Merk
Tilgang til denne siden krever autorisasjon. Du kan prøve å logge på eller endre kataloger.
Tilgang til denne siden krever autorisasjon. Du kan prøve å endre kataloger.
Denne artikkelen er et arkiv som beskriver oppdateringer gjort i tidligere versjoner av Defender for Cloud Apps. Hvis du vil se den nyeste listen over nyheter, kan du se Nyheter i Defender for Cloud Apps.
Juli 2025
Appstyring tilgjengelig i åtte nye områder
App Governance er nå også tilgjengelig i Brasil, Sverige, Norge, Sveits, Sør-Afrika, Sør-Korea, De arabiske emirater og Asia/Stillehavskysten. Hvis du vil ha mer informasjon, kan du se Slå på appstyring for Microsoft Defender for Cloud Apps.
Oppdaterte nettverkskrav for GCC- og Gov-kunder
Hvis du vil støtte kontinuerlige sikkerhetsforbedringer og vedlikeholde tjenestetilgjengelighet, krever Microsoft Defender for Cloud Apps nå oppdaterte brannmurkonfigurasjoner for kunder i GCC- og Gov-miljøer.
Hvis du vil unngå tjenesteavbrudd, må du gjøre noe innen 25. august 2025 og oppdatere brannmurkonfigurasjonen på følgende måte:
Tillat utgående trafikk på port 443 til følgende IP-områder:
51.54.53.136/2951.54.114.160/2962.11.173.176/29
Hvis du bruker Azure tjenestekoder, kan du legge AzureFrontDoor.MicrosoftSecurity til i tillatelseslisten for brannmuren.
Legg til følgende endepunkt i brannmurens tillatelsesliste på port 443:
discoveryresources-cdn-prod.cloudappsecurity.com
Hvis du vil se den fullstendige listen over nødvendige IP-adresser og endepunkter, kan du se Nettverkskrav.
Juni 2025
Datatypen Virkemåter i Microsoft Defender for Cloud Apps – generell tilgjengelighet
Datatypen Behaviors forbedrer den generelle nøyaktigheten for trusselregistrering ved å redusere varsler på generiske avvik og varsler om overflatefunksjon bare når observerte mønstre samsvarer med reelle sikkerhetsscenarioer. Nå kan du bruke virkemåter til å utføre undersøkelser i avansert jakt, bygge bedre egendefinerte oppdagelser basert på atferdssignaler og dra nytte av automatisk inkludering av kontekstrelatert atferd i hendelser. Dette gir klarere kontekst og hjelper sikkerhetsoperasjonsteamene med å redusere varslingstretthet, prioritere og reagere mer effektivt.
Hvis du vil ha mer informasjon, kan du se:
Ny modell for dynamisk trusselregistrering
Microsoft Defender for Cloud Apps nye dynamiske trusselregistreringsmodellen tilpasser seg kontinuerlig det stadig skiftende trussellandskapet for SaaS-apper. Denne fremgangsmåten sikrer at organisasjonen forblir beskyttet med oppdatert gjenkjenningslogikk uten behov for manuelle policyoppdateringer eller ny konfigurasjon. Flere eldre policyer for avviksregistrering er allerede sømløst overført til denne adaptive modellen, og leverer smartere og mer responsiv sikkerhetsdekning.
Hvis du vil ha mer informasjon, kan du se Opprette Defender for Cloud Apps policyer for avviksregistrering.
Mai 2025
Fornyet sammendragsrapport for Cloud Discovery Executive
Cloud Discovery Executive Summary-rapporten er oppdatert med en modernisert utforming og et strømlinjeformet format. Den nye versjonen reduserer rapporten fra 26 sider til seks sider, med fokus på den mest relevante og gjennomførbare innsikten, samtidig som lesbarheten og brukervennligheten forbedres. Hvis du vil ha mer informasjon, kan du se Hvordan du genererer en skyoppdagelsesrapport.
Ny lagerside for programmer er nå tilgjengelig i Defender XDR
Den nye Programmer-siden i Microsoft Defender XDR gir en samlet oversikt over alle SaaS og tilkoblede OAuth-programmer på tvers av miljøet ditt. Denne visningen bidrar til å effektivisere programoppdagelse, overvåking og risikovurdering.
Hvis du vil ha mer informasjon, kan du se Oversikt over programbeholdning.
Endringer i Microsoft Defender for Cloud Apps siem-agenttilgjengelighet
Som en del av vår pågående konvergensprosess på tvers av Microsoft Defender arbeidsbelastninger, vil Microsoft Defender for Cloud Apps SIEM-agenter bli avskrevet fra november 2025.
For å sikre kontinuitet og tilgang til data som for øyeblikket er tilgjengelige gjennom Microsoft Defender for Cloud Apps SIEM-agenter, anbefaler vi overgang til følgende støttede API-er:
- Hvis du vil ha varsler og aktiviteter, kan du se: Microsoft Defender XDR API for strømming.
- Hvis du vil ha Microsoft Entra ID Protection-påloggingshendelser, kan du se tabellen IdentityLogonEvents i det avanserte jaktskjemaet.
- For API for Microsoft Graph Security Alerts kan du se: Liste alerts_v2
- Hvis du vil vise Microsoft Defender for Cloud Apps varsler data i API-en for Microsoft Defender XDR hendelser, kan du se Microsoft Defender XDR hendelses-API-er og hendelsesressurstypene
Hvis du vil ha detaljert veiledning, kan du se Overføre fra Defender for Cloud Apps SIEM-agent til støttede API-er.
Ny og forbedret katalogside for skyapper
Katalogsiden for Skyappen er fornyet for å oppfylle sikkerhetsstandarder. Den nye utformingen inkluderer forbedret navigasjon, noe som gjør det enklere for deg å oppdage og administrere skyprogrammene dine.
Hvis du vil ha mer informasjon, kan du se: Finne skyappen og beregne risikoresultater.
April 2025
Oppdatering av brannmurkonfigurasjon som kreves innen 29. april 2025
Utfør umiddelbar handling innen april 29 2025, for å sikre optimal servicekvalitet og forhindre avbrudd i enkelte tjenester. Denne endringen påvirker bare organisasjonen hvis du bruker en brannmur-tillatelsesliste som begrenser utgående trafikk basert på IP-adresser eller Azure tjenestekoder. Oppdater brannmurreglene for å tillate utgående trafikk på port 443 for følgende IP-adresser: 13.107.228.0/24, 13.107.229.0/24, 13.107.219.0/24, 13.107.227.0/24, 150.171.97.0/24. Alternativt kan du bruke som en ekstra Azure servicekode, AzureFrontDoor.MicrosoftSecurity, som justeres for å gjenspeile området ovenfor innen 28. april 2025.\
- Denne oppdateringen skal være fullført, og IP-adressene eller den nye Azure-tjenestekoden legges til i brannmurens tillatelsesliste innen 29. april 2025.
- Denne endringen påvirker bare kommersielle kunder av Microsoft Defender for Cloud Apps. Kunder som er koblet til Gov US1- eller GCC-datasentre, blir ikke berørt.\
- Mer informasjon: Nettverkskrav.
OAuth-appinformasjon er nå tilgjengelig i angrepsbaner (forhåndsvisning)
Den Security Exposure Management plattformen inkluderer nå OAuth-programmer som en del av angrepsbanen og angrepsoverflatekartopplevelsene. Med denne forbedringen kan du visualisere hvordan angripere kan utnytte OAuth-apper til å bevege seg sidelengs i miljøet og få tilgang til kritiske ressurser. Ved å identifisere disse angrepsbanene og undersøke tilknyttede tillatelser, kan du redusere eksponeringen og forbedre sikkerhetsstillingen til Microsoft 365-tjenestene dine.
Hvis du vil ha mer informasjon, kan du se Undersøke OAuth-programangrepsbaner i Defender for Cloud Apps (forhåndsvisning)
OAuthAppInfo-tabell lagt til i Defender XDR avansert jakt (forhåndsvisning)
OAuthAppInfo-tabellen er nå tilgjengelig i Defender XDR avansert jakt, slik at sikkerhetsteam kan utforske og analysere OAuth-apprelaterte metadata med forbedret synlighet.
Denne tabellen inneholder detaljer om Microsoft 365-tilkoblede OAuth-programmer som er registrert med Microsoft Entra ID og tilgjengelig gjennom Defender for Cloud Apps appstyringsfunksjonalitet.
Siden Nye programmer i Defender XDR (forhåndsvisning)
Den nye Programmer-siden konsoliderer alle SaaS- og tilkoblede OAuth-programmer til én enkelt, enhetlig beholdning. Denne sentraliserte visningen effektiviserer programoppdagelse, overvåking og administrasjon, noe som gir større synlighet og kontroll over hele miljøet.
Siden viser viktige innsikter, for eksempel risikoresultater, bruksmønstre, utgiverbekreftelsesstatus og rettighetsnivåer. Denne innsikten hjelper deg med raskt å identifisere og håndtere programmer med høy risiko eller ukodede programmer.
Hvis du vil ha mer informasjon, kan du se Oversikt over programbeholdning
Mars 2025
Forbedret identitetsbeholdning (forhåndsversjon)
Identiteter-siden under Aktiva er oppdatert for å gi bedre synlighet og administrasjon av identiteter i hele miljøet. Den oppdaterte siden for identitetsbeholdning inneholder nå følgende faner:
Identiteter: En konsolidert visning av identiteter på tvers av Active Directory, Entra ID. Denne Identiteter-fanen uthever viktige detaljer, inkludert identitetstyper og brukerens informasjon.
Skyprogramkontoer: Gir innsikt i kontoer fra tilkoblede programmer via Defender for Cloud Apps, slik at du kan undersøke kontotillatelser, gruppemedlemskap, aliaser og programmene som er i bruk.
Hvis du vil ha mer informasjon, kan du se informasjon om identitetslager, skyprogramkontoer.
Role-Based Access Control omfang for Virkemåter (forhåndsvisning)
Defender for Cloud Apps kunder kan nå konfigurere Role-Based Access Control (RBAC)-omfang for «Virkemåter». Denne nye funksjonen gjør det mulig for administratorer å definere og administrere tilgangstillatelser mer nøyaktig. Administratorer kan sikre at brukere har riktig tilgangsnivå til bestemte programdata basert på rollene og ansvarsoppgavene. Ved å bruke RBAC-omfang kan organisasjoner forbedre sin sikkerhetsstilling, effektivisere operasjoner og redusere risikoen for uautorisert tilgang.
Hvis du vil ha mer informasjon, kan du se:
Februar 2025
Forbedret synlighet i OAuth-apper som er koblet til Microsoft 365 – generell tilgjengelighet
Defender for Cloud Apps brukere som bruker appstyring, kan få innsyn i opprinnelsen til OAuth-apper som er koblet til Microsoft 365. Du kan filtrere og overvåke apper som har ekstern opprinnelse, for proaktivt å gjennomgå slike apper og forbedre organisasjonens sikkerhetsstilling.
Med de nye *tillatelsesfilter- og eksportfunksjonene kan du raskt identifisere apper med bestemte tillatelser for å få tilgang til Microsoft 365.
Nå kan du få detaljert innsikt i data som brukes av apper ved hjelp av eldre EWS API sammen med Microsoft Graph. Den forbedrede dekningen av databruksinnsikt gjør det mulig å få dypere innsyn i apper som får tilgang til e-postmeldinger ved hjelp av eldre EWS API.
Vi utvider også dekningen av tilgangsnivåfunksjonen for alle populære API-tillatelser fra Microsoft. Den forbedrede dekningen av klassifisering på rettighetsnivå gjør det mulig å vise og overvåke apper med kraftige tillatelser til eldre og andre ikke-Graph-API-er som har tilgang til Microsoft 365.
Hvis du vil ha mer informasjon, kan du se detaljert innsikt i OAuth-apper.
Forbedret nøyaktighet for varslingskilde
Microsoft Defender for Cloud Apps forbedrer varslingskildene for å levere mer nøyaktig informasjon. Denne oppdateringen, som bare gjelder for nye varsler, gjenspeiles på tvers av ulike opplevelser og API-er, inkludert Microsoft Defender-portalen, avansert jakt og Graph API. Microsoft Defender for Cloud Apps forbedrer varslingskildene for å levere mer nøyaktig informasjon. Denne oppdateringen, som bare gjelder for nye varsler, gjenspeiles på tvers av ulike opplevelser og API-er, inkludert Microsoft Defender-portalen, avansert jakt og Graph API. Målet er å forbedre nøyaktigheten av varslingsopprinnelser, noe som forenkler bedre identifisering, administrasjon og respons på varsler.
Hvis du vil lære mer om de ulike varslingskildene i Defender XDR kan du se delen Varselkilderi Undersøk varsler i Microsoft Defender XDR – Microsoft Defender XDR | Microsoft Learn
Oppdateringer for nettverkskrav
Microsoft Defender for Cloud Apps har forbedret sikkerheten og ytelsen. Nettverksinformasjon i brannmurer og flere tredjepartstjenester må oppdateres for å overholde de nye standardene. For å sikre uavbrutt tilgang til tjenestene våre må du bruke disse endringene innen 16. mars 2025. Microsoft Defender for Cloud Apps har forbedret sikkerheten og ytelsen. Nettverksinformasjon i brannmurer og flere tredjepartstjenester må oppdateres for å overholde de nye standardene. For å sikre uavbrutt tilgang til tjenestene våre må du bruke disse endringene innen 27. mars 2025.
Hvis du vil koble til tredjepartsapper og aktivere Defender for Cloud Apps, bruker du følgende IP-adresser:
| Datasenter | IP-adresser | DNS-navn |
|---|---|---|
| USA1 | 13.64.26.88, 13.64.29.32, 13.80.125.22, 13.91.91.243, 40.74.1.235, 40.74.6.204, 51.143.58.207, 52.137.89.147, 52.183.75.62, 23.101.201.123, 20.228.186.154 | *.us.portal.cloudappsecurity.com |
| USA2 | 13.80.125.22, 20.36.222.59, 20.36.222.60, 40.74.1.235, 40.74.6.204, 51.143.58.207, 52.137.89.147, 52.183.75.62, 52.184.165.82, 20.15.114.156, 172.202.90.196 | *.us2.portal.cloudappsecurity.com |
| USA3 | 13.80.125.22, 40.74.1.235, 40.74.6.204, 40.90.218.196, 40.90.218.198, 51.143.58.207, 52.137.89.147, 52.183.75.62, 20.3.226.231, 4.255.218.227 | *.us3.portal.cloudappsecurity.com |
| EU1 | 13.80.125.22, 40.74.1.235, 40.74.6.204, 40.119.154.72, 51.143.58.207, 52.137.89.147, 52.157.238.58, 52.174.56.180, 52.183.75.62, 20.71.203.39, 137.116.224.49 | *.eu.portal.cloudappsecurity.com |
| EU2 | 13.80.125.22, 40.74.1.235, 40.74.6.204, 40.81.156.154, 40.81.156.156, 51.143.58.207, 52.137.89.147, 52.183.75.62, 20.0.210.84, 20.90.9.64 | *.eu2.portal.cloudappsecurity.com |
| Gov US1 | 13.72.19.4, 52.227.143.223 | *.us1.portal.cloudappsecurity.us |
| GCC | 52.227.23.181, 52.227.180.126 | *.us1.portal.cloudappsecuritygov.com |
For US Government GCC High-kunder :
| IP-adresser | DNS-navn | |
|---|---|---|
| Øktkontroller | USA Gov Arizona: 52.244.144.65, 52.244.43.90, 52.244.43.225, 52.244.215.117, 52.235.134.195, 52.126.54.167, 52.126.55.65 USA Gov Virginia: 13.72.27.223, 13.72.27.219, 13.72.27.220, 13.72.27.222, 20.141.230.137, 52.235.179.167, 52.235.184.112 |
*.mcas-gov.us *.admin-mcas-gov.us |
| Tilgangskontroller | USA Gov Arizona: 52.244.215.83, 52.244.212.197, 52.127.2.97, 52.126.54.254, 52.126.55.65 USA Gov Virginia: 13.72.27.216, 13.72.27.215, 52.127.50.130, 52.235.179.123, 52.245.252.18, 52.245.252.131, 52.245.252.191, 52.245.253.12, 52.245.253.58, 52.245.253.229, 52.245.254.39, 52.245.254.51, 52.245.254.212, 52.245.254.245, 52.235.184.112, 52.235.184.112 |
*.access.mcas-gov.us *.access.cloudappsecurity.us |
| SAML-proxy | USA Gov Arizona: 20.140.49.129, 52.126.55.65 USA Gov Virginia: 52.227.216.80, 52.235.184.112 |
*.saml.cloudappsecurity.us |
For US Government GCC-kunder :
| IP-adresser | DNS-navn | |
|---|---|---|
| Øktkontroller | USA Gov Arizona: 52.235.147.86, 52.126.49.55, 52.126.48.233 USA Gov Virginia: 52.245.225.0, 52.245.224.229, 52.245.224.234, 52.245.224.228, 20.141.230.215, 52.227.10.254, 52.126.48.233, 52.227.3.207 |
*.mcas-gov.ms *.admin-mcas-gov.ms |
| Tilgangskontroller | USA Gov Arizona: 52.127.2.97, 52.235.143.220, 52.126.48.233 USA Gov Virginia: 52.245.224.235, 52.245.224.227, 52.127.50.130, 52.245.222.168, 52.245.222.172, 52.245.222.180, 52.245.222.209, 52.245.223.38, 52.245.223.72, 52.245.223.177, 52.245.223.181, 52.245 .223.182, 52.245.223.190, 23.97.12.140, 52.227.3.207 |
*.access.mcas-gov.ms |
| SAML-proxy | Usa Gov Arizona: 52.126.48.233 USA Gov Virginia: 52.227.216.80, 52.126.48.233, 52.227.3.207 |
*.saml.cloudappsecuritygov.com |
Hvis du vil holde deg oppdatert på IP-områder, anbefales det å referere til følgende Azure tjenestekoder for Microsoft Defender for Cloud Apps tjenester. De nyeste IP-områdene finnes i tjenestekoden. Hvis du vil ha mer informasjon, kan du se Azure IP-områder.
November 2024
Varsel om intern øktkontrollprogram
Enterprise-programmet Microsoft Defender for Cloud Apps – øktkontroller brukes internt av appkontrolltjenesten for betinget tilgang.
Kontroller at det ikke finnes noen CA-policy som begrenser tilgangen til dette programmet.
For policyer som begrenser alle eller visse programmer, må du kontrollere at dette programmet er oppført som et unntak eller bekrefte at blokkeringspolicyen er bevisst.
Hvis du vil ha mer informasjon, kan du se Eksempel: Opprette Microsoft Entra ID policyer for betinget tilgang for bruk med Defender for Cloud Apps.
Defender for Cloud Apps støtte for Graph API (forhåndsversjon)
Defender for Cloud Apps kunder kan nå spørre etter data om oppdagede apper via Graph-API-en. Bruk Graph-API-en til å tilpasse visninger og automatisere flyter på siden Oppdagede apper , for eksempel bruke filtre til å vise bestemte data. API-en støtter bare GET-funksjoner .
Hvis du vil ha mer informasjon, kan du se:
- Arbeide med oppdagede apper via Graph API
- Microsoft Graph-API-referanse for Microsoft Defender for Cloud Apps
SaaS Security-initiativ i Exposure Management
Microsoft Security Exposure Management tilbyr en fokusert, metrisk drevet måte å spore eksponering på i bestemte sikkerhetsområder ved hjelp av sikkerhetsinitiativer. SaaS-sikkerhetsinitiativet gir en sentralisert plassering for alle anbefalte fremgangsmåter knyttet til SaaS-sikkerhet, kategorisert i 12 målbare måledata. Disse måledataene er utformet for effektiv administrasjon og prioritering av det store antallet sikkerhetsanbefalinger. Denne funksjonen er generell tilgjengelighet (over hele verden) – Vær oppmerksom på Microsoft Security Exposure Management data og funksjoner for øyeblikket er utilgjengelige i skyer fra amerikanske myndigheter – GCC, GCC High og DoD
Hvis du vil ha mer informasjon, kan du se SaaS sikkerhetsinitiativ.
Synlighet i appopprinnelse (forhåndsvisning)
Defender for Cloud Apps brukere som bruker appstyring, vil kunne få innsyn i opprinnelsen til OAuth-apper som er koblet til Microsoft 365. Du kan filtrere og overvåke apper som har ekstern opprinnelse, for proaktivt å gjennomgå slike apper og forbedre organisasjonens sikkerhetsstilling.
Hvis du vil ha mer informasjon, kan du se detaljert innsikt i OAuth-apper.
Tillatelsesfilter- og eksportfunksjoner (forhåndsvisning)
Defender for Cloud Apps brukere som bruker appstyring, kan bruke det nye tillatelsesfilteret og eksportere funksjoner for raskt å identifisere apper med bestemte tillatelser for å få tilgang til Microsoft 365.
Hvis du vil ha mer informasjon, kan du se filtre for appstyring.
Innsyn i tilgangsnivå for populære API-er fra Microsoft (forhåndsversjon)
Defender for Cloud Apps brukere som bruker appstyring, kan nå få innsyn i tilgangsnivå for alle populære API-tillatelser for Microsofts førsteparter. Den forbedrede dekningen av klassifisering på rettighetsnivå gjør det mulig å vise og overvåke apper med kraftige tillatelser til eldre og andre ikke-Graph-API-er som har tilgang til Microsoft 365.
Hvis du vil ha mer informasjon, kan du se OAuth-apptillatelsesrelaterte detaljer om appstyring.
Detaljert databruksinnsikt i EWS API-tilgang (forhåndsvisning)
Defender for Cloud Apps brukere som bruker appstyring, kan nå få detaljert innsikt i data som brukes av apper ved hjelp av eldre EWS API sammen med Microsoft Graph. Den forbedrede dekningen av databruksinnsikt gjør det mulig å få dypere innsyn i apper som får tilgang til e-postmeldinger ved hjelp av eldre EWS API.
Hvis du vil ha mer informasjon, kan du se OAuth-appens databruksinnsikt om appstyring.
Oktober 2024
Nye avviksdata i tabellen CloudAppEvents for avansert jakt
Defender for Cloud Apps brukere som bruker avansert jakt i Microsoft Defender-portalen, kan nå bruke de nye LastSeenForUser- og UncommonForUser-kolonnene for spørringer og gjenkjenningsregler.
De nye kolonnene er utformet for å hjelpe deg med å identifisere uvanlige aktiviteter som kan virke mistenkelige, og gi deg mulighet til å opprette mer nøyaktige egendefinerte oppdagelser og undersøke eventuelle mistenkelige aktiviteter som oppstår.
Hvis du vil ha mer informasjon, kan du se dataskjemaet Advanced Hunting "CloudAppEvents".
Ny appkontroll for betinget tilgang / innebygde data i avansert jakt i Tabellen CloudAppEvents
Defender for Cloud Apps brukere som bruker avansert jakt i Microsoft Defender-portalen, kan nå bruke de nye AuditSource- og SessionData-kolonnene for spørringer og gjenkjenningsregler. Bruk av disse dataene gjør det mulig for spørringer som vurderer bestemte overvåkingskilder, inkludert tilgangs- og øktkontroll, og spørringer etter bestemte innebygde økter.
Hvis du vil ha mer informasjon, kan du se dataskjemaet Advanced Hunting "CloudAppEvents".
Nye data i skyappeventstabell for avansert jakt – OAuthAppId
Defender for Cloud Apps brukere som bruker avansert jakt i Microsoft Defender-portalen, kan nå bruke den nye OAuthAppId-kolonnen for spørringer og gjenkjenningsregler.
Hvis du bruker OAuthAppId , kan spørringene som vurderer bestemte OAuth-programmer, gjøre spørringer og gjenkjenningsregler mer nøyaktige.
Hvis du vil ha mer informasjon, kan du se dataskjemaet Advanced Hunting "CloudAppEvents".
September 2024
Fremtving Microsoft Edge i nettleseren når du åpner forretningsapper
Administratorer som forstår kraften i Microsoft Edge-beskyttelse i nettleseren, kan nå kreve at brukerne bruker Microsoft Edge når de får tilgang til bedriftens ressurser.
En hovedårsak er sikkerhet, siden hindringen for å omgå øktkontroller ved hjelp av Microsoft Edge er høyere enn med omvendt proxy-teknologi.
Hvis du vil ha mer informasjon, kan du se Bruke Microsoft Edge-beskyttelse i nettleseren når du åpner forretningsapper.
Koble veggmaleri til Defender for Cloud Apps (forhåndsvisning)
Defender for Cloud Apps støtter nå tilkoblinger til Mural-kontoer ved hjelp av appkoblings-API-er, noe som gir deg innsyn i og kontroll over organisasjonens bruk av Mural.
Hvis du vil ha mer informasjon, kan du se:
- Slik bidrar Defender for Cloud Apps til å beskytte Mural-miljøet
- Koble til apper for å få synlighet og kontroll med Microsoft Defender for Cloud Apps
- Hjelpesenter for veggmaleri
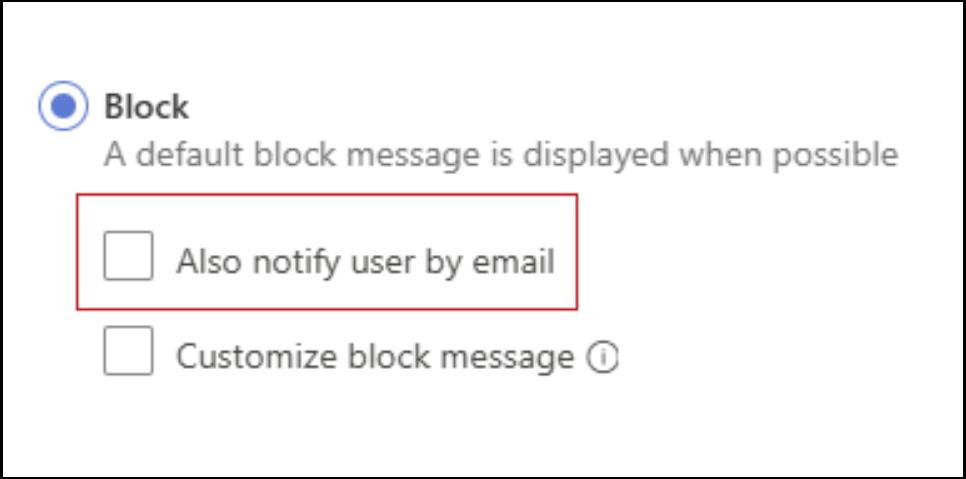
Fjerne muligheten til å sende e-post til sluttbrukere om blokkerte handlinger
Fra og med 1. oktober 2024 avslutter vi funksjonen som varsler sluttbrukere via e-post når handlingen blokkeres av øktpolicyer.
Dette alternativet sikrer at hvis en brukers handling blokkeres, får de både en nettlesermelding og et e-postvarsel.
Administratorer kan ikke lenger konfigurere denne innstillingen når de oppretter nye øktpolicyer.
Eksisterende øktpolicyer med denne innstillingen utløser ikke e-postvarsler til sluttbrukere når en blokkeringshandling utføres.
Sluttbrukere vil fortsette å motta blokkeringsmeldingen direkte via nettleseren og vil slutte å motta blokkeringsvarsel via e-post.
Skjermbilde av alternativet varsle sluttbrukeren via e-post:
30. august 2024
Omorganisert Defender for Cloud Apps dokumentasjon
Vi har omorganisert Microsoft Defender for Cloud Apps dokumentasjon for å utheve de viktigste produktsøylene og brukstilfellene våre, og for å samsvare med den generelle Microsoft Defender dokumentasjonen.
Bruk tilbakemeldingsmekanismene øverst og nederst på hver dokumentasjonsside til å sende oss kommentarer på Defender for Cloud Apps dokumentasjon.
Eksport av aktivitetslogger i stor skala (forhåndsversjon)
En ny brukeropplevelse dedikert til å gi brukerne muligheten til å eksportere fra «aktivitetslogg»-siden opptil seks måneder tilbake eller opptil 100 000 hendelser.
Du kan filtrere resultatene ved hjelp av tidsintervall og ulike andre filtre og til og med skjule private aktiviteter.
Hvis du vil ha mer informasjon, kan du se Eksporter aktiviteter for seks måneder siden.
Juli 2024
Konfigurer og bygg inn en egendefinert nettadresse for støtte i Blokker sider (forhåndsvisning)
Tilpass blokkeringsopplevelsen for Microsoft Defender for Cloud Apps(MDA) for apper som blokkeres ved hjelp av Cloud Discovery.
Du kan konfigurere en egendefinert nettadresse for omadressering på blokksider:
- Slik utdanner og omdirigerer du sluttbrukere til organisasjonens policy for akseptabel bruk
- Slik veileder du sluttbrukere på fremgangsmåten for å sikre et unntak for blokk
Hvis du vil ha mer informasjon, kan du se Konfigurere egendefinert NETTADRESSE for MDA-blokksider.
Beskyttelse i nettleseren for macOS-brukere og nylig støttede policyer (forhåndsversjon)
Microsoft Edge-nettleserbrukere fra macOS som er begrenset til øktpolicyer, er nå beskyttet med beskyttelse i nettleseren.
Følgende øktpolicyer støttes nå:
- Blokkere og overvåke opplasting av sensitive filer
- Blokker og overvåk lim inn
- Blokker og overvåk opplasting av skadelig programvare
- Blokker og overvåk nedlasting av skadelig programvare
Beskyttelse i nettleseren støttes med de to siste stabile versjonene av Microsoft Edge (for eksempel hvis den nyeste Microsoft Edge er 126, fungerer beskyttelse i nettleseren for v126 og v125).
Juni 2024
Automatisk omadressering for den klassiske Defender for Cloud Apps-portalen – generell tilgjengelighet
Den klassiske Microsoft Defender for Cloud Apps portalopplevelsen og funksjonaliteten har blitt konvergert til Microsoft Defender-portalen. Fra og med juni 2024 omdirigeres alle kunder som bruker den klassiske Defender for Cloud Apps-portalen automatisk til Microsoft Defender XDR, uten mulighet til å gå tilbake til den klassiske portalen.
Hvis du vil ha mer informasjon, kan du se Microsoft Defender for Cloud Apps i Microsoft Defender XDR.
Microsoft Entra ID apper registreres automatisk for appkontroll for betinget tilgang (forhåndsvisning)
Når du nå oppretter tilgangs- eller øktpolicyer med appkontroll for betinget tilgang, blir Microsoft Entra ID-appene automatisk pålastet og tilgjengelige for bruk i policyene dine.
Når du oppretter tilgangs- og øktpolicyer, velger du appene dine ved å filtrere etter automatisert Azure AD pålasting, for Microsoft Entra ID apper eller manuell pålasting for apper som ikke er Microsoft IdP-apper.
Eksempel:
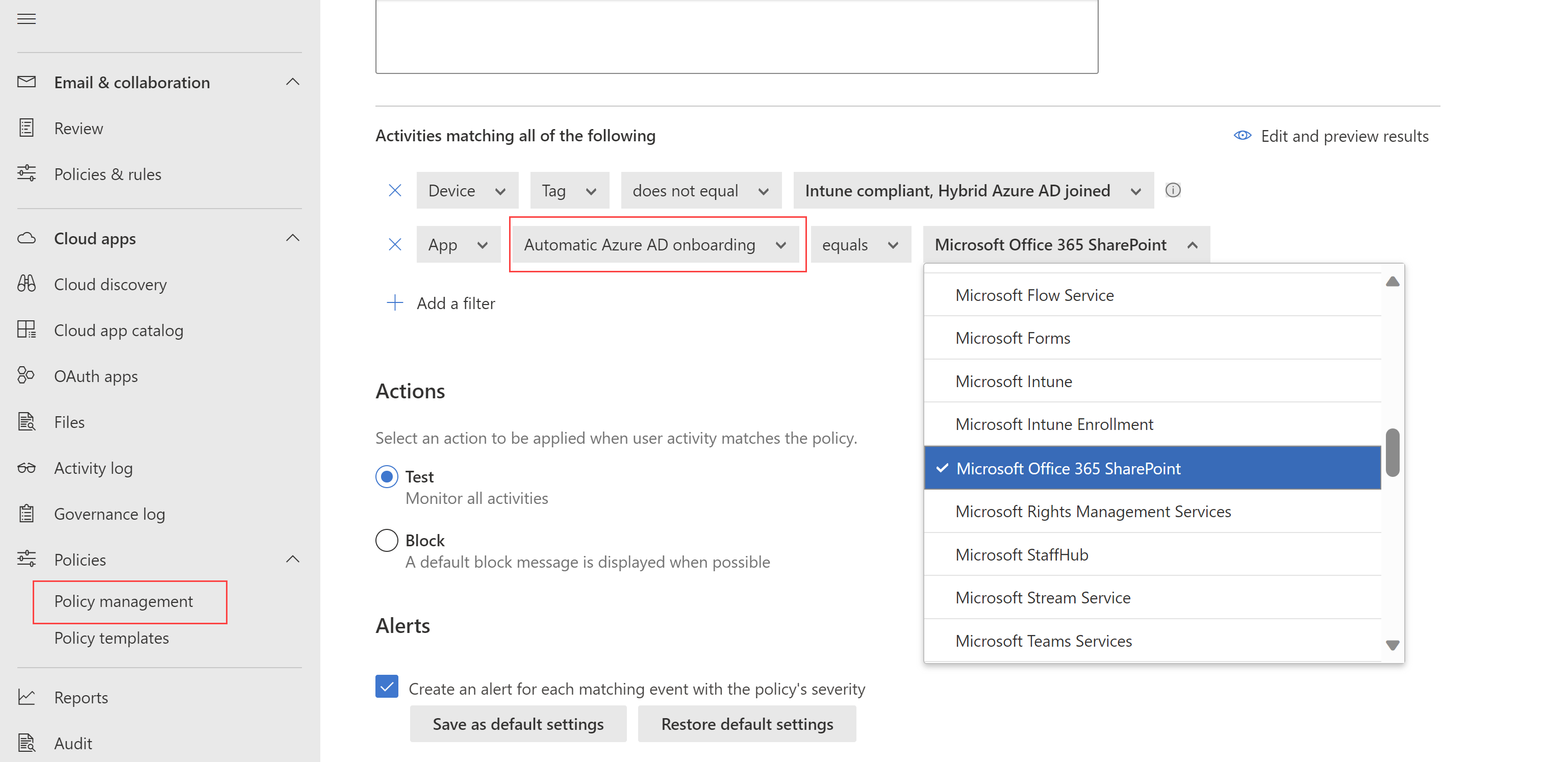
Ekstra trinn for bruk av appkontroll for betinget tilgang inkluderer fortsatt:
- Opprette en policy for Microsoft Entra ID betinget tilgang for appene du vil kontrollere med Defender for Cloud Apps appkontroll for betinget tilgang.
