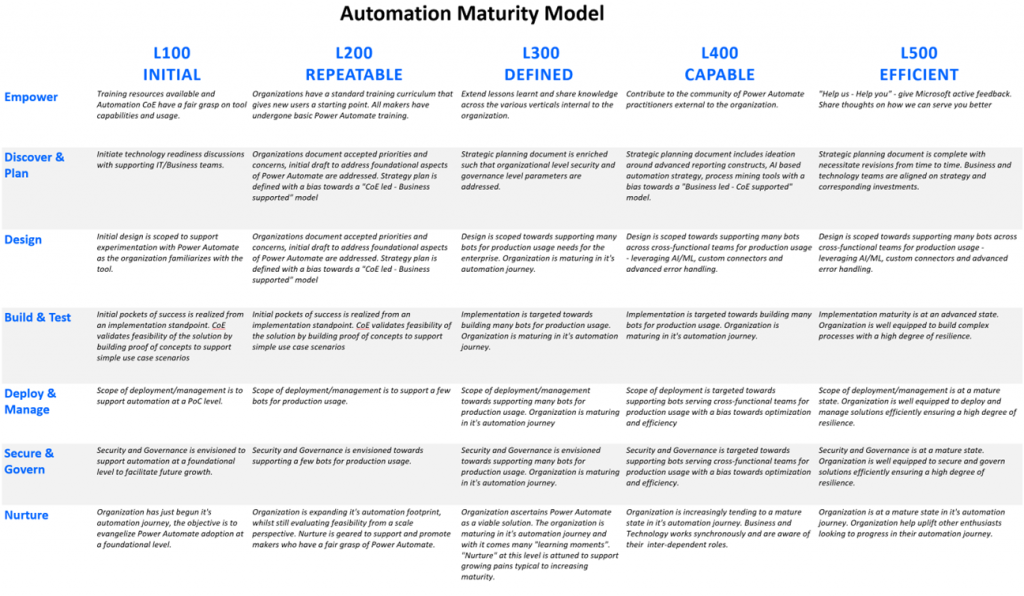
The following sections present detailed characteristics of an organization at each maturity level of the Power Platform automation maturity model for each type of capability.
Empower
| Level |
Details |
| 100: Initial |
Goal: Training resources available and Automation CoE have a fair grasp on tool capabilities and usage Indicators: - CoE have undergone initial training. (RPA in a day, Knowledge articles).
Resources: Maker Learning Resources |
| 200: Repeatable |
Goal: Organizations have a standard training curriculum that gives new users a starting point. All makers have undergone basic Power Automate training. Indicators: - Leverage Microsoft's training resources and accredit knowledge gained through certification programs
Resources: Microsoft Certified: Power Platform Fundamentals |
| 300: Defined |
Goal: Extend lessons learned and share knowledge across the various verticals internal to the organization. Indicators: - Internal Monthly hackathons/ know-how sessions are conducted.
- Leverage Power Platform Yammer groups
- Lunch and learn sessions
Resources: Organize Hackathons |
| 400: Capable |
Goal: Contribute to the community of Power Automate practitioners external to the organization. Indicators: - Engage and involve in Power Automate community based external events.
Resources: Microsoft Power Automate Community |
| 500: Efficient |
Goal: "Help us - Help you" - give Microsoft active feedback. Indicators: - Provide product feedback and showcase product capabilities to Microsoft organized initiatives such as Ignite and likewise.
Resources: Microsoft Ignite |
Discover & Plan
| Level |
Details |
| 100: Initial |
Goal: Initiate technology readiness discussions with supporting IT/Business teams. Indicators: - Architectural review meetings are established involving technology and business stakeholders.
- Key decision makers and stakeholders are identified
Resources: Power Automate Architecture - High Level |
| 200: Repeatable |
Goal: Organizations document accepted priorities and concerns, initial draft to address foundational aspects of Power Automate are addressed. Strategy plan is defined with a bias towards a "CoE led - Business supported" model Indicators: - High-level guidelines to address network, security and infrastructure concerns are defined
- Stakeholder roles and responsibilities are defined (Business, CoE, Security, Compliance and Admin)
- High level ROI factors are defined
Resources: |
| 300: Defined |
Goal: Strategic planning document is enriched such that organizational level security and governance level parameters are addressed. Indicators: - Network provisioning parameters including VM compute, machine groups and VNET setup are defined
- Credential/Access Management strategy is well defined - makers, administrators and CoE users and their corresponding roles and privileges are documented.
