターゲット リソース] リストに表示されない場合は、次の問題が原因として考えられます。
[サブスクリプション] フィルターが、ターゲットがデプロイされるサブスクリプションを除外するように設定されている。 サブスクリプション フィルターをクリックし、選択済みのサブスクリプションを変更してください。リソースがまだ追加されていない。 [ターゲット] ビューに移動してターゲットを有効にしてください。 その後で、[フォールトの追加] ペインを閉じてもう一度開くと、更新されたターゲット リストが表示されます。
リソースが、そのフォールトのターゲットの種類に対してまだ有効になっていない。 フォールト ライブラリ を参照して、どのターゲットの種類がそのフォールトに使用されているかを確認してください。 その後で、[ターゲット] ビューに移動してそのターゲットの種類を有効にしてください。 この種類は、microsoft-agent フォールトの場合はエージェントベース、他のすべてのターゲットの種類の場合はサービス直接です。 その後で、[フォールトの追加] ペインを閉じてもう一度開くと、更新されたターゲット リストが表示されます。
リソースで、そのフォールトの機能がまだ有効になっていない。 フォールト ライブラリ を参照してそのフォールトの機能名を確認してください。 その後で、[ターゲット] ビューに移動してターゲット リソースの [アクションの管理] を選択します。 実行しようとしているフォールトに対応する機能のチェックボックスを選択して [保存] を選択します。 その後で、[フォールトの追加] ペインを閉じてもう一度開くと、更新されたターゲット リストが表示されます。
リソースが最近追加されたばかりで、まだ Resource Graph に存在していない。 [ターゲット リソース] リストには、Resource Graph への照会の結果が表示されます。 新しいターゲットが有効化されてから、その更新が Resource Graph に反映されるまでに最大 5 分かかることがあります。 数分待ってから、[フォールトの追加] ペインをもう一度開いてください。
実験を作成するときに "microsoft:agent プロバイダーにはマネージド ID が必要です" というエラーが返される このエラーは、お使いの VM にエージェントがデプロイされていないときに発生します。 インストール手順については、エージェントベースの障害を使用する実験の作成と実行 に関するページを参照してください。
実験を作成するときに "コンテンツ メディアの種類 'null' はサポートされていません。 'application/json' のみがサポートされます" というエラーが返される このエラーは、Azure Resource Manager テンプレートまたは Chaos Studio REST API を使用して実験を作成するときに発生することがあります。 このエラーは、実験定義の中の JSON の形式に誤りがあることを示しています。 中かっこや角かっこ ({} と []) の不一致などの構文エラーがあるかどうかを調べてください。 調べるには、Visual Studio Code などの JSON リンターを使用します。
実験を実行するときに問題が発生することがあります。
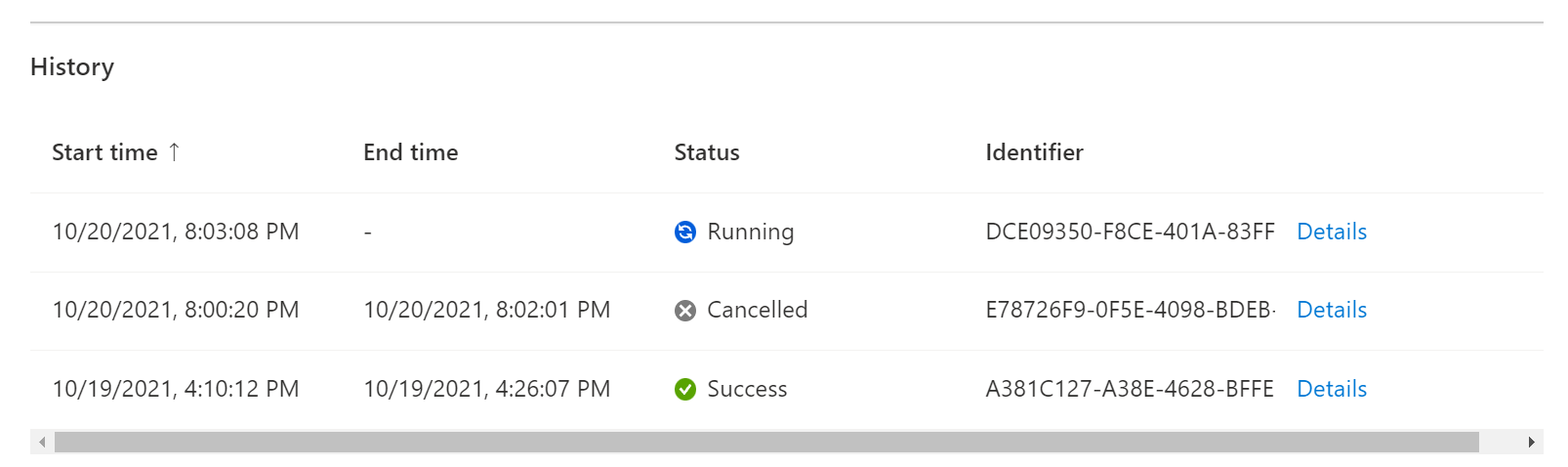
Azure portal の [実験] リストで実験名を選択すると、[実験の概要] が表示されます。 [履歴] セクションで、失敗した実験実行の横にある [詳細] をクリックして詳細なエラー情報を確認してください。
または、REST API を使用して実験の実行の詳細を取得します。 REST API サンプルの記事 で詳細を確認してください。
az rest --method post --url "https://management.azure.com/{experimentId}/executions/{executionDetailsId}/getExecutionDetails?api-version={apiVersion}"
エージェントベースのフォールトが失敗して "ターゲットが正しく追加されていることと適切な読み取りアクセス許可が実験 msi に付与されていることを確認してください" というエラーが返される このエラーは Azure portal を使用してエージェントを追加した場合に発生することがありますが、これは既知の問題です。 エージェント ベースのターゲットを有効にしても、ユーザー割り当てマネージド ID は VM または仮想マシン スケール セットに割り当てられません。