- Manuelle trinn til innebygde ikke-Microsoft IdP-apper, inkludert konfigurering av IdP-en til å fungere med Defender for Cloud Apps.
Hvis du vil ha mer informasjon, kan du se:
- Beskytt apper med Microsoft Defender for Cloud Apps appkontroll for betinget tilgang
- Prosessflyt for betinget tilgang-appkontroll
- Opprett tilgangspolicyer
- Opprett øktpolicyer
Defender for Cloud Apps søk på macOS (forhåndsversjon)
Defender for Cloud Apps støtter nå skyappoppdagelse på macOS-enheter sammen med Microsoft Defender for endepunkt-integrering. Defender for Cloud Apps og Defender for Endpoint sammen gir en sømløs Shadow IT-synlighet og kontrollløsning.
Sammen med denne forbedringen har alternativet Win10 Endpoint-brukere på Cloud Discovery-siden fått nytt navn til Defender-administrerte endepunkter.
Hvis du vil ha mer informasjon, kan du se:
- Integrere Microsoft Defender for endepunkt med Microsoft Defender for Cloud Apps
- Undersøke apper som oppdages av Microsoft Defender for endepunkt
AKS støttes for automatisk loggsamling (forhåndsversjon)
Microsoft Defender for Cloud Apps loggsamleren støtter nå Azure Kubernetes Service (AKS) når mottakertypen er Syslog-tls, og du kan konfigurere automatisk logginnsamling på AKS for kontinuerlig rapportering med Defender for Cloud Apps.
Hvis du vil ha mer informasjon, kan du se Konfigurere automatisk opplasting av logger ved hjelp av Docker på Azure Kubernetes Service (AKS).
Ny appkontroll for betinget tilgang / innebygde data for den avanserte skyappeventstabellen (forhåndsvisning)
Defender for Cloud Apps brukere som bruker avansert jakt i Microsoft Defender-portalen, kan nå bruke de nye AuditSource- og SessionData-kolonnene for spørringer og gjenkjenningsregler. Bruk av disse dataene gjør det mulig for spørringer som vurderer bestemte overvåkingskilder, inkludert tilgangs- og øktkontroll, og spørringer etter bestemte innebygde økter.
Hvis du vil ha mer informasjon, kan du se dataskjemaet Advanced Hunting "CloudAppEvents".
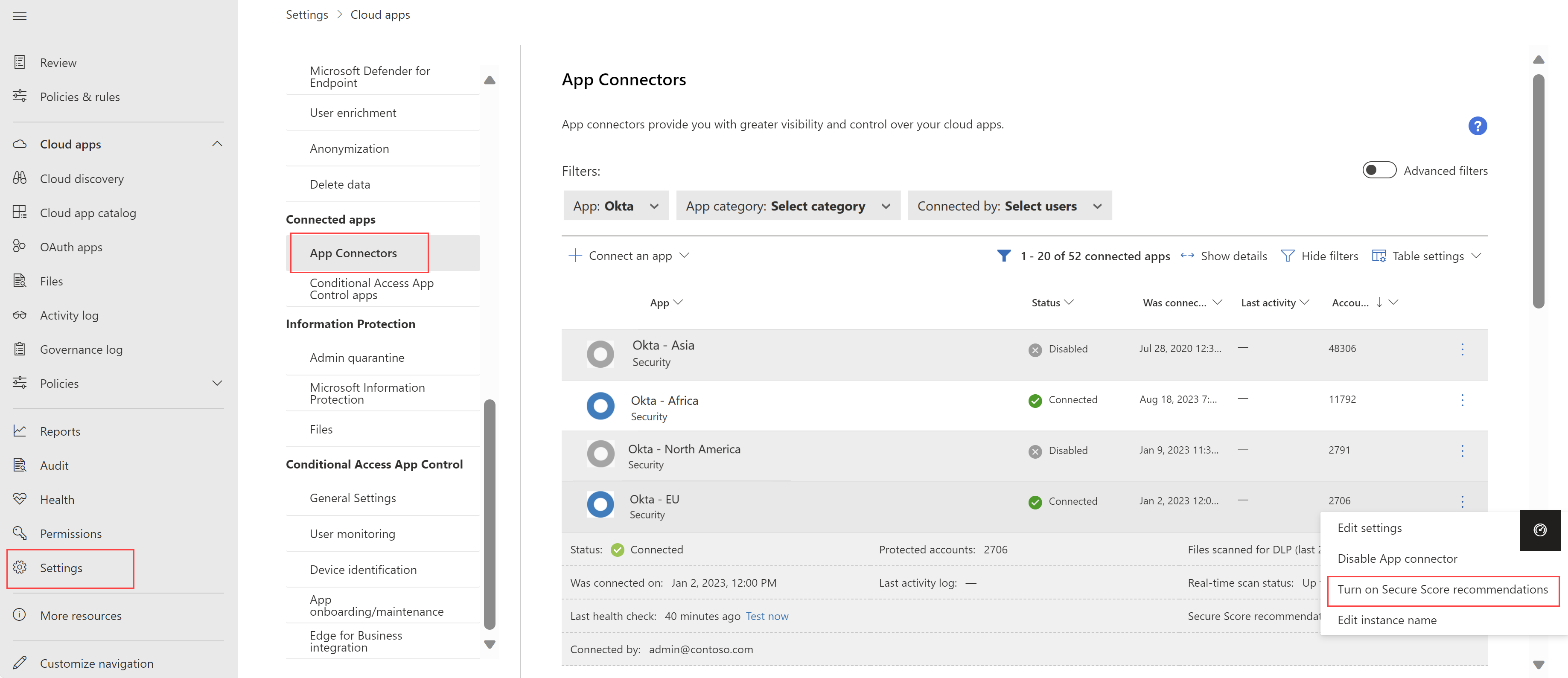
SSPM-støtte for flere forekomster av samme app er generelt tilgjengelig
Defender for Cloud Apps støtter nå SaaS security posture management (SSPM) på tvers av flere forekomster av samme app. Hvis du for eksempel har flere forekomster av Okta, kan du konfigurere anbefalinger for sikker poengsum for hver forekomst enkeltvis. Hver forekomst vises som et eget element på App Connectors-siden . Eksempel:
Hvis du vil ha mer informasjon, kan du se SaaS security posture management (SSPM).
Mai 2024
Defender for Cloud Apps i Microsoft Defender-portalen – generell tilgjengelighet og forhåndsvarsel for omadressering
Den Defender for Cloud Apps opplevelsen i Microsoft Defender-portalen er generelt tilgjengelig, og automatisk omadressering fra den klassiske portalen er aktivert som standard for alle kunder.
Fra og med 16. juni 2024 vil veksleknappen for omadressering ikke lenger være tilgjengelig. Fra da av omdirigeres alle brukere som har tilgang til den klassiske Microsoft Defender for Cloud Apps-portalen, automatisk til Microsoft Defender-portalen, uten mulighet til å melde seg ut.
For å klargjøre for denne endringen anbefaler vi at alle kunder som fortsatt bruker den klassiske portalflyttingsoperasjonen til Microsoft Defender-portalen. Hvis du vil ha mer informasjon, kan du se Microsoft Defender for Cloud Apps i Microsoft Defender XDR.
Slå på alternativer for forhåndsvisning i hovedinnstillingene for Microsoft Defender XDR (forhåndsvisning)
Nå kan forhåndsvisningskunder administrere innstillinger for forhåndsvisningsfunksjoner sammen med andre Microsoft Defender XDR forhåndsvisningsfunksjoner.
Velg Innstillinger > Microsoft Defender XDR > Generell > forhåndsvisning for å slå forhåndsvisningsfunksjoner på eller av etter behov. Eksempel:
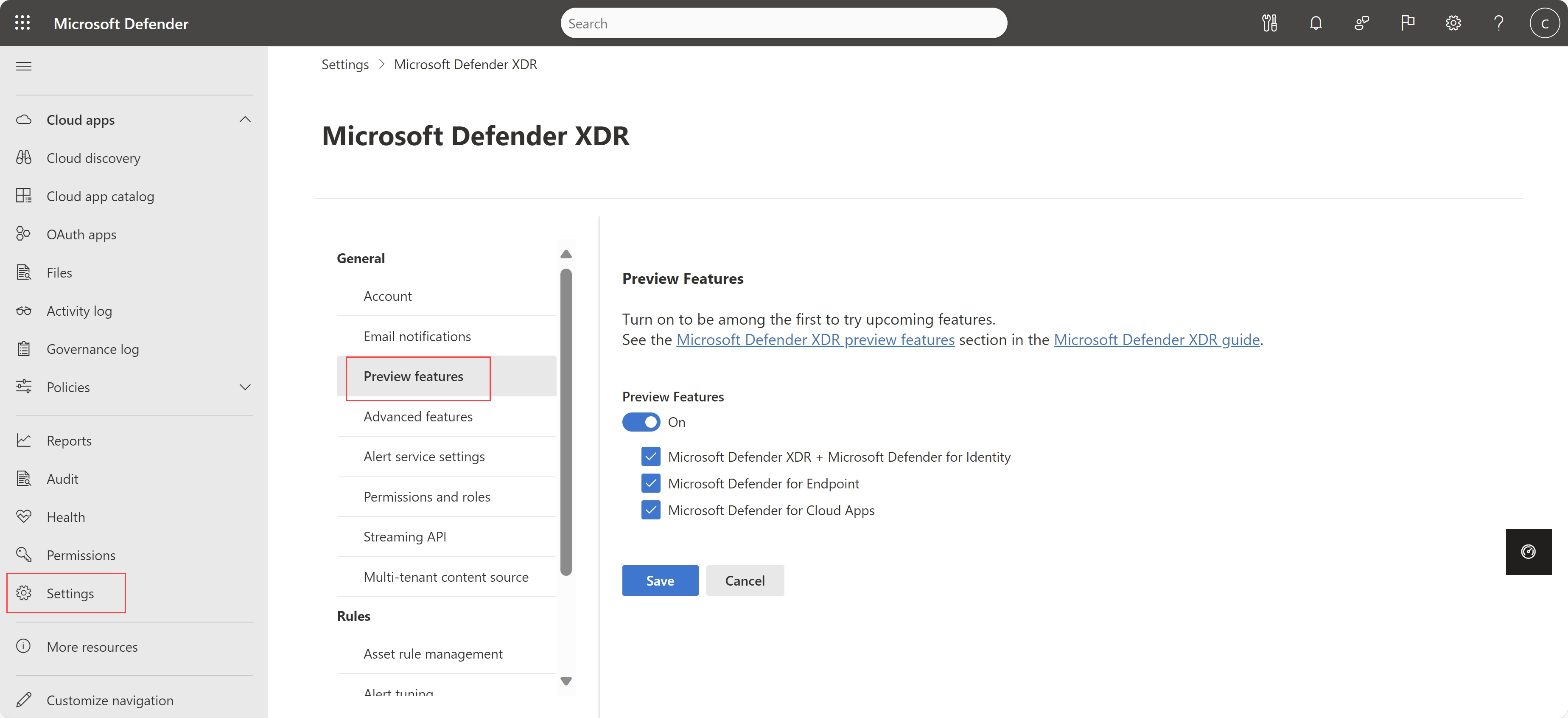
Kunder som ennå ikke bruker forhåndsvisningsfunksjoner, fortsetter å se de eldre innstillingene under System preview-funksjoner for Innstillinger-skyapper >>>.
Hvis du vil ha mer informasjon, kan du se Microsoft Defender XDR forhåndsvisningsfunksjoner.
Appstyring tilgjengelig for offentlige skyer
Funksjoner for appstyring i Defender for Cloud Apps er nå tilgjengelige i offentlige skyer. Hvis du vil ha mer informasjon, kan du se:
- Appstyring i Microsoft Defender for Cloud Apps
- Microsoft Defender for Cloud Apps for US Government-tilbud
April 2024
Aktiver datakryptering fra Microsoft Defender-portalen
Nå kan du fullføre prosessen for å kryptere Defender for Cloud Apps inaktive data med din egen nøkkel ved å aktivere datakryptering fra Innstillinger-området i Microsoft Defender-portalen.
Denne funksjonen er nå begrenset på den klassiske Microsoft Defender for Cloud Apps-portalen, og er bare tilgjengelig fra Microsoft Defender-portalen.
Hvis du vil ha mer informasjon, kan du se Kryptere Defender for Cloud Apps inaktive data med din egen nøkkel (BYOK).
Mars 2024
Ny logginnsamlingsversjon utgitt
Vi lanserte en ny versjon av en loggsamler med de nyeste sikkerhetsoppdateringene. Den nye versjonen er columbus-0.272.0-signed.jar, og bildenavnet er mcaspublic.azurecr.io/public/mcas/logcollectormed koden latest/0.272.0.
Endringer omfatter oppgradering av avhengigheter, for eksempel:
- amazon-corretto
- Ubuntu
- libssl
- oauthlib
- logback
- setuptools
Hvis du vil ha mer informasjon, kan du se Avansert administrasjon av logginnsamling.
Podman støttes for automatisk loggsamling (forhåndsversjon)
Microsoft Defender for Cloud Apps loggsamleren støtter nå Podman, og du kan konfigurere automatisk loggsamling på Podman for kontinuerlig rapportering med Defender for Cloud Apps.
Automatisk logginnsamling støttes ved hjelp av en Docker-beholder på flere operativsystemer. For Linux-distribusjoner som bruker RHEL versjon 7.1 og nyere, må du bruke Podman som beholderens kjøretidssystem.
Hvis du vil ha mer informasjon, kan du se Konfigurere automatisk loggopplasting ved hjelp av Podman.
Nye avviksdata for den avanserte skyappeventstabellen (forhåndsvisning)
Defender for Cloud Apps brukere som bruker avansert jakt i Microsoft Defender-portalen, kan nå bruke de nye LastSeenForUser- og UncommonForUser-kolonnene for spørringer og gjenkjenningsregler. Bruk av disse dataene bidrar til å utelukke falske positiver og finne avvik.
Hvis du vil ha mer informasjon, kan du se dataskjemaet Advanced Hunting "CloudAppEvents".
Nye trusselregistreringer for Microsoft Copilot for Microsoft 365
Defender for Cloud Apps tilbyr nå nye oppdagelser for risikable brukeraktiviteter i Microsoft Copilot for Microsoft 365 med Microsoft 365-koblingen.
- Relaterte varsler vises sammen med andre Microsoft Defender XDR varsler i Microsoft Defender-portalen.
- Copilot for Microsoft 365-aktiviteter er tilgjengelig i Defender for Cloud Apps aktivitetsloggen.
- På Microsoft Defender portalens avanserte jaktside er Copilot for Microsoft 365-aktiviteter tilgjengelige i CloudAppEvents-tabellen under Microsoft Copilot for Microsoft 365-programmet.
Hvis du vil ha mer informasjon, kan du se:
- Kom i gang med Microsoft Copilot for Microsoft 365
- Slik bidrar Defender for Cloud Apps til å beskytte Microsoft 365-miljøet
- Undersøke varsler i Microsoft Defender XDR
- Defender for Cloud Apps aktivitetslogg
- Proaktivt jakten på trusler med avansert jakt
- Tabellen CloudAppEvents i avansert jaktskjema
Data i bevegelsesbeskyttelse for Microsoft Edge for bedrifter brukere (forhåndsvisning)
Defender for Cloud Apps brukere som bruker Microsoft Edge for bedrifter og er underlagt øktpolicyer, er nå beskyttet direkte fra nettleseren. Beskyttelse i nettleseren reduserer behovet for proxyer, noe som forbedrer både sikkerhet og produktivitet.
Beskyttede brukere opplever en problemfri opplevelse med skyappene sine, uten ventetids- eller appkompatibilitetsproblemer og med et høyere sikkerhetsbeskyttelsesnivå.
Beskyttelse i nettleseren er aktivert som standard, og rulles gradvis ut på tvers av leiere, fra tidlig i mars 2024.
Hvis du vil ha mer informasjon, kan du se Beskyttelse i nettleseren med Microsoft Edge for bedrifter (forhåndsvisning),Beskytt apper med Microsoft Defender for Cloud Apps appkontroll for betinget tilgang og øktpolicyer.
Defender for Cloud Apps i Microsoft Defender-portalen er nå tilgjengelig for alle Defender for Cloud Apps roller
Den Defender for Cloud Apps opplevelsen i Microsoft Defender portalen er nå tilgjengelig for alle Defender for Cloud Apps roller, inkludert følgende roller som tidligere var begrenset:
- App-/forekomstadministrator
- Brukergruppeadministrator
- Global administrator for Cloud Discovery
- Administrator for Cloud Discovery-rapport
Hvis du vil ha mer informasjon, kan du se innebygde administratorroller i Defender for Cloud Apps.
Viktig
Microsoft anbefaler at du bruker roller med færrest tillatelser. Dette bidrar til å forbedre sikkerheten for organisasjonen. Global administrator er en svært privilegert rolle som bør begrenses til nødscenarioer når du ikke kan bruke en eksisterende rolle.
Februar 2024
SSPM-støtte for flere tilkoblede apper i generell tilgjengelighet
Defender for Cloud Apps gir deg sikkerhetsanbefalinger for SaaS-programmene for å hjelpe deg med å forhindre mulige risikoer. Disse anbefalingene vises via Microsoft Secure Score når du har en kobling til et program.
Defender for Cloud Apps har nå forbedret sin SSPM-støtte i generell tilgjengelighet ved å inkludere følgende apper:
SSPM støttes nå også for Google Workspace i generell tilgjengelighet.
Obs!
Hvis du allerede har en kobling til en av disse appene, kan poengsummen din i Sikker poengsum oppdateres automatisk i henhold til dette.
Hvis du vil ha mer informasjon, kan du se:
- SaaS security posture management (SSPM)
- Synlighet for bruker, appstyring og sikkerhetskonfigurasjon
- Microsoft Sikkerhetsvurdering
Nye appstyringsvarsler for legitimasjonstilgang og sideflytting
Vi har lagt til følgende nye varsler for appstyringskunder:
- Program som starter flere mislykkede KeyVault-leseaktivitet uten å lykkes
- Sovende OAuth App bruker hovedsakelig MS Graph eller Exchange Web Services som nylig ble sett på som tilgang Azure Resource Manager arbeidsbelastninger
Hvis du vil ha mer informasjon, kan du se Appstyring i Microsoft Defender for Cloud Apps.
Januar 2024
SSPM-støtte for flere forekomster av samme app (forhåndsvisning)
Defender for Cloud Apps støtter nå SaaS security posture management (SSPM) på tvers av flere forekomster av samme app. Hvis du for eksempel har flere forekomster av AWS, kan du konfigurere anbefalinger for sikker poengsum for hver forekomst individuelt. Hver forekomst vises som et eget element på App Connectors-siden . Eksempel:
Hvis du vil ha mer informasjon, kan du se SaaS security posture management (SSPM).
Begrensning fjernet for antall filer som kan kontrolleres for opplasting i øktpolicyer (forhåndsvisning)
Øktpolicyer støtter nå kontroll over opplasting av mapper med mer enn 100 filer, uten grense for antall filer som kan inkluderes i opplastingen.
Hvis du vil ha mer informasjon, kan du se Beskytt apper med Microsoft Defender for Cloud Apps appkontroll for betinget tilgang.
Automatisk omadressering for den klassiske Defender for Cloud Apps-portalen (forhåndsvisning)
Den klassiske Microsoft Defender for Cloud Apps portalopplevelsen og funksjonaliteten har blitt konvergert til Microsoft Defender-portalen. Fra og med 9. januar 2024 omdirigeres kunder som bruker den klassiske Defender for Cloud Apps-portalen med forhåndsvisningsfunksjoner automatisk til Microsoft Defender XDR, uten mulighet til å gå tilbake til den klassiske portalen.
Hvis du vil ha mer informasjon, kan du se:
- Microsoft Defender for Cloud Apps i Microsoft Defender XDR
- Microsoft Defender XDR forhåndsvisningsfunksjoner
Desember 2023
Nye IP-adresser for portaltilgang og SIEM-agenttilkobling
IP-adressene som brukes for portaltilgang og SIEM-agenttilkoblinger, er oppdatert. Pass på å legge til de nye IP-ene i brannmurens tillatelsesliste i henhold til dette for å holde tjenesten fullstendig funksjonell. Hvis du vil ha mer informasjon, kan du se:
Justering av gjenværende arbeidsperiode for første skanninger
Vi har justert gjenværende arbeidsperiode for første skanninger etter å ha koblet en ny app til Defender for Cloud Apps. Følgende appkoblinger har alle en innledende søkereserveperiode på sju dager:
Hvis du vil ha mer informasjon, kan du se Koble til apper for å få synlighet og kontroll med Microsoft Defender for Cloud Apps.
SSPM-støtte for flere tilkoblede apper
Defender for Cloud Apps gir deg sikkerhetsanbefalinger for SaaS-programmene for å hjelpe deg med å forhindre mulige risikoer. Disse anbefalingene vises via Microsoft Secure Score når du har en kobling til et program.
Defender for Cloud Apps har nå forbedret sin SSPM-støtte ved å inkludere følgende apper: (forhåndsvisning)
SSPM støttes nå også for Google Workspace i generell tilgjengelighet.
Obs!
Hvis du allerede har en kobling til en av disse appene, kan poengsummen din i Sikker poengsum oppdateres automatisk i henhold til dette.
Hvis du vil ha mer informasjon, kan du se:
- SaaS security posture management (SSPM)
- Synlighet for bruker, appstyring og sikkerhetskonfigurasjon
- Microsoft Sikkerhetsvurdering
November 2023
rotasjon for Defender for Cloud Apps programsertifikat
Defender for Cloud Apps planlegger å rotere programsertifikatet. Hvis du tidligere eksplisitt har klarert det eldre sertifikatet og for øyeblikket har SIEM-agenter som kjører på nyere versjoner av Java Development Kit (JDK), må du klarere det nye sertifikatet for å sikre fortsatt SIEM-agenttjeneste. Selv om det sannsynligvis ikke er nødvendig med noen handling, anbefaler vi at du kjører følgende kommandoer for å validere:
Bytt til bin-mappen for Java-installasjonen i et kommandolinjevindu, for eksempel:
cd "C:\Program Files (x86)\Java\jre1.8.0_291\bin"Utfør denne kommandoen:
keytool -list -keystore ..\lib\security\cacertsHvis du ser følgende fire aliaser, betyr det at du tidligere eksplisitt har klarert sertifikatet vårt og må utføre handlinger. Hvis disse aliasene ikke finnes, skal ingen handling være nødvendig.
- azuretls01crt
- azuretls02crt
- azuretls05crt
- azuretls06crt
Hvis du har behov for handling, anbefaler vi at du allerede stoler på de nye sertifikatene for å forhindre problemer når sertifikatene er fullstendig rotert.
Hvis du vil ha mer informasjon, kan du se vårt problem med nye versjoner av Feilsøkingsveiledning for Java .
CSPM-støtte i Microsoft Defender for Sky
Med de kontinuerlige Microsoft Defender for Cloud Apps konvergens til Microsoft Defender XDR, støttes CSPM-tilkoblinger (cloud security posture management) fullt ut via Microsoft Defender for Cloud.
Vi anbefaler at du kobler Azure-, AWS- og Google Cloud Platform (GCP)-miljøer til Microsoft Defender for skyen for å få de nyeste CSPM-funksjonene.
Hvis du vil ha mer informasjon, kan du se:
- Hva er Microsoft Defender for skyen?
- Cloud Security Posture Management (CSPM) i Defender for Cloud
- Koble Azure-abonnementene til Microsoft Defender for Cloud
- Koble AWS-kontoen til Microsoft Defender for Cloud
- Koble GCP-prosjektet til Microsoft Defender for Sky
Obs!
Kunder som fortsatt bruker den klassiske Defender for Cloud Apps-portalen, ser ikke lenger sikkerhetskonfigurasjonsvurderinger for Azure-, AWS- og GCP-miljøer.
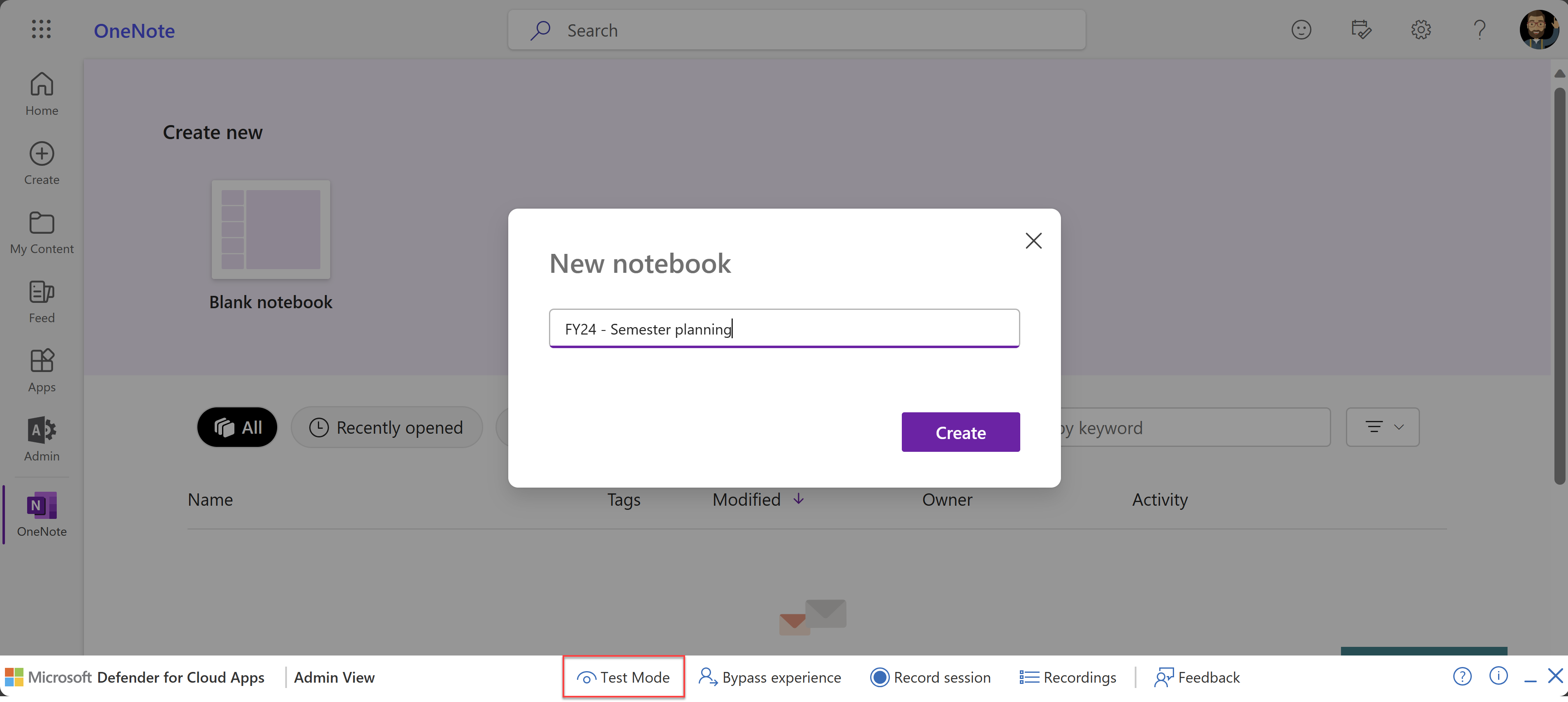
Testmodus for administratorbrukere (forhåndsvisning)
Som administratorbruker vil du kanskje teste kommende proxy-feilrettinger før den nyeste Defender for Cloud Apps utgivelsen distribueres fullstendig til alle leiere. For å hjelpe deg med dette, Defender for Cloud Apps nå en testmodus som er tilgjengelig fra verktøylinjen Admin visning.
Når du er i testmodus, vises bare administratorbrukere for eventuelle endringer som er angitt i feilrettingene. Det er ingen innvirkning på andre brukere. Vi oppfordrer deg til å sende tilbakemeldinger om de nye løsningene til Microsofts kundestøtteteam for å øke hastigheten på utgivelsessyklusene.
Når du er ferdig med å teste den nye løsningen, deaktiverer du testmodus for å gå tilbake til vanlig funksjonalitet.
Bildet nedenfor viser for eksempel den nye testmodusknappen på Admin vis-verktøylinjen, som er lagt over OneNote som brukes i en nettleser.
Hvis du vil ha mer informasjon, kan du se Diagnostisere og feilsøke med Admin vis verktøylinje ogtestmodus.
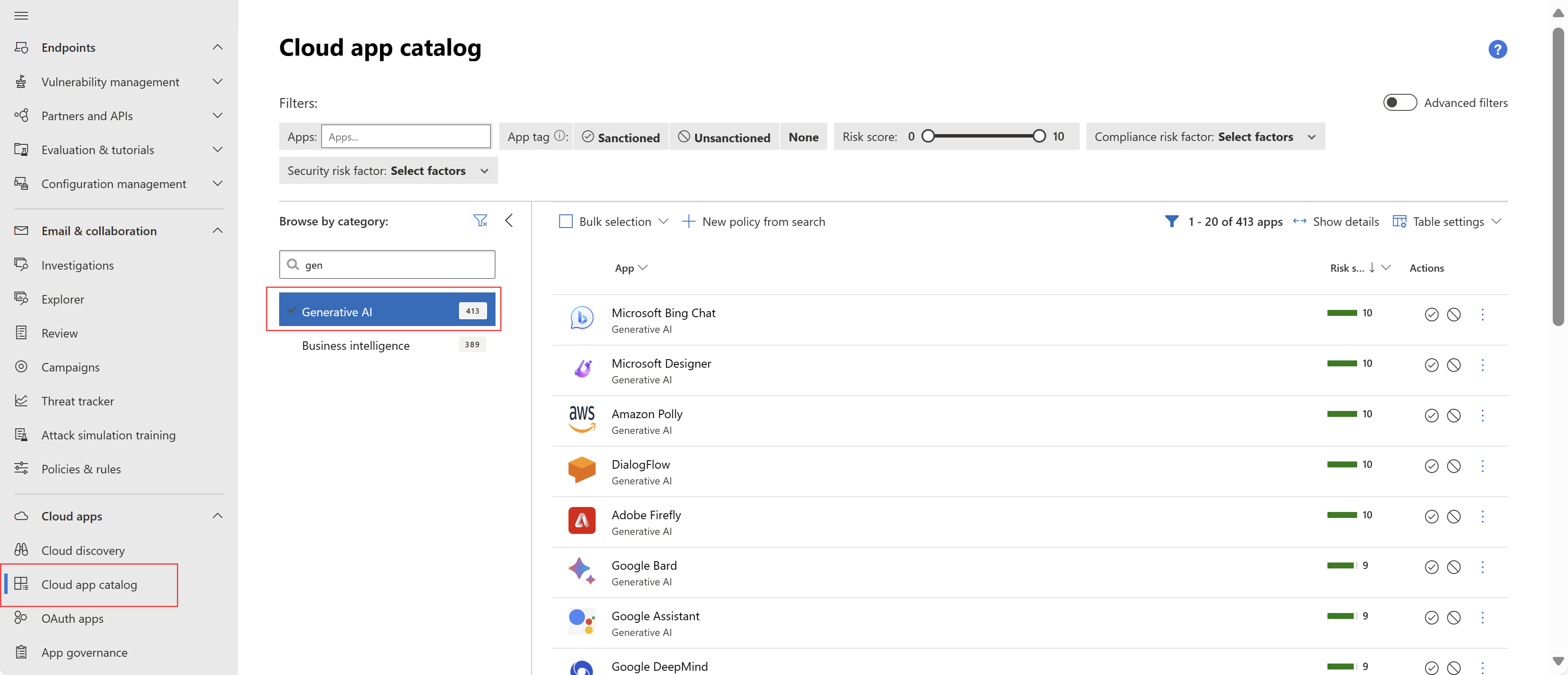
Ny katalogkategori for skyapp for Generative AI
Den Defender for Cloud Apps appkatalogen støtter nå den nye Generative AI-kategorien for store språkmodellapper (LLM), for eksempel Microsoft Bing Chat, Google Bard, ChatGPT og mer. Sammen med denne nye kategorien har Defender for Cloud Apps lagt til hundrevis av generative AI-relaterte apper i katalogen, noe som gir innsyn i hvordan generative AI-apper brukes i organisasjonen og hjelper deg med å administrere dem på en sikker måte.
Du vil for eksempel kanskje bruke Defender for Cloud Apps-integrering med Defender for Endpoint til å godkjenne eller blokkere bruken av bestemte LLM-apper basert på en policy.
Hvis du vil ha mer informasjon, kan du se Finne skyappen og beregne risikoresultater.
Generell tilgjengelighet for flere Shadow IT-hendelser med Defender for Endpoint
Defender for Cloud Apps nå kan oppdage Shadow IT-nettverkshendelser oppdaget fra Defender for Endpoint-enheter som arbeider i samme miljø som en nettverksproxy, i generell tilgjengelighet.
Hvis du vil ha mer informasjon, kan du se Oppdag apper via Defender for endepunkt når endepunktet er bak en nettverksproxy og Integrere Microsoft Defender for endepunkt.
Oktober 2023
Automatisk omdirigering til Microsoft Defender XDR generell tilgjengelighet
Nå blir alle kunder automatisk omdirigert til Microsoft Defender XDR fra den klassiske Microsoft Defender for Cloud Apps-portalen, siden omadresseringen er generelt tilgjengelig. Administratorer kan fortsatt oppdatere omadresseringsinnstillingen etter behov for å fortsette å bruke den klassiske Defender for Cloud Apps-portalen.
Integrering av Defender for Cloud Apps i Microsoft Defender XDR effektiviserer prosessen med å oppdage, undersøke og redusere trusler mot brukere, apper og data, slik at du kan se gjennom mange varsler og hendelser fra én enkelt glassrute i ett XDR-system.
Hvis du vil ha mer informasjon, kan du se Microsoft Defender for Cloud Apps i Microsoft Defender XDR.
September 2023
Flere oppdagelser for Shadow IT-hendelser (forhåndsvisning)
Defender for Cloud Apps kan nå oppdage Shadow IT-nettverkshendelser oppdaget fra Defender for Endpoint-enheter som arbeider i samme miljø som en nettverksproxy.
Hvis du vil ha mer informasjon, kan du se Oppdag apper via Defender for endepunkt når endepunktet er bak en nettverksproxy (forhåndsvisning) og integrere Microsoft Defender for endepunkt.
Kontinuerlig NRT-frekvens som støttes for CloudAPPEvents-tabellen (forhåndsvisning)
Defender for Cloud Apps støtter nå kontinuerlig (NRT)-frekvens for gjenkjenningsregler ved hjelp av CloudAppEvents-tabellen.
Hvis du angir at en egendefinert gjenkjenning skal kjøre i kontinuerlig frekvens (NRT), kan du øke organisasjonens mulighet til å identifisere trusler raskere. Hvis du vil ha mer informasjon, kan du se Opprette og behandle regler for egendefinerte gjenkjenninger.