- Security Controls and RBAC policies are documented
- Data Encryption/Retention and Management strategy defined
- Business continuity and Disaster recovery plan in place
Resources: |
| 400: Capable |
Goal: Strategic planning document includes ideation around advanced reporting constructs, AI based automation strategy, process mining tools with a bias towards a "Business led - CoE supported" model Indicators: - Detailed operational and functional level analytics including KYC, Machine management, ROI calculator, License Utilization, Common exceptions list, top makers are defined.
- Opportunities to leverage AI builder.
- Process discovery through process mining
Resources: |
| 500: Efficient |
Goal: Strategic planning document is complete with necessitate revisions from time to time. Business and technology teams are aligned on strategy and corresponding investments. Indicators: - Strategy to automate governance based manual processes - ALM, Machine Management, DLP, Access Management and License Management.
- Design best practices shared amongst the Power Automate community.
Resources: |
Design
| Level |
Details |
| 100: Initial |
Goal: Initial design is scoped to support experimentation with Power Automate as the organization familiarizes with the tool. Indicators: - Design perspectives around the usage of API versus UI are explored
- Environment demarcation (Dev/Test/Prod) isn't well established.
Resources: Overview of different types of flows |
| 200: Repeatable |
Goal: Design is scoped to support a few bots in the production environment addressing basic automation needs within a department. Organization is still very early in its automation journey. Indicators: - Design considerations around logging and credential management are still at a rudimentary stage.
- Clear demarcation between (Dev/Test/Prod) is established at this point.
- Practitioners have a clear understanding on when to use API versus UI from a design perspective.
Resources: |
| 300: Defined |
Goal: Design is scoped towards supporting many bots for production usage needs for the organization. Organization is maturing in its automation journey. Indicators: - Logging and credential management is well established from a design perspective.
- Identity Security and Access Management tool integration to the infrastructure are well laid out.
- Code Review standards are well defined.
- Designing exception handling models using Try-Catch-Finally pattern
- Consider storage technology that scales proportionally
Resources: |
| 400: Capable |
Goal: Design is scoped towards supporting many bots across cross-functional teams for production usage - leveraging AI/ML, custom connectors and advanced error handling. Indicators: - Design considerations around templatization of common patterns and practices is well established.
- Establishing clear design strategies/blueprint on the usage of custom connectors is defined.
- Designing application health probes to check availability of the critical part of the systems such as load balancers and traffic managers.
Resources: |
| 500: Efficient |
Goal: Design is at a matured state and addresses all architectural challenges from an infrastructure, security, and governance perspective in conformance to the overarching organizational guidelines. Indicators: - Auto scaling capabilities - design thinking around use of machine groups based on process volume are well laid out.
- Advanced auditing capabilities to support proactive monitoring is supported
- Design considerations to handle transient faults in a cloud infrastructure
Resources: Handling Transient Faults in Azure |
Build & Test
| Level |
Details |
| 100: Initial |
Goal: Initial pockets of success are realized from an implementation standpoint. CoE validates feasibility of the solution by building proof of concepts to support simple use case scenarios. Indicators: - Practitioners build basic cloud and desktop flows to understand ground level functionality of the tool.
- Testing is confined to a PoC level.
- Monitoring is manual.
- Implementation is confined to a generic development environment.
Resources: Basic cloud and desktop flows |
| 200: Repeatable |
Goal: Implementation is targeted towards building a few bots for production usage. Organization continues to explore Power Automate capabilities. Indicators: - Code isn't adequately modularized/organized at this point.
- Code promotion between environments is manual.