この問題を解決するには、Azure portal で VM または仮想マシン スケール セットに移動して [ID] に移動します。 [ユーザー割り当て] タブを開いて、ユーザー割り当て ID を VM に追加してください。 完了後に、エージェントを接続するために VM の再起動が必要になる場合があります。
このエラーは、複数のエージェント障害を同時に実行しようとすると発生します。 現在、エージェントは一度に 1 件のエージェント障害の実行のみをサポートしており、複数のエージェント障害を同時に実行する実験を定義すると失敗します。
実験の開始後、次のようなエラー メッセージが表示される場合があります: The long-running operation has failed. InternalServerError. The target resource(s) could not be resolved. Error Code: OperationFailedException。 通常、これは実験の ID に必要なアクセス許可がないことを意味しています。
このエラーを解決するには、実験のシステム割り当てマネージド ID またはユーザー割り当てマネージド ID に、実験内のすべてのリソースに対するアクセス許可があることを確認します。 アクセス許可の詳細はこちらで確認してください: Azure Chaos Studio でのアクセス許可とセキュリティ 。 たとえば、実験が仮想マシンを対象としている場合は、その仮想マシンの ID ページに移動し、"仮想マシン共同作成者" ロールを実験のマネージド ID に割り当てます。
AKS Chaos Mesh の障害の使用時に発生すると考えられる一般的なエラーにはいくつかあります。
テーブルを展開する
エラー メッセージ
推奨されるアクション
このクラスターはローカル アカウントを無効にするように設定されているため、静的資格情報の取得は許可されません。
バージョン 2.2 時点における AKS Chaos Mesh の障害では、Kubernetes ローカル アカウントまたは Microsoft Entra 認証を使用できます。 実験を移行する方法については、こちらの Chaos Studio AKS の障害での Microsoft Entra 認証の使用 に関する記事を参照してください。
提供された構成が無効だったため、Chaos Mesh の実験を開始できませんでした
jsonSpec にすべての必須フィールドが含まれていることを確認します。
Chaos Mesh バージョン "x.x.x" は、現在 Chaos Studio ではサポートされていません
インストールされているバージョンを Azure Chaos Studio バージョンの互換性 ページに照らして確認し、目的のバージョンが一覧にない場合は機能の要求 を提出します。
オブジェクト参照がオブジェクト インスタンスに設定されていません。
これはバージョン 2.2 エラーの既知のバグです。 修正プログラムは、2025 年 1 月上旬にデプロイを完了する予定です。 これは、ローカル アカウントが有効になっているクラスターで新しい AKS Chaos Mesh 障害バージョン (2.2) を使用する場合に発生します。 回避策は、UI で "(非推奨)" とマークされている v2.1 エラーを使用するか、Entra 認証が有効になっている AKS クラスターを使用することです。
システム割り当てまたはユーザー割り当てマネージド ID を既存の実験に追加しようとすると、保存に失敗します。 既に マネージド ID が割り当てられている実験にユーザー割り当てまたはシステム割り当てマネージド ID を追加しようとすると、実験のデプロイは失敗します。 目的のマネージド ID を追加する前に、まず 目的のテストで既存のユーザー割り当てまたはシステム割り当てマネージド ID を削除しておく必要があります。
実験の [カスタム ロールのアクセス許可] チェックボックスがオンになっている場合、Chaos Studio により、必要なアクセス許可を持つカスタム ロールが作成され、実験の ID に割り当てられます。 ただし、これには次のロールの割り当てとロール定義の制限が適用されます。
各 Azure サブスクリプションには、4,000 個というロールの割り当ての上限があります。
各 Microsoft Entra テナントには、5,000 個 (中国の Azure の場合は 2,000 個のロール定義) というロール定義の上限があります。
これらの制限のいずれかに達すると、このエラーが発生します。 これを回避するには、代わりに手動で実験 ID にアクセス許可を付与します。