August 2023
Nye sikkerhetsanbefalinger i Sikker poengsum (forhåndsversjon)
Nye Microsoft Defender for Cloud Apps anbefalinger er lagt til som forbedringshandlinger for Microsoft Secure Score. Hvis du vil ha mer informasjon, kan du se Nyheter i Microsoft Secure Score og Microsoft Secure Score.
Oppdateringer for Microsoft 365-kobling
Vi har gjort følgende oppdateringer for Defender for Cloud Apps Microsoft 365-kobling:
- (Forhåndsvisning) Oppdatert SSPM-støtte med nye cis-referansesikkerhetsanbefalinger .
- Justerte navnene på eksisterende anbefalinger for å samsvare med CIS-referanseverdien.
Hvis du vil vise relaterte data, må du kontrollere at du har konfigurert Microsoft 365-koblingen. Hvis du vil ha mer informasjon, kan du se Koble Microsoft 365 til Microsoft Defender for Cloud Apps.
Juli 2023
Log collector versjon 0.255.0
Defender for Cloud Apps har gitt ut Defender for Cloud Apps log collector versjon 0.255.0, inkludert oppdateringer til amazon-corretto og openssl avhengigheter.
Filnavnet for den nye versjonen er columbus-0.255.0-signed.jar, og bildenavnet er mcaspublic.azurecr.io/public/mcas/logcollectormed latest/0.255.0 koden.
Hvis du vil oppdatere loggsamleren, må du stoppe loggsamleren i miljøet ditt, fjerne det gjeldende bildet, installere det nye og oppdatere sertifikatene.
Hvis du vil ha mer informasjon, kan du se Avansert administrasjon av logginnsamling.
ServiceNow-koblingen støtter nå Utah-versjon
Defender for Cloud Apps ServiceNow-koblingen støtter nå ServiceNow Utah-versjonen. Hvis du vil ha mer informasjon, kan du se Koble ServiceNow til Microsoft Defender for Cloud Apps
Oppdateringer for Google Workspace-kobling
Google Workspace-koblingen støtter nå:
- (Forhåndsvisning) Verktøy for SaaS Security Posture Management (SSPM) for økt synlighet i SaaS-appenes holdningsfeilkonfigureringer sammenlignet med de ideelle appkonfigurasjonene. SSPM-funksjoner hjelper deg med proaktivt å redusere risikoen for brudd og angrep uten å måtte være sikkerhetsekspert for hver plattform.
- Aktiver godkjenningskontroll med flere faktorer. Hvis du vil vise relaterte data, må du kontrollere at du har konfigurert Google Workspace-koblingen.
Hvis du vil ha mer informasjon, kan du se Koble Google Workspace til Microsoft Defender for Cloud Apps.
Egendefinerte koblinger med åpen app-koblingsplattform (forhåndsvisning)
Defender for Cloud Apps nye kodeløse, åpne appkoblingsplattformen hjelper SaaS-leverandører med å opprette appkoblinger for SaaS-appene sine.
Opprett Defender for Cloud Apps koblinger for å utvide appsikkerhetsfunksjoner på tvers av kundenes SaaS-økosystemer, sikre data, redusere risikoer og forsterke den generelle SaaS-sikkerhetsstillingen.
Hvis du vil ha mer informasjon, kan du se Microsoft Defender for Cloud Apps åpne appkoblingsplattformen.
Nye appkoblinger for Asana og Miro (forhåndsversjon)
Defender for Cloud Apps støtter nå innebygde appkoblinger for Asana og Miro, som begge kan inneholde kritiske data i organisasjonen og er derfor mål for ondsinnede aktører. Koble disse appene til Defender for Cloud Apps for bedre innsikt i brukernes aktiviteter og trusselregistrering med maskinlæringsbaserte avviksregistreringer.
Hvis du vil ha mer informasjon, kan du se:
Konsolidering av økt- og tilgangspolicy
Defender for Cloud Apps forenkler nå arbeidet med både økt- og tilgangspolicyer. Tidligere, for å opprette en økt eller tilgangspolicy for en vertsapp, for eksempel Exchange, Teams eller Gmail, må kundene opprette en egen policy for alle relevante ressursapper, for eksempel SharePoint, OneDrive eller Google Drive. Fra og med 11. juli 2023 trenger du nå bare å opprette én enkelt policy på den vertsbaserte appen.
Hvis du vil ha mer informasjon, kan du se:
Automatisk omadressering til Microsoft Defender XDR (forhåndsvisning)
Kunder som bruker forhåndsvisningsfunksjoner, omdirigeres nå automatisk til Microsoft Defender XDR fra den klassiske Microsoft Defender for Cloud Apps-portalen. Administratorer kan fortsatt oppdatere omadresseringsinnstillingen etter behov for å fortsette å bruke den klassiske Defender for Cloud Apps-portalen.
Hvis du vil ha mer informasjon, kan du se Omadressere kontoer fra Microsoft Defender for Cloud Apps til Microsoft Defender XDR.
Juni 2023
Obs!
Fra og med juni 2023 er oppdateringer for appstyring oppført sammen med andre Microsoft Defender for skyfunksjoner. Hvis du vil ha informasjon om tidligere versjoner, kan du se Hva er nytt i appstyringstillegget for Defender for Cloud Apps.
Nye IP-adresser for tilgangs- og øktkontroller
IP-adressene som brukes for våre tilgangs- og øktkontrolltjenester, er oppdatert. Pass på å oppdatere brannmurens tillatelsesliste i henhold til dette for å holde tjenesten fullstendig funksjonell. Adresser som nylig er lagt til, omfatter:
| Datasenter | Offentlige IP-er |
|---|---|
| Brasil, sør | 191.235.54.192, 191.235.58.85, 191.235.59.0, 191.235.58.255, 191.235.58.203, 191.235.57.180, 191.235.58.56, 191.235.58.201, 20.206.229.223, 191.235.55.73, 20.206.75.66, 20.226.100.200, 20.206.231.146, 104.41.37.185 |
| USA, vest 3 | 20.14.38.222, 20.14.38.249, 20.150.153.126, 20.150.157.146, 20.150.157.211, 20.150.152.101, 20.106.80.235, 20.106.81.123, 20.150.158.183, 20.150.153.110, 20.118.150.70, 20.118.145.8, 20.150.143.88, 20.125.76.39, 20.106.103.34, 20.163.100.176 |
| Europa, nord | 20.166.182.165, 20.166.182.171, 20.166.182.163, 20.166.182.193, 4.231.129.248, 20.54.22.195, 4.231.129.246, 20.67.137.212, 40.127.131.206, 20.166.182.159, 20.166.182.182, 68.219.99.39, 20.166.182.204, 68.219.99.63 |
| Canada, sentralt | 20.175.151.201, 20.175.142.34, 20.175.143.233, 4.205.74.15, 20.175.142.19, 20.175.142.143, 20.175.140.191, 20.175.151.166, 20.175.140.185, 20.175.143.220, 20.175.140.128, 20.104.25.35, 4.205.74.7, 20.220.128.26 |
| Øst-Asia | 20.195.89.186, 20.195.89.213, 20.195.89.128, 20.195.89.62, 20.195.89.219, 20.239.27.66, 20.239.26.193, 20.195.89.72, 20.195.89.166, 20.195.89.56, 20.187.114.178, 20.239.119.245, 20.205.119.72, 20.187.116.207 |
| Australia, sørvest | 20.211.237.204, 20.92.29.167, 4.198.154.86, 4.198.66.117, 4.198.66.135, 20.11.210.40, 4.198.66.90, 20.92.8.154, 4.198.66.105, 4.198.66.78, 20.190.102.146, 4.198.66.126, 4.198.66.94, 4.198.66.92 |
| India, sentralt | 20.219.226.117, 20.204.235.50, 20.235.81.243, 20.204.235.230, 20.219.226.224, 20.204.236.111, 20.204.236.147, 20.204.236.213, 20.204.236.115, 20.204.236.74, 20.204.236.17, 20.235.115.136, 20.219.218.134, 20.204.251.239, 4.224.61.207 |
| Sørøst-Asia | 20.24.14.233 |
| Frankrike, sentralt | 20.74.115.131, 20.74.94.109, 20.111.40.153, 20.74.94.42, 20.74.94.220, 51.103.31.141, 20.74.95.102, 20.74.94.113, 51.138.200.138, 20.74.94.139, 20.74.94.136, 51.103.95.227, 20.74.114.253, 20.74.94.73 |
| Europa, vest | 20.76.199.12, 20.160.197.20, 20.76.199.126, 20.76.198.169, 20.4.196.150, 20.76.199.32, 13.69.81.118, 20.76.151.201, 20.76.199.49, 20.76.198.36, 20.76.199.14, 20.76.198.91, 20.93.194.151, 20.229.66.63 |
| Storbritannia, vest | 20.90.53.127, 51.142.187.141, 20.68.122.206, 20.90.53.162, 20.90.53.126, 20.90.50.109, 20.90.53.132, 20.90.53.133, 20.68.124.199, 20.90.49.200, 51.142.187.196, 20.254.168.148, 51.137.144.240, 20.90.50.115 |
| USA, øst | 40.117.113.165, 20.168.249.164, 172.173.135.148, 52.142.27.43, 20.237.22.163, 20.121.150.131, 20.237.18.20, 20.237.16.199, 20.237.16.198, 20.237.23.162, 20.124.59.116, 20.237.18.21, 20.124.59.146, 20.237.22.162 |
Hvis du vil ha mer informasjon, kan du se Nettverkskrav.
Appstyring nå tilgjengelig som en del av Defender for Cloud Apps lisens
Appstyring er nå inkludert som en del av Microsoft Defender for Cloud Apps lisenser og krever ikke lenger en tilleggslisens.
I Microsoft Defender-portalen går du til Status for appstyringstjeneste > for innstillinger > for skyapper > for enten å aktivere appstyring hvis tilgjengelig, eller registrere deg for ventelisten.
Eksisterende innehavere av prøvelisenser for appstyringstillegget har frem til 31. juli 2023 å aktivere veksleknappen og beholde appstyringstilgangen.
Hvis du vil ha mer informasjon, kan du se:
- Appstyring Defender for Cloud Apps i Microsoft Defender XDR
- Aktiver appstyring for Microsoft Defender for Cloud Apps.
OAuth-konvergens for appstyring
For kunder som har aktivert appstyring, har vi konsoliderte funksjoner for overvåking og policyhåndhevelse for alle OAuth-apper i appstyring.
I Microsoft Defender-portalen har vi slått sammen alle funksjonene opprinnelig under Skyapper > OAuth-apper under appstyring, der du kan administrere alle OAuth-apper under én enkelt glassrute.
Hvis du vil ha mer informasjon, kan du se Vis appene dine.
Forbedret jaktopplevelse for OAuth-appaktiviteter
Appstyring gjør det nå enkelt for deg å jakte med appdata til neste nivå ved å gi dypere innsikt i OAuth-appen, slik at du kan hjelpe SOC med å identifisere aktivitetene til en app og ressursene den har fått tilgang til.
OAuth app innsikt inkluderer:
- Forhåndsdefinerte spørringer som bidrar til å strømlinjeforme undersøkelsen
- Innsyn i dataene ved hjelp av resultatvisningen
- Muligheten til å inkludere OAuth-appdata, for eksempel ressurs-, app-, bruker- og appaktivitetsdetaljer i egendefinerte gjenkjenninger.
Hvis du vil ha mer informasjon, kan du se Jakten på trusler i appaktiviteter.
Oppdatering av apphygiene med Microsoft Entra
Fra og med 1. juni 2023 vil administrasjon av ubrukte apper, ubrukt legitimasjon og utløpende legitimasjon bare være tilgjengelig for appstyringskunder med Microsoft Entra Workload Identities Premium.
Hvis du vil ha mer informasjon, kan du se Sikre apper med funksjoner for apphygiene og hva er identiteter for arbeidsbelastninger?.
Mai 2023
Policyer for generering av virkemåte genererer ikke lenger varsler (forhåndsvisning). Fra og med 28. mai 2023 genererer ikke policyer som genererer virkemåter i Microsoft Defender XDR avansert jakt varsler. Policyene fortsetter å generere virkemåter uavhengig av aktivering eller deaktivert i leierkonfigurasjonen.
Hvis du vil ha mer informasjon, kan du se Undersøke virkemåter med avansert jakt (forhåndsvisning).
Programmer som ikke kan blokkeres (forhåndsversjon): Hvis du vil hindre brukere i å forårsake nedetid ved et uhell, hindrer Defender for Cloud Apps deg nå å blokkere forretningskritiske Microsoft-tjenester. Hvis du vil ha mer informasjon, kan du se Styre oppdagede apper.
April 2023
Defender for Cloud Apps utgivelse 251-252
søndag 30. april 2023
Den Microsoft Defender for Cloud Apps integreringen i Microsoft Defender XDR er generelt tilgjengelig (GA). Hvis du vil ha mer informasjon, kan du se Microsoft Defender for Cloud Apps i Microsoft Defender XDR.
Alternativet for automatisk omadressering er Generelt tilgjengelig (GA). Administratorer kan bruke dette alternativet til å omdirigere brukere fra den frittstående Defender for Cloud Apps-portalen til Microsoft Defender XDR.
Som standard er dette alternativet satt til Av. Administratorer må eksplisitt melde seg på ved å bytte veksleknappen til På for å bruke Microsoft Defender XDR opplevelse utelukkende.
Hvis du vil ha mer informasjon, kan du se Omadressere kontoer fra Microsoft Defender for Cloud Apps til Microsoft Defender XDR.
Oppdateringer for innstillingssider:
Funksjonene på følgende sider er fullstendig integrert i Microsoft Defender XDR, og har derfor ikke sin egen frittstående opplevelse i Microsoft Defender XDR:
- Innstillinger > Azure AD identitetsbeskyttelse
- Appstyring for innstillinger >
- Innstillinger > Microsoft Defender for identitet
Følgende sider er planlagt for nedgradering sammen med Microsoft Defender for Cloud Apps portalen:
- Innstillinger for > eksport av innstillinger
- Logg for webtrafikk for aktivitetslogg >
Defender for Cloud Apps utgivelse 250
24. april 2023 kl.
Zoom App-kobling for SSPM (offentlig forhåndsversjon)
Defender for Cloud-apper støtter nå en ny Zoom App-kobling for SSPM. Hvis du vil ha mer informasjon, kan du se Koble zoom til Microsoft Defender for Cloud Apps.
2. april 2023 kl.
- Ny «virkemåte»-datatype i Microsoft Defender XDR avansert jakt (forhåndsvisning)
For å forbedre trusselbeskyttelsen og redusere varslingstretthet har vi lagt til et nytt datalag kalt «atferd» i Microsoft Defender for Cloud Apps opplevelse i Microsoft Defender XDR avansert jakt. Denne funksjonen er ment å gi relevant informasjon for undersøkelser ved å identifisere avvik eller andre aktiviteter som kan være relatert til sikkerhetsscenarioer, men ikke nødvendigvis indikere ondsinnet aktivitet eller en sikkerhetshendelse. I denne første fasen vil noen av Microsoft Defender for avviksregistreringer for Cloud App også presenteres som virkemåter. I fremtidige faser vil disse gjenkjenningene bare generere virkemåter og ikke varsler. Hvis du vil ha mer informasjon, kan du se Undersøke virkemåter med avansert jakt (forhåndsvisning).
Mars 2023
Defender for Cloud Apps utgivelse 249
19. mars 2023 kl.
-
Automatisk omadressering fra Microsoft Defender for Cloud Apps til Microsoft Defender-portalen (forhåndsvisning)
Med en ny veksleknapp for automatisk omadressering kan du utløse automatisk omadressering fra Microsoft Defender for Cloud Apps til Microsoft Defender XDR. Når omadresseringsinnstillingen er aktivert, rutes brukere som har tilgang til Microsoft Defender for Cloud Apps-portalen automatisk til Microsoft Defender-portalen. Aktiver/deaktiver standardverdien er satt til Av, og administratorer må eksplisitt melde seg på automatisk omadressering og begynne å bruke Microsoft Defender XDR utelukkende. Du har fortsatt muligheten til å melde deg ut av Microsoft Defender XDR opplevelser og bruke Microsoft Defender for Cloud Apps frittstående portal. Dette kan gjøres ved å slå av veksleknappen. Hvis du vil ha mer informasjon, kan du se Omadressere kontoer fra Microsoft Defender for Cloud Apps til Microsoft Defender XDR.
Appstyring mars 2023-utgivelse
- Offentlig forhåndsvisning av apphygiene: Appstyring gir nå innsikt og policyfunksjonalitet for ubrukte apper, apper med ubrukt legitimasjon og apper med utløpende legitimasjon. Hver av disse funksjonene har en forhåndsdefinert policy utenfor boksen, og du kan også definere dine egne egendefinerte policyer. Du kan eksportere denne innsikten fra applisten for enkel rapportering og triage på tvers av organisasjonen.
Defender for Cloud Apps utgivelse 248
5. mars 2023 kl.
Raskere innlastingstid for beskyttede økter
Vi har gjort betydelige forbedringer i innlastingstiden for nettsider som er beskyttet av øktpolicyer. Sluttbrukere som er begrenset til øktpolicyer, enten fra en stasjonær eller mobil enhet, kan nå få en raskere og mer sømløs nettleseropplevelse. Vi har vært vitne til en forbedring på mellom 10 % og 40 %, avhengig av programmet, nettverket og kompleksiteten til nettsiden.Støtte for Tokyo ServiceNow-versjon
Defender for Cloud Apps-koblingen for ServiceNow støtter nå ServiceNow Tokyo-versjonen. Med denne oppdateringen kan du beskytte de nyeste versjonene av ServiceNow ved hjelp av Defender for Cloud Apps. Hvis du vil ha mer informasjon, kan du se Koble ServiceNow til Microsoft Defender for Cloud Apps.
Februar 2023
Appstyring februar 2023-utgivelse
- Forbedret opplevelse for varslingsundersøkelse: Appstyring gir nå ytterligere informasjon administratorer trenger for å undersøke og utbedre hendelser og varsler. Denne forbedringen inneholder flere detaljer under Hva som skjedde og Anbefalte handlinger i varselartikkelen på Microsoft Defender XDR varselsider. Denne informasjonen er tilgjengelig for alle varsler om appstyring, inkludert varsler utløst av regler for trusselregistrering, forhåndsdefinerte policyer og brukerdefinerte policyer. Mer informasjon om den forbedrede varslingsopplevelsen.
- App Governance app hygiene funksjoner offentlig forhåndsvisning: App Governance innsikt og kontroller på ubrukte apper, apper med ubrukt legitimasjon og apper med utløpende legitimasjon lansert til offentlig forhåndsvisning 15. februar 2023. Administratorer kan sortere, filtrere og eksportere på appens dato som sist ble brukt, legitimasjon ubrukt siden, og utløpsdato for legitimasjon. En forhåndsdefinert policy for ubrukte apper, apper med ubrukt legitimasjon og apper med utløpende legitimasjon kommer ut av boksen.
Defender for Cloud Apps utgivelse 246 og 247
19. februar 2023 kl.
SaaS Security Posture Management (SSPM) funksjoner oppdatere kunngjøringer (GA og offentlig forhåndsvisning)
Vi har gjort viktige forbedringer i styringen og beskyttelsen av tredjeparts programmer for programvare som tjeneste (SaaS). Disse forbedringene inkluderer vurderinger for å identifisere risikable sikkerhetskonfigurasjoner ved hjelp av Microsoft Defender for Cloud Apps, og jevnere integrering i Microsoft Secure Score-opplevelsen. Vi har nå lansert Salesforce og ServiceNow til generell tilgjengelighet, mens Okta, GitHub, Citrix ShareFile og DocuSign for øyeblikket er i offentlig forhåndsversjon. Hvis du vil ha mer informasjon, kan du se Koble til apper for å få synlighet og kontroll med Microsoft Defender for Cloud Apps.Handlinger for styring av policy for gjenkjenning av skadelig programvare er nå tilgjengelig (forhåndsversjon)
Automatiske handlinger for filer som oppdages av policyen for gjenkjenning av skadelig programvare, er nå tilgjengelige som en del av policykonfigurasjonen. Handlingene er forskjellige fra app til app. Hvis du vil ha mer informasjon, kan du se handlinger for styring av skadelig programvare (forhåndsvisning).Versjonsoppdatering for Log Collector
Vi har lansert en ny logginnsamlingsversjon med de nyeste sikkerhetsløsningene.
Ny versjon: columbus-0.246.0-signed.jar
Bildenavn: mcaspublic.azurecr.io/public/mcas/logcollector merke: latest/0.246.0 bilde-ID: eeb3c4f1a64cDocker-bildet ble gjenoppbygd med disse oppdateringene:
Avhengighetsnavn Fra versjon Til versjon Kommentarer amazon-corretto 8.222.10.1-linux-x64 8.352.08.1-linux-x64 openssl 1.1.1 1.1.1q 1.1.1s 1.1.1-serien er tilgjengelig og støttes frem til 11. september 2023. Rent ftpd 1.0.49 1.0.50 fasterxml.jackson.core.version 2.13.3 2.14.1 2.14 ble utgitt i november 2022 org.jacoco 0.7.9 0.8.8 Versjon 0.8.8 fra 05. apr. 2022 Hvis du vil begynne å bruke den nye versjonen, må du stoppe loggsamlerne, fjerne det gjeldende bildet og installere det nye.
Hvis du vil bekrefte at den nye versjonen kjører, kjører du følgende kommando i Docker-beholderen:
cat /var/adallom/versions | grep columbus-
Januar 2023
Defender for Cloud Apps utgivelse 244 og 245
22. januar 2023 kl.
-
Filpolicy – utforsking av flere SITer
Defender for Cloud Apps inneholder allerede muligheten til å utforske samsvar mellom policyfiler som inneholder sensitive informasjonstyper (SIT-er). Nå kan Defender for Cloud Apps også skille mellom flere SITer i samme filsamsvar. Denne funksjonen, kjent som korte bevis, lar Defender for Cloud Apps bedre administrere og beskytte organisasjonens sensitive data. Hvis du vil ha mer informasjon, kan du se Undersøke bevis (forhåndsvisning).
Oppdateringer laget i 2022
Obs!
Fra og med 28. august 2022 kan ikke brukere som ble tilordnet en Azure AD Security Reader-rolle, administrere Microsoft Defender for Cloud Apps varsler. Hvis du vil fortsette å behandle varsler, bør brukerens rolle oppdateres til en Azure AD sikkerhetsoperator.
Defender for Cloud Apps utgivelse 240, 241, 242 og 243
25. desember 2022
-
Azure AD identitetsbeskyttelse
Azure AD varsler om identitetsbeskyttelse kommer direkte til Microsoft Defender XDR. Policyene for Microsoft Defender for Cloud Apps påvirker ikke varslene i Microsoft Defender-portalen. Azure AD policyer for identitetsbeskyttelse fjernes gradvis fra listen over policyer for skyapper i Microsoft Defender Portal. Hvis du vil konfigurere varsler fra disse policyene, kan du se Konfigurer Azure AD IP-varslingstjeneste.
Defender for Cloud Apps utgivelse 237, 238 og 239
30. oktober 2022 kl.
Opprinnelig integrering av Microsoft Defender for Cloud Apps i Microsoft Defender XDR er nå i offentlig forhåndsversjon
Hele Defender for Cloud Apps i Microsoft Defender XDR er nå tilgjengelig for offentlig forhåndsversjon.SecOps og sikkerhetsadministratorer opplever disse store fordelene:
- Tid og kostnader som er lagret
- Helhetlig undersøkelsesopplevelse
- Ekstra data og signaler i avansert jakt
- Integrert beskyttelse på tvers av alle sikkerhetsarbeidsbelastninger
Hvis du vil ha mer informasjon, kan du se Microsoft Defender for Cloud Apps i Microsoft Defender XDR.
Appstyring oktober 2022-utgivelse
- Lagt til innsikt og utbedring for sensitivt innhold: Appstyring gir innsikt og automatiserte utbedringsfunksjoner gjennom forhåndsdefinerte og egendefinerte policyer for apper som får tilgang til innhold med Microsoft Purview informasjonsbeskyttelse etiketter. Bedriftsadministratorer har nå innsyn i arbeidsbelastningene som disse appene får tilgang til, og om de får tilgang til sensitive data i disse arbeidsbelastningene. Med forhåndsdefinerte og egendefinerte policyer varsles administratorer om apper som har forsøkt å få tilgang til sensitive data. I tillegg kan appstyring automatisk deaktivere ikke-kompatielle apper.
- Utvidet dekning for å inkludere alle API-apper som ikke er Graph- – Appstyring har utvidet dekningen for å sikre flere apper i leieren. I tillegg til OAuth-apper som bruker Microsoft Graph API, gir appstyring nå synlighet og beskyttelse for alle OAuth-apper som er registrert på Microsoft Entra ID. Mer informasjon om dekning av appstyring.
Defender for Cloud Apps utgivelse 236
18. september 2022 kl.
-
Egnyte API-kobling er generelt tilgjengelig
Egnyte API-koblingen er generelt tilgjengelig, noe som gir deg dypere synlighet og kontroll over organisasjonens bruk av Egnyte-appen. Hvis du vil ha mer informasjon, kan du se Hvordan Defender for Cloud Apps bidrar til å beskytte Egnyte-miljøet ditt.
Defender for Cloud Apps utgivelse 235
4. september 2022 kl.
Versjonsoppdatering for Log Collector
Vi har lansert en ny logginnsamlingsversjon med de nyeste sikkerhetsløsningene.Ny versjon: columbus-0.235.0-signed.jar
Hovedendringer:
- Docker-bilde ble gjenoppbygd med de nyeste oppdateringene
- Openssl-biblioteket ble oppdatert fra 1.1.1l til 1.1.1q
- fasterxml.jackson.core.version ble oppdatert fra 2.13.1 til 2.13.3
Hvis du vil oppdatere versjonen, stopper du loggsamlerne, fjerner det gjeldende bildet og installerer et nytt.
Kjør denne kommandoen i Docker-beholderen for å bekrefte versjonen:cat var/adallom/versions | grep columbus-
Hvis du vil ha mer informasjon, kan du se Konfigurere automatisk loggopplasting for kontinuerlige rapporter.Pålastingsprogram til øktkontroller (forhåndsvisning)
Prosessen med pålasting av et program som skal brukes til øktkontroller, er forbedret og bør øke suksessraten for pålastingsprosessen. Slik angir du et program:- Gå til appkontrolllisten for betinget tilgang i Innstillinger –>appkontroll for betinget tilgang.
- Når du har valgt Onboard med øktkontroll, får du se et Rediger dette appskjemaet .
- Hvis du vil ta programmet med i øktkontroller, må du velge alternativet Bruk appen med øktkontroller .
Hvis du vil ha mer informasjon, kan du se Distribuer appkontroll for betinget tilgang for katalogapper med Azure AD.
Defender for Cloud Apps utgivelse 234
21. august 2022 kl.
Funksjonsparitet mellom kommersielle og offentlige tilbud
Vi har konsolidert flyten som gjør at Microsoft Defender for Cloud Apps data kan brukes gjennom Microsoft Defender XDR. Hvis du vil bruke disse dataene i Microsoft Defender for skyen, bør Microsoft Defender XDR brukes. Hvis du vil ha mer informasjon, kan du se Microsoft Defender XDR leverer enhetlig XDR-opplevelse til GCC-, GCC High- og DoD-kunder og Koble Microsoft Defender XDR data til Microsoft Sentinel.Beskytte apper som bruker ikke-standard porter med øktkontroller
Denne funksjonen gjør det mulig for Microsoft Defender for Cloud Apps å håndheve øktpolicyer for programmer som bruker andre portnumre enn 443. Splunk og andre programmer som bruker andre porter enn 443, vil nå være kvalifisert for øktkontroll.
Det er ingen konfigurasjonskrav for denne funksjonen. Funksjonen er for øyeblikket i forhåndsvisningsmodus. Hvis du vil ha mer informasjon, kan du se Beskytt apper med Microsoft Defender for Cloud Apps appkontroll for betinget tilgang.
Defender for Cloud Apps utgivelse 232 og 233
7. august 2022 kl.
-
MITRE-teknikker
De Defender for Cloud Apps avviksdeteksjonene for trusselbeskyttelse vil nå inkludere MITRE-teknikker og subtekniques der det er relevant, i tillegg til MITRE-taktikken som allerede eksisterer. Disse dataene vil også være tilgjengelige i sideruten for varselet i Microsoft Defender XDR. Hvis du vil ha mer informasjon, kan du se Slik undersøker du varsler om avviksregistrering.
Viktig
Nedgradering av gamle proxy-suffiksdomener for øktkontroller (gradvis utrulling)
Fra 15. september 2022 vil Defender for Cloud Apps ikke lenger støtte suffiksdomener i skjemaet<appName>.<region>.cas.ms.
I november 2020 flyttet vi til suffiksdomener i form av <appName>.mcas.ms, men ga fortsatt nådetid til å bytte fra de gamle suffiksene.
Sluttbrukere har svært liten sjanse til å støte på navigasjonsproblemer på et slikt domene. Det kan imidlertid være situasjoner der de kan ha problemer – for eksempel hvis bokmerker lagres i det gamle domeneskjemaet eller en gammel kobling lagres et sted.
Hvis brukere støter på følgende melding:
Tilkoblingen for dette området er ikke sikker.
missing.cert.microsoft.sharepoint.com.us.cas.ms sendte et ugyldig svar
De bør manuelt erstatte URL-delen .<region>.cas.ms med .mcas.us.
Appstyring juli 2022-utgivelse
- Lagt til flere forhåndsdefinerte policyer: Appstyring lanserte fem flere av bokspolicyene for å oppdage uregelmessige appvirkemåter. Disse policyene aktiveres som standard, men du kan deaktivere dem hvis du velger det. Mer informasjon her
- Nytt videobibliotek: Appstyring opprettet et nytt bibliotek med korte videoer om funksjoner i appstyring, hvordan du bruker dem og informasjon om hvordan du finner ut mer. Ta en titt her
- Integrering av sikker poengsum for GA: Integrering av Microsoft Secure Score med app governance (AppG)-tillegget til Microsoft Defender for Cloud Apps (MDA) har nådd generell tilgjengelighet. AppG-kunder mottar nå anbefalinger i Secure Score, som hjelper dem med å sikre Microsoft 365 OAuth-appene sine. Hvorfor er denne integreringen viktig? Secure Score er en representasjon av en organisasjons sikkerhetsstilling og et inngangspunkt til ulike muligheter til å forbedre den holdningen. Ved å følge anbefalinger for sikker poengsum forbedrer kundene robustheten mot kjente og fremvoksende trusler. AppG er en funksjon for sikkerhets- og policybehandling som er utformet for OAuth-aktiverte apper som har tilgang til Microsoft 365-data. Med dyp integrasjon i arbeidsbelastninger og trusselgjenkjenningsfunksjoner er AppG godt egnet til å redusere store angrepsoverflater i enterprise-appøkosystemer betydelig. Ved å følge AppG-relaterte anbefalinger og aktivere foreslåtte policyinnstillinger, kan virksomheter beskytte både apper og data mot misbruk og faktisk dårlig aktøraktivitet.
Defender for Cloud Apps utgivelse 231
10. juli 2022 kl.
-
Hash-koder for skadelig programvare tilgjengelig for SharePoint og OneDrive (forhåndsvisning)
I tillegg til fil-hash-koder som er tilgjengelige for skadelig programvare som er oppdaget i ikke-Microsoft-lagringsapper, gir nå nye varsler om gjenkjenning av skadelig programvare hash-koder for skadelig programvare som er oppdaget i SharePoint og OneDrive. Hvis du vil ha mer informasjon, kan du se gjenkjenning av skadelig programvare.
Defender for Cloud Apps utgivelse 230
26. juni 2022 kl.
-
SaaS Security Posture Management-funksjoner for Salesforce og ServiceNow
Vurderinger av sikkerhetsstillinger er tilgjengelige for Salesforce og ServiceNow. Hvis du vil ha mer informasjon, kan du se Sikkerhetsstillingsadministrasjon for SaaS-apper.
Defender for Cloud Apps utgivelse 227, 228 og 229
tirsdag 14. juni 2022
Admin revisjonsforbedringer
Ekstra Defender for Cloud Apps administratoraktiviteter er lagt til:- Status for filovervåking – slå av/på
- Opprette og slette policyer
- Redigering av policyer er beriket med mer data
- Admin administrasjon: legge til og slette administratorer
For hver av aktivitetene som er oppført ovenfor, finner du detaljene i aktivitetsloggen. Hvis du vil ha mer informasjon, kan du se Admin aktivitetsovervåking.
DocuSign API Connector er generelt tilgjengelig
DocuSign API-koblingen er generelt tilgjengelig, noe som gir deg dypere synlighet og kontroll over organisasjonens bruk av DocuSign-appen. Hvis du vil ha mer informasjon, kan du se Hvordan Defender for Cloud Apps bidrar til å beskytte DocuSign-miljøet.
Appstyring mai 2022-utgivelse
- Forhåndsdefinerte policyer GA: Appstyring lanserte et sett med standardpolicyer for å oppdage uregelmessige appvirkemåter. Disse policyene aktiveres som standard, men du kan deaktivere dem hvis du velger det. Mer informasjon her
- Teams arbeidsbelastning GA: Appstyring la til innsikt, policyfunksjoner og styring for Teams-arbeidsbelastningen. Du kan se databruk, bruk av tillatelser og opprette policyer for Teams-tillatelser og -bruk.
- Varsler om appstyring samlet i M365D-varsler og hendelseskøer: Køen for appstyring varsler er forenet med Microsoft Defender XDR varsler og aggregeres i hendelser.
Defender for Cloud Apps utgivelse 226
1. mai 2022 kl.
-
Forbedringer i gjenkjenning av skadelig programvare for ikke-Microsoft-lagringsapper
Defender for Cloud Apps har innført store forbedringer i gjenkjenningsmekanismen for ikke-Microsoft-lagringsapper. Dette reduserer antallet falske positive varsler.
Defender for Cloud Apps utgivelse 225
24. april 2022 kl.
-
Støtte for Roma- og San Diego ServiceNow-versjoner
Defender for Cloud Apps-koblingen for ServiceNow støtter nå Roma- og San Diego-versjoner av ServiceNow. Med denne oppdateringen kan du beskytte de nyeste versjonene av ServiceNow ved hjelp av Defender for Cloud Apps. Hvis du vil ha mer informasjon, kan du se Koble ServiceNow til Microsoft Defender for Cloud Apps.
Defender for Cloud Apps utgivelse 222, 223 og 224
3. april 2022 kl.