- Power Automate Desktop installation and setup is manual
- Implementation covers both DPA (Digital Process Automation) and RPA (Robotic Process Automation) scenarios
- On-premises Gateway / Direct Machine connectivity implemented
- ROI calculation is primarily manual at this point
Resources: On-premises Gateway / Direct Machine connectivity |
| 300: Defined |
Goal: Implementation is targeted towards building many bots for production usage. Organization is maturing in its automation journey. Indicators: - Code is well modularized/organized - main flows and sub flows.
- Code promotion between environments is automated for both managed and unmanaged solutions
- Power Automate Desktop installation and setup is automated
- Credentials are managed through Azure Key Vault (or equivalent)
- Exception Handling best practices are implemented for:
- Cloud Flows: using Configure run after, Try/Catch, Error
- Desktop Flows: Action level and block level exception handling
Resources: |
| 400: Capable |
Goal: Implementation is targeted towards building many bots supporting cross-functional teams for production usage with a bias towards high level of resilience and reusability. Indicators: - Custom connectors, API support (for in house applications) are built by pro-developers to facilitate citizen developers to build automation.
- Reusable templates for both cloud and desktop flows are utilized.
- ROI calculation is automated.
- Processes are implemented leveraging AI Builder.
- Parallel execution of workloads to improve throughput are implemented
- Business Component Testing is well executed (validating other components, workload management, process branching, exception handling and performance measurement)
Resources: |
| 500: Efficient |
Goal: Implementation maturity is at an advanced state. Organization is well equipped to build complex processes with a high degree of resilience. Indicators: - Implementing distributed execution of workloads utilizing machine groups across auto-scaled virtual machines.
- Fusion teams involving developers from Cloud, AI and other technology capabilities build hybrid automation solutions.
Resources: Fusion Teams |
Deploy & Manage
| Level |
State of Nurture and Citizen Makers |
| 100: Initial |
Goal: Scope of deployment/management is to support automation at a PoC level. Indicators: - ALM is at a rudimentary stage, bot development is confined to a generic development environment.
- Network/Infrastructure deployment isn't scalable - confined to a bot(s)
- Automation is primarily executed in attended mode
- Bot monitoring and management are manual
- Source Control not implemented
Resources: Deployment and Management Guidelines |
| 200: Repeatable |
Goal: Scope of deployment/management is to support a few bots for production usage. Indicators: - Efforts to automate application deployment is underway.
- Version Control using source control software is implemented
- Backup and restore environments established
- Automation deployment supports both attended and unattended modes of execution
Resources: |
| 300: Defined |
Goal: Scope of deployment/management towards supporting many bots for production usage. Organization is maturing in its automation journey. Indicators: - ALM is automated - export, deploy, import pipelines in place
- Static Analyzers not yet implemented, validation and verification are manual
- Role privileges defining citizen developer/admin/auditor across environments are implemented.
- Configuration management and patch updates across multiple machines are managed using tools like Intune or SCCM.
- Monitoring/Reporting metrics (using Power BI/equivalent reporting tool) from a bot deployment perspective is in place (may not be real time)
Resources: |
| 400: Capable |
Goal: Scope of deployment is targeted towards supporting bots serving cross-functional teams for production usage with a bias towards optimization and efficiency. Indicators: - Leverage Dataverse to build use case specific dashboards.
- Add VM Insights solution to your Log Analytics workspace
- Configure connectivity tests using Connection Monitor in Azure
- Network deployment from a High Availability standpoint is complete - Azure availability zones, Azure disaster recovery implementation in place.
- Monitoring/Reporting metrics (using Power BI/equivalent reporting tool) from a bot deployment perspective is in place (is real time)
Resources: |
| 500: Efficient |
Goal: Scope of deployment/management is at a mature state. Organization is well equipped to deploy and manage solutions efficiently ensuring a high degree of resilience. Indicators: - Utilize Azure Monitor for monitoring workloads and resource utilization.
- Detect anomalous behavior by setting alerts, visual logs and monitoring.
- Log network traffic using NSG (Network Security Group) log flows using Azure Network Watcher
Resources: |
Secure & Govern
| Level |
Details |
| 100: Initial |
Goal: Security and Governance are envisioned to support automation at a foundational level to facilitate future growth. Indicators: - Governance/Security implementation maturity is at a rudimentary stage as there are fewer bots to oversee.
