Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to: ✅ Warehouse and Mirrored Database in Microsoft Fabric
Sharing is a convenient way to provide users read access to your data for downstream consumption. Sharing allows downstream users in your organization to consume a Warehouse using T-SQL, Spark, or Power BI. You can customize the level of permissions that the shared recipient is granted to provide the appropriate level of access.
Note
You must be an admin or member in your workspace to share an item in Microsoft Fabric.
Get started
After identifying the Warehouse item you would like to share with another user in your Fabric workspace, select the quick action in the row to Share.
The following animated gif reviews the steps to select a warehouse to share, select the permissions to assign, and then finally Grant the permissions to another user.
Share a warehouse
You can share your Warehouse from the OneLake or Warehouse item by choosing Share from quick action, as highlighted in the following image.
You're prompted with options to select who you would like to share the Warehouse with, what permissions to grant them, and whether they'll be notified by email.
Fill out all required fields, select Grant access.
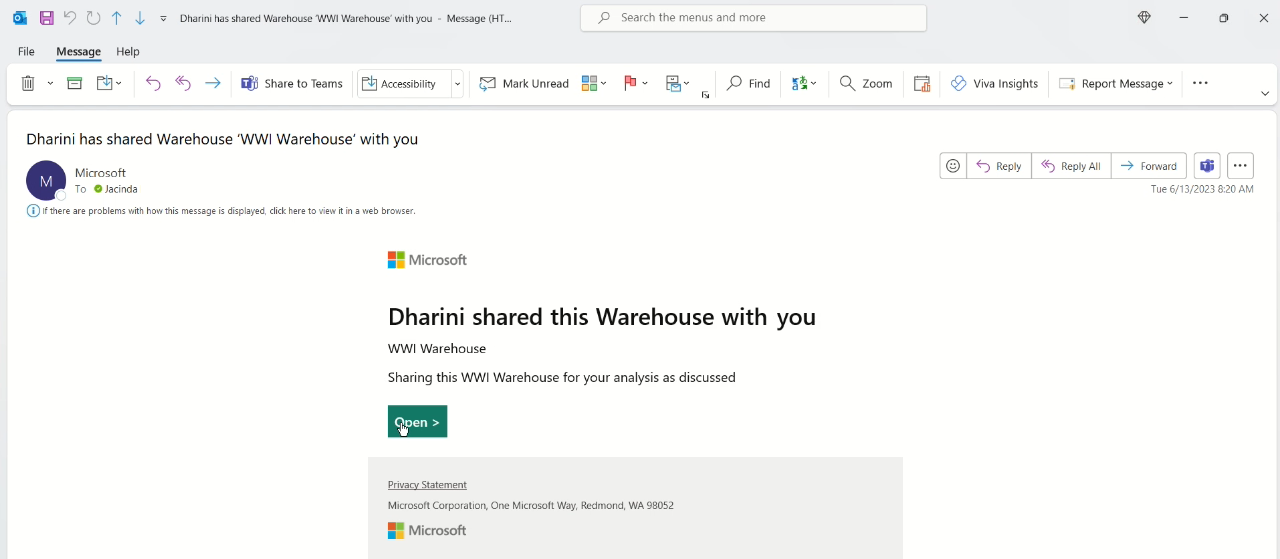
When the shared recipient receives the email, they can select Open and navigate to the Warehouse OneLake catalog page.
Depending on the level of access the shared recipient has been granted, the shared recipient is now able to connect to the SQL analytics endpoint, query the Warehouse, build reports, or read data through Spark.
Fabric security roles
Here's more detail about each of the permissions provided:
If no additional permissions are selected - The shared recipient by default receives "Read" permission, which only allows the recipient to connect to the SQL analytics endpoint, the equivalent of CONNECT permissions in SQL Server. The shared recipient won't be able to query any table or view or execute any function or stored procedure unless they're provided access to objects within the Warehouse using T-SQL GRANT statement.
Tip
ReadData (used by the warehouse for T-SQL permissions), ReadAll (used by OneLake and the SQL analytics endpoint), and Build (used by Power BI) are separate permissions that do not overlap.