-
Oppdaterte alvorsgradnivåer for avviksregistreringer for Defender for Cloud Apps
Alvorsgradnivåene for Defender for Cloud Apps innebygde varsler for avviksregistrering endres for bedre å gjenspeile risikonivået i tilfelle sanne positive varsler. De nye alvorsgradnivåene vises på policysiden: https://portal.cloudappsecurity.com/#/policy
Defender for Cloud Apps utgivelse 221
20. februar 2022 kl.
-
Egnyte App Connector tilgjengelig i offentlig forhåndsversjon
En ny appkobling for Egnyte er tilgjengelig i offentlig forhåndsversjon. Nå kan du koble Microsoft Defender for Cloud Apps til Atlassian for å overvåke og beskytte brukere og aktiviteter. Hvis du vil ha mer informasjon, kan du se Koble Egnyte til Microsoft Defender for Cloud Apps (forhåndsvisning).
Defender for Cloud Apps utgivelse 220
6. februar 2022 kl.
-
Ny loggsamler for skyoppdagelse
Cloud Discovery-loggsamleren er oppdatert til Ubuntu 20.04. Hvis du vil installere den, kan du se Konfigurere automatisk loggopplasting for kontinuerlige rapporter.
Defender for Cloud Apps utgivelse 218 og 219
23. januar 2022 kl.
-
Atlassian app connector tilgjengelig i offentlig forhåndsversjon
En ny app-kobling for Atlassian er tilgjengelig i offentlig forhåndsversjon. Nå kan du koble Microsoft Defender for Cloud Apps til Atlassian for å overvåke og beskytte brukere og aktiviteter. For mer informasjon, se Connect Atlassian å Microsoft Defender for Cloud Apps (forhåndsvisning).
Oppdateringer laget i 2021
Defender for Cloud Apps utgivelse 216 og 217
26. desember 2021
Ikke-Microsoft-aktiviteter i avansert jakt
Apper som ikke er fra Microsoft, er nå inkludert i Tabellen CloudAppEvent i Microsoft Defender XDR avansert jakt. Hvis du vil ha mer informasjon, kan du se blogginnlegget Microsoft Defender XDR Tech Community.NetDocuments API-kobling er nå i generell tilgjengelighet
NetDocuments API-koblingen er i generell tilgjengelighet, noe som gir deg mer innsyn i og kontroll over hvordan NetDocument-appen brukes i organisasjonen. Hvis du vil ha mer informasjon, kan du se Hvordan Cloud App Security bidrar til å beskytte NetDocuments
Defender for Cloud Apps utgivelse 214 og 215
28. november 2021 kl.
-
NetDocuments-appkobling tilgjengelig i offentlig forhåndsversjon
En ny appkobling for NetDocuments er tilgjengelig i offentlig forhåndsversjon. Nå kan du koble Microsoft Defender for Cloud Apps til NetDocuments for å overvåke og beskytte brukere og aktiviteter. Hvis du vil ha mer informasjon, kan du se Koble NetDocuments til Microsoft Defender for Cloud Apps.
Cloud App Security utgivelse 212 og 213
31. oktober 2021 kl.
Umulig reise, aktivitet fra sjeldne land/områder, aktivitet fra anonyme IP-adresser og aktivitet fra mistenkelige IP-adressevarsler vil ikke gjelde for mislykkede pålogginger.
Etter en grundig sikkerhetsgjennomgang bestemte vi oss for å skille mislykket påloggingshåndtering fra varslene nevnt ovenfor. Fra nå av utløses de bare av vellykkede påloggingstilfeller og ikke av mislykkede pålogginger eller angrepsforsøk. Påloggingsvarsel for masse mislyktes vil fremdeles bli brukt hvis det finnes uregelmessige, store påloggingsforsøk på en bruker. Hvis du vil ha mer informasjon, kan du se Atferdsanalyse og avviksregistrering.Ny avviksregistrering: Uvanlig Internett-adresse for en OAuth-app
Vi har utvidet avviksregistreringene våre til å inkludere mistenkelig tillegg av privilegert legitimasjon i en OAuth-app. Den nye gjenkjenningen er nå tilgjengelig utenfor boksen og aktiveres automatisk. Gjenkjenningen kan indikere at en angriper har kompromittert appen og bruker den til skadelig aktivitet. Hvis du vil ha mer informasjon, kan du se Uvanlig Internett-adresse for en OAuth-app.Ny gjenkjenning: Aktivitet fra passordspray-tilknyttede IP-adresser
Denne gjenkjenningen sammenligner IP-adresser som utfører vellykkede aktiviteter i skyprogrammene, med IP-adresser identifisert av Microsofts trusselintelligenskilder som nylig utførte angrep med passordspray. Den varsler om brukere som var ofre for passordspraykampanjer og klarte å få tilgang til skyprogrammene dine fra de ondsinnede IP-ene. Dette nye varselet genereres av eksisterende aktivitet fra policyen for mistenkelige IP-adresser . Hvis du vil ha mer informasjon, kan du se Aktivitet fra mistenkelige IP-adresser.Smartsheet- og OneLogin API-koblinger er nå generelt tilgjengelige
Smartsheet- og OneLogin API-koblinger er nå generelt tilgjengelige. Nå kan du koble Microsoft Cloud App Security til Smartsheet og OneLogin for å overvåke og beskytte brukere og aktiviteter. Hvis du vil ha mer informasjon, kan du se Koble til Smartsheet og Koble til OneLogin.Ny Shadow IT-integrasjon med åpne systemer
Vi har lagt til opprinnelig integrering med Åpne systemer som gir deg skygge-IT-synlighet i appbruk og kontroll over apptilgang. Hvis du vil ha mer informasjon, kan du se Integrere Cloud App Security med åpne systemer.
Cloud App Security utgivelse 209, 210 og 211
10. oktober 2021 kl.
Slack API-kobling er nå generelt tilgjengelig
Slack API-kobling er generelt tilgjengelig, noe som gir deg mer synlighet i og kontroll over hvordan appen brukes i organisasjonen. Hvis du vil ha mer informasjon, kan du se Hvordan Cloud App Security bidrar til å beskytte Slack Enterprise.Ny advarselsopplevelse for overvåkede apper med Microsoft Defender for endepunkt er nå generelt tilgjengelig
Cloud App Security har utvidet sin opprinnelige integrasjon med Microsoft Defender for endepunkt. Du kan nå bruke myk blokk på tilgang til apper merket som overvåket ved hjelp av Microsoft Defender for endepunkt sin nettverksbeskyttelsesfunksjonalitet. Sluttbrukere kan hoppe over blokken. Blokkomkoblingsrapporten er tilgjengelig i Cloud App Security oppdagede appopplevelsen. Hvis du vil ha mer informasjon, kan du se:Ny oppdaget appopplevelse i generell tilgjengelighet
Som en del av kontinuerlig forbedring av enhetsopplevelsene introduserer vi en modernisert oppdaget appopplevelse for å dekke oppdagede nettapper og OAuth-apper og gi en enhetlig visning av en programenhet. Hvis du vil ha mer informasjon, kan du se Arbeide med appsiden.
Cloud App Security utgivelse 208
22. august 2021 kl.
Ny oppdaget appopplevelse i offentlig forhåndsversjon
Som en del av kontinuerlig forbedring av enhetsopplevelsene introduserer vi en modernisert oppdaget appopplevelse for å dekke oppdagede nettapper og OAuth-apper og gi en enhetlig visning av en programenhet. Hvis du vil ha mer informasjon, kan du se Arbeide med appsiden.Tilleggsprogram for appstyring for Cloud App Security tilgjengelig i offentlig forhåndsversjon
Appstyringstillegget for Microsoft Cloud App Security er en funksjon for sikkerhets- og policyadministrasjon som er utformet for OAuth-aktiverte apper som har tilgang til Microsoft 365-data via Microsoft Graph-API-er. Appstyring gir full synlighet, utbedring og styring av hvordan disse appene får tilgang til, bruker og deler sensitive data som er lagret i Microsoft 365, gjennom handlingsrettet innsikt og automatiserte policyvarsler og -handlinger. Hvis du vil ha mer informasjon:Smartsheet-appkobling tilgjengelig i offentlig forhåndsversjon
En ny appkobling for Smartsheet er tilgjengelig i offentlig forhåndsversjon. Nå kan du koble Microsoft Cloud App Security til Smartsheet for å overvåke og beskytte brukere og aktiviteter. Hvis du vil ha mer informasjon, kan du se Koble Smartsheet til Microsoft Cloud App Security.
Cloud App Security utgivelse 207
8. august 2021 kl.
-
Ny advarselsopplevelse for overvåkede apper med Microsoft Defender for endepunkt (offentlig forhåndsversjon)
Cloud App Security har utvidet sin opprinnelige integrasjon med Microsoft Defender for endepunkt (MDE). Du kan nå bruke myk blokk på tilgang til apper merket som overvåket ved hjelp av Microsoft Defender for endepunkt sin nettverksbeskyttelsesfunksjonalitet. Sluttbrukere kan hoppe over blokken. Blokkomkoblingsrapporten er tilgjengelig i Cloud App Security oppdagede appopplevelsen. Hvis du vil ha mer informasjon, kan du se:
Cloud App Security utgivelse 206
25. juli 2021 kl.
-
Ny logganalyse for Åpne systemer i Cloud Discovery
Cloud App Security's Cloud Discovery analyserer et bredt spekter av trafikklogger for å rangere og score apper. Nå inkluderer Cloud Discovery en innebygd logganalyse for å støtte Open Systems-formatet. Hvis du vil ha en liste over støttede logganalyser, kan du se Støttede brannmurer og proxyer.
Cloud App Security utgivelse 205
11. juli 2021 kl.
Zendesk-appkobling tilgjengelig i offentlig forhåndsversjon
En ny appkobling for Zendesk er tilgjengelig i offentlig forhåndsversjon. Nå kan du koble Microsoft Cloud App Security til Zendesk for å overvåke og beskytte brukere og aktiviteter. Hvis du vil ha mer informasjon, kan du se Connect Zendesk.Ny Cloud Discovery-analyse for Wandera
Cloud Discovery i Cloud App Security analyserer et bredt spekter av trafikklogger for å rangere og score apper. Nå inkluderer Cloud Discovery en innebygd logganalyse for å støtte Wandera-formatet. Hvis du vil ha en liste over støttede logganalyser, kan du se Støttede brannmurer og proxyer.
Cloud App Security utgivelse 204
27. juni 2021 kl.
-
Slack- og OneLogin-appkoblinger som er tilgjengelige i offentlig forhåndsversjon
Nye appkoblinger er nå tilgjengelige for Slack og OneLogin i offentlig forhåndsversjon. Nå kan du koble Microsoft Cloud App Security til Slack og OneLogin for å overvåke og beskytte brukere og aktiviteter. Hvis du vil ha mer informasjon, kan du se Koble til Slack og Koble til OneLogin.
Cloud App Security utgivelse 203
13. juni 2021 kl.
Vis bekreftet utgiver som angir i O365 OAuth-apper
Cloud App Security dukker nå opp om en utgiver av en Microsoft 365 OAuth-app er bekreftet av Microsoft for å aktivere høyere appklarering. Denne funksjonen er i en gradvis utrulling. Hvis du vil ha mer informasjon, kan du se Arbeide med OAuth-appsiden.Azure Active Directory Cloud App Security-administrator
En Cloud App Security administratorrolle er lagt til i Azure Active Directory (Azure AD), slik at tilordningen av globale administratorfunksjoner kan Cloud App Security alene via Azure AD. Hvis du vil ha mer informasjon, kan du se Microsoft 365 og Azure AD roller med tilgang til Cloud App Security.Viktig
Microsoft anbefaler at du bruker roller med færrest tillatelser. Dette bidrar til å forbedre sikkerheten for organisasjonen. Global administrator er en svært privilegert rolle som bør begrenses til nødscenarioer når du ikke kan bruke en eksisterende rolle.
Eksporter egendefinert kode og appdomener per oppdaget app
Eksporter til CSV på siden for oppdagede apper inkluderer nå programmets egendefinerte appkoder og tilknyttede nettdomener. Hvis du vil ha mer informasjon, kan du se Arbeide med oppdagede apper.Viktig
Forbedret URL-adresse for proxy for tilgangskontroller (gradvis utrulling)
Fra begynnelsen av juli 2021 vil vi endre tilgangsendepunktet fra<mcas-dc-id>.access-control.cas.mstilaccess.mcas.ms. Sørg for at du oppdaterer reglene for nettverksapparater før slutten av juni, da dette kan føre til tilgangsproblemer. Hvis du vil ha mer informasjon, kan du se Access- og øktkontroller
Cloud App Security utgivelse 200, 201 og 202
30. mai 2021 kl.
-
Godkjenningskontekst (step-up-godkjenning) i offentlig forhåndsversjon
Vi har lagt til muligheten til å beskytte brukere som arbeider med rettighetsbeskyttede og privilegerte ressurser, ved å kreve Azure AD policyer for betinget tilgang som skal revurderes i økten. Hvis det for eksempel oppdages en endring i IP-adressen fordi en ansatt i en svært følsom økt har flyttet fra kontoret til kaffebaren nede, kan du konfigurere trinn opp til å godkjenne brukeren på nytt. Hvis du vil ha mer informasjon, kan du se Krev trinnvis godkjenning (godkjenningskontekst) ved risikable handlinger.
Cloud App Security utgivelse 199
18. april 2021 kl.
Tilgjengelighet for instrumentbord for tjenestetilstand
Det forbedrede Cloud App Security servicetilstandsinstrumentbordet er nå tilgjengelig i Microsoft 365 administrasjon-portalen for brukere med overvåkede tjenestetilstandstillatelser. Mer informasjon om Microsoft 365 administrasjon roller. I instrumentbordet kan du konfigurere varsler, slik at relevante brukere kan holde seg oppdatert med gjeldende Cloud App Security status. Hvis du vil lære hvordan du konfigurerer e-postvarsler og tilleggsinformasjon om instrumentbordet, kan du se Slik kontrollerer du tjenestetilstanden for Microsoft 365.AIP-støtte avskrevet
Etikettbehandling fra Azure Information Protection-portalen (klassisk) avvikles fra og med 1. april 2021. Kunder uten utvidet AIP-støtte bør overføre etikettene sine til Microsoft Purview informasjonsbeskyttelse for å fortsette å bruke følsomhetsetiketter i Cloud App Security. Uten overføring til Microsoft Purview informasjonsbeskyttelse eller utvidet AIP-støtte, deaktiveres filpolicyer med følsomhetsetiketter. Hvis du vil ha mer informasjon, kan du se Forstå overføring av enhetlig merking.DLP nær sanntidslansering fullført for Dropbox, ServiceNow, AWS og Salesforce
Ny filskanning i nær sanntid er tilgjengelig i Dropbox, ServiceNow og Salesforce. Ny S3-samlingsoppdagelse i nær sanntid er tilgjengelig i AWS. Hvis du vil ha mer informasjon, kan du se Koble til apper.Offentlig forhåndsversjon for overordnede følsomhetsetiketter for rettigheter
Cloud App Security støtter overstyrende følsomhetsetiketter for filer som ble merket utenfor Cloud App Security. Hvis du vil ha mer informasjon, kan du se Hvordan integrere Microsoft Purview med Defender for Cloud Apps.Utvidede avansert jakthendelser
Vi har utvidet de tilgjengelige hendelsene i Cloud App Security. Microsoft Defender XDR Advanced Hunting omfatter nå telemetri fra Microsoft OneDrive, SharePoint Online, Microsoft 365, Dynamics 365, Dropbox, Power BI, Yammer, Skype for Business og Power Automate, i tillegg til Exchange Online og Teams, som var tilgjengelige til nå. Hvis du vil ha mer informasjon, kan du se Apper og tjenester som dekkes.
Cloud App Security utgivelse 198
Utgitt 4. april 2021
Utelukkelse av Azure Active Directory-grupper enheter fra oppdaging
Vi har lagt til muligheten til å utelate oppdagede enheter basert på importerte Azure Active Directory-grupper. Hvis du utelater Azure AD grupper, skjules alle oppdagelsesrelaterte data for alle brukere i disse gruppene. Hvis du vil ha mer informasjon, kan du se Utelat enheter.Støtte for API-kobling for ServiceNow Orlando- og Paris-versjoner
Vi har lagt til støtte for ServiceNow API-koblingen til Orlando- og Paris-versjonene. Hvis du vil ha mer informasjon, kan du se Koble ServiceNow til Microsoft Cloud App Security.Bruk alltid den valgte handlingen selv om data ikke kan skannes
Vi har lagt til en ny avmerkingsboks i øktpolicyer som behandler data som ikke kan skannes som et samsvar for policyen.Obs!
Avskrivingsvarsel: Denne funksjonen erstatter både Behandle kryptert som samsvar, og Behandle filer som ikke kan skannes som samsvar, i tillegg til å legge til ny funksjonalitet. Nye policyer vil inneholde den nye avmerkingsboksen som standard, deaktivert som standard. Eksisterende policyer overføres til den nye avmerkingsboksen 30. mai. Policyer med ett eller begge alternativene valgt, har det nye alternativet valgt som standard. alle andre policyer vil fjerne merkingen.
Cloud App Security utgivelse 197
Utgitt 21. mars 2021
Varsel om avskriving av statusside
29. april avskriver Cloud App Security statussiden for tjenestetilstanden, og erstatter den med instrumentbordet for tjenestetilstand i Microsoft 365 administrasjon-portalen. Endringen justerer Cloud App Security med andre Microsoft-tjenester og gir en forbedret tjenesteoversikt.Obs!
Bare brukere med tillatelser for å overvåke tjenestetilstand kan få tilgang til instrumentbordet. Hvis du vil ha mer informasjon, kan du se Om administratorroller.
I instrumentbordet kan du konfigurere varsler, slik at relevante brukere kan holde seg oppdatert med gjeldende Cloud App Security status. Hvis du vil lære hvordan du konfigurerer e-postvarsler og tilleggsinformasjon om instrumentbord, kan du se Slik kontrollerer du tjenestetilstanden for Microsoft 365.
Kobling for OAuth-appsamtykke
Vi har lagt til muligheten til å undersøke omfangsaktivitet i spesifikke OAuth-appens samtykkeaktiviteter direkte fra OAuth-appvisningen. Hvis du vil ha mer informasjon, kan du se Slik undersøker du mistenkelige OAuth-apper.
Cloud App Security utgivelse 195 og 196
Utgitt 7. mars 2021
Forbedret SKYGGE-IT-oppdagelse med Microsoft Defender for endepunkt
Vi har forbedret Defender for Endpoint-integrering ytterligere ved hjelp av forbedrede signaler for Defender-agenten, noe som gir mer nøyaktig appoppdagelse og organisatorisk brukerkontekst.Hvis du vil dra nytte av de nyeste forbedringene, må du sørge for at organisasjonens endepunkter oppdateres med de nyeste Windows 10 oppdateringene:
- KB4601383: Windows 10, versjon 1809
- KB4601380: Windows 10, versjon 1909
- KB4601382: Windows 10, versjon 20H2, versjon 21H1 Insider
Konfigurerbar øktlevetid
Vi gjør det mulig for kunder å konfigurere en kortere øktlevetid for appkontroll for betinget tilgang. Som standard har økter som er utsatt for Cloud App Security en maksimal levetid på 14 dager. Hvis du vil ha mer informasjon om å forkorte øktlevetid, kontakter du oss på mcaspreview@microsoft.com.
Cloud App Security utgivelse 192, 193 og 194
Utgitt 7. februar 2021
Oppdateringer til Policyer-siden
Vi har oppdatert Policyer-siden og lagt til en fane for hver policykategori. Vi har også lagt til en Alle policyer-fane for å gi deg en fullstendig liste over alle policyene dine. Hvis du vil ha mer informasjon om policykategoriseringen, kan du se Policytyper.Forbedret eksport av Microsoft 365 OAuth-apper
Vi har forbedret aktiviteter for Microsoft 365 OAuth-apper som eksporteres til CSV-filen med nettadressen for omadressering av OAuth-appene. Hvis du vil ha mer informasjon om eksport av OAuth-appaktiviteter, kan du se OAuth-appovervåking.Oppdateringer til portalgrensesnittet
I de kommende månedene oppdaterer Cloud App Security brukergrensesnittet for å gi en mer konsekvent opplevelse på tvers av Microsoft 365-sikkerhetsportaler. Finn ut mer
Cloud App Security utgivelse 189, 190 og 191
Utgitt 10. januar 2021
Ny logginnsamlingsversjon
Oppgradert Log collector for Shadow IT-oppdagelse er nå tilgjengelig. Den inneholder følgende oppdateringer:- Vi har oppgradert vår Pure-FTPd versjon til den nyeste versjonen: 1.0.49. TLS < 1.2 er nå deaktivert som standard.
- Vi har deaktivert innrammingsfunksjonen «oktett talt» i RSyslog for å hindre mislykket behandling.
Hvis du vil ha mer informasjon, kan du se Konfigurere automatisk loggopplasting for kontinuerlige rapporter.
Ny avviksregistrering: Mistenkelig tillegg av legitimasjon til en OAuth-app
Vi har utvidet avviksregistreringene våre til å inkludere mistenkelig tillegg av privilegert legitimasjon i en OAuth-app. Den nye gjenkjenningen er nå tilgjengelig utenfor boksen og aktiveres automatisk. Gjenkjenningen kan indikere at en angriper har kompromittert appen og bruker den til skadelig aktivitet. Hvis du vil ha mer informasjon, kan du se Uvanlig tillegg av legitimasjon i en OAuth-app.Forbedret overvåking for Skygge-IT-oppdagelsesaktiviteter
Vi har oppdatert overvåkingen for Shadow IT-aktiviteter for å inkludere handlinger utført av administratorer. Følgende nye aktiviteter er nå tilgjengelige i aktivitetsloggen og kan brukes som en del av Cloud App Security undersøkelsesopplevelsen.- Merke eller oppheve merking av apper
- Opprette, oppdatere eller slette loggsamlere
- Opprette, oppdatere eller slette datakilder
Nye REST-API-endepunkter for databerikelse
Vi har lagt til følgende API-endepunkter for databerikelse , slik at du kan administrere IP-adresseområder fullstendig ved hjelp av API-en. Bruk vårt eksempel på administrasjonsskript for å hjelpe deg med å komme i gang. Hvis du vil ha mer informasjon om områder, kan du se Arbeide med IP-områder og -koder.
Oppdateringer laget i 2020
Obs!
Produktnavnene for trusselbeskyttelse fra Microsoft endres. Les mer om dette og andre oppdateringer her. Vi kommer til å bruke de nye navnene i fremtidige versjoner.
Cloud App Security utgivelse 187 og 188
Utgitt 22. november 2020
Ny Shadow IT-integrering med Menlo Security
Vi har lagt til opprinnelig integrering med Menlo Security som gir deg skygge-IT-synlighet i appbruk og kontroll over apptilgang. Hvis du vil ha mer informasjon, kan du se Integrere Cloud App Security med Menlo Security.Ny Cloud Discovery WatchGuard-logganalyse
Cloud App Security Cloud Discovery analyserer et bredt spekter av trafikklogger for å rangere og score apper. Nå inkluderer Cloud Discovery en innebygd logganalyse for å støtte WatchGuard-formatet. Hvis du vil ha en liste over støttede logganalyser, kan du se Støttede brannmurer og proxyer.Ny tillatelse for global administratorrolle for Cloud Discovery
Cloud App Security tillater nå brukere med global administratorrolle for Cloud Discovery å opprette API-tokener og bruke alle Cloud Discovery-relaterte API-er. Hvis du vil ha mer informasjon om rollen, kan du se Innebygde Cloud App Security administratorroller.Viktig
Microsoft anbefaler at du bruker roller med færrest tillatelser. Dette bidrar til å forbedre sikkerheten for organisasjonen. Global administrator er en svært privilegert rolle som bør begrenses til nødscenarioer når du ikke kan bruke en eksisterende rolle.
Forbedret glidebryter for følsomhet: Umulig reise
Vi har oppdatert glidebryteren for følsomhet for umulige reiser for å konfigurere ulike følsomhetsnivåer for ulike brukeromfang, noe som gir bedre kontroll over gjengivelsen av varsler for brukeromfang. Du kan for eksempel definere et høyere følsomhetsnivå for administratorer enn for andre brukere i organisasjonen. Hvis du vil ha mer informasjon om denne avviksregistreringspolicyen, kan du se Umulig reise.Forbedret url-suffiks for proxy for øktkontroller (gradvis utrulling)
7. juni 2020 begynte vi gradvis å rulle ut våre forbedrede proxy-øktkontroller for å bruke ett enhetlig suffiks som ikke inkluderer navngitte områder. Brukere ser<AppName>.mcas.msfor eksempel suffiks i stedet<AppName>.<Region>.cas.msfor . Hvis du rutinemessig blokkerer domener i nettverksapparater eller gatewayer, må du sørge for at du tillater liste over alle domenene som er oppført under Access- og øktkontroller.
Cloud App Security utgivelse 184, 185 og 186
Utgitt 25. oktober 2020
Ny forbedret varslingsovervåking og administrasjonsopplevelse
Som en del av våre kontinuerlige forbedringer for overvåking og administrering av varsler, har siden Cloud App Security varsler blitt forbedret basert på tilbakemeldingene dine. Statusene Løst og Avvist erstattes av Lukket-statusen med en løsningstype i den forbedrede opplevelsen. Finn ut merNy global alvorsgradinnstilling for signaler som sendes til Microsoft Defender for endepunkter
Vi har lagt til muligheten til å angi den globale alvorsgradinnstillingen for signaler som sendes til Microsoft Defender for endepunkt. Hvis du vil ha mer informasjon, kan du se Hvordan integrere Microsoft Defender for endepunkt med Cloud App Security.Ny rapport for sikkerhetsanbefalinger
Cloud App Security gir deg sikkerhetskonfigurasjonsvurderinger for Azure, Amazon Web Services (AWS) og Google Cloud Platform (GCP) som gir deg innsikt i sikkerhetskonfigurasjonshull i multiskymiljøet ditt. Nå kan du eksportere detaljerte rapporter om sikkerhetsanbefalinger for å hjelpe deg med å overvåke, forstå og tilpasse skymiljøer for å beskytte organisasjonen bedre. Hvis du vil ha mer informasjon om hvordan du eksporterer rapporten, kan du se rapporten over sikkerhetsanbefalinger.Forbedret url-suffiks for proxy for øktkontroller (gradvis utrulling)
7. juni 2020 begynte vi gradvis å rulle ut våre forbedrede proxy-øktkontroller for å bruke ett enhetlig suffiks som ikke inkluderer navngitte områder. Brukere ser<AppName>.mcas.msfor eksempel suffiks i stedet<AppName>.<Region>.cas.msfor . Hvis du rutinemessig blokkerer domener i nettverksapparater eller gatewayer, må du sørge for at du tillater liste over alle domenene som er oppført under Access- og øktkontroller.Oppdateringer til katalogen for skyapper
Vi har gjort følgende oppdateringer i cloud app-katalogen vår:- Teams Admin Center er oppdatert som en frittstående app
- Microsoft 365 administrasjon Center har fått nytt navn til Office-portalen
Terminologioppdatering
Vi har oppdatert termmaskinen til enheten som en del av den generelle Microsoft-innsatsen for å justere terminologi på tvers av produkter.
Cloud App Security utgivelse 182 og 183
Utgitt 6. september 2020
-
Tilgangs- og øktkontroller for Azure Portal GA
Appkontroll for betinget tilgang for Azure Portal er nå generelt tilgjengelig. Hvis du vil ha mer informasjon, kan du se Beskytt apper med Microsoft Defender for Cloud Apps appkontroll for betinget tilgang.
Cloud App Security utgivelse 181
Utgitt 9. august 2020
Ny logganalyse for Cloud Discovery Menlo Security
Cloud App Security Cloud Discovery analyserer et bredt spekter av trafikklogger for å rangere og score apper. Nå inkluderer Cloud Discovery en innebygd logganalyse for å støtte Menlo Security CEF-formatet. Hvis du vil ha en liste over støttede logganalyser, kan du se Støttede brannmurer og proxyer.Azure Active Directory (AD) Cloud App Discovery-navn vises i portalen
For Azure AD P1- og P2-lisenser har vi oppdatert produktnavnet i portalen til Cloud App Discovery. Mer informasjon om Cloud App Discovery.
Cloud App Security utgivelse 179 og 180
Utgitt 26. juli 2020
Ny avviksregistrering: Mistenkelige nedlastingsaktiviteter for OAuth-appfiler
Vi har utvidet avviksregistreringene våre til å inkludere mistenkelige nedlastingsaktiviteter av en OAuth-app. Den nye gjenkjenningen er nå tilgjengelig utenfor boksen og automatisk aktivert for å varsle deg når en OAuth-app laster ned flere filer fra Microsoft SharePoint eller Microsoft OneDrive på en måte som er uvanlig for brukeren.Ytelsesforbedringer ved hjelp av proxy-hurtigbufring for øktkontroller (gradvis utrulling)
Vi har gjort ekstra ytelsesforbedringer i øktkontrollene våre ved å forbedre mekanismene for hurtigbufring av innhold. Den forbedrede tjenesten er enda mer strømlinjeformet og gir økt svartid når du bruker øktkontroller. Øktkontroller bufrer ikke privat innhold, og justeres etter de riktige standardene for bare å bufre delt (offentlig) innhold. Hvis du vil ha mer informasjon, kan du se Hvordan øktkontroll fungerer.Ny funksjon: Lagre sikkerhetskonfigurasjonsspørringer
Vi har lagt til muligheten til å lagre spørringer for instrumentbordfiltrene for sikkerhetskonfigurasjon for Azure, Amazon Web Services (AWS) og Google Cloud Platform (GCP). Dette kan bidra til å gjøre fremtidige undersøkelser enda enklere ved å bruke vanlige spørringer på nytt. Mer informasjon om konfigurasjonsanbefalinger for sikkerhet.Forbedrede varsler for avviksregistrering
Vi har utvidet informasjonen vi oppgir for avviksregistreringsvarsler til å inkludere en tilordning til tilsvarende MITRE ATT&CK-taktikk. Denne tilordningen hjelper deg med å forstå fasen og virkningen av angrepet og hjelpe deg med undersøkelsene dine. Mer informasjon om hvordan du undersøker varsler om avviksregistrering.Forbedret gjenkjenningslogikk: Aktivitet for løsepengevirus
Vi har oppdatert gjenkjenningslogikken for løsepengevirusaktivitet for å gi bedre nøyaktighet og redusert varslingsvolum. Hvis du vil ha mer informasjon om denne policyen for avviksregistrering, kan du se Løsepengevirusaktivitet.Rapporter om identitetssikkerhetsstilling: Synlighet for koder
Vi har lagt til enhetskoder i rapporter om identitetssikkerhetsstilling som gir ekstra innsikt om enheter. Sensitive-koden kan for eksempel hjelpe deg med å identifisere risikable brukere og prioritere undersøkelser. Mer informasjon om å undersøke risikable brukere.
Cloud App Security utgivelse 178
Utgitt 28. juni 2020
Nye sikkerhetskonfigurasjoner for Google Cloud Platform (gradvis utrulling)
Vi har utvidet sikkerhetskonfigurasjonene våre med flereskyer for å gi sikkerhetsanbefalinger for Google Cloud Platform, basert på GCP CIS-referanseverdien. Med denne nye funksjonaliteten gir Cloud App Security organisasjoner én visning for å overvåke samsvarsstatusen på tvers av alle skyplattformer, inkludert Azure abonnementer, AWS-kontoer og nå GCP-prosjekter.Nye appkoblinger GA
Vi har lagt til følgende appkoblinger i porteføljen vår av generelt tilgjengelige API-koblinger, noe som gir deg mer innsyn i og kontroll over hvordan appene brukes i organisasjonen:Ny registrering av skadelig programvare i sanntid
Vi har utvidet øktkontrollene våre for å oppdage potensiell skadelig programvare ved hjelp av Microsoft Trusselintelligens ved filopplastinger eller nedlastinger. Den nye gjenkjenningen er nå generelt tilgjengelig utenfor boksen og kan konfigureres til å automatisk blokkere filer identifisert som potensiell skadelig programvare. Hvis du vil ha mer informasjon, kan du se Blokkere skadelig programvare ved opplasting eller nedlasting.Forbedret tilgang og øktkontroller med IdP GA
Tilgangs- og øktkontroller for SAML-apper som er konfigurert med en hvilken som helst identitetsleverandør, er nå generelt tilgjengelig. Hvis du vil ha mer informasjon, kan du se Beskytt apper med Microsoft Defender for Cloud Apps appkontroll for betinget tilgang.Forbedring av risikabel maskinundersøkelse
Cloud App Security gir muligheten til å identifisere risikable maskiner som en del av skygge-IT-undersøkelse. Nå har vi lagt til risikonivået Microsoft Defender Advanced Threat Protection Machine på maskinsiden, noe som gir analytikere mer kontekst når de undersøker maskiner i organisasjonen. Hvis du vil ha mer informasjon, kan du se Undersøke enheter i Cloud App Security.Ny funksjon: Selvbetjent deaktiver appkobling (gradvis utrulling)
Vi har lagt til muligheten til å deaktivere appkoblinger direkte i Cloud App Security. Hvis du vil ha mer informasjon, kan du se Deaktivere appkoblinger.
Cloud App Security utgivelse 177
Utgitt 14. juni 2020
Ny gjenkjenning av skadelig programvare i sanntid (forhåndsversjon, gradvis utrulling)
Vi har utvidet øktkontrollene våre for å oppdage potensiell skadelig programvare ved hjelp av Microsoft Trusselintelligens ved filopplastinger eller nedlastinger. Den nye gjenkjenningen er nå tilgjengelig utenfor boksen og kan konfigureres til å automatisk blokkere filer identifisert som potensiell skadelig programvare. Hvis du vil ha mer informasjon, kan du se Blokkere skadelig programvare ved opplasting eller nedlasting.Ny tilgangstokenstøtte for tilgangs- og øktkontroller
Vi har lagt til muligheten til å behandle tilgangstoken- og kodeforespørsler som pålogginger når du legger inn apper for tilgang og øktkontroller. Hvis du vil bruke tokener, velger du tannhjulikonet for innstillinger, velger Appkontroll for betinget tilgang, redigerer den aktuelle appen (tre prikker-menyen >Rediger app), velger Behandle tilgangstoken og kodeforespørsler som apppålogginger, og deretter velger du Lagre. Hvis du vil ha mer informasjon, kan du se Beskytt apper med Microsoft Defender for Cloud Apps appkontroll for betinget tilgang.Forbedret url-suffiks for proxy for øktkontroller (gradvis utrulling)
7. juni 2020 begynte vi gradvis å rulle ut våre forbedrede proxy-øktkontroller for å bruke ett enhetlig suffiks som ikke inkluderer navngitte områder. Brukere ser<AppName>.mcas.msfor eksempel suffiks i stedet<AppName>.<Region>.cas.msfor . Hvis du rutinemessig blokkerer domener i nettverksapparater eller gatewayer, må du sørge for at du tillater liste over alle domenene som er oppført under Access- og øktkontroller.Ny dokumentasjon
Cloud App Security dokumentasjon er utvidet til å omfatte følgende nytt innhold:- Bruk Cloud App Security REST-API: Finn ut mer om API-funksjonene våre, og begynn å integrere programmene dine med Cloud App Security.