- Sensitive data that needs to be encrypted are identified in the bot building/exploration process.
- Access rights required to connect to external systems are identified.
Resources: Encrypt Sensitive Data |
| 200: Repeatable |
Goal: Security and Governance are envisioned towards supporting a few bots for production usage. Indicators: - Conditional Access Policies - define policies in Azure for Power Automate to grant or block based on user/group, device, location.
- Encrypt data at REST and in-transit
- Enforce HTTPS only communication for internet facing applications
- Encrypt connection to virtual machines using RDP
- Firewall Protection - Define Network security groups to allow/deny traffic outbound/inbound.
- Manage sensitive data in desktop flow - encrypt the data by using input as text type.
Resources: |
| 300: Defined |
Goal: Security and Governance are envisioned towards supporting many bots for production usage. Organization is maturing in its automation journey. Indicators: - Gateway/Machine connectivity is automated.
- License management is an automated process, licenses are assigned/unassigned based on team/department utilization needs.
- Secure credential storage and rotation in place.
- Access Management is automated to manage access as required to file paths, artifacts and applications.
- Usage of Dataverse Teams and Microsoft Entra groups, to effectively govern user permissions.
- Review Connector usage in PPAC (Power Platform Admin Center).
Resources: |
| 400: Capable |
Goal: Security and Governance are targeted towards supporting bots serving cross-functional teams for production usage with a bias towards optimization and efficiency. Indicators: - Proactive monitoring in place.
- Implement Cross Tenant Block to restrict third-party tenant access.
- Implement Granular End Point DLP definitions for connectors.
- Ensure Compliance standards are met based on industry (for example, PCI DSS - Payment Card Industry Data Standard etc.
Resources: |
| 500: Efficient |
Goal: Security and Governance are at a mature state. Organization is well equipped to secure and govern solutions efficiently ensuring a high degree of resilience. Indicators: - Implement Security Information Event Management (SIEM) to deliver intelligent security analytics and threat intelligence.
- Establish an app discovery process to identify new app connections (using application security management tools like, Microsoft Cloud App Security Management).
Resources: Security Information Event Management (SIEM) |
Nurture
| Level |
State of Fusion Teams |
| 100: Initial |
Goal: Organization has just begun its automation journey, the objective is to evangelize Power Automate adoption at a foundational level. Indicators: - Identify teams that need to be part of the automation journey
- Advocate the importance and impact of automation at a team setting level
Resources: Digital Transformation |
| 200: Repeatable |
Goal: Organization is expanding its automation footprint, whilst still evaluating feasibility from a scale perspective. Nurture is geared to support and promote makers who have a fair grasp of Power Automate. Indicators: - Allocate Roles and responsibilities based on individual job functions
- Automation Product Champions
- Automation Makers
- Automation CoE Team
- Establish point of contacts and stream leads whose objective is to evangelize and support automation across the organization.
Resources: Allocate Roles and responsibilities |
| 300: Defined |
Goal: Organization ascertains Power Automate as a viable solution. The organization is maturing in its automation journey and with it comes many "learning moments". "Nurture" at this level is attuned to support growing pains typical to increasing maturity. Indicators: - Beacons of automation support other citizen developers as they progress through a "try-fail-succeed" cycle.
- Citizen developers stride towards promoting solutions to production, while being supported through each step by their peers.
Resources: Beacons of automation |
| 400: Capable |
Goal: Organization is increasingly tending to a mature state in its automation journey. Indicators: - Teams share success stories, citizen developers advocate ROI gains across the organization because of automation.
- Teams initially hesitant to automation, begin to embrace automation convinced by its value proposition.
Resources: Real-World Automation Success Stories |
| 500: Efficient |
Goal: Organization is at a mature state in its automation journey. Indicators: - Offer individual recognitions and career paths to promising citizen developers.
- Encourage citizen developers to blog about their learnings and automation journey to benefit other enthusiasts who are starting out.
Resources: Career Paths for citizen developers |