"Read all data using SQL" is selected ("ReadData" permissions) - The shared recipient can read all the tables and views within the Warehouse in read-only mode. The shared recipient can also choose to copy the SQL analytics endpoint provided and connect to a client tool to run these queries. ReadData is the equivalent of db_datareader role in SQL Server. If you want to further restrict and provide granular access to some objects within the Warehouse, you can do this using T-SQL
GRANT/REVOKE/DENYstatements.- In the SQL analytics endpoint of the Lakehouse, "Read all SQL Endpoint data" is equivalent to "Read all data using SQL".
"Read all data using Apache Spark" is selected ("ReadAll" permissions) - The shared recipient should only be provided ReadAll if they want complete access to your warehouse's files using the Spark engine. A shared recipient with ReadAll permissions can find the Azure Blob File System (ABFS) path to the specific file in OneLake from the Properties pane in the Warehouse editor. The shared recipient can then use this path within a Spark Notebook to read this data. The recipient can also subscribe to OneLake events generated for the data warehouse in Real time hub.
- "Subscribe to events" ("SubscribeOneLakeEvents" permissions) - A shared recipient with this permission can subscribe to OneLake events generated for the warehouse in Fabric Real-Time Hub.
For example, a user with ReadAll permissions can query the data in
FactSalewith a Spark query in a new notebook."Build reports on the default dataset" is selected ("Build" permissions) - The shared recipient can build reports on top of the default semantic model that is connected to your Warehouse to create Power BI reports on this data from the OneLake catalog or Power BI Desktop. The Build checkbox is selected by default, but can be unchecked.