- Undersøk varsler om avviksregistrering: Bli kjent med de tilgjengelige UEBA-varslene, hva de betyr, identifiser risikoen de utgjør, forstå omfanget av et brudd, og handlingen du kan utføre, utbedre situasjonen.
Cloud App Security utgivelse 176
Utgitt 31. mai 2020
Ny funksjon for personvern for aktivitet
Vi har forbedret muligheten til å bestemme detaljert hvilke brukere du vil overvåke, med muligheten til å gjøre aktiviteter private. Med denne nye funksjonen kan du angi brukere basert på gruppemedlemskap hvis aktiviteter skjules som standard. Bare autoriserte administratorer har mulighet til å velge å vise disse private aktivitetene, der hver forekomst overvåkes i styringsloggen. Hvis du vil ha mer informasjon, kan du se Aktivitetspersonvern.Ny integrering med Azure Active Directory-galleri (Azure AD)
Vi har brukt den opprinnelige integreringen med Azure AD for å gi deg muligheten til å navigere direkte fra en app i katalogen for skyapper til den tilsvarende Azure AD Gallery-appen, og administrere den i galleriet. Hvis du vil ha mer informasjon, kan du se Behandle apper med Azure AD Galleri.Nytt tilbakemeldingsalternativ tilgjengelig i valgte policyer
Vi er interessert i å motta tilbakemeldinger og lære hvordan vi kan hjelpe deg. Så nå gir en ny dialogboks for tilbakemelding deg muligheten til å forbedre Cloud App Security, når du oppretter, endrer eller sletter en fil, avviksregistrering eller øktpolicy.Forbedret url-suffiks for proxy for øktkontroller (gradvis utrulling)
Fra og med 7. juni 2020 ruller vi gradvis ut våre forbedrede proxy-øktkontroller for å bruke ett enhetlig suffiks som ikke inkluderer navngitte områder. Brukere ser<AppName>.mcas.msfor eksempel suffiks i stedet<AppName>.<Region>.cas.msfor . Hvis du rutinemessig blokkerer domener i nettverksapparater eller gatewayer, må du sørge for at du tillater liste over alle domenene som er oppført under Access- og øktkontroller.Ytelsesforbedringer for øktkontroller (gradvis utrulling)
Vi har forbedret nettverksytelsen betydelig. Den forbedrede tjenesten er enda mer strømlinjeformet og gir økt svartid når du bruker øktkontroller.Ny risikabel aktivitetsregistrering: Uvanlig mislykket pålogging
Vi har utvidet vår nåværende evne til å oppdage risikabel atferd. Den nye gjenkjenningen er nå tilgjengelig utenfor boksen og aktiveres automatisk for å varsle deg når et uvanlig mislykket påloggingsforsøk identifiseres. Uvanlige mislykkede påloggingsforsøk kan være en indikasjon på et potensielt passord-spray brute force angrep (også kjent som lav og langsom metode). Denne gjenkjenningen påvirker den overordnede prioritetspoengsummen for undersøkelser for brukeren.Forbedret tabellopplevelse
Vi har lagt til muligheten til å endre størrelsen på kolonnebredder i tabeller, slik at du kan utvide eller begrense kolonner for å tilpasse og forbedre måten du viser tabeller på. Du kan også gjenopprette det opprinnelige oppsettet ved å velge menyen for tabellinnstillinger og velge Standardbredde.
Cloud App Security utgivelse 175
Utgitt 17. mai 2020
Ny Shadow IT Discovery-integrasjon med Corrata (forhåndsversjon)
Vi har lagt til opprinnelig integrering med Corrata som gir deg skygge-IT-synlighet i appbruk og kontroll over apptilgang. Hvis du vil ha mer informasjon, kan du se Integrere Cloud App Security med korrelasjon.Nye logganalyser for Cloud Discovery
Cloud App Security Cloud Discovery analyserer et bredt spekter av trafikklogger for å rangere og score apper. Nå inkluderer Cloud Discovery en innebygd logganalyse for å støtte Corrata og Cisco ASA med FirePOWER 6.4-loggformater. Hvis du vil ha en liste over støttede logganalyser, kan du se Støttede brannmurer og proxyer.Forbedret instrumentbord (gradvis utrulling) Som en del av våre kontinuerlige forbedringer i portalutformingen ruller vi nå gradvis ut det forbedrede instrumentbordet Cloud App Security. Instrumentbordet er modernisert basert på tilbakemeldinger og gir en forbedret brukeropplevelse med oppdatert innhold og data. Hvis du vil ha mer informasjon, kan du se Gradvis distribusjon av det forbedrede instrumentbordet.
Forbedret styring: Bekreft bruker kompromittert for avviksregistreringer
Vi har utvidet våre gjeldende styringshandlinger for avvikspolicyer til å inkludere Bekreft brukerkompromisset , slik at du proaktivt kan beskytte miljøet mot mistenkelig brukeraktivitet. Hvis du vil ha mer informasjon, kan du se handlinger for aktivitetsstyring.
Cloud App Security utgivelse 173 og 174
Utgitt 26. april 2020
-
Nytt CEF-format for SIEM-agent for varsler
Som en del av vårt forsøk på å berike varslingsinformasjonen i CEF-filene som brukes av generiske SIEM-servere, har vi utvidet formatet til å inkludere følgende klientfelt:IPv4-adresse
IPv6-adresse
IP-adresseplassering
Hvis du vil ha mer informasjon, kan du se CEF-filformatet.
-
Forbedret oppdagelseslogikk: Umulig reise
Vi har oppdatert gjenkjenningslogikken for umulige reiser for å gi bedre nøyaktighet og redusert varslingsvolum. Hvis du vil ha mer informasjon om denne avviksregistreringspolicyen, kan du se Umulig reise.
Cloud App Security utgivelse 172
Utgitt 5. april 2020
Forbedret tilgang og øktkontroller med IdP (forhåndsversjon)
Tilgangs- og øktkontroller støtter nå SAML-apper som er konfigurert med en hvilken som helst identitetsleverandør. Den offentlige forhåndsvisningen av denne nye funksjonen rulles nå gradvis ut. Hvis du vil ha mer informasjon, kan du se Beskytt apper med Microsoft Defender for Cloud Apps appkontroll for betinget tilgang.Ny bulkdekanonymisering av brukere og maskiner
Vi har utvidet og forenklet prosessen med å dekanonymisere én eller flere brukere og maskiner som undersøkes. Hvis du vil ha mer informasjon om massedekanonymisering, kan du se Hvordan anonymisering av data fungerer.
Cloud App Security utgivelse 170 og 171
Utgitt 22. mars 2020
Ny avviksregistrering: Uvanlig område for skyressurs (forhåndsversjon)
Vi har utvidet vår nåværende evne til å oppdage uregelmessig oppførsel for AWS. Den nye gjenkjenningen er nå tilgjengelig utenfor boksen og aktiveres automatisk for å varsle deg når en ressurs opprettes i et AWS-område der aktiviteten vanligvis ikke utføres. Angripere bruker ofte en organisasjons AWS-kreditter til å utføre ondsinnede aktiviteter som krypto-gruvedrift. Det å oppdage en slik uregelmessig oppførsel kan bidra til å redusere et angrep.Nye aktivitetspolicymaler for Microsoft Teams
Cloud App Security tilbyr nå følgende nye aktivitetspolicymaler, slik at du kan oppdage potensielt mistenkelige aktiviteter i Microsoft Teams:- Endring av tilgangsnivå (Teams): Varsler når tilgangsnivået til et team endres fra privat til offentlig.
- Ekstern bruker lagt til (Teams): Varsler når en ekstern bruker legges til i et team.
- Massesletting (Teams): Varsler når en bruker sletter et stort antall team.
Integrering av identitetsbeskyttelse for Azure Active Directory (Azure AD)
Nå kan du kontrollere alvorlighetsgraden av Azure AD varsler om identitetsbeskyttelse som er inntatt i Cloud App Security. I tillegg, hvis du ikke allerede har aktivert Azure AD risikokrevende påloggingsgjenkjenning, aktiveres gjenkjenningen automatisk til å ta varsler med høy alvorlighetsgrad. Hvis du vil ha mer informasjon, kan du se Azure Integrering av Active Directory Identity Protection.
Cloud App Security utgivelse 169
Utgitt 1. mars 2020
Ny gjenkjenning for arbeidsdag
Vi har utvidet de gjeldende avvikende virkemåtevarslingene for Arbeidsdag. De nye varslene inkluderer følgende geolokasjonsgjenkjenninger for brukere:Forbedret Salesforce-loggsamling
Cloud App Security støtter nå Salesforces hendelseslogg per time. Hendelseslogger per time gir deg akselerert overvåking i nærheten av sanntidsovervåking av brukeraktiviteter. Hvis du vil ha mer informasjon, kan du se Connect Salesforce.Støtte for AWS-sikkerhetskonfigurasjon ved hjelp av en hovedkonto
Cloud App Security støtter nå bruk av en hovedkonto. Ved å koble til hovedkontoen kan du motta sikkerhetsanbefalinger for alle medlemskontoer i alle områder. Hvis du vil ha mer informasjon om hvordan du kobler til en hovedkonto, kan du se Slik kobler du AWS-sikkerhetskonfigurasjon til Defender for Cloud Apps.Øktkontroller støtte for moderne nettlesere
Cloud App Security øktkontroller inkluderer nå støtte for den nye Microsoft Edge-nettleseren basert på Chromium. Selv om vi fortsetter å støtte de nyeste versjonene av Internet Explorer og den eldre versjonen av Microsoft Edge, er støtten begrenset, og vi anbefaler at du bruker den nye Microsoft Edge-nettleseren.
Cloud App Security utgivelse 165, 166, 167 og 168
Utgitt 16. februar 2020
Nye blokk ikke-helliggjorte apper med Microsoft Defender ATP
Cloud App Security har utvidet sin opprinnelige integrasjon med Microsoft Defender Advanced Threat Protection (ATP). Nå kan du blokkere tilgang til apper merket som ikke-helliggjort ved hjelp av Microsoft Defender ATPs nettverksbeskyttelsesfunksjonalitet. Hvis du vil ha mer informasjon, kan du se Blokkere tilgang til ikke-helliggjorte skyapper.Avviksregistrering av ny OAuth-app
Vi har utvidet vår nåværende mulighet til å oppdage ondsinnet OAuth-appsamtykke. Den nye gjenkjenningen er nå tilgjengelig utenfor boksen og aktiveres automatisk for å varsle deg når en potensielt skadelig OAuth-app er autorisert i miljøet ditt. Denne oppdagelsen bruker Microsofts sikkerhetsundersøkelser og ekspertise innen trusselintelligens til å identifisere skadelige apper.Logginnsamlingsoppdateringer
Den Docker-baserte loggsamleren ble forbedret med følgende viktige oppdateringer:Oppgradering av beholderoperativsystemets versjon
Sikkerhetsoppdateringer for Java-sikkerhet
Oppgradering av Syslog-tjenesten
Stabilitet og ytelsesforbedringer
Vi anbefaler på det sterkeste at du oppgraderer miljøet til denne nye versjonen. Hvis du vil ha mer informasjon, kan du se Log Collector-distribusjonsmoduser.
Støtte for ServiceNow New York
Cloud App Security støtter nå den nyeste versjonen (New York) av ServiceNow. Hvis du vil vite mer om hvordan du sikrer ServiceNow, kan du se Koble ServiceNow til Microsoft Cloud App Security.Forbedret oppdagelseslogikk: Umulig reise
Vi har oppdatert gjenkjenningslogikken for umulige reiser for å gi bedre dekning og bedre nøyaktighet. Som en del av denne oppdateringen oppdaterte vi også gjenkjenningslogikken for umulig reise fra bedriftsnettverk.Ny terskel for aktivitetspolicyer
Vi har lagt til en terskel for aktivitetspolicyer for å hjelpe deg med å administrere volumet av varsler. Policyer som utløser et stort antall treff i flere dager, deaktiveres automatisk. Hvis du mottar et systemvarsel om dette, bør du prøve å begrense policyer ved å legge til ekstra filtre, eller, hvis du bruker policyer til rapporteringsformål, bør du vurdere å lagre dem som spørringer i stedet.
Oppdateringer laget i 2019
Cloud App Security utgivelse 162, 163 og 164
Utgitt 8. desember 2019
-
Endre til SIEM-aktiviteter og varsler i CEF-format
Portal-URL-formatet (CS1) for aktivitets- og varselinformasjon som sendes av Cloud App Security til SIEMer, er endret tilhttps://<tenant_name>.portal.cloudappsecurity.comog inneholder ikke lenger datasenterplasseringen. Kunder som bruker mønstersamsvar for nettadressen for portalen, bør oppdatere mønsteret for å gjenspeile denne endringen.
Cloud App Security utgivelse 160 og 161
Utgitt 3. november 2019
Søkedata i Azure Sentinel (forhåndsversjon)
Cloud App Security integreres nå med Azure Sentinel. Deling av varsel- og oppdagelsesdata med Azure Sentinel gir følgende fordeler:Aktiver korrelasjon av søkedata med andre datakilder for dypere analyse.
Vis data i Power BI med forhåndsdefinerte instrumentbord eller bygg dine egne visualiseringer.
Nyt lengre oppbevaringsperioder med Log Analytics.
Hvis du vil ha mer informasjon, kan du se Azure Sentinel integrering.
Google Cloud Platform-kobling (forhåndsversjon)
Cloud App Security utvider sine IaaS-overvåkingsfunksjoner utover Amazon Web Services og Azure og støtter nå Google Cloud Platform. Dette gjør at du sømløst kan koble til og overvåke alle GCP-arbeidsbelastningene med Cloud App Security. Tilkoblingen gir deg et kraftig sett med verktøy for å beskytte GCP-miljøet, inkludert:Innsyn i alle aktiviteter som utføres gjennom administrasjonskonsollen og API-kall.
Muligheten til å opprette egendefinerte policyer og bruke forhåndsdefinerte maler til å varsle om risikable hendelser.
Alle GCP-aktiviteter dekkes av avviksregistreringsmotoren vår og varsler automatisk om mistenkelig oppførsel, for eksempel umulig reise, mistenkelige masseaktiviteter og aktivitet fra et nytt land/område.
Hvis du vil ha mer informasjon, kan du se Koble Google Workspace til Microsoft Defender for Cloud Apps.
Nye policymaler
Cloud App Security inkluderer nå nye innebygde aktivitetspolicymaler for anbefalte fremgangsmåter for Google Cloud Platform-sikkerhet.Forbedret logganalyse for cloud discovery
Cloud App Security Cloud Discovery analyserer et bredt spekter av trafikklogger for å rangere og score apper. Nå støtter Cloud Discoverys innebygde logganalyse Ironport WSA 10.5.1-loggformatet.Brukerlandingsside som kan tilpasses for øktkontroller
Vi har lansert muligheten for administratorer til å tilpasse målsiden som brukerne ser når de navigerer til en app som en øktpolicy brukes på. Nå kan du vise organisasjonens logo og tilpasse meldingen som vises. Hvis du vil begynne å tilpasse, går du til Innstillinger-siden og velger brukerovervåking under Appkontroll for skytilgang.Nye gjenkjenninger
Mistenkelige endringer i AWS-loggingstjenesten (forhåndsversjon): Varsler deg når en bruker gjør endringer i loggingstjenesten i CloudTrail. Angripere slår for eksempel ofte av overvåking i CloudTrail for å skjule fotavtrykkene til angrepet.
Flere vm-opprettelsesaktiviteter: Varsler deg når en bruker utfører et uvanlig antall vm-opprettelsesaktiviteter, sammenlignet med den lærde grunnlinjen. Gjelder nå for AWS.
Cloud App Security utgivelse 159
Utgitt 6. oktober 2019
Ny logganalyse for Cloud Discovery ContentKeeper
Cloud App Security Cloud Discovery analyserer et bredt spekter av trafikklogger for å rangere og score apper. Nå inkluderer Cloud Discovery en innebygd logganalyse for å støtte ContentKeeper-loggformater. Hvis du vil ha en liste over støttede logganalyser, kan du se Støttede brannmurer og proxyer.Nye oppdagelser
Følgende nye policyer for avviksregistrering er tilgjengelige utenfor boksen og aktiveres automatisk:Mistenkelig e-postslettingsaktivitet (forhåndsversjon)
Varsler deg når en bruker utfører uvanlige aktiviteter for sletting av e-post. Denne policyen kan hjelpe deg med å oppdage brukerpostbokser som kan bli kompromittert av potensielle angrepsvektorer, for eksempel kommando- og kontrollkommunikasjon (C&C/C2) via e-post.Flere rapportdelinger i Power BI (forhåndsversjon)
Varsler deg når en bruker utfører et uvanlig antall aktiviteter for rapportdeling i Power BI, sammenlignet med den lærde grunnlinjen.Flere vm-opprettelsesaktiviteter (forhåndsversjon)
Varsler deg når en bruker utfører et uvanlig antall vm-opprettelsesaktiviteter, sammenlignet med den lærde grunnlinjen. Gjelder for øyeblikket for Azure.Aktiviteter for sletting av flere lagringsplass (forhåndsversjon)
Varsler deg når en bruker utfører et uvanlig antall aktiviteter for sletting av lagring, sammenlignet med den lærde grunnlinjen. Gjelder for øyeblikket for Azure.
Cloud App Security utgivelse 158
Utgitt 15. september 2019
Tilpass navn på skyoppdagelsesrapport
Den overordnede rapporten i Cloud Discovery gir deg en oversikt over Shadow IT-bruk på tvers av organisasjonen. Du har nå muligheten til å tilpasse rapportnavnet før du genererer det. Hvis du vil ha mer informasjon, kan du se Generer lederrapport for Cloud Discovery.Oversiktsrapport for nye policyer
Cloud App Security oppdager policysamsvar og logger varsler som du kan bruke til å forstå skymiljøet dypere, der det er definert. Nå kan du eksportere en policyoversiktsrapport som viser aggregerte varslingsmåledata per policy for å hjelpe deg med å overvåke, forstå og tilpasse policyene dine for å beskytte organisasjonen bedre. Hvis du vil ha mer informasjon om hvordan du eksporterer rapporten, kan du se oversiktsrapporten Policyer.
Cloud App Security utgivelse 157
Utgitt 1. september 2019
Påminnelse: Slutt på støtte for TLS 1.0 og 1.1 den 8. september
Microsoft flytter alle sine onlinetjenester til Transport Layer Security (TLS) 1.2+ for å gi best mulig kryptering. Fra og med 8. september 2019 vil ikke Cloud App Security lenger støtte TLS 1.0 og 1.1, og tilkoblinger som bruker disse protokollene, støttes ikke. Hvis du vil ha mer informasjon om hvordan endringen påvirker deg, kan du se blogginnlegget vårt.Ny oppdagelse – mistenkelig Microsoft Power BI deling (forhåndsversjon)
Den nye mistenkelige delingspolicyen for Power BI-rapporter er nå tilgjengelig utenfor boksen og automatisk aktivert for å varsle deg når en potensielt sensitiv Power BI-rapport deles mistenkelig utenfor organisasjonen.Ny eksportfunksjon for OAuth-appovervåking
Cloud App Security overvåker alle OAuth-autorisasjonsaktiviteter for å gi deg omfattende overvåking og undersøkelse av aktiviteter som utføres. Nå kan du også eksportere detaljene for brukere som godkjente en bestemt OAuth-app, og gi deg tilleggsinformasjon om brukerne, som du deretter kan bruke til videre analyse.Forbedret overvåking av Okta-hendelser
Cloud App Security støtter nå den nye API-en for systemlogg, utgitt av Okta. Hvis du vil ha mer informasjon om hvordan du kobler til Okta, kan du se Koble til Okta.Arbeidsdagkobling (forhåndsversjon)
En ny appkobling er nå tilgjengelig for Workday. Nå kan du koble arbeidsdagen til Cloud App Security for å overvåke aktiviteter og beskytte brukere og aktiviteter. Hvis du vil ha mer informasjon, kan du se Koble til arbeidsdag.Forbedret vurdering for risikofaktoren «Passordpolicy»
Katalogen for skyapper gir nå detaljert vurdering av risikofaktoren for passordpolicy . Ved å holde pekeren over informasjonsikonet kan du se en oversikt over de spesifikke policyene som håndheves av appen.
Cloud App Security utgivelse 156
Utgitt 18. august 2019
Nye logganalyser for Cloud Discovery
Cloud App Security Cloud Discovery analyserer et bredt spekter av trafikklogger for å rangere og score apper. Nå inkluderer Cloud Discovery en innebygd logganalyse for å støtte Stormshield- og Forcepoint LEEF-loggformater.Forbedringer for aktivitetslogg
Cloud App Security gir deg nå større innsyn i uklassifiserte aktiviteter som utføres av apper i miljøet ditt. Disse aktivitetene er tilgjengelige i aktivitetsloggen og i aktivitetspolicyer. Hvis du vil se uklassifiserte aktiviteter, velger du Uspesifisert i Type-filteret. Hvis du vil ha mer informasjon om aktivitetsfiltre, kan du se Aktivitetsfiltre og spørringer.Forbedring av risikobrukerundersøkelse
Cloud App Security gir muligheten til å identifisere risikable brukere på brukere- og kontosiden etter bestemte grupper, apper og til og med roller. Nå kan du også undersøke brukerne i organisasjonen etter prioritetspoengsummen for undersøkelse . Hvis du vil ha mer informasjon, kan du se Forstå prioritetspoengsummen for undersøkelsen.Forbedringer for aktivitetspolicy
Nå kan du opprette aktivitetspolicyvarsler basert på aktivitetsobjekter. Denne funksjonen lar deg for eksempel opprette varsler om endringer i Azure administrative roller i Active Directory. Hvis du vil ha mer informasjon om aktivitetsobjekter, kan du se Aktivitetsfiltre.
Cloud App Security utgivelse 155
Utgitt 4. august 2019
Nye policymaler
Cloud App Security inkluderer nå nye innebygde aktivitetspolicymaler for anbefalte fremgangsmåter for AWS-sikkerhet.Varsel: Slutt på støtte for TLS 1.0 og 1.1 den 8. september
Microsoft flytter alle sine onlinetjenester til Transport Layer Security (TLS) 1.2+ for å gi best mulig kryptering. Fra og med 8. september 2019 vil ikke Cloud App Security lenger støtte TLS 1.0 og 1.1, og tilkoblinger som bruker disse protokollene, støttes ikke. Hvis du vil ha mer informasjon om hvordan endringen påvirker deg, kan du se blogginnlegget vårt.Forbedret logikk for interaktive påloggingsaktiviteter (gradvis utrulling)
Vi ruller gradvis ut ny logikk for å identifisere om en Azure Active Directory-påloggingsaktivitet er interaktiv. Den nye logikken forbedrer Cloud App Security muligheten til bare å vise påloggingsaktiviteter som startes av en bruker.
Cloud App Security utgivelse 154
Utgitt 21. juli 2019
Om bord og distribuer appkontroll for betinget tilgang for alle apper er nå GA
Siden forhåndsvisning av appkontroll for betinget tilgang for en app forrige måned, har vi fått enorme tilbakemeldinger og er glade for å kunngjøre GA. Med denne nye funksjonen kan du distribuere alle nettapper for å arbeide med økt- og tilgangspolicyer, noe som muliggjør kraftig overvåking og kontroll i sanntid.Vurdering av sikkerhetskonfigurasjon for AWS
Cloud App Security ruller gradvis ut muligheten til å få en sikkerhetskonfigurasjonsvurdering av Amazon Web Services-miljøet for CIS-samsvar, og gir anbefalinger for manglende konfigurasjoner og sikkerhetskontroller. Denne muligheten gir organisasjoner én visning for overvåking av samsvarsstatus for alle tilkoblede AWS-kontoer.Avviksregistreringer for OAuth-appen
Vi har utvidet vår nåværende evne til å oppdage mistenkelige OAuth-apper. Fire nye oppdagelser er nå tilgjengelige utenfor boksen som profilerer metadataene til OAuth-apper som er autorisert i organisasjonen, for å identifisere de som er potensielt skadelige.
Cloud App Security utgivelse 153
Utgitt 7. juli 2019
Forbedret Dropbox-støtte
Cloud App Security støtter nå papirkurvstyringshandlingen for Dropbox – denne styringshandlingen kan brukes manuelt eller automatisk som en del av en filpolicy.Nye utvalgte apper for Cloud Access App Control
Appkontroll for betinget tilgang for følgende utvalgte apper er nå generelt tilgjengelig:- OneDrive for Business
- SharePoint Online
- Azure DevOps
- Exchange Online
- Power BI
Godkjenn filer identifisert som skadelig programvare
Cloud App Security skanner filer fra de tilkoblede appene for eksponering og skadelig programvare for DLP. Nå kan du godkjenne filer som er identifisert som skadelig programvare, men som er bekreftet trygge etter en undersøkelse. Godkjenning av en fil fjerner den fra rapporten for registrering av skadelig programvare og undertrykker fremtidige treff på denne filen. Hvis du vil ha mer informasjon om gjenkjenning av skadelig programvare, kan du se Cloud App Security avviksregistrering.
Cloud App Security utgivelse 152
Utgitt 23. juni 2019
-
Distribuer appkontroll for betinget tilgang for alle apper (forhåndsversjon)
Vi er glade for å kunngjøre at vi har utvidet vår støtte for appkontroll for betinget tilgang til alle nettapper, i tillegg til den rike støtten vi allerede tilbyr for våre utvalgte programmer. Med denne nye funksjonen kan du distribuere alle nettapper for å arbeide med økt- og tilgangspolicyer, noe som muliggjør kraftig overvåking og kontroll i sanntid. Du kan for eksempel beskytte nedlastinger med Azure Information Protection etiketter, blokkere opplasting av sensitive dokumenter, blant annet overvåking. -
Overvåking av portalaktivitet
Cloud App Security overvåker all administratoraktivitet i portalen for å gi deg omfattende overvåking og undersøkelse av aktiviteter som utføres. Nå kan du også eksportere opptil 90 dager med aktiviteter for videre undersøkelser og analyser, for eksempel overvåking av en administrator som undersøker en bestemt bruker eller viser bestemte varsler. Hvis du vil eksportere loggen, går du til siden Behandle innstillinger for administratortilgang . -
Logg av egendefinert økt fra Cloud App Security portal
Nå kan du konfigurere automatisk avlogging av administrasjonsøkter til portalen som er inaktiv lenger enn en angitt periode.
Cloud App Security utgivelse 151
Utgitt 9. juni 2019
-
Hybrid UEBA – opprinnelig integrering med Azure ATP (forhåndsversjon)
Cloud App Security integreres nå opprinnelig med Azure ATP for å gi én enkelt visning av identitetsaktiviteter i både skyapper og det lokale nettverket. Hvis du vil ha mer informasjon, kan du se Azure Advanced Threat Protection-integrering. -
UEBA-forbedringer
For å hjelpe deg med å identifisere trusler som faller under radaren, bruker Cloud App Security nå unik profilering for å gi risikoresultater for individuelle aktiviteter og varsler. Risikoresultatene kan brukes til å identifisere aktiviteter som ikke er mistenkelige nok på egen hånd til å utløse varsler. Men ved å aggregere risikoresultatene til en brukers prioritetspoengsum for undersøkelse, hjelper Cloud App Security deg med å identifisere risikabel atferd og fokusere undersøkelsen. Disse nye funksjonene er nå tilgjengelige på vår nyutformede brukerside. -
Ny risikofaktor lagt til i katalogen for skyapper
Skyappkatalogen inkluderer nå risikofaktoren for disaster recovery plan, slik at du kan vurdere appene i Cloud App Catalog for støtte for forretningskontinuitet. -
Microsoft Flow connector GA
Siden du forhåndsviser Microsoft Cloud App Security støtte for Microsoft Flow-koblingen i fjor, er koblingen nå generelt tilgjengelig. -
Automatisert styringsforbedring for filpolicyer
Cloud App Security støtter nå konfigurering av papirkurvstyringshandlingen for filpolicyer – denne styringshandlingen gir deg muligheten til automatisk å flytte filer til papirkurvmappen. -
Forbedret støtte for Google Drive
Cloud App Security støtter nå papirkurvstyringshandlingen for Google Drive – denne styringshandlingen gir deg muligheten til å flytte Google Drive-filer til papirkurvmappen. -
Ny tillatelse for rollene som appadministrator og gruppeadministrator
Rollene app/forekomstadministrator og brukergruppeadministrator støtter nå skrivebeskyttet tilgang. -
Eldre påloggingsaktiviteter for godkjenning (gradvis utrulling)
Cloud App Security dukker nå opp Azure Active Directory-påloggingsaktiviteter som bruker eldre protokoller som ActiveSync. Disse påloggingsaktivitetene kan vises i aktivitetsloggen og kan brukes når du konfigurerer policyer.
Cloud App Security utgivelse 150
Utgitt 26. mai 2019
-
Eksportforbedring for varsler
Når du eksporterer varsler til CSV fra Varsler-siden , vil resultatene nå inkludere datoen for varslingsløsningen eller oppsigelsen.
Cloud App Security utgivelse 148 og 149
Utgitt 12. mai 2019
Webex App-kobling tilgjengelig
En ny appkobling er nå tilgjengelig for Cisco Webex Teams i offentlig forhåndsversjon. Nå kan du koble Microsoft Cloud App Security til Cisco Webex Teams for å overvåke og beskytte brukere, aktiviteter og filer. Hvis du vil ha mer informasjon, kan du se Koble til WebexNye plasseringer for Microsoft Data Classification Service
Microsoft Data Classification Service er nå tilgjengelig på fire nye steder – Australia, India, Canada og Japan. Hvis Office-leieren er plassert på disse plasseringene, kan du nå bruke Microsoft Data Classification Service som innholdsinspeksjonsmetode i Microsoft Cloud App Security filpolicyer.Oppdagelse av Shadow PaaS og IaaS
Microsoft Cloud App Security har utvidet sine Cloud Discovery-funksjoner og tilbyr nå også Shadow IT for ressurser som driftes på IaaS- og PaaS-løsninger som Microsoft Azure, Amazon Web Services og Google Cloud Platform. Cloud Discovery gir deg nå innsyn i hvilke egendefinerte apper som kjører på toppen av IaaS og PaaS, lagringskontoer som opprettes og mer. Bruk denne nye funksjonen for å finne ut hvilke ressurser som finnes, hvem som får tilgang til hver av dem, og hvor mye trafikk som overføres.App-attesting
Microsoft Cloud App Security samsvars- og risikovurdering gjør det nå mulig for skyleverandører å bekrefte at appen deres er oppdatert i Cloud App Catalog. Denne piloten gjør det mulig for skyleverandører å fylle ut et selvattrestspørringsspørreskjema basert på cloud appkatalogens risikoattributter for å sikre at risikovurderingen i Cloud App Security er nøyaktig og oppdatert. Brukere kan deretter få en indikasjon på hvilke risikoattributter som ble testet av leverandøren (i stedet for vurdert av Cloud App Security-teamet), og når hvert attributt ble sendt inn av leverandøren. Hvis du vil ha mer informasjon, kan du se Attest appen.Detaljnivå for Arbeidsbelastning for Microsoft 365
Når du kobler Microsoft 365 til Microsoft Cloud App Security, har du nå kontroll over hvilke arbeidsbelastninger du vil koble til. Kunder som for eksempel bare er interessert i å koble til Microsoft 365 for aktivitetsovervåking, kan nå gjøre dette under tilkoblingsprosessen, eller ved å redigere en eksisterende Microsoft 365-kobling. Som en del av denne endringen vises ikke lenger OneDrive og SharePoint som separate koblinger, men inkluderes i Microsoft 365-koblingen som arbeidsbelastningen for Microsoft 365-filer . Kunder med en eksisterende Microsoft 365-kobling påvirkes ikke av denne endringen.Forbedret støtte for Teams
Nå kan du overvåke og blokkere sending av meldinger i Teams-nettappen i sanntid ved å konfigurere en øktpolicy basert på sensitivt innhold.
Cloud App Security utgivelse 147
Utgitt 14. april 2019
Ny logganalyse for Cloud Discovery
Cloud App Security Cloud Discovery inkluderer nå en innebygd logganalyse for å støtte Palo Alto LEEF-loggformatet.Oppdateringer for øktpolicyer
- Ekstra innholdsinspeksjonsmetode for øktpolicyer: Når du angir en øktpolicy, har du nå muligheten til å velge DataKlassifiseringstjeneste som en innholdsinspeksjonsmetode for filer. Dataklassifiseringstjenesten gir brukeren et bredt spekter av innebygde sensitive typer som skal brukes til å identifisere sensitiv informasjon.
- Bedre filtillatelser kontrollerer øktpolicyer: Når du oppretter en øktpolicy for å kontrollere nedlastinger ved hjelp av Cloud App Security, kan du nå automatisk bruke tillatelser per bruker, for eksempel skrivebeskyttet, på dokumentene ved nedlasting fra skyappene. Dette gir større fleksibilitet og muligheten til å beskytte informasjon utover de forhåndskonfigurerte firmaetikettene.
- Kontroll for stor filnedlasting: Når innholdsinspeksjon er aktivert i øktpolicyer, kan du nå kontrollere hva som skjer når en bruker prøver å laste ned en stor fil. Hvis filen er for stor til å skanne ved nedlasting, kan du velge om den skal blokkeres eller tillates.
Cloud App Security utgivelse 146
Utgitt 31. mars 2019
-
Umulig reiseforbedring
Umulig reisedeteksjon ble forbedret med dedikert støtte til naboland/regioner. -
Ekstra attributtstøtte for den generiske CEF-parseren
Cloud Discovery-logganalysestøtten for generisk CEF-format ble forbedret for å støtte ekstra attributter. -
Områdetilgang til Cloud Discovery-rapporter
I tillegg til søkerollen Admin, kan du nå begrense tilgangen til bestemte discovery-rapporter. Med denne forbedringen kan du konfigurere rettigheter til data for bestemte områder og forretningsenheter. -
Støtte for ny rolle: Global leser
Microsoft Cloud App Security støtter nå rollen Azure AD global leser. Den globale leseren har full skrivebeskyttet tilgang til alle aspekter av Microsoft Cloud App Security, men kan ikke endre noen innstillinger eller utføre noen handlinger.