-
- Monitor – Users with Monitor permission can query Dynamic Management Views (DMVs), such as
sys.dm_exec_requests, query text, system connections, sessions, and Insights views. This permission is typically required for operational monitoring, troubleshooting, and performance analysis.
- Monitor – Users with Monitor permission can query Dynamic Management Views (DMVs), such as
Audit – Users with Audit permission can enable, configure, and query audit logs. With this permission, users can access auditing data to review activity history, monitor compliance, and support security investigations.
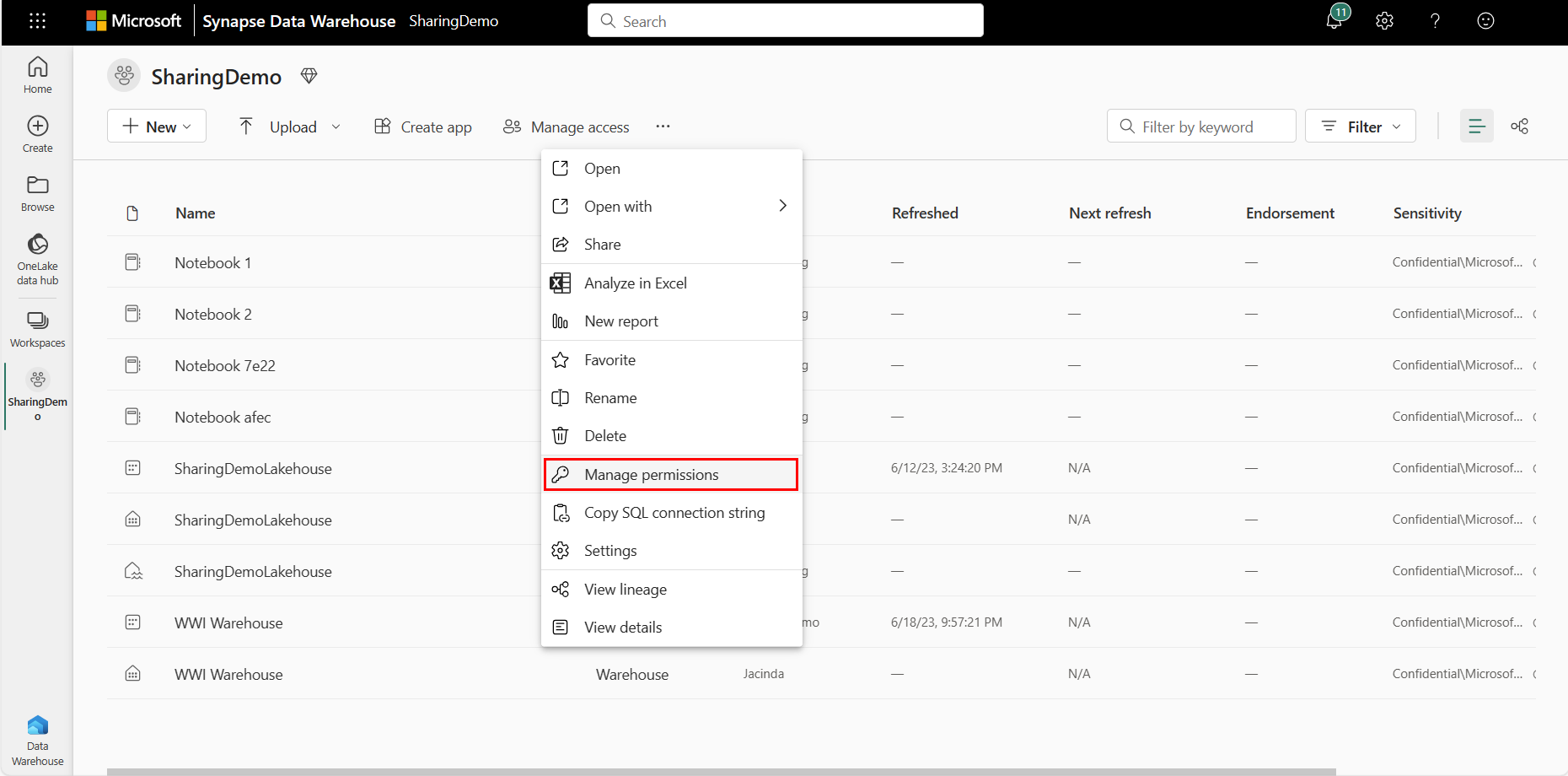
Manage permissions
The Manage permissions page shows the list of users who have been given access by either assigning to Workspace roles or item permissions.
If you're a member of the Admin or Member workspace roles, go to your workspace and select More options. Then, select Manage permissions.
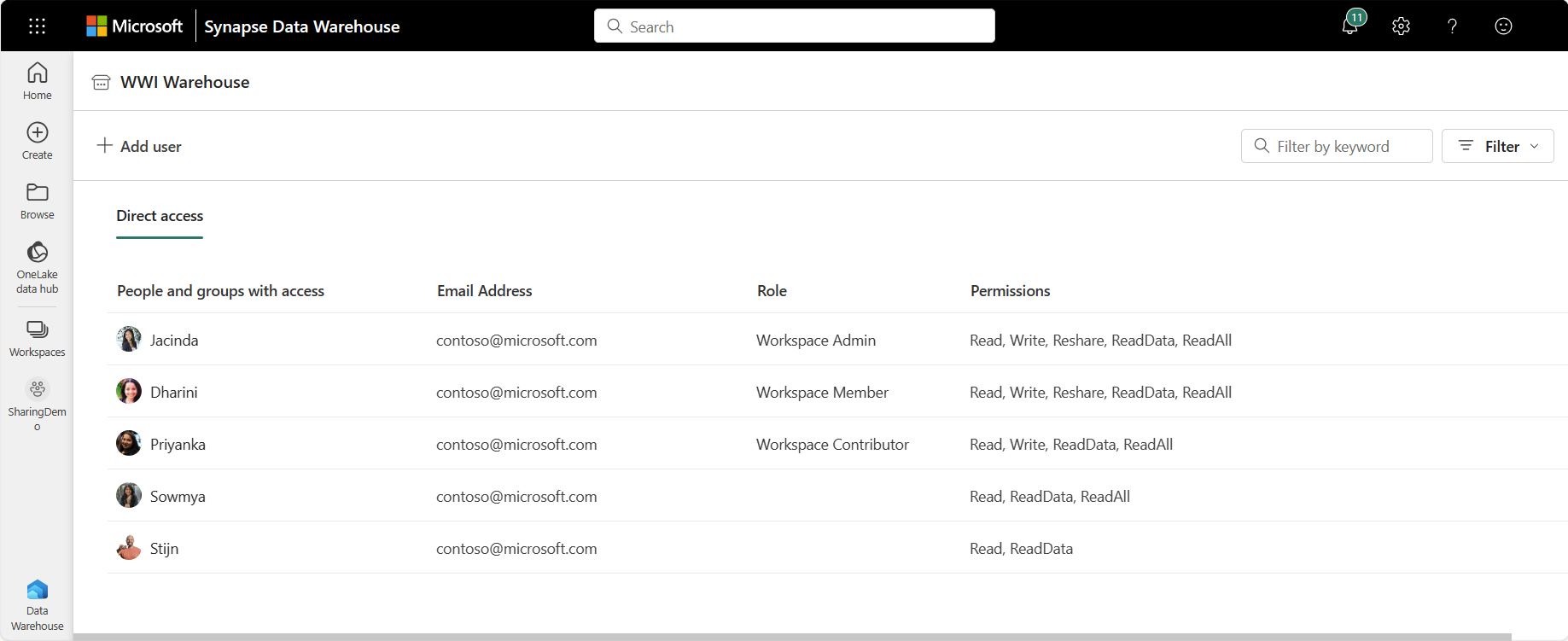
For users who were provided workspace roles, you'll see the corresponding user, workspace role, and permissions.
The following table lists which permission each role has by default and whether the permission is shareable.
| Permission | Given by default to | Shareable |
|---|---|---|
| Read | Admin, Member, Contributor, Viewer | Yes |
| ReadData | Admin, Member, Contributor, Viewer | Yes |
| ReadAll | Admin, Member, Contributor | Yes |
| Build | Admin, Member, Contributor | Yes |
| Write | Admin, Member, Contributor | No |
| Monitor | Admin, Member, Contributor | N/A - can't be granted on its own |
| Audit | Admin | N/A - can't be granted on its own |
| Reshare | Admin, Member | N/A - can't be granted on its own |
| Restore | Admin | No |
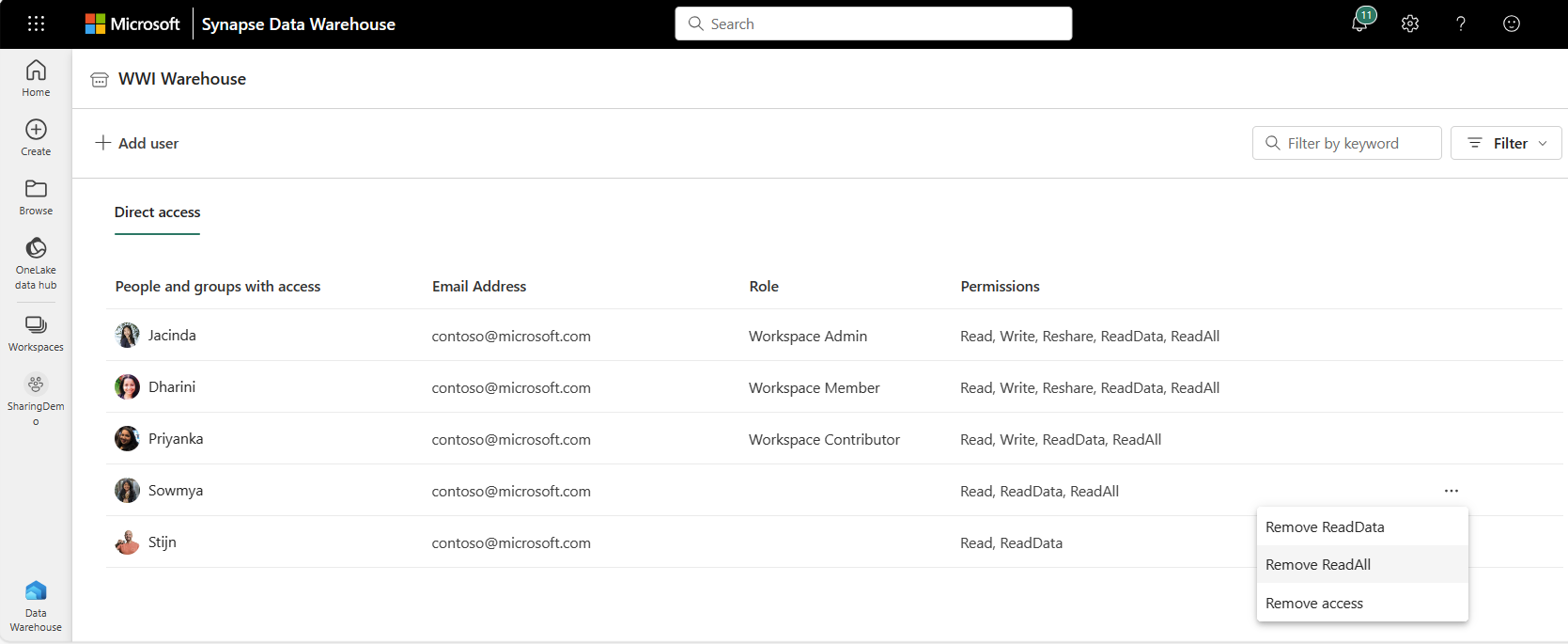