Cloud App Security utgivelse 145
Utgitt 17. mars 2019
-
Microsoft Defender ATP-integrering er nå GA
I fjor annonserte vi integrering med Windows Defender Advanced Threat Protection som forbedrer Discovery of Shadow IT i organisasjonen, og utvider det utover bedriftsnettverket. Aktivert med ett enkelt klikk, er vi glade for å kunngjøre at denne unike integrasjonen nå er generelt tilgjengelig. -
Dynamics 365 CRM-støtte
Cloud App Security lagt til overvåking og kontroll i sanntid for Dynamics 365 CRM, slik at du kan beskytte forretningsprogrammene og det sensitive innholdet som er lagret i disse appene. Hvis du vil ha mer informasjon om hva som kan gjøres med Dynamics 365 CRM, kan du se denne artikkelen.
Cloud App Security utgivelse 144
Utgitt 3. mars 2019
Unified SecOps-undersøkelse for hybridmiljøer
Fordi mange organisasjoner har hybridmiljøer, starter angrep i skyen og pivoterer deretter til lokale, noe som betyr at SecOps-team må undersøke disse angrepene fra flere steder. Ved å kombinere signaler fra skyen og lokale kilder, inkludert Microsoft Cloud App Security, Azure ATP og Azure AD Identity Protection, styrker Microsoft sikkerhetsanalytikere ved å tilby enhetlig identitet og brukerinformasjon, i én enkelt konsoll, og avslutte behovet for å veksle mellom sikkerhetsløsninger. Dette gir SecOps-teamene mer tid og riktig informasjon til å ta bedre beslutninger, og aktivt utbedre de virkelige identitetstruslene og risikoene. Hvis du vil ha mer informasjon, kan du se Unified SecOps Investigation for Hybrid EnvironmentsSandkassefunksjoner for oppdagelse av skadelig programvare (gradvis utrulling)
Cloud App Security sine funksjoner for gjenkjenning av skadelig programvare utvides til å omfatte muligheten til å identifisere nulldags skadelig programvare gjennom avansert sandkasseteknologi.
Som en del av denne funksjonen identifiserer Cloud App Security automatisk mistenkelige filer og detonerer dem for å se etter mistenkelig filvirkemåte og indikatorer på at filen har ondsinnede hensikter (skadelig programvare). Som en del av denne endringen inkluderer policyer for registrering av skadelig programvare nå et gjenkjenningstypefelt som gjør det mulig å filtrere etter trusselintelligens og sandkasse.Oppdateringer for betinget tilgang
Appkontroll for betinget tilgang har lagt til muligheten til å overvåke og blokkere følgende aktiviteter:- Filopplastinger i alle apper – aktivere scenarioer som å forhindre opplasting av kjente utvidelser for skadelig programvare, og sikre at brukere beskytter filer med Azure Information Protection før opplasting.
- Kopier og lim inn i en hvilken som helst app – avrunding av robuste kontroller av dataeksfiltrering som allerede omfattet kontroll av nedlasting, utskrift og egendefinerte aktiviteter, for eksempel deling.
- Send melding – sørg for at personlige data, for eksempel passord, ikke deles i populære samarbeidsverktøy som Slack, Salesforce og Workplace av Facebook.
- Øktpolicyer inkluderer nå innebygde maler for å gjøre det mulig for organisasjonen å aktivere populær sanntidsovervåking og -kontroll over de sanksjonerte appene dine, for eksempel Blokker opplasting basert på innholdsinspeksjon i sanntid.
Cloud App Security utgivelse 143
Utgitt 17. februar 2019
Omfangsdistribusjon for appforekomster
Omfangsdistribusjon kan nå konfigureres på appforekomstnivå, noe som gir større detaljnivå og kontroll.Rolleforbedringer
- Rollene til dataadministratoren og sikkerhetsoperatøren Microsoft 365 støttes nå i Cloud App Security. Dataadministratorrollen gjør det mulig for brukere å administrere alt filrelatert, og vise Cloud Discovery-rapportene. Sikkerhetsoperatorer har tillatelse til å behandle varsler og vise policykonfigurasjon.
- Sikkerhetsleserrollen har nå muligheten til å konfigurere SIEM-agenten, noe som gir bedre tillatelses omfang.
Støtte for Microsoft Flow
Cloud App Security overvåker nå brukeraktiviteter i Microsoft Flow. Aktivitetene som støttes, er aktivitetene som flyt rapporterte til Microsoft 365-overvåkingsloggen.Gruppering av varselenhet
Varselsiden grupperer nå relaterte enheter som var involvert i et varsel for å hjelpe deg med etterforskningen.
Cloud App Security utgivelse 142
Utgitt 3. februar 2019
Konfigurasjon av øktpolicy i Azure AD
Nå kan du konfigurere øktpolicyer for å overvåke brukere eller blokkere nedlastinger i sanntid, direkte i Azure AD betinget tilgang. Du kan fortsatt konfigurere avanserte øktpolicyer direkte i Cloud App Security. Hvis du vil ha mer informasjon, kan du se Beskytt apper med Microsoft Defender for Cloud Apps appkontroll for betinget tilgang.Foreslåtte og lagrede spørringer for OAuth-apper
Foreslåtte spørringer er lagt til på OAuth-appsiden, og inneholder forhåndsdefinerte undersøkelsesmaler for å filtrere OAuth-appene. Foreslåtte spørringer inkluderer egendefinerte filtre for å identifisere risikable apper, for eksempel apper som er autorisert av administratorer. Lagrede spørringer gjør det mulig å lagre egendefinerte spørringer for fremtidig bruk, på samme måte som lagrede spørringer som er tilgjengelige i dag i aktivitetsloggen og oppdagingssidene.Standardkonfigurasjon for Microsoft 365-overvåking
Hvis du vil aktivere overvåking av Microsoft 365-aktiviteter i Cloud App Security, må du nå aktivere overvåking i sikkerhets- og samsvarssenteret for Office, dette er et resultat av en endring i Microsoft 365-overvåking. Denne endringen må bare utføres hvis du ikke allerede har aktivert overvåking av Microsoft 365-aktiviteter i Cloud App Security.Støtte for Utvidet boks
Cloud App Security støtter nå to nye styringshandlinger for Box:Utløp av delt kobling – denne styringshandlingen gir deg muligheten til å angi en utløpsdato for en delt kobling, og deretter vil den ikke lenger være aktiv.
Endre tilgangsnivå for delingskobling – Denne styringshandlingen gir deg muligheten til å endre tilgangsnivået for den delte koblingen mellom bare firmaet, bare samarbeidspartnere og offentligheten.
Støtte for flere plasseringer i OneDrive
Cloud App Security gir nå full innsyn i OneDrive-filer, selv om de er spredt over flere geografiske plasseringer. Beskyttelse er nå tilgjengelig for filer som er plassert på de ekstra plasseringene og hovedplasseringen.Forbedring av portalnavigasjon
Den Cloud App Security portalen ble forbedret for å gi bedre navigering og bedre justering Cloud App Security med Microsofts andre sikkerhetstjenester, for strømlinjeformet brukervennlighet.
Cloud App Security utgivelse 141
Utgitt 20. januar 2019
Forbedringer for risikovurdering i skyen
- Risikovurdering for skyapp ble forbedret med to nye opplevelser.
- Et nytt datatypeattributt vurderer hva slags innhold brukere kan laste opp til appen. Du kan bruke dette attributtet til å vurdere en app i henhold til følsomheten til hver datatype i organisasjonen.
- For å få en mer omfattende risikooversikt over en app, kan du nå enkelt bla fra appens risikovurdering til risikovurderingen av vertsselskapet ved å klikke på vertsfirmaattributtet .
- Risikovurdering for skyapp ble forbedret med to nye opplevelser.
Forbedret filkontekst for varslingsundersøkelse for avviksregistrering
- Avviksregistreringsundersøkelsen ble forbedret, slik at du kan se mer innsikt knyttet til filene som er involvert i et varsel. Når varsler utløses for filrelaterte uvanlige aktivitetsvarsler (Last ned, Del, Slett), er denne neddrillingen tilgjengelig. Hvis de fleste av de berørte filene for eksempel er fra samme mappe eller deler samme filtype, ser du denne innsikten i delen Ekstra risiko i varselet.
Spørringer for filundersøkelse
- Cloud App Security mulighet til å opprette og lagre egendefinerte spørringer ble utvidet til Filer-siden. Spørringer på Fil-siden lar deg opprette spørringsmaler som kan brukes på nytt for grundig undersøkelse.
Cloud App Security utgivelse 139, 140
Utgitt 6. januar 2019
Endring i filgjenkjenning
Filer som deles med alle i SharePoint og One Drive, anses nå som internepå grunn av endringer i SharePoint og One Drive. Så hvis en fil oppdages som er delt med alle, behandles den nå som en intern fil– dette påvirker hvordan filen håndteres av policyer og vises på filsiden.Endring i filovervåking
Standard virkemåte for filovervåking endret for nye og inaktive kunder. Nå må du aktivere filovervåking for å aktivere funksjonen via Innstillinger-filer>. Eksisterende aktive kunder påvirkes ikke av denne endringen.Avansert justering for policyer for avviksregistrering
Nå kan du påvirke avviksregistreringsmotoren for å undertrykke eller vise varsler i henhold til preferansene dine.- I policyen for umulig reise kan du angi glidebryteren for følsomhet for å bestemme nivået av uregelmessig atferd som kreves før et varsel utløses.
- Du kan også konfigurere om varslene for aktivitet fra sjeldne land/område, anonyme IP-adresser, mistenkelige IP-adresser og umulige reiser skal analysere både mislykkede og vellykkede pålogginger eller bare vellykkede pålogginger.
Støtte for flere klareringskjeder
Appkontroll for betinget tilgang støtter nå tillegging og bruk av flere klarerte rot- eller mellomliggende sertifikater som en form for enhetsbehandling.Ny Cloud Discovery-rolle (gradvis utrulling)
Cloud App Security gir nå en ny administratorrolle for Brukere av Cloud Discovery. Denne rollen kan brukes for å begrense tilgangen til en administratorbruker til bare Innstillinger for cloud discovery og data i Cloud App Security-portalen.Støtte for Microsoft Purview informasjonsbeskyttelse enhetlige etiketter (gradvis utrulling)
Cloud App Security støtter nå Microsoft Purview informasjonsbeskyttelse enhetlige etiketter. For kunder som allerede har overført klassifiseringsetikettene sine for Sikkerhets- og samsvarssenter for Microsoft 365, vil Cloud App Security identifisere og arbeide med disse etikettene som beskrevet i integrering med Azure Information Protection.
Støtte for PDF-filmerking (gradvis utrulling)
For kunder som bruker enhetlige etiketter, støtter Cloud App Security nå automerking for PDF-filer.
Oppdateringer laget i 2018
Cloud App Security utgivelse 138
Utgitt 9. desember 2018
Automatisk loggopplasting ved hjelp av Docker på Windows
Cloud App Security støtter nå automatisk loggopplasting for Windows 10 (fall creators update) og Windows Server, versjon 1709 og nyere ved hjelp av Docker for Windows. Hvis du vil ha mer informasjon og instruksjoner om hvordan dette kan konfigureres, kan du se Docker lokalt i Windows.Cloud App Security integreres med Microsoft Flow for å gi egendefinerte strategibøker for varslingsautomatisering og -orkestrering. Hvis du vil ha mer informasjon og instruksjoner for integrering, kan du se Integrere med Microsoft Flow.
Cloud App Security utgivelse 137
Utgitt 25. november 2018
Lagt til støtte for Dynamics
Cloud App Security inkluderer nå støtte for Microsoft Dynamics-aktivitetene som støttes i microsoft 365-overvåkingsloggen.Skanner kryptert innhold (forhåndsversjon)
Cloud App Security gjør det nå mulig å skanne innhold som er beskyttet av Azure Information Protection beskyttelsesetiketter. Dette gjør at du kan finne sensitivt innhold, selv i filer som allerede er kryptert av Azure Information Protection.Heads up – ny terminologi!
Navnet på apptillatelsesfunksjonene ble endret for klarhet – det kalles nå OAuth-apper.
Cloud App Security utgivelse 136
Utgitt 11. november 2018
Oppdateringer for Cloud Discovery
Den egendefinerte logganalysen ble forbedret for å støtte ekstra og mer komplekse netttrafikkloggformater. Som en del av disse forbedringene kan brukere nå skrive inn egendefinerte overskrifter for hodeløse CSV-loggfiler, bruke spesielle skilletegn for nøkkelverdifiler, behandle Syslog-filformat og mer.Nye policyer for avviksregistrering
Mistenkelige regler for innboksmanipulering: Denne policyen profilerer miljøet ditt og utløser varsler når mistenkelige regler som sletter eller flytter meldinger eller mapper er angitt i en brukers innboks. Dette kan indikere at brukerens konto er kompromittert, at meldinger skjules med hensikt, og at postboksen brukes til å distribuere søppelpost eller skadelig programvare i organisasjonen.Støtte for grupper i apptillatelsespolicyer
Cloud App Security gir deg nå muligheten til å definere policyer for apptillatelse mer detaljert, basert på gruppemedlemskapene til brukerne som godkjente appene. En administrator kan for eksempel bestemme seg for å angi en policy som tilbakekaller uvanlige apper hvis de ber om høye tillatelser, bare hvis brukeren som godkjente tillatelsene, er medlem av administratorgruppen.Appkontroll for betinget tilgang integreres nå med lokale apper via Azure Active Directory-Programproxy
- Den Azure AD Programproxy gir enkel pålogging og sikker ekstern tilgang for nettappene som driftes lokalt.
- Disse lokale nettappene kan nå rutes til Microsoft Cloud App Security via Azure AD betinget tilgang for å gi overvåking og kontroller i sanntid, via tilgangs- og øktpolicyer.
Cloud App Security utgivelse 133, 134, 135
Utgitt oktober 2018
Nye policyer for avviksregistrering rulles gradvis ut
- Den nye policyen for datautfiltrering til apper som ikke er helliggjort, aktiveres automatisk for å varsle deg når en bruker eller IP-adresse bruker en app som ikke er godkjent for å utføre en aktivitet som ligner på et forsøk på å eksfiltrere informasjon fra organisasjonen.
- Den nye policyen for flere slettede VM-aktiviteter profilerer miljøet ditt og utløser varsler når brukere sletter flere vm-er i én enkelt økt, i forhold til grunnlinjen i organisasjonen.
- Den nye policyen for datautfiltrering til apper som ikke er helliggjort, aktiveres automatisk for å varsle deg når en bruker eller IP-adresse bruker en app som ikke er godkjent for å utføre en aktivitet som ligner på et forsøk på å eksfiltrere informasjon fra organisasjonen.
Dataklassifiseringstjeneste tilgjengelig for APAC
- Innholdsinspeksjon av dataklassifiseringstjeneste er nå tilgjengelig for APAC-kunder. Hvis du vil ha en liste over fullstendig regional støtte, kan du se Integrering av Microsoft Data Classification Services.
Cloud Discovery-støtte for i-Filter
- Funksjonen Cloud App Security Cloud Discovery har nå forbedret støtte for i-Filter syslog-parseren.
Cloud App Security utgivelse 132
Utgitt 25. september 2018
Appkontroll for betinget tilgang for Microsoft 365 er nå i offentlig forhåndsversjon
- Appkontroll for betinget tilgang støtter nå også Microsoft 365 og alle apper som er konfigurert med Open ID Connect.
- Gi tilbakemelding fra en økt: Med dette nye verktøyet kan du gi tilbakemelding til Cloud App Security team om ytelsen til et program under øktkontroll, direkte fra økten.
Opprinnelig integrering med Microsoft Defender ATP for Shadow IT Discovery utover korpsen din
- Microsoft Cloud App Security integreres nå opprinnelig med Windows Defender Advanced Threat Protection (ATP) for å gi distribusjonsløse Shadow IT-oppdagelsesfunksjoner for på og av bedriftens nettverksbruk av skyapper. Dette gjør at du kan utføre Cloud Discovery på maskiner, selv når de ikke er i bedriftsnettverket ditt. Det muliggjør også maskinbasert undersøkelse: Når du har identifisert en risikabel bruker, kan du deretter kontrollere alle maskinene brukeren har åpnet for å oppdage potensielle risikoer. Hvis du identifiserer en risikabel maskin, kan du kontrollere alle brukerne som brukte den til å undersøke potensielle risikoer. Hvis du vil ha mer informasjon, kan du se Windows Defender Advanced Threat Protection-integrering med Microsoft Cloud App Security.
Innholdsinspeksjon for krypterte filer
- Cloud App Security støtter nå innholdsinspeksjon av beskyttede filer som er kryptert som ble beskyttet ved hjelp av Azure Information Protection. Nå kan du undersøke disse krypterte filene for å foreslå omklassifisering og identifisere ekstra brudd på DLP-eksponering og sikkerhetspolicyer.
Cloud App Security utgivelse 131
Utgitt 2. september 2018
Oppheve tillatelser for risikable OAuth-apper automatisk
Nå kan du kontrollere hvilke OAuth-apper brukerne har tilgang til, ved å oppheve apptillatelse for OAuth-apper på Office, Google eller Salesforce. Når du oppretter en apptillatelsespolicy, kan du nå angi policyen for å oppheve tillatelsen til en app.Cloud Discovery ekstra innebygd analyse støttes
Cloud Discovery støtter nå powerpoint Web Security Cloud-loggformatet.
Cloud App Security utgivelse 130
Utgitt 22. august 2018
Ny menylinje
Hvis du vil gi en mer konsekvent administratoropplevelse på tvers av Microsoft 365-produkter og gjøre det enklere å veksle mellom Microsofts sikkerhetsløsninger, flyttes Cloud App Security portalmenylinjen til venstre side av skjermen. Denne konsekvente navigasjonsopplevelsen hjelper deg med å orientere deg når du flytter fra én Microsoft-sikkerhetsportal til en annen.Innvirkning på OAuth-appens poengsum
Nå kan du sende tilbakemeldinger fra Cloud App Security-teamet for å fortelle oss om det er oppdaget en OAuth-app i organisasjonen som virker ondsinnet. Denne nye funksjonen gjør at du kan være en del av sikkerhetsfellesskapet vårt og forbedre risikopoengsummen og -analysen for OAuth-appen. Hvis du vil ha mer informasjon, kan du se Administrere app-permiOAuth-apper.Nye Cloud Discovery-analyser
Cloud Discovery-analyser støtter nå iboss Secure Cloud Gateway og Sophos XG.
Cloud App Security utgivelse 129
Utgitt 5. august 2018
Nye policyer for avviksregistrering – mistenkelige e-postregler
Nye policyer for avviksregistrering ble lagt til som oppdager mistenkelige regler for videresending av e-post, for eksempel hvis en bruker opprettet en innboksregel som videresender en kopi av alle e-postmeldinger til en ekstern adresse.Denne versjonen inneholder løsninger og forbedringer for flere problemer.
Cloud App Security utgivelse 128
Utgitt 22. juli 2018
Handlinger for OAuth-apper på tvers av flere apper
For OAuth-apper som har fått apptillatelser, kan du nå forby eller godkjenne flere apper i én enkelt handling. Du kan for eksempel se gjennom alle appene som er gitt tillatelse av brukere i organisasjonen, velge alle appene du vil forby, og deretter klikke forby apper for å tilbakekalle alt samtykke som er gitt, og vil ikke lenger tillate brukere å gi tillatelse til disse appene. Hvis du vil ha mer informasjon, kan du se Administrere OAuth-apper.Forbedret støtte for Azure programmer
For Azure ruller vi nå gradvis ut muligheten til å oppdage programmer som brukerkontoaktiviteter utført av Azure-programmene (både interne og eksterne). Dette gjør at du kan opprette policyer som varsler deg hvis et program utfører uventede og uautoriserte aktiviteter. Hvis du vil ha mer informasjon, kan du se Koble Azure til Microsoft Cloud App Security.Dataklassifiseringsmotor oppdatert med nye GDPR-sensitive typer
Cloud App Security Data Classification Service la til nye GDPR-sensitive typer i dataklassifiseringsmotoren vår, slik at du kan oppdage GDPR-relatert innhold i filene dine.Oppdateringer til katalogen for skyapper
Katalogen for skyappen inneholder nå en juridisk risikokategori (i tillegg til generell, sikkerhet og samsvar) for å hjelpe deg med å administrere datavern og eierskapssamsvar, inkludert GDPR-beredskap. Den nye risikokategorien inneholder GDPR-klargjøringserklæringen for skytjenesten og statusen for hver GDPR-rammeverkkontroll for å hjelpe til med å vurdere GDPR-klargjøringen for hver skyapp. Som en del av denne forbedringen ble følgende risikoattributter flyttet fra annen risikokategori til kategorien Juridisk:- DMCA
- Dataeierskap
- Policy for dataoppbevaring
I tillegg blir den nye risikokategorien scoret separat, slik at du kan konfigurere vekting av poengsum i henhold til preferanser og prioriteringer. Hvis du vil ha mer informasjon, kan du se Risikopoengsum.
Ny foreslått spørring: GDPR klar
Det finnes en ny foreslått spørring som gjør det mulig å identifisere oppdagede apper som er GDPR klare. Siden GDPR nylig ble en topp prioritet for sikkerhetsadministratorer, hjelper denne spørringen deg med å enkelt identifisere apper som er GDPR-klare og reduserer trusselen ved å vurdere risikoen for de som ikke er det.
Cloud App Security utgivelse 127
Utgitt 8. juli 2018
- Du har nå muligheten til å se generiske aktiviteter for Microsoft 365. I aktivitetsloggen og aktivitetspolicyer kan du nå filtrere Microsoft 365-aktivitetene for uspesifiserte aktiviteter. Hvis du ser gjennom disse aktivitetene, kan du undersøke informasjon om aktiviteter som ennå ikke er klassifisert etter type i Cloud App Security, og du kan bruke disse aktivitetene til å sende forespørsler til Cloud App Security gruppe for å opprette nye aktivitetstyper basert på disse aktivitetene.
Cloud App Security utgivelse 126
Utgitt 24. juni 2018
Kontroll-GA for app for betinget tilgang
Microsoft Cloud App Security appkontroll for betinget tilgang (omvendt proxy) er nå generelt tilgjengelig for alle SAML-programmer. Appkontroll for betinget tilgang integreres direkte med Azure AD policyer for betinget tilgang for å overvåke og kontrollere brukernes økter i sanntid, samtidig som de kan være produktive. Siden første forhåndsvisning av funksjonen har mange funksjoner og forbedringer blitt gjort, inkludert:- Muligheten til å opprette en tilgangspolicy for å administrere tilgang til de samme appene fra opprinnelige klienter, i tillegg til å opprette en øktpolicy for nettlesertrafikk.
- Apppålastingsprosessen ble strømlinjeformet for å støtte egendefinerte SAML-programmer i organisasjonen.
- Som en del av det Azure verdensomspennende nettverket har integreringen og grensesnittet blitt forbedret for en sømløs opplevelse for brukere som befinner seg hvor som helst i verden.
Innholdsinspeksjon med Microsoft Data Classification Service GA
Microsoft Cloud App Security-integrering med Microsoft Data Classification Services er nå generelt tilgjengelig. Denne integreringen gjør det mulig for deg å bruke Microsoft Data Classification Service opprinnelig for å klassifisere filene i skyappene dine. Hvis du vil ha mer informasjon, kan du se Microsoft Data Classification Services-integrering. Denne funksjonen er for øyeblikket bare tilgjengelig i USA og Europa (unntatt Frankrike).Cloud Discovery-rapport
Microsoft Cloud App Security ruller gradvis ut muligheten til å generere en cloud discovery executive PDF-rapport. Denne rapporten gir en oversikt over Shadow IT-bruken som ble identifisert i organisasjonen, som fremhever de beste appene og brukerne i bruk generelt og i ledende kategorier, og fokuserer på risikoen som Shadow IT utgjør i organisasjonen. I tillegg gir rapporten en liste over anbefalinger for hvordan du kan forbedre synligheten til, og kontrollere, Skygge IT i organisasjonen. Bruk denne rapporten til å sikre at potensielle risikoer og trusler fjernes, og at organisasjonen forblir trygg og sikker.Gjenkjenning av skadelig programvare
Funksjonen for gjenkjenning av skadelig programvare rulles gradvis ut som automatisk oppdager skadelige filer i skylagringen, uavhengig av filtypen. Microsoft Cloud App Security bruker Microsofts trusselintelligens til å gjenkjenne om visse filer er knyttet til kjente angrep fra skadelig programvare eller potensielt skadelige. Hvis du vil ha mer informasjon, kan du se policyer for avviksregistrering.Automatisert utbedring for mistenkelige aktiviteter
Nå kan du angi automatiske utbedringshandlinger for mistenkelig økt utløst av policyene for avviksregistrering. Denne forbedringen gjør at du kan bli varslet umiddelbart når et brudd oppstår og bruke styringshandlinger automatisk, for eksempel avbryte brukeren. Hvis du vil ha mer informasjon, kan du se policyer for avviksregistrering.Vurdering av sikkerhetskonfigurasjon for Azure
Microsoft Cloud App Security ruller gradvis ut muligheten til å få en sikkerhetskonfigurasjonsvurdering av Azure miljøet, og gir anbefalinger for manglende konfigurasjon og sikkerhetskontroll. Den gir deg for eksempel beskjed om du mangler MFA for administrative brukere. Hvis du vil ha mer informasjon, kan du se Integrering av Cloud Security Posture Management.Automatisert gjenkjenning av risikable OAuth-apper
I tillegg til den eksisterende undersøkelsen av OAuth-apper som er koblet til miljøet ditt, ruller Microsoft Cloud App Security nå gradvis ut muligheten til å angi automatiserte varsler for å gi deg beskjed når en OAuth-app oppfyller bestemte kriterier. Du kan for eksempel automatisk bli varslet når det finnes apper som krever et høyt tilgangsnivå og ble godkjent av mer enn 50 brukere. Hvis du vil ha mer informasjon, kan du se policyer for apptillatelser.Administrasjonsstøtte for administrert sikkerhetstjenesteleverandør (MSSP)
Microsoft Cloud App Security gir nå en bedre administrasjonsopplevelse for MSSP-er. Eksterne brukere kan nå konfigureres som administratorer og tilordnes alle rollene som er tilgjengelige i Microsoft Cloud App Security. For å gjøre det mulig for mssps å tilby tjenester på tvers av flere kundeleier, kan administratorer som har tilgangsrettigheter til mer enn én leier, nå enkelt bytte leiere i portalen. Hvis du vil ha informasjon om administrasjon av administratorer, kan du se Administrere administratorer.Integrering med ekstern DLP GA
Microsoft Cloud App Security lar deg bruke eksisterende investeringer i tredjeparts klassifiseringssystemer, for eksempel DLP-løsninger (Data Loss Prevention), og lar deg skanne innholdet i skyprogrammer ved hjelp av eksisterende distribusjoner som kjører i miljøet ditt. Hvis du vil ha mer informasjon, kan du se Ekstern DLP-integrering.
Cloud App Security utgivelse 125
Utgitt 10. juni 2018
Ny undersøkelsesfunksjonalitet for toppbrukere:
Microsoft Cloud App Security lagt til et nytt undersøkelseskort på instrumentbordet som viser de beste brukerne etter antall åpne varsler om trusselregistrering. Med dette undersøkelseskortet kan du fokusere trusselundersøkelsen på brukere med høyest antall mistenkelige økter.Støtte for AWS S3-samlinger:
Microsoft Cloud App Security kan nå oppdage AWS S3-samlinger og delingsnivåer. Dette gir varsler og innsyn i offentlig tilgjengelige AWS-samlinger. Dette gjør det også mulig å opprette policyer basert på samlinger og bruke automatisk styring. I tillegg finnes det en ny policymal som kalles Offentlig tilgjengelige S3-samlinger (AWS) som du kan bruke til enkelt å opprette en policy for å styre AWS-lagring. Hvis du vil aktivere disse nye funksjonene, må du sørge for at du oppdaterer AWS-tilkoblede apper ved å legge til de nye tillatelsene som er beskrevet i Connect AWS.Admin rettigheter basert på brukergrupper:
Nå kan du angi administrative tillatelser til Microsoft Cloud App Security-administratorer per brukergruppe. Du kan for eksempel angi en bestemt bruker som administrator bare for brukere i Tyskland. Dette gjør det mulig for brukeren å vise og endre informasjon i Microsoft Cloud App Security bare for brukergruppen «Tyskland – alle brukere». Hvis du vil ha mer informasjon, kan du se Administrere administratortilgang.
Cloud App Security utgivelse 124
Utgitt 27. mai 2018
GDPR-risikovurdering lagt til i katalogen for skyapper
13 nye risikofaktorer ble lagt til Microsoft Cloud App Security. Disse risikofaktorene følger sjekklisten for GDPR-rammeverket for å gjøre det mulig for deg å vurdere appene i cloud app-katalogen i henhold til GDPR-forskriftene.Integrer med Microsoft Data Classification Service
Microsoft Cloud App Security gjør det nå mulig å bruke Microsoft Data Classification Service opprinnelig for å klassifisere filene i skyappene dine. Microsoft Data Classification Service gir en enhetlig informasjonsbeskyttelsesopplevelse på tvers av Microsoft 365, Azure Information Protection og Microsoft Cloud App Security. Den lar deg utvide det samme rammeverket for dataklassifisering til tredjeparts skyapper som er beskyttet av Microsoft Cloud App Security, ved å ta i bruk beslutningene du allerede har tatt på tvers av et enda større antall apper.Koble til Microsoft Azure (gradvis utrulling)
Microsoft Cloud App Security utvider sine IaaS-overvåkingsfunksjoner utover Amazon Web Services og støtter nå Microsoft Azure. Dette gjør at du sømløst kan koble til og overvåke alle Azure abonnementer med Cloud App Security. Denne tilkoblingen gir deg et kraftig sett med verktøy for å beskytte Azure miljøet, inkludert:Innsyn i alle aktiviteter som utføres gjennom portalen
Muligheten til å opprette egendefinerte policyer for å varsle om uønsket virkemåte, og muligheten til automatisk å beskytte mulige risikable brukere ved å suspendere eller tvinge dem til å logge på igjen.
Alle Azure aktiviteter dekkes av avviksregistreringsmotoren vår og varsler automatisk om mistenkelig oppførsel i Azure Portal, for eksempel umulig reise, mistenkelige masseaktiviteter og aktivitet fra et nytt land/område.
Hvis du vil ha mer informasjon, kan du se Koble Azure til Microsoft Cloud App Security.
Omfangsdistribusjoner (gradvis utrulling)
Microsoft Cloud App Security gir virksomheter muligheten til å bestemme detaljert hvilke brukere de vil overvåke og beskytte basert på gruppemedlemskap. Med denne funksjonen kan du velge brukere som ikke har aktiviteter som ikke vil vises for noen av de beskyttede programmene. Omfangsovervåkingsfunksjonen er spesielt nyttig for:- Samsvar – Hvis samsvarsforskriftene krever at du avstår fra å overvåke brukere fra visse land/regioner på grunn av lokale forskrifter.
- Lisensiering – Hvis du vil overvåke færre brukere for å holde seg innenfor grensene for Microsoft Cloud App Security-lisensene dine. Hvis du vil ha mer informasjon, kan du se Omfangsdistribusjon.
Varsel om brudd på appen for oppdagede apper
Vi har nå et innebygd varsel for å varsle deg når noen av appene som er oppdaget av en leier, er brutt. Varselet gir informasjon om tidspunktet og datoen for bruddet, hvilke brukere som brukte appen, og vil koble til offentlig tilgjengelige kilder som gir informasjon om bruddet.Ny e-postserver
Cloud App Security e-postserveren er endret og bruker ulike IP-adresseområder. Hvis du vil forsikre deg om at du kan få varsler, kan du legge til de nye IP-adressene i listen over tillatelser for søppelpost. Microsoft Cloud App Security aktiverer dette for brukere som tilpasser varslene sine, slik at du kan bruke MailChimp®, en tredjeparts e-posttjeneste. Hvis du vil se listen over IP-adresser for e-postserveren og instruksjoner for aktivering av arbeid med MailChimp, kan du se Nettverkskrav og E-postinnstillinger.
Cloud App Security utgivelse 123
Utgitt 13. mai 2018
-
Avviksregistreringspolicy for omfang:
Policyene for avviksregistrering kan nå begrenses. Dette gjør at du kan angi at hver policy for avviksregistrering bare skal inkludere bestemte brukere eller grupper, og utelate bestemte brukere eller grupper. Du kan for eksempel angi aktivitet fra sjelden fylkesgjenkjenning til å ignorere en bestemt bruker som reiser ofte.
Cloud App Security utgivelse 122
Utgitt 29. april 2018
Gradvis utrulling: Du kan nå angi administrative tillatelser til Microsoft Cloud App Security administratorer per app. Du kan for eksempel angi en bestemt bruker som administrator bare for G Suite. Dette gjør det mulig for brukeren å vise og endre informasjon i Microsoft Cloud App Security bare når den er knyttet utelukkende til G Suite. Hvis du vil ha mer informasjon, kan du se Administrere administratortilgang.
Gradvis utrulling: Okta-administratorroller er nå synlige i Microsoft Cloud App Security og er tilgjengelige for hver rolle som en kode underBrukergrupper for innstillinger>.
Cloud App Security utgivelse 121
Utgitt 22. april 2018
Den offentlige forhåndsvisningen av appkontroll for betinget tilgang (tidligere kjent som Cloud App Security Proxy) er forbedret med funksjoner som gir dypere innsyn i og kontroll over ulike programmer. Nå kan du opprette en øktpolicy med et aktivitetstypefilter , for å overvåke og blokkere ulike appspesifikke aktiviteter. Dette nye filteret utvider de eksisterende funksjonene for filnedlastingskontroll for å gi deg omfattende kontroll over programmene i organisasjonen og fungerer hånd i hånd med Azure Betinget tilgang i Active Directory for å gi synlighet og kontroll over risikable brukerøkter i sanntid, for eksempel økter med B2B-samarbeidsbrukere eller brukere som kommer fra en uadministrert enhet. Hvis du vil ha mer informasjon, kan du se Øktpolicyer.
Gradvis utrulling: Cloud App Security policyer for avviksregistrering er forbedret til å omfatte to nye typer trusselregistrering: Løsepengevirusaktivitet og avsluttet brukeraktivitet. Cloud App Security utvidet sine ransomware deteksjon evner med avvik deteksjon for å sikre en mer omfattende dekning mot sofistikerte Ransomware angrep. Ved hjelp av vår ekspertise for sikkerhetsforskning for å identifisere atferdsmønstre som gjenspeiler løsepengevirusaktivitet, sikrer Cloud App Security helhetlig og robust beskyttelse. Avsluttet brukeraktivitet gjør det mulig å overvåke kontoene til avsluttede brukere, som kan ha blitt avsluttet fra firmaapper, men i mange tilfeller beholder de fortsatt tilgangen til bestemte firmaressurser. Hvis du vil ha mer informasjon, kan du se Få øyeblikkelig atferdsanalyse og avviksregistrering.
Cloud App Security utgivelse 120
Utgitt 8. april 2018
For Microsoft 365 og Azure AD ruller vi nå gradvis ut muligheten til å oppdage interne programmer som brukerkontoaktiviteter utført av Microsoft 365- og Azure AD-programmer (både interne og eksterne). Dette gjør at du kan opprette policyer som varsler deg hvis et program utfører uventede og uautoriserte aktiviteter.
Når du eksporterer en liste over apptillatelser til CSV, inkluderes ekstra felt som utgiver, tillatelsesnivå og fellesskapsbruk for å hjelpe til med prosessen for overholdelse og undersøkelse.
Den tilkoblede ServiceNow-appen ble forbedret, slik at interne tjenesteaktiviteter ikke lenger registreres som utført av «Gjest» og ikke lenger utløser falske positive varsler. Disse aktivitetene representeres nå som I/T som alle andre tilkoblede apper.
Cloud App Security utgivelse 119
Utgitt 18. mars 2018
Siden for IP-adresseområder inneholder innebygde IP-adresser som oppdages av Cloud App Security. Dette inkluderer IP-adresser for identifiserte skytjenester, for eksempel Azure og Microsoft 365, og trusselintelligensfeeden som automatisk beriker IP-adresser med informasjon om kjente risikable IP-adresser.
Når Cloud App Security forsøker å kjøre en styringshandling på en fil, men mislykkes fordi filen er låst, vil den nå automatisk prøve styringshandlingen på nytt.
Cloud App Security utgivelse 118
Utgitt 4. mars 2018
Du kan nå dra nytte av Microsoft Cloud App Security skygge-IT-oppdagelses- og overvåkingsfunksjoner på dine egne proprietære egendefinerte apper. Den nye muligheten til å legge til egendefinerte apper i Cloud Discovery gjør det mulig å overvåke appbruk og bli varslet om endringer i bruksmønsteret. Hvis du vil ha mer informasjon, kan du se Beskytte egendefinerte apper. Denne funksjonen rulles gradvis ut.
Innstillingssidene for Cloud App Security-portalen ble utformet på nytt. Den nye utformingen konsoliderer alle innstillingssidene, gir søkefunksjonalitet og en forbedret utforming.
Cloud Discovery støtter nå Barracuda F-serie brannmurer og Barracuda F-serien Firewall Web Log Streaming.
Søkefunksjonaliteten på bruker- og IP-adressesidene gjør det nå mulig for autofullføring å gjøre det enklere for deg å finne det du leter etter.
Nå kan du utføre massehandlinger på sidene Utelat enheter og Utelat IP-adresseinnstillinger. Dette gjør det enklere for deg å velge flere brukere eller IP-adresser og utelate dem fra å bli overvåket som en del av Cloud Discovery i organisasjonen.
Cloud App Security utgivelse 117
Utgitt 20. februar 2018
Cloud App Security dypere integrering med Azure Information Protection gjør det nå mulig å beskytte filer i G Suite. Med denne offentlige forhåndsvisningsfunksjonen kan du skanne og klassifisere filer i G Suite, og automatisk bruke Azure Etiketter for beskyttelse av informasjon for beskyttelse. Hvis du vil ha mer informasjon, kan du se Azure Information Protection integrering.
Cloud Discovery støtter nå Digital Arts i-FILTER.
Siem-agenttabellen inneholder nå flere detaljer for enklere administrasjon.
Cloud App Security utgivelse 116
Utgitt 4. februar 2018
Cloud App Security sin policy for avviksregistrering ble forbedret med nye scenariobaserte oppdagelser, inkludert umulig reise, aktivitet fra en mistenkelig IP-adresse og flere mislykkede påloggingsforsøk. De nye policyene aktiveres automatisk, noe som gir forhåndsdefinert trusselregistrering på tvers av skymiljøet. I tillegg viser de nye policyene mer data fra Cloud App Security-gjenkjenningsmotoren, for å hjelpe deg med å øke hastigheten på undersøkelsesprosessen og inneholde pågående trusler. Hvis du vil ha mer informasjon, kan du se Få øyeblikkelig atferdsanalyse og avviksregistrering.
Gradvis utrulling: Cloud App Security korrelerer nå mellom brukere og kontoene deres på tvers av SaaS-apper. Dette gjør at du enkelt kan undersøke alle aktivitetene for en bruker, på tvers av alle de ulike korrelerte SaaS-appene, uansett hvilken app eller konto de brukte.
Gradvis utrulling: Cloud App Security støtter nå flere forekomster av den samme tilkoblede appen. Hvis du for eksempel har flere forekomster av Salesforce (én for salg, én for markedsføring), kan du koble dem til både for å Cloud App Security og administrere dem fra samme konsoll for å opprette detaljerte policyer og dypere undersøkelser.
Cloud Discovery-analyser støtter nå to ekstra checkpoint-formater, XML og KPC.
Cloud App Security utgivelse 115
Utgitt 21. januar 2018
- Denne utgivelsen gir en forbedret opplevelse når du velger bestemte mapper i filpolicyer. Nå kan du enkelt vise og velge flere mapper som skal inkluderes i en policy.
- På siden Oppdagede apper :
- Med funksjonen for massemerking kan du bruke egendefinerte koder (i tillegg til sanksjonerte og ikke-helliggjorte merker).
- Når du genererer en IP-adresserapport, eller generer en bruker, kan du rapportere at de eksporterte rapportene nå inneholder informasjon om hvorvidt trafikken var fra godkjente eller ikke-godkjente apper.
- Nå kan du be om en ny API-appkobling fra Microsoft Cloud App Security-teamet direkte i portalen, fra siden Koble til en app.
Cloud App Security utgivelse 114
Utgitt 7. januar 2018
Fra og med versjon 114 ruller vi gradvis ut muligheten til å opprette og lagre egendefinerte spørringer i sidene Aktivitetslogg og Oppdagede apper. Med egendefinerte spørringer kan du opprette filtermaler som kan brukes på nytt for grundig undersøkelse. I tillegg er foreslåtte spørringer lagt til for å gi forhåndsdefinerte undersøkelsesmaler for å filtrere aktiviteter og oppdagede apper. De foreslåtte spørringene inkluderer egendefinerte filtre for å identifisere risikoer som representasjonsaktiviteter, administratoraktiviteter, risikable ikke-kompatile skylagringsapper, bedriftsapper med svak kryptering og sikkerhetsrisikoer. Du kan bruke foreslåtte spørringer som utgangspunkt, endre dem slik du ønsker, og deretter lagre dem som en ny spørring. Hvis du vil ha mer informasjon, kan du se Aktivitetsfiltre og spørringer og Oppdagede appfiltre og spørringer.
Du kan nå kontrollere gjeldende Cloud App Security tjenestestatus ved å gå status.cloudappsecurity.com eller direkte fra portalen ved å klikkestatus for hjelpesystemet>.
Oppdateringer laget i 2017
Cloud App Security utgivelse 113
Utgitt 25. desember 2017
Vi er glade for å kunngjøre at Cloud App Security nå støtter dypere integrering med Azure Information Protection. Med denne offentlige forhåndsvisningsfunksjonen kan du skanne og klassifisere filer i skyapper, og automatisk bruke Azure etiketter for beskyttelse av informasjon for beskyttelse. Denne funksjonen er tilgjengelig for Box, SharePoint og OneDrive. Hvis du vil ha mer informasjon, kan du se Azure Information Protection integrering.
Cloud Discovery-logganalyser støtter nå generiske formater: LEEF, CEF og W3C.
Cloud App Security utgivelse 112
Utgitt 10. desember 2017
- Nå kan du få tilgang til den relevante innsiktsskuffen ved å klikke på et brukernavn eller en IP-adresse i aktivitetsloggen.
- Når du undersøker aktiviteter, kan du nå enkelt vise alle aktiviteter i samme tidsperiode fra innsiktsskuffen ved å klikke på klokkeikonet. Med klokkeikonet kan du vise alle aktiviteter som er utført innen 48 timer etter aktiviteten du viser.
- Det ble gjort forbedringer i logganalysen for Cloud Discovery for Juniper SRX.
- For aktiviteter som overvåkes av proxyen, ble Aktivitet-objektet utvidet til å omfatte informasjon som er relevant for DLP-skanninger. Samsvarende policyer ble utvidet til å omfatte DLP-brudd hvis de finnes.
Cloud App Security utgivelse 111
Utgitt 26. november 2017
Oppdagelsespolicyer støtter nå appkoder som en betingelse og som en styringshandling. I tillegg kan du automatisk merke nylig oppdagede apper med egendefinerte koder, for eksempel populære apper. Du kan også bruke appkoden som et filter. «Varsle meg når en app i visningslisten» har mer enn 100 brukere på én enkelt dag.
Tidsfilteret ble forbedret for å gjøre det mer brukervennlig.
Med innholdsinspeksjon kan du nå skille mellom innhold, metadata og filnavn, slik at du kan velge hva du vil undersøke.
En ny styringshandling ble lagt til for G Suite. Nå kan du redusere offentlig tilgang til delte filer. Med denne handlingen kan du angi at offentlig tilgjengelige filer bare skal være tilgjengelige med en delt kobling.
Alle OKTA-påloggingsaktiviteter til andre programmer vises nå i Cloud App Security med opprinnelse fra OKTA. Du kan vise og filtrere basert på målprogrammet som påloggingen ble utført i aktivitetsobjektfeltet for aktiviteten.
Cloud App Security utgivelse 110
Utgitt 12. november 2017
Nå generelt tilgjengelig: Vi begynner å rulle ut en ny distribusjonsmodus for loggsamleren. I tillegg til den nåværende virtuelle apparatbaserte distribusjonen, kan den nye Docker (beholder) baserte loggsamleren installeres som en pakke på Ubuntu-maskiner både lokalt og i Azure. Når du bruker Docker, eies vertsmaskinen av kunden, som fritt kan oppdatere og overvåke den.
Når du bruker det nye blå spørsmålstegnet i hjørnet, kan du nå få tilgang til den relevante Cloud App Security dokumentasjonssiden fra sidene i portalen. Hver kobling er kontekstavhengig og tar deg til informasjonen du trenger, basert på siden du er på.
Nå kan du sende tilbakemeldinger fra alle sidene i Cloud App Security-portalen. Med tilbakemelding kan du rapportere feil, be om nye funksjoner og dele opplevelsen direkte med Cloud App Security-teamet.
Forbedringer ble gjort i cloud discovery-muligheten til å gjenkjenne underdomener for dypdykksundersøkelser i organisasjonens skybruk. Hvis du vil ha mer informasjon, kan du se Arbeide med oppdagede apper.
Cloud App Security utgivelse 109
Utgitt 29. oktober 2017
Utrulling av proxy-funksjoner for Microsoft Cloud App Security har startet. Microsoft Cloud App Security-proxyen gir deg verktøyene du trenger for å få synlighet og kontroll over tilgangen til skymiljøet i sanntid, og aktiviteter i den. Eksempel:
- Unngå datalekkasjer ved å blokkere nedlastinger før de skjer.
- Angi regler som tvinger data som er lagret i og lastet ned fra skyen, til å beskyttes med kryptering.
- Få innsyn i ubeskyttede endepunkter, slik at du kan overvåke hva som gjøres på uadministrerte enheter.
- Kontroller tilgang fra ikke-innlemmede nettverk eller risikable IP-adresser.
Hvis du vil ha mer informasjon, kan du se Beskytte apper med appkontroll for betinget tilgang.
Vi ruller gradvis ut muligheten til å filtrere i henhold til bestemte tjenesteaktivitetsnavn. Dette nye aktivitetstypefilteret er mer detaljert, slik at du kan overvåke bestemte appaktiviteter, i motsetning til mer generelle aktivitetstyper. Tidligere kunne du for eksempel filtrere etter Kjør-kommandoen, og nå kan du filtrere etter bestemte EXO-cmdleter. Aktivitetsnavnet kan også vises i aktivitetsskuffen under Type (i app). Denne funksjonen vil etter hvert erstatte aktivitetstypefilteret.
Cloud Discovery støtter nå Cisco ASA med FirePOWER.
Ytelsesforbedringer ble gjort på discovery-bruker- og IP-sidene for å forbedre brukeropplevelsen.
Cloud App Security utgivelser 105, 106, 107, 108
Utgitt september/oktober 2017
- Cloud App Security inkluderer nå et datasenter i EU. I tillegg til vårt amerikanske datasenter gjør EUs datasenter det mulig for Cloud App Security kunder å være i fullstendig samsvar med nye og kommende europeiske standardiseringer og sertifiseringer.
- Nye filtre ble lagt til på appkoblingssiden som gir deg enklere filtrering og ekstra innsikt.
- Cloud Discovery på loggfiler som bare har MÅL-IP-informasjon, ble forbedret.
Cloud App Security utgivelse 104
Utgitt 27. august 2017
- Nå kan du legge til IP-områder samtidig ved å opprette et skript ved hjelp av API-en for IP-adresseområder. API-en finner du fra menylinjen i Cloud App Security portalen ved å klikke spørsmålstegnet og deretter API-dokumentasjonen.
- Cloud Discovery gir nå bedre synlighet for blokkerte transaksjoner, ved å presentere både de totale transaksjonene og de blokkerte transaksjonene.
- Nå kan du filtrere skyprogrammer basert på om de er sertifisert med ISO 27017. Denne nye risikofaktoren for skyappkatalogen bestemmer om programleverandøren har denne sertifiseringen. ISO 27017 etablerer vanlige godtatte kontroller og retningslinjer for behandling og beskyttelse av brukerinformasjon i et offentlig databehandlingsmiljø i skyen.
- For å gjøre det mulig for deg å forberede deg på GDPR-samsvar, samlet vi gdpr-klargjøringserklæringene fra skyappene i Cloud App Catalog. Det påvirker ennå ikke apprisikoresultatet, men gir deg en kobling til apputgiverens GDPR-klargjøringsside når den er angitt. Microsoft har ikke bekreftet dette innholdet og er ikke ansvarlig for gyldigheten.
Cloud App Security utgivelse 103
Utgitt 13. august 2017
Cloud App Security lagt til Azure Information Protection opprinnelig beskyttelsesstøtte for følgende Office-filer :docm, .docx, .dotm, .dotx, .xlam, .xlsb, .xlsm, .xlsx, .xltx, .xps, .potm, .potx, .ppsx, .ppsm, .pptm, .pptx, .thmx, .vsdx, .vsdm, .vssx, .vssm, .vstx, .vstm (i stedet for generisk beskyttelse).
Alle Azure active directory-samsvarsadministratorer får automatisk lignende tillatelser i Cloud App Security. Tillatelser omfatter muligheten til å skrivebeskytte og behandle varsler, opprette og endre filpolicyer, tillate filstyringshandlinger og vise alle de innebygde rapportene under dataadministrasjon.
Vi utvidet konteksten for DLP-brudd fra 40 til 100 tegn for å hjelpe deg med å forstå konteksten til bruddene bedre.
Detaljerte feilmeldinger til den egendefinerte loggopplasteren for skysøk, slik at du enkelt kan feilsøke feil i loggopplasting.
Skriptet for Cloud Discovery-blokk ble utvidet for å støtte Zscaler-format.
Ny risikofaktor for skyappkatalog: dataoppbevaring etter kontoavslutning. Dette gjør at du kan sørge for at dataene fjernes når du avslutter en konto i en skyapp.
Cloud App Security utgivelse 102
Utgitt 30. juli 2017
Siden IP-adresseinformasjon er avgjørende for nesten alle undersøkelser, kan du nå vise detaljert informasjon om IP-adresser i aktivitetsskuffen. Fra en bestemt aktivitet kan du nå klikke på IP-adressefanen for å vise konsoliderte data om IP-adressen. Dataene inkluderer antall åpne varsler for den bestemte IP-adressen, en trendgraf over nylig aktivitet og et plasseringskart. Denne funksjonen muliggjør enkel neddrilling. Når du for eksempel undersøker umulige reisevarsler, kan du enkelt forstå hvor IP-adressen ble brukt, og om den var involvert i mistenkelige aktiviteter eller ikke. Du kan utføre handlinger direkte i IP-adresseskuffen som gjør det mulig for deg å merke en IP-adresse som risikabelt, VPN eller firma for å lette fremtidig undersøkelse og opprettelse av policyer. Hvis du vil ha mer informasjon, kan du se IP-adresseinnsikt
I Cloud Discovery kan du nå bruke egendefinerte loggformater for automatiserte loggopplastinger. Med egendefinerte loggformater kan du enkelt automatisere opplasting av logger fra SIEM-er, for eksempel Splunk-servere eller andre formater som ikke støttes.
De nye brukerundersøkelseshandlingene aktiverer et ekstra nivå av neddrilling til brukerundersøkelser. Fra undersøkelsessidene kan du nå høyreklikke på en aktivitet, bruker eller konto og bruke ett av følgende nye filtre for avansert undersøkelse og filtrering: Vis relatert aktivitet, Vis relatert styring, Vis relaterte varsler, Vis eide filer, Vis filer som deles med denne brukeren.
Katalogen for skyapp inneholder nå et nytt felt for dataoppbevaring etter kontoavslutning. Med denne risikofaktoren kan du sørge for at dataene fjernes når du avslutter en konto i en skyapp.
Cloud App Security har nå forbedret synlighet i aktiviteter angående Salesforce-objekter. Objekter inkluderer kundeemner, kontoer, kampanjer, muligheter, profiler og saker. Innsyn i tilgangen til kontosider gjør det for eksempel mulig å konfigurere en policy som varsler deg hvis en bruker viser et uvanlig stort antall kontosider. Dette er tilgjengelig via Salesforce App Connector når du har aktivert Salesforce Event Monitoring i Salesforce (en del av Salesforce Shield).
Ikke spor er nå tilgjengelig for private forhåndsversjonskunder! Nå kan du kontrollere hvilke brukeres aktivitetsdata som behandles. Med denne funksjonen kan du angi bestemte grupper i Cloud App Security som «Ikke spor». Nå kan du for eksempel bestemme deg for ikke å behandle aktivitetsdata for brukere som befinner seg i Tyskland eller land/område som ikke er bundet av en bestemt samsvarslov. Dette kan implementeres på tvers av alle apper i Cloud App Security, for en bestemt app eller til og med for et bestemt delprogram. I tillegg kan denne funksjonen brukes til å forenkle gradvis utrulling av Cloud App Security. Hvis du vil ha mer informasjon eller bli med i den private forhåndsvisningen for denne funksjonen, kontakter du kundestøtte eller kontorepresentant.
Cloud App Security utgivelse 100
Utgitt 3. juli 2017
Nye funksjoner
Sikkerhetsutvidelser: Sikkerhetsutvidelser er et nytt instrumentbord for sentralisert administrasjon av alle sikkerhetsutvidelser for Cloud App Security. Utvidelser inkluderer API-tokenbehandling, SIEM-agenter og eksterne DLP-koblinger. Det nye instrumentbordet er tilgjengelig i Cloud App Security under «Innstillinger».
- API-tokener – generer og administrer dine egne API-tokener for å integrere Cloud App Security med tredjepartsprogramvare ved hjelp av våre RESTful API-er.
- SIEM-agenter – SIEM-integrering ble tidligere plassert direkte under «Innstillinger», nå tilgjengelig som en fane i Sikkerhetsutvidelser.
- Ekstern DLP (forhåndsvisning) – Cloud App Security lar deg bruke eksisterende investeringer i tredjeparts klassifiseringssystemer, for eksempel DLP-løsninger (Data Loss Prevention), og lar deg skanne innholdet i skyprogrammer ved hjelp av eksisterende distribusjoner som kjører i miljøet ditt. Kontakt kontoansvarlig for å bli med i forhåndsvisningen.
Automatisk sanksjon/ikke-helliggjørelse: Nye policyer for appgjenkjenning gir Cloud Discovery muligheten til automatisk å angi apper med sanksjonert/ikke-helliggjort etikett. Dette gir deg muligheten til automatisk å identifisere apper som er i strid med organisasjonens retningslinjer og forskrifter, og legge dem til i det genererte blokkeringsskriptet.
Cloud App Security-filetiketter: Nå kan du bruke Cloud App Security filetiketter for å gi mer innsikt i filene den skanner. For hver fil som skannes av Cloud App Security DLP, kan du nå vite om filene ble blokkert fra å bli inspisert fordi de ble kryptert eller skadet. Du kan for eksempel konfigurere policyer for å varsle og sette passordbeskyttede filer i karantene som deles eksternt. Denne funksjonen er tilgjengelig for filer som skannes etter 3. juli 2017.
Du kan filtrere etter disse filene ved hjelp av filterklassifiseringsetikettene>Cloud App Security:
- Azure RMS kryptert – filer med innhold som ikke ble inspisert fordi de har Azure RMS-krypteringssett.
- Passord kryptert – filer med innhold som ikke ble inspisert fordi de er passordbeskyttet av brukeren.
- Skadet fil – filer med innhold som ikke ble kontrollert fordi innholdet ikke kunne leses.
Brukerinnsikt: Undersøkelsesopplevelsen ble oppgradert for å aktivere forhåndsdefinert innsikt om den fungerende brukeren. Med ett enkelt klikk kan du nå se en omfattende oversikt over brukerne fra aktivitetsskuffen, innsikt inkluderer hvilken plassering de koblet fra, hvor mange åpne varsler de er involvert i, og metadatainformasjonen deres.
Appkoblingsinnsikt: Under App Connectors inkluderer hver tilkoblede app nå en appskuff i tabellen for enklere neddrilling i statusen. Detaljer som er angitt, inkluderer når App-koblingen ble koblet til og siste tilstandskontroll på koblingen. Du kan også overvåke statusen for DLP-skanning på hver app: totalt antall filer som undersøkes av DLP og statusen for sanntidsskanningene (forespurte skanninger kontra faktiske skanninger). Du kan se om frekvensen av filer som skannes av Cloud App Security i sanntid, er lavere enn det forespurte nummeret, og om leieren kan overskride kapasiteten og oppleve en forsinkelse i DLP-resultatene.
Katalogtilpasning for skyapp:
- Appkoder: Nå kan du opprette egendefinerte koder for apper. Disse kodene kan brukes som filtre for å dykke dypere inn i bestemte typer apper som du vil undersøke. Egendefinert overvåkingsliste, tilordning til en bestemt forretningsenhet eller egendefinerte godkjenninger, for eksempel «godkjent av juridisk».
- Egendefinerte notater: Når du ser gjennom og vurderer de ulike programmene som ble oppdaget i hele miljøet, kan du nå lagre konklusjoner og innsikt i notatene.
- Egendefinert risikopoengsum: Nå kan du overstyre risikoresultatet for en app. Hvis for eksempel risikoresultatet for en app er 8 og det er en godkjent app i organisasjonen, kan du endre risikoresultatet til 10 for organisasjonen. Du kan også legge til notater for å gjøre justeringen av endringen tydelig når noen ser gjennom appen.
Ny distribusjonsmodus for logginnsamling: Vi begynner å rulle ut en ny distribusjonsmodus er nå tilgjengelig for loggsamleren. I tillegg til den gjeldende distribusjonen basert på virtuelle apparater, kan den nye Docker (beholder)-baserte loggsamleren installeres som en pakke på Windows- og Ubuntu-maskiner både lokalt og i Azure. Når du bruker Docker, eies vertsmaskinen av kunden, som fritt kan oppdatere og overvåke den.
Kunngjøringer:
- Katalogen for skyapper støtter nå over 15 000 apper som kan oppdages
- Samsvar: Cloud App Security er offisielt SOC1/2/3 sertifisert av Azure. Hvis du vil ha en fullstendig liste over sertifiseringer, kan du se samsvarstilbud og filtrere resultatene for Cloud App Security.
Andre forbedringer:
- Forbedret analyse: Forbedringer ble gjort i cloud discovery-logganalysemekanismen. Det er mindre sannsynlig at interne feil oppstår.
- Forventede loggformater: Det forventede loggformatet for Cloud Discovery-logger inneholder nå eksempler på både Syslog-format og FTP-format.
- Status for opplasting av loggsamler: Nå kan du se logginnsamlingsstatusen i portalen og feilsøke feil raskere ved hjelp av statusvarsler i portalen og systemvarslene.
Cloud App Security utgivelse 99
Utgitt 18. juni 2017
Nye funksjoner
- Nå kan du kreve at brukere logger på igjen alle Microsoft 365- og Azure AD-apper. Krev pålogging på nytt som en rask og effektiv utbedring for varsler om mistenkelig brukeraktivitet og kompromitterte kontoer. Du finner den nye styringen i policyinnstillingene og varselsidene ved siden av alternativet Avvis bruker.
- Nå kan du filtrere etter aktivitetstildelingsaktiviteter for legg til representasjonsrolle i aktivitetsloggen. Denne aktiviteten gjør det mulig å oppdage når en administrator har gitt en programrepresentasjonsrolle til en bruker eller systemkonto ved hjelp av cmdlet New-ManagementRoleAssignment. Denne rollen gjør det mulig for imitatoren å utføre operasjoner ved hjelp av tillatelsene som er knyttet til den representerte kontoen, i stedet for tillatelsene som er knyttet til imitatorens konto.
Forbedringer for søk i skyen:
- Cloud Discovery-data kan nå berikes med Azure Active Directory-brukernavndata. Når du aktiverer denne funksjonen, vil brukernavnet som mottas i søketrafikkloggene, bli matchet og erstattet av Azure AD brukernavn. Berikelse muliggjør følgende nye funksjoner:
- Du kan undersøke Skygge-IT-bruk ved å Azure Active Directory-bruker.
- Du kan koordinere den oppdagede skyappen med API-ens innsamlede aktiviteter.
- Deretter kan du opprette egendefinerte logger basert på Azure AD brukergrupper. For eksempel en Shadow IT-rapport for en bestemt markedsføringsavdeling.
- Det ble gjort forbedringer i Juniper syslog parser. Den støtter nå welf- og sd-syslog-formatene.
- Forbedringer ble gjort til Palo Alto parser for bedre applikasjonsoppdagelse.
- Hvis du vil kontrollere at loggene lastes opp, kan du nå se statusen til loggsamlerne i Cloud App Security-portalen.
Generelle forbedringer:
- Innebygde IP-adressekoder og egendefinerte IP-koder anses nå som hierarkisk, med egendefinerte IP-koder som har forrang over innebygde IP-koder. Hvis for eksempel en IP-adresse er merket som Risikobasert basert på trusselintelligens, men det finnes en egendefinert IP-kode som identifiserer den som firma, har den egendefinerte kategorien og kodene forrang.
Cloud App Security utgivelse 98
Utgitt 4. juni 2017
Oppdateringer for Cloud Discovery:
- Brukere kan nå utføre avansert filtrering på oppdagede apper. Filtrering gjør det mulig å utføre grundige undersøkelser. Filtrering av apper basert på bruk. Wow mye laste opp trafikk fra oppdagede apper av visse typer? Hvor mange brukere brukte bestemte kategorier av oppdagede apper? Du kan også utføre flervalg i venstre panel for å velge flere kategorier.
- Startet utrulling av nye maler for Cloud Discovery som er basert på populære søk, for eksempel «ikke-kompatibel skylagringsapp». Disse grunnleggende filtrene kan brukes som maler til å utføre analyser på de oppdagede appene.
- For brukervennlighet kan du nå utføre handlinger som sanksjon og helliggjøring på tvers av flere apper i én handling.
- Vi ruller nå ut muligheten til å opprette egendefinerte oppdagelsesrapporter basert på Azure Active Directory-brukergrupper. Hvis du for eksempel vil se skybruken av markedsføringsavdelingen, kan du importere markedsføringsgruppen ved hjelp av funksjonen importer brukergruppe, og deretter opprette en egendefinert rapport for denne gruppen.
Nye funksjoner:
- RBAC for sikkerhetslesere fullført utrulling. Med denne funksjonen kan du administrere tillatelsene du gir til administratorene i Cloud App Security-konsollen. Som standard har alle Azure Active Directory-administratorer, globale administratorer for Microsoft 365 og sikkerhetsadministratorer alle tillatelser i portalen. Alle sikkerhetslesere i Azure Active Directory og Microsoft 365 har skrivebeskyttet tilgang i Cloud App Security. Du kan legge til ekstra administratorer eller overstyre tillatelser ved hjelp av alternativet Behandle tilgang. Hvis du vil ha mer informasjon, kan du se Administrere administratortillatelser.
- Vi ruller nå ut detaljerte rapporter om trusselintelligens for risikable IP-adresser som oppdages av Microsofts intelligente sikkerhetsgraf. Når en aktivitet utføres av et botnet, ser du navnet på botnet (hvis tilgjengelig) med en kobling til en detaljert rapport om det bestemte botnet.
Cloud App Security utgivelse 97
Utgitt 24. mai 2017
Nye funksjoner:
- Undersøk filer og brudd på policyen: Nå kan du se alle policysamsvar på Filer-siden. I tillegg er filvarselsiden forbedret til nå å inkludere en egen fane for loggen for den bestemte filen. Forbedringen gjør det mulig å drille ned i bruddloggen på tvers av alle policyer for den bestemte filen. Hver logghendelse inneholder et øyeblikksbilde av filen på varseltidspunktet. Den inneholder en indikasjon på om filen ble slettet eller satt i karantene.
- Admin karantene er nå tilgjengelig i privat forhåndsversjon for Microsoft 365 SharePoint og OneDrive for Business filer. Med denne funksjonen kan du sette filer som samsvarer med policyer i karantene, eller angi en automatisert handling for å sette dem i karantene. Quarantining fjerner filene fra brukerens SharePoint-katalog og kopierer originalene til plasseringen for administratorkarantene du velger.
Forbedringer for Cloud Discovery:
- Cloud Discovery-støtte for Cisco Meraki-logger er forbedret.
- Alternativet for å foreslå en forbedring av Cloud Discovery gjør det nå mulig å foreslå en ny risikofaktor.
- Den egendefinerte logganalysen ble forbedret for å støtte loggformater ved å skille innstillingen for tid og dato, og for å gi deg muligheten til å angi tidsstempel.
- Begynner å rulle ut muligheten til å opprette egendefinerte oppdagelsesrapporter basert på Azure Active Directory-brukergrupper. Hvis du for eksempel vil se skybruken av markedsføringsavdelingen, importerer du markedsføringsgruppen ved hjelp av funksjonen importer brukergruppe, og deretter oppretter du en egendefinert rapport for denne gruppen.
Andre oppdateringer:
- Cloud App Security inkluderer nå støtte for Microsoft Power BI aktiviteter som støttes i microsoft 365-overvåkingsloggen. Denne funksjonen rulles gradvis ut. Du må aktivere denne funksjonaliteten i Power BI-portalen.
- I aktivitetspolicyer kan du nå angi at brukere skal varsle og utsette handlinger på tvers av alle tilkoblede apper. Du kan for eksempel angi at en policy alltid skal varsle brukerens overordnede og stoppe brukeren umiddelbart når brukeren har flere mislykkede pålogginger i en tilkoblet app.
OOB-utgivelse
- I en rask reaksjon på løsepengeviruset som feide over hele verden, la Cloud App Security-teamet til en ny mal for aktivitetsgjenkjenning av potensiell løsepengevirus i portalen som inkluderer signaturutvidelsen av WannaCrypt. Vi råder deg til å angi denne policyen i dag.
Cloud App Security utgivelse 96
Utgitt 8. mai 2017
Nye funksjoner:
Hvis du fortsetter den gradvise utrullingen av sikkerhetslesertillatelsen, kan du administrere tillatelsene du gir til administratorene i Cloud App Security-konsollen. Alle Azure Active Directory og globale administratorer og sikkerhetsadministratorer for Microsoft 365 har som standard alle tillatelser i portalen. Alle sikkerhetslesere i Azure Active Directory og Microsoft 365 har skrivebeskyttet tilgang i Cloud App Security. Hvis du vil ha mer informasjon, kan du se Administrere administratortillatelser.
Viktig
Microsoft anbefaler at du bruker roller med færrest tillatelser. Dette bidrar til å forbedre sikkerheten for organisasjonen. Global administrator er en svært privilegert rolle som bør begrenses til nødscenarioer når du ikke kan bruke en eksisterende rolle.
Fullført utrulling av støtte for Cloud Discovery for brukerdefinerte logganalyser for CSV-baserte logger. Cloud App Security gjør det mulig å konfigurere en analyse for dine tidligere apparater som ikke støttes, ved å gi deg verktøyene til å avgrense hvilke kolonner som samsvarer med bestemte data. Hvis du vil ha mer informasjon, kan du se Egendefinert logganalyse.
Forbedringer:
Cloud Discovery støtter nå Juniper SSG-apparater.
Støtte for Cloud Discovery for Cisco ASA-logger er forbedret for bedre synlighet.
Nå kan du enklere kjøre massehandlinger og velge flere poster i Cloud App Security portaltabeller: sidelengden er økt for å forbedre masseoperasjoner.
Den utgående delingen etter domene, og eiere av innebygde rapporter for delte filer kan nå kjøres for Salesforce-data.
Vi starter utrullingen av ekstra Salesforce-aktiviteter, slik at du kan spore interessant informasjon som ble hentet fra aktivitetsdataene. Disse aktivitetene omfatter visning og redigering av kontoer, kundeemner, muligheter og ulike andre interessante Salesforce-objekter.
Nye aktiviteter ble lagt til for Exchange, slik at du kan overvåke hvilke tillatelser som ble gitt for brukerpostbokser eller postboksmapper. Disse aktivitetene omfatter:
- Legg til mottakertillatelser
- Fjern mottakertillatelser
- Legge til mappetillatelser for postboks
- Fjerne mappetillatelser for postboks
- Angi mappetillatelser for postboks
Du kan for eksempel nå overvåke brukere som har fått SendAs-tillatelser til andre brukeres postbokser, og som et resultat kan du nå sende e-postmeldinger i navnet.
Cloud App Security utgivelse 95
Utgitt 24. april 2017
Oppdateringer:
Kontoer-siden er oppdatert med forbedringer som gjør det enklere å oppdage risikoer. Nå kan du enklere filtrere etter interne og eksterne kontoer. Se med et øyekast om en bruker har administratortillatelser. Du kan utføre handlinger på hver konto per app, for eksempel fjerne tillatelser, fjerne brukerens samarbeid, avbryte brukeren. I tillegg vises importerte brukergrupper for hver konto.
For Microsoft-arbeidskontoer (Microsoft 365 og Azure Active Directory) grupperer Cloud App Security ulike brukeridentifikatorer, for eksempel proxy-adresser, aliaser, SID og mer under én enkelt konto. Alle aliaser som er relatert til en konto, vises under den primære e-postadressen. Basert på listen over brukeridentifikatorer, for aktiviteter hvis aktør er en brukeridentifikator. Skuespilleren vises som det primære brukernavnet UPN (brukerhovednavn). Grupper tilordnes og policyer brukes basert på UPN. Denne endringen forbedrer undersøkelse av aktiviteter og smelter alle relaterte aktiviteter til samme økt for avvik og gruppebaserte policyer. Denne funksjonen rulles gradvis ut i løpet av neste måned.