You can choose to add or remove permissions using Manage permissions:
- Remove access removes all item permissions.
- Remove ReadData removes the ReadData permissions.
- Remove ReadAll removes ReadAll permissions.
- Remove Build removes Build permissions on the corresponding default semantic model.
Data protection features
Microsoft Fabric data warehousing supports several technologies that administrators can use to protect sensitive data from unauthorized viewing. By securing or obfuscating data from unauthorized users or roles, these security features can provide data protection in both a Warehouse and SQL analytics endpoint without application changes.
- Column-level security prevents unauthorized viewing of columns in tables.
- Row-level security prevents unauthorized viewing of rows in tables, using familiar
WHEREclause filter predicates. - Dynamic data masking prevents unauthorized viewing of sensitive data by using masks to prevent access to complete, such as email addresses or numbers.
Limitations
- If you provide item permissions or remove users who previously had permissions, permission propagation can take up to two hours. The new permissions are visible in Manage permissions immediately. Sign in again to ensure that the permissions are reflected in your SQL analytics endpoint.
- Shared recipients are able to access the Warehouse using owner's identity (delegated mode). Ensure that the owner of the Warehouse is not removed from the workspace.
- Shared recipients only have access to the Warehouse they receive and not any other items within the same workspace as the Warehouse. If you want to provide permissions for other users in your team to collaborate on the Warehouse (read and write access), add them as Workspace roles such as Member or Contributor.