Robotkoden ble lagt til som en mulig risikofaktor i den innebygde rapporten For nettleserbruk. I tillegg til at nettleserbruken merkes som utdatert, kan du nå se når nettleserbruk ble utført av en robot.
Når du oppretter en filpolicy for innholdsinspeksjon, kan du nå angi at filteret bare skal inkludere filer med minst 50 treff.
Cloud App Security utgivelse 94
Utgitt 2. april 2017
Nye funksjoner:
- Cloud App Security er nå integrert med Azure RMS. Du kan beskytte filer i Microsoft 365 OneDrive og Sharepoint Online med Microsoft Rights Management direkte fra Cloud App Security-portalen. Beskyttelse kan oppnås fra Filer-siden . Hvis du vil ha mer informasjon, kan du se Integrere med Azure Information Protection. Støtte for ekstra programmer vil være tilgjengelig i fremtidige versjoner.
- Frem til nå, når robot- og crawleraktiviteter finner sted på nettverket, var det spesielt vanskelig å identifisere fordi aktivitetene ikke utføres av en bruker på nettverket. Uten at du vet det, kan roboter og kravlesøkere kjøre skadelige verktøy på datamaskinene dine. Nå gir Cloud App Security deg verktøyene til å se når roboter og crawlere utfører aktiviteter på nettverket. Du kan bruke den nye brukeragentkoden til å filtrere aktiviteter i aktivitetsloggen. Med brukeragentkoden kan du filtrere alle aktiviteter som utføres av roboter, og du kan bruke den til å opprette en policy som varsler deg hver gang denne typen aktivitet oppdages. Du blir oppdatert når fremtidige utgivelser inkluderer denne risikable aktiviteten som innebygd i varsler om avviksregistrering.
- Den nye siden for enhetlige apptillatelser gjør det enklere å undersøke tillatelsene brukerne har gitt til tredjepartsapper. Ved å klikke på Undersøk>apptillatelser kan du nå vise en liste over alle tillatelsene brukerne har gitt til tredjepartsapper. En side med apptillatelser per tilkoblede app gjør det mulig å bedre sammenligne mellom de ulike appene og tillatelsene som er gitt. Hvis du vil ha mer informasjon, kan du se Behandle apptillatelser.
- Du kan filtrere data direkte fra tabellskuffen for enklere undersøkelse. I aktivitetsloggen er sidene for Filer-tabellen og Apptillatelser nå forbedret med nye kontekstavhengige handlinger som gjør pivotering i undersøkelsesprosessen mye enklere. Vi har også lagt til hurtigkoblinger til konfigurasjonssider og muligheten til å kopiere data med ett enkelt klikk. Hvis du vil ha mer informasjon, kan du se informasjon om hvordan du arbeider med filen og aktivitetsskuffene.
- Støtte for Microsoft Teams til Aktivitetslogger for Microsoft 365 og utrulling av varsler ble fullført.
Cloud App Security utgivelse 93
Utgitt 20. mars 2017
Nye funksjoner:
- Nå kan du bruke policyer for å inkludere eller utelate importerte brukergrupper.
- Cloud App Security Anonymisering kan du nå konfigurere en egendefinert krypteringsnøkkel. Hvis du vil ha mer informasjon, kan du se Anonymisering av Cloud Discovery.
- Hvis du vil ha mer kontroll over bruker- og kontoadministrasjon, har du nå direkte tilgang til Azure AD kontoinnstillinger for hver bruker og konto fra kontosiden. Bare klikk på tannhjulet ved siden av hver bruker. Denne endringen gir enklere tilgang til administrasjonsfunksjoner for avanserte brukeradministrasjonsfunksjoner, konfigurasjon av MFA, detaljer om brukerpålogginger og muligheten til å blokkere pålogging.
- Nå kan du eksportere et blokkeringsskript for apper som ikke er helliggjort, via Cloud App Security-API-en. Finn ut mer om API-ene våre i Cloud App Security-portalen ved å klikke spørsmålstegnet på menylinjen, etterfulgt av API-dokumentasjon.
- Den Cloud App Security app-koblingen for ServiceNow ble utvidet til å omfatte støtte for OAuth-tokener (som introdusert i Genève, Helsinki, Istanbul). Denne endringen gir en mer robust API-tilkobling til ServiceNow som ikke er avhengig av distribusjonsbrukeren. Hvis du vil ha mer informasjon, kan du se Koble ServiceNow til Microsoft Cloud App Security. Eksisterende kunder kan oppdatere innstillingene sine på tilkoblingssiden for ServiceNow-appen.
- Hvis du har konfigurert ekstra tredjeparts DLP-skannere, viser DLP-skannestatusen nå statusen for hver kobling uavhengig for å forbedre synligheten.
- Cloud App Security inkluderer nå støtte for Microsoft Teams-aktiviteter som støttes i Microsoft 365-overvåkingsloggen. Denne funksjonen rulles gradvis ut.
- For Exchange Online representasjonshendelser kan du nå filtrere etter tilgangsnivået som brukes – delegert, administrator eller delegert administrator. Du kan søke etter hendelser som viser representasjonsnivået som interesserer deg i aktivitetsloggen, ved å søke etter Aktivitetsobjekter-element>.
- I appskuffen på Apptillatelser-fanen i Microsoft 365-apper kan du nå se utgiveren av hver app. Du kan også bruke Publisher som et filter for undersøkelse av ekstra apper fra samme utgiver.
- Risikable IP-adresser vises nå som en uavhengig risikofaktor i stedet for vektet under den generelle lokasjonsrisikofaktoren .
- Når Azure Information Protection etiketter er deaktivert på en fil, vises de deaktiverte etikettene som deaktivert i Cloud App Security. Slettede etiketter vises ikke.
Ekstra Salesforce-støtte:
- Du kan nå stoppe salesforce-brukere i Cloud App Security. Denne handlingen kan utføres i Kontoer-fanen i Salesforce Connector. Klikk tannhjulet på slutten av raden til en bestemt bruker, og velgAvbryt eller Bruk ikke bruk. Suspendering og unsuspend kan også brukes som en styringshandling som en del av en policy. Alle midlertidige og ubrukte aktiviteter som utføres i Cloud App Security, loggføres i styringsloggen.
- Forbedret synlighet for Innholdsdeling for Salesforce: Nå kan du se hvilke filer som ble delt med hvem, inkludert offentlig delte filer, filer som er delt med grupper og filer som er delt med hele Salesforce-domenet. Forbedret synlighet rulles ut med tilbakevirkende kraft til nye og gjeldende tilkoblede Salesforce-apper. Det kan ta litt tid før denne informasjonen oppdateres første gang.
- Vi har forbedret dekningen for følgende Salesforce-hendelser, og atskilt dem fra aktiviteten Administrer brukere :
- Redigere tillatelser
- Opprett bruker
- Endre rolle
- Tilbakestill passord
Cloud App Security utgivelse 90, 91, 92
Utgitt februar 2017
Spesiell kunngjøring:
Cloud App Security er nå offisielt sertifisert med Microsoft Compliance for ISO, HIPAA, CSA STAR, EU-modellklausuler og mer. Se den fullstendige listen over sertifiseringer i artikkelen Om microsofts samsvarstilbud ved å velge Cloud App Security.
Nye funksjoner:
Importere brukergrupper (forhåndsversjon) Når du kobler til apper ved hjelp av API-koblinger, kan du nå Cloud App Security importere brukergrupper fra Microsoft 365 og Azure Active Directory. Vanlige scenarioer som bruker importerte brukergrupper inkluderer: å undersøke hvilke dokumenter HR-personene ser på, eller du kan kontrollere om det er noe uvanlig som skjer i ledergruppen, eller om noen fra administratorgruppen utførte en aktivitet utenfor USA. Hvis du vil ha mer informasjon og instruksjoner, kan du se Importere brukergrupper.
I aktivitetsloggen kan du nå filtrere brukere og brukere i grupper for å vise hvilke aktiviteter som ble utført av en bestemt bruker, og som ble utført på en bestemt bruker. Du kan for eksempel undersøke aktiviteter der brukeren utga seg for å være andre, og aktiviteter der andre representerte denne brukeren. Hvis du vil ha mer informasjon, kan du se Aktiviteter.
Når du undersøker en fil på Filer-siden , kan du nå se mer informasjon om samarbeidspartnerne hvis du driller ned i samarbeidspartnerne til en bestemt fil. Denne informasjonen omfatter om de er interne eller eksterne, forfattere eller lesere (filtillatelser), og når en fil deles med en gruppe, kan du nå se alle brukere som er medlemmer av gruppen. Når du ser alle brukerne, kan du se om gruppemedlemmene er eksterne brukere.
IPv6-støtte er nå tilgjengelig for alle apparater.
Cloud Discovery støtter nå Barracuda-apparater.
Cloud App Security systemvarsler dekker nå SIEM-tilkoblingsfeil. Hvis du vil ha mer informasjon, kan du se SIEM-integrering.
Cloud App Security inkluderer nå støtte for følgende aktiviteter:
Microsoft 365, SharePoint/OneDrive: Oppdater programkonfigurasjon, Fjern eier fra gruppe, Slett nettsted, Opprett mappe
Dropbox: Legg til medlem i gruppen, Fjern medlem fra gruppe, Opprett gruppe, Gi nytt navn til gruppe, Endre gruppemedlemsnavn
Boks: Fjern element fra gruppe, Oppdater delt elementressurs, Legg til bruker i gruppe, Fjern bruker fra gruppe
Cloud App Security utgivelse 89
Utgitt 22. januar 2017
Nye funksjoner:
Vi begynner å rulle ut muligheten til å vise DLP-hendelser for Microsoft 365 Security and Compliance Center i Cloud App Security. Hvis du konfigurerte DLP-policyer i Sikkerhets- og samsvarssenter for Microsoft 365, ser du dem i Cloud App Security aktivitetsloggen når policysamsvar oppdages. Informasjonen i aktivitetsloggen inneholder filen eller e-postmeldingen som utløste samsvaret, samt policyen eller varselet om at den samsvarte. Med sikkerhetshendelsesaktiviteten kan du vise DLP-policysamsvar for Microsoft 365 i aktivitetsloggen for Cloud App Security. Ved hjelp av denne funksjonen kan du:
- Se alle DLP-treff som kommer fra Microsoft 365 DLP-motoren.
- Varsel om DLP-policyen for Microsoft 365 samsvarer med en bestemt fil, et SharePoint-område eller en bestemt policy.
- Undersøk DLP-treff med en bredere kontekst, for eksempel eksterne brukere som åpnet eller lastet ned en fil som utløste et DLP-policysamsvar.
Aktivitetsbeskrivelsene er forbedret for klarhet og konsekvens. Hver aktivitet gir nå en tilbakemeldingsknapp. Hvis det er noen ting du ikke forstår eller har spørsmål om, kan du gi oss beskjed.
Forbedringer:
- En ny styringshandling ble lagt til for Microsoft 365 som gjør det mulig å fjerne alle eksterne brukere av en fil. Denne handlingen gjør det for eksempel mulig å implementere policyer som fjerner eksterne ressurser fra filer med bare intern klassifisering.
- Forbedret identifisering av eksterne brukere i SharePoint Online. Når du filtrerer for gruppen «eksterne brukere», vises ikke systemkontoen app@ SharePoint.
Cloud App Security utgivelse 88
Utgitt 8. januar 2017
Nye funksjoner:
- Koble SIEM-en til Cloud App Security. Nå kan du sende varsler og aktiviteter automatisk til din valg frie SIEM ved å konfigurere SIEM-agenter. Nå tilgjengelig som en offentlig forhåndsvisning. Hvis du vil ha fullstendig dokumentasjon og detaljer, kan du ta en titt på Integrering med SIEM.
- Cloud Discovery støtter nå IPv6. Vi rullet ut støtte til Palo Alto og Juniper, og flere apparater vil bli rullet ut i fremtidige utgivelser.
Forbedringer:
- Det er en ny risikofaktor i katalogen for skyapper. Nå kan du vurdere en app basert på om den krever brukergodkjenning. Apper som håndhever godkjenning og ikke tillater anonym bruk, får en sunnere risikopoengsum.
- Vi ruller ut nye aktivitetsbeskrivelser for å være mer brukervennlige og konsekvente. Søk etter aktiviteter påvirkes ikke av denne endringen.
- Vi inkluderte forbedret brukerenhetsidentifikasjon, slik at Cloud App Security kunne berike et større antall hendelser med enhetsinformasjon.
Oppdateringer laget i 2016
Cloud App Security utgivelse 87
Utgitt 25. desember 2016
Nye funksjoner:
- Vi er i ferd med å rulle ut data anonymisering slik at du kan dra nytte av Cloud Discovery samtidig som du beskytter brukernes personvern. Data anonymisering utføres ved å kryptere brukernavninformasjon.
- Vi er i ferd med å rulle ut muligheten til å eksportere et blokkerende skript fra Cloud App Security til ekstra apparater. Med skriptet kan du enkelt redusere SKYGGE-IT ved å blokkere trafikk til apper som ikke er helliggjort. Dette alternativet er nå tilgjengelig for:
- BlueCoat ProxySG
- Cisco ASA
- Fortinet
- Juniper SRX
- Palo Alto
- Websense
- En ny filstyringshandling ble lagt til som gjør det mulig å tvinge en fil til å arve tillatelser fra overordnet, og slette eventuelle unike tillatelser som ble angitt for filen eller mappen. Med denne handlingen for filstyring kan du endre fil- eller mappetillatelsene som skal arves fra den overordnede mappen.
- En ny brukergruppe ble lagt til kalt Ekstern. Denne gruppen er en standard brukergruppe som er forhåndskonfigurert av Cloud App Security for å inkludere alle brukere som ikke er en del av de interne domenene. Du kan bruke denne brukergruppen som et filter. Du kan for eksempel finne aktiviteter som utføres av eksterne brukere.
- Cloud Discovery-funksjonen støtter nå Sophos Cyberoam-apparater.
Feilrettinger:
- SharePoint Online- og One Drive for Business-filer ble vist i filpolicyrapporten og på Filer-siden som intern i stedet for Privat. Denne feilen ble løst.
Cloud App Security utgivelse 86
Utgitt 13. desember 2016
Nye funksjoner:
- Alle Cloud App Security frittstående lisenser gir deg muligheten til å aktivere Azure Information Protection skanning fra de generelle innstillingene (uten å måtte opprette en policy).
Forbedringer:
- Nå kan du bruke «eller» i filfilteret for filnavnet og i MIME-typefilteret for filer og policyer. Denne endringen muliggjør scenarier som å skrive inn ordet "pass" ELLER "driver" når du oppretter en policy for personlige data. Filteret samsvarer med alle filer som har «pass» eller «driver» i filnavnet.
- Når en policy for DLP-innholdsinspeksjon kjøres som standard, blir dataene i de resulterende bruddene maskert. Nå kan du avdekke de fire siste tegnene i overtredelsen.
Mindre forbedringer:
- Nye Postboksrelaterte hendelser i Microsoft 365 (Exchange) har å gjøre med videresendingsregler og legge til og fjerne representantpostbokstillatelser.
- Ny hendelse som overvåker samtykket til nye apper i Azure Active Directory.
Cloud App Security utgivelse 85
Utgitt 27. november 2016
Nye funksjoner:
- Det ble gjort et skille mellom sanksjonerte apper og tilkoblede apper. Sanksjonering og helliggjøring er nå et merke som kan brukes på oppdagede apper og alle apper i appkatalogen. Tilkoblede apper er apper som du koblet til ved hjelp av API-koblingen for dypere synlighet og kontroll. Du kan nå merke apper som sanksjonert eller ikke helliggjort, eller koble dem til ved hjelp av appkoblingen, der det er tilgjengelig.
- Som en del av denne endringen ble siden sanksjonerte apper erstattet med en ny utforming av tilkoblede apper som eksterniserer statusdata om koblingene.
- Loggsamlerne er lettere tilgjengelig i sin egen linje i Innstillinger-menyen under Kilder.
- Når du oppretter et aktivitetspolicyfilter, kan du redusere falske positiver ved å velge å ignorere gjentatte aktiviteter når de utføres på samme målobjekt av samme bruker. Flere forsøk på å laste ned den samme filen av samme person utløser for eksempel ikke et varsel.
- Det ble gjort forbedringer i aktivitetsskuffen. Når du nå klikker på et aktivitetsobjekt i aktivitetsskuffen, kan du drille ned for mer informasjon.
Forbedringer:
- Det ble gjort forbedringer i avviksregistreringsmotoren, inkludert de umulige reisevarslingene, som IP-informasjon nå er tilgjengelig for i varselbeskrivelsen.
- Forbedringer ble gjort i de komplekse filtrene for å gjøre det mulig å legge til det samme filteret mer enn én gang for finjustering av filtrerte resultater.
- Fil- og mappeaktiviteter i Dropbox ble atskilt for bedre synlighet.
Feilrettinger:
- En feil i systemvarslingsmekanismen som skapte falske positiver, ble løst.
Cloud App Security utgivelse 84
Utgitt 13. november 2016
Nye funksjoner:
- Cloud App Security støtter nå Microsoft Azure Information Protection inkludert forbedret integrering og automatisk klargjøring. Du kan filtrere filer og angi filpolicyer ved hjelp av kodesikker klassifisering og deretter angi klassifiseringsetiketten du vil vise. Etikettene angir også om klassifiseringen ble angitt av noen i organisasjonen eller av personer fra en annen leier (ekstern). Du kan også angi aktivitetspolicyer basert på Azure Information Protection klassifiseringsetiketter og aktivere automatisk skanning etter klassifiseringsetiketter i Microsoft 365. Hvis du vil ha mer informasjon om hvordan du drar nytte av denne flotte nye funksjonen, kan du se Integrere med Azure Information Protection.
Forbedringer:
- Det ble gjort forbedringer i aktivitetsloggen for Cloud App Security:
- Microsoft 365-hendelser fra sikkerhets- og samsvarssenteret er nå integrert med Cloud App Security og er synlige i aktivitetsloggen.
- All Cloud App Security aktivitet registreres i aktivitetsloggen Cloud App Security som administrativ aktivitet.
- For å hjelpe deg med å undersøke filrelaterte varsler, kan du nå vise listen over aktiviteter som ble utført på den samsvarende filen, i hvert varsel som kommer fra en filpolicy.
- Den umulige reisealgoritmen i avviksregistreringsmotoren ble forbedret for å gi bedre støtte til små leietakere.
Mindre forbedringer:
- Grensen for aktivitetseksport ble opphøyd til 10 000.
- Når du oppretter en øyeblikksbilderapport i den manuelle opplastingsprosessen for skysøk, får du nå et nøyaktig estimat for hvor lang tid loggbehandlingen tar.
- I en filpolicy fungerer nå styringshandlingen Fjern samarbeidspartner på grupper.
- Mindre forbedringer ble gjort på siden apptillatelser .
- Når mer enn 10 000 brukere har gitt tillatelser til en app som kobler til Microsoft 365, lastes listen sakte inn. Denne tregheten er løst.
- Ekstra attributter ble lagt til i appkatalogen angående betalingskortbransjen.
Cloud App Security utgivelse 83
Utgitt 30. oktober 2016
Nye funksjoner:
- For å forenkle filtrering i aktivitetsloggen og filloggen har lignende filtre blitt konsolidert. Bruk aktivitetsfiltrene: Aktivitetsobjekt, IP-adresse og bruker. Bruk filfilteret Samarbeidspartnere til å finne nøyaktig det du trenger.
- Fra aktivitetsloggskuffen, under Kilde, kan du klikke koblingen for Vis rådata. Denne handlingen laster ned rådataene som brukes til å generere aktivitetsloggen for større neddrilling i apphendelser.
- Lagt til støtte for ekstra påloggingsaktiviteter i Okta. [Privat forhåndsvisning]
- Lagt til støtte for ekstra påloggingsaktiviteter i Salesforce.
Forbedringer:
- Forbedret brukervennlighet for øyeblikksbilderapporter og feilsøking i Cloud Discovery.
- Forbedret synlighet i varslingslisten for varsler på flere apper.
- Forbedret brukervennlighet når du oppretter nye kontinuerlige skyoppdagingsrapporter.
- Forbedret brukervennlighet i styringsloggen.
Cloud App Security utgivelse 82
Utgitt 9. oktober 2016
Forbedringer:
- Aktivitetene Endre e-post og Endre passord er nå uavhengige av den generiske Administrer brukere-aktiviteten i Salesforce.
- Lagt til en avklaring for sms daglig varslingsgrense. Maksimalt 10 meldinger sendes per telefonnummer per dag (UTC).
- Et nytt sertifikat ble lagt til Cloud Discovery-attributtene for Privacy Shield, som erstattet Safe Harbor (bare relevant for amerikanske leverandører).
- Feilsøking er lagt til i feilmeldingene om feil i API-koblingen for å gjøre det enklere å løse problemer.
- Forbedring i oppdateringsfrekvensen for microsoft 365 tredjeparts appskanning.
- Forbedringer i instrumentbordet for cloud discovery.
- Checkpoint Syslog-parseren ble forbedret.
- Forbedringer i styringsloggen for å forby og oppheve merking av tredjepartsapper.
Feilrettinger:
- Forbedret prosess for opplasting av en logo.
Cloud App Security utgivelse 81
Utgitt 18. september 2016
Forbedringer:
Cloud App Security er nå en førstepartsapp i Microsoft 365! Fra nå av kan du koble Microsoft 365 til Cloud App Security med ett enkelt klikk.
Nytt utseende i styringsloggen– den ble nå oppgradert til samme tydelige utseende som aktivitetsloggen og Filer-tabellen. Bruk de nye filtrene til enkelt å finne det du trenger og overvåke styringshandlingene dine.
Det ble gjort forbedringer i avviksregistreringsmotoren for flere mislykkede pålogginger og ekstra risikofaktorer.
Det ble gjort forbedringer i øyeblikksbilderapportene for Cloud Discovery.
Det ble gjort forbedringer i administrative aktiviteter i aktivitetsloggen. Endre passord, Oppdater bruker, Tilbakestill passord angir nå om aktiviteten ble utført som en administrativ aktivitet.
Varselfiltrene for systemvarsler ble forbedret.
Etiketten for en policy i et varsel kobler nå tilbake til policyrapporten.
Hvis det ikke er angitt noen eier for en Dropbox-fil, sendes e-postmeldinger med varsel til mottakeren du angir.
Cloud App Security støtter ytterligere 24 språk som utvider støtten til totalt 41 språk.
Cloud App Security utgivelse 80
Utgitt 4. september 2016
Forbedringer:
- Når DLP-skanningen mislykkes, får du nå en forklaring på hvorfor Cloud App Security ikke kunne skanne filen. Hvis du vil ha mer informasjon, kan du se Innholdsinspeksjon.
- Forbedringer ble gjort i avviksdeteksjonsmotorene, inkludert forbedringer i de umulige reisevarslingene.
- Det ble gjort forbedringer i avvis varslingsopplevelsen. Du kan også legge til tilbakemeldinger slik at du kan la Cloud App Security-teamet få vite om varselet var interessant og hvorfor. Tilbakemeldingen din brukes til å forbedre Cloud App Security-gjenkjenninger.
- Cisco ASA Cloud Discovery-analysene ble forbedret.
- Du mottar nå et e-postvarsel når den manuelle opplastingen i Cloud Discovery fullføres.
Cloud App Security utgivelse 79
Utgitt 21. august 2016
Nye funksjoner:
Nytt instrumentbord for cloud discovery – et helt nytt instrumentbord for skyoppdagelse er tilgjengelig, utformet for å gi deg mer innsikt i hvordan skyapper brukes i organisasjonen. Den gir en oversikt over hvilke typer apper som brukes, åpne varsler og risikonivåene for apper i organisasjonen. Den gir deg også beskjed om hvem de beste appbrukerne er i organisasjonen, og gir deg et plasseringskart for apphovedkvarteret. Det nye instrumentbordet har flere alternativer for filtrering av dataene, slik at du kan generere bestemte visninger, avhengig av hva du er mest interessert i, og enkel å forstå grafikk for å gi deg hele bildet med et øyekast.
Nye Cloud Discovery-rapporter – Hvis du vil vise resultater for Cloud Discovery, kan du nå generere to typer rapporter, øyeblikksbilderapporter og kontinuerlige rapporter. Øyeblikksbilderapporter gir ad hoc-synlighet på et sett med trafikklogger du laster opp manuelt fra brannmurer og proxyer. Kontinuerlige rapporter viser resultatene av alle logger som videresendes fra nettverket ved hjelp av loggsamlere for Cloud App Security. Disse nye rapportene gir bedre synlighet over alle data, automatisk identifisering av uregelmessig bruk som identifisert av den Cloud App Security maskinlæringsmotoren for avviksregistrering, og identifisering av uregelmessig bruk som definert av deg ved hjelp av den robuste og granulære policymotoren. Hvis du vil ha mer informasjon, kan du se Konfigurere Cloud Discovery.
Forbedringer:
- Generelle brukervennlighetsforbedringer på følgende sider: Policysider, Generelle innstillinger, E-postinnstillinger.
- I Varsler-tabellen er det nå enklere å skille mellom leste og uleste varsler. Lesevarslingene har en blå linje til venstre og er nedtonet for å angi at du allerede har lest dem.
- Aktivitetspolicyen Gjentatte aktivitetsparametere ble oppdatert.
- På Kontoer-siden ble en brukertypekolonne lagt til, slik at du nå kan se hvilken type brukerkonto hver bruker har. Brukertypene er appspesifikke.
- Nær sanntidsstøtte ble lagt til for filrelaterte aktiviteter i OneDrive og SharePoint. Når en fil endres, utløser Cloud App Security en skanning nesten umiddelbart.
Cloud App Security utgivelse 78
Utgitt 7. august 2016
Forbedringer:
Fra en bestemt fil kan du nå høyreklikke og finne relaterte. I aktivitetsloggen kan du bruke målobjektfilteret og deretter velge den bestemte filen.
Forbedrede filanalyser for Cloud Discovery Log, inkludert tillegg av Juniper og Cisco ASA.
Cloud App Security gjør det nå mulig å gi tilbakemelding om forbedring av varsler når du lukker et varsel. Du kan bidra til å forbedre kvaliteten på Cloud App Security varslingsfunksjonen ved å fortelle oss hvorfor du lukker varselet. Det er for eksempel ikke interessant, du har mottatt for mange lignende varsler, den faktiske alvorlighetsgraden bør være lavere. Varselet er ikke nøyaktig.
Når du åpner filskuffen i filpolicyvisningen, eller når du viser en filskuff, ble den nye koblingen til samsvarende policyer lagt til. Når du klikker på den, kan du vise alle treff, og du er nå aktivert for å lukke alle.
Organisasjonsenheten en bruker tilhører, legges nå til i alle relevante varsler.
Et e-postvarsel sendes nå for å gi deg beskjed når behandlingen fullføres for de manuelt opplastede loggene.
Cloud App Security utgivelse 77
Utgitt 24. juli 2016
Forbedringer:
- Ikonet for Eksport av skysøk-knappen ble forbedret for brukervennlighet.
- Når du undersøker en aktivitet, kan du nå se rådata hvis brukeragenten ikke ble analysert.
- To nye risikofaktorer ble lagt til avviksdeteksjonsmotoren:
- Cloud App Security bruker nå IP-adressekodene som er knyttet til et botnet og anonyme IP-adresser som en del av beregningen av risiko.
- Microsoft 365-aktivitet overvåkes nå for høye nedlastingshastigheter. Hvis nedlastingshastigheten for Microsoft 365 er høyere enn organisasjonens, eller en bestemt brukers, normal nedlastingsfrekvens, utløses et avviksregistreringsvarsel.
- Cloud App Security er nå kompatibel med den nye API-en for sikker deling av Dropbox.
- Forbedringer ble gjort for å legge til detaljer i oppdagelseslogganalysefeilene, inkludert: Ingen skyrelaterte transaksjoner, alle hendelser er utdaterte, skadet fil, loggformat samsvarer ikke.
- Datofilteret for aktivitetsloggen ble forbedret. den inneholder nå muligheten til å filtrere etter tid.
- Siden for IP-adresseområder ble forbedret for brukervennlighet.
- Cloud App Security inkluderer nå støtte for Microsoft Azure Information Protection (forhåndsversjon). Du kan filtrere filer og angi filpolicyer ved hjelp av Kode sikker klassifisering. Deretter angir du nivået på klassifiseringsetiketten du vil vise. Etikettene angir også om klassifiseringen ble angitt av noen i organisasjonen eller av personer fra en annen leier (ekstern).
Cloud App Security utgivelse 76
Utgitt: 10. juli 2016
Forbedringer:
- Lister over brukere i innebygde rapporter kan nå eksporteres.
- Forbedret brukervennlighet for aggregert aktivitetspolicy.
- Forbedret støtte for meldingsanalyse for TMG W3C-brannmurloggen.
- Forbedret brukervennlighet for rullegardinlisten for filstyringshandling, som nå er delt inn i samarbeids-, sikkerhets- og undersøkelseshandlinger.
- Forbedret oppdagelse av umulig reise for Exchange Online aktivitet av: Send e-post.
- En ny liste over titler (søkebaner) ble lagt til øverst på varslene og policysidene for å gjøre navigasjonen enklere.
Feilrettinger:
- Det forhåndsinnstilte uttrykket for kredittkort i DLP-innstillingen for filpolicyer ble endret til Alle: Finance: Credit Card.
Cloud App Security utgivelse 75
Utgitt: 27. juni 2016
Nye funksjoner:
- Nye tillegg ble lagt til i den voksende listen over støttede Salesforce-hendelser. Hendelser inkluderer å gi innsikt i rapporter, delte koblinger, innholdsdistribusjon, representert pålogging og mer.
- Ikonene for de tilkoblede appene på instrumentbordet Cloud App Security ble justert med statusen for appene slik de vises på instrumentbordet for å gjenspeile de siste 30 dagene.
- Støtte for skjermer med full bredde.
Feilrettinger:
- Telefonnumre for SMS-varsel valideres nå ved innsetting.
Cloud App Security utgivelse 74
Utgitt: 13. juni 2016
- Varsel-skjermen ble oppdatert for å gi deg mer informasjon med et øyekast. Oppdateringer inkluderer muligheten til å se alle brukeraktiviteter med et øyekast, et kart over aktiviteter, relaterte brukerstyringslogger, en beskrivelse av årsaken til at varselet utløses, og ekstra grafer og kart fra brukersiden.
- Hendelser som genereres av Cloud App Security inkluderer nå hendelsestypen, formatet, policygruppene, relaterte objekter og en beskrivelse.
- Nye IP-adressekoder ble lagt til for Microsoft 365 Apps for enterprise, OneNote, Office Online og de innebygde sikkerhetsfunksjonene for alle postbokser i skyen.
- Du har nå et alternativ for å laste opp logger fra hovedmenyen for søk.
- Kategorifilteret for IP-adresse ble forbedret. IP-adressekategorien null kalles nå ukategorisert. En ny kategori kalt Ingen verdi ble lagt til for å inkludere alle aktiviteter som ikke har IP-adressedata.
- Sikkerhetsgrupper i Cloud App Security kalles nå for brukergrupper for å unngå forvirring med Active Directory-sikkerhetsgrupper.
- Det er nå mulig å filtrere per IP-adresse og filtrere ut hendelser uten en IP-adresse.
- Det ble gjort endringer i innstillingene for varslings-e-postmeldinger som ble sendt når treff oppdages i aktivitetspolicyer og filpolicyer. Nå kan du legge til e-postadresser for mottakere du vil legge til kopi med varselet.
Cloud App Security utgivelse 73
Utgitt: 29. mai 2016
- Oppdaterte varslingsfunksjoner: Nå kan du angi at varsler per policy skal sendes via e-post eller sendes som en tekstmelding.
- Varslingsside: Forbedret utforming for bedre å aktivere avanserte løsningsalternativer og hendelsesbehandling.
- Juster policy: Med varsler kan du nå flytte fra alternativer for varslingsløsning direkte til siden for policyinnstillinger for å gjøre det enklere å finjustere basert på varsler.
- Forbedringer i beregningen av avviksregistreringsrisikopoengsum og redusert usann-positiv sats basert på tilbakemeldinger fra kunder.
- Aktivitetsloggeksport inkluderer nå hendelses-ID, hendelseskategori og navn på hendelsestype.
- Forbedret utseende og brukervennlighet for styringshandlinger for policyoppretting.
- Forenklet undersøkelse og kontroll for Microsoft 365 – Valg av Microsoft 365 velger automatisk alle apper som er en del av Microsoft 365 Suite.
- Varsler sendes nå til e-postadressen som er konfigurert i den tilkoblede appen.
- Ved tilkoblingsfeil gis nå en detaljert beskrivelse av feilen av skyappen.
- Når en fil samsvarer med en policy, angis det nå en URL-adresse for å få tilgang til filen i filskuffen.
- Når et varsel utløses av en aktivitetspolicy eller en policy for avviksregistrering, sendes det et nytt detaljert varsel som gir informasjon om samsvaret.
- Et automatisk systemvarsel utløses når en appkobling kobles fra.
- Nå kan du lukke og løse ett enkelt varsel eller et masseutvalg av varsler fra siden varsler.
Cloud App Security utgivelse 72
Utgitt: 15. mai 2016
Generelle forbedringer for utseende og infrastruktur, inkludert:
- Nytt diagram for å gi mer hjelp med skyopplastingsprosessen for manuell loggopplasting.
- Forbedret prosess for oppdatering av ukjente («Andre») loggfiler. Denne prosessen inkluderer et popup-vindu som gir deg beskjed om at filen krever ekstra gjennomgang. Du blir varslet når dataene er tilgjengelige.
- Flere aktivitets- og filbrudd utheves når du undersøker en aktivitets- og fillogg for utdaterte nettlesere og operativsystemer.
Forbedrede filanalyser for Cloud Discovery Log, inkludert tillegg av Cisco ASA, Cisco FWSM, Cisco Meraki og W3C.
Kjente problemforbedringer for Cloud Discovery.
Nye aktivitetsfiltre er lagt til for eierens domene og intern/ekstern tilknytning.
Det ble lagt til et nytt filter som gjør det mulig å søke etter et Microsoft 365-objekt (filer, mapper, nettadresser).
Muligheten ble lagt til for å konfigurere en minimal risikopoengsum for policyer for avviksregistrering.
Når du angir et varsel som skal sendes når en policy brytes, kan du nå angi et minimumsgradsnivå for alvorlighetsgrad som du vil bli varslet om. Du kan velge å bruke organisasjonens standardinnstilling for dette, og du kan angi en bestemt varselinnstilling som standard for organisasjonen.
Hvis det oppstår problemer, er vi her for å hjelpe. Hvis du vil ha hjelp eller støtte for produktproblemet, kan du åpne en støtteforespørsel.