- Currently, when you share a Warehouse and choose Read all data using SQL, the shared recipient can access the Warehouse editor in a read-only mode. These shared recipients can create queries, but cannot currently save their queries.
- Currently, sharing a Warehouse is only available through the user experience.
- If you want to provide granular access to specific objects within the Warehouse, share the Warehouse with no additional permissions, then provide granular access to specific objects using T-SQL GRANT statement. For more information, see T-SQL syntax for GRANT, REVOKE, and DENY.
- If you see that the ReadAll permissions and ReadData permissions are disabled in the sharing dialog, refresh the page.
- Shared recipients do not have permission to reshare a Warehouse.
- If a report built on top of the Warehouse is shared with another recipient, the shared recipient needs more permissions to access the report. This depends on the mode of access to the semantic model by Power BI:
- If accessed through Direct query mode then ReadData permissions (or granular SQL permissions to specific tables/views) need to be provided to the Warehouse.
- If accessed through Direct Lake mode, then ReadData permissions (or granular permissions to specific tables/views) need to be provided to the Warehouse. Direct Lake mode is the default connection type for semantic models that use a Warehouse or SQL analytics endpoint as a data source. For more information, see Direct Lake mode.
- If accessed through Import mode then no additional permissions are needed.
- Currently, sharing a warehouse directly with an SPN is not supported.
- The sharing dialog for warehouses provides the option to subscribe to OneLake events. Currently, permission to subscribe to OneLake events is granted along with the Read All Apache Spark permission.