Manage multitenant operations for defense organizations
This article defines how multitenant defense organizations should manage operations across Microsoft Entra tenants to meet zero trust requirements. It covers application management, identity governance, and security operations. The primary and secondary Microsoft Entra tenant administrators have distinct responsibilities in each area. Primary and secondary tenant(s) must coordinate application onboarding, entitlement management, and threat detection and response (see figure 1). For more information, see identifying tenant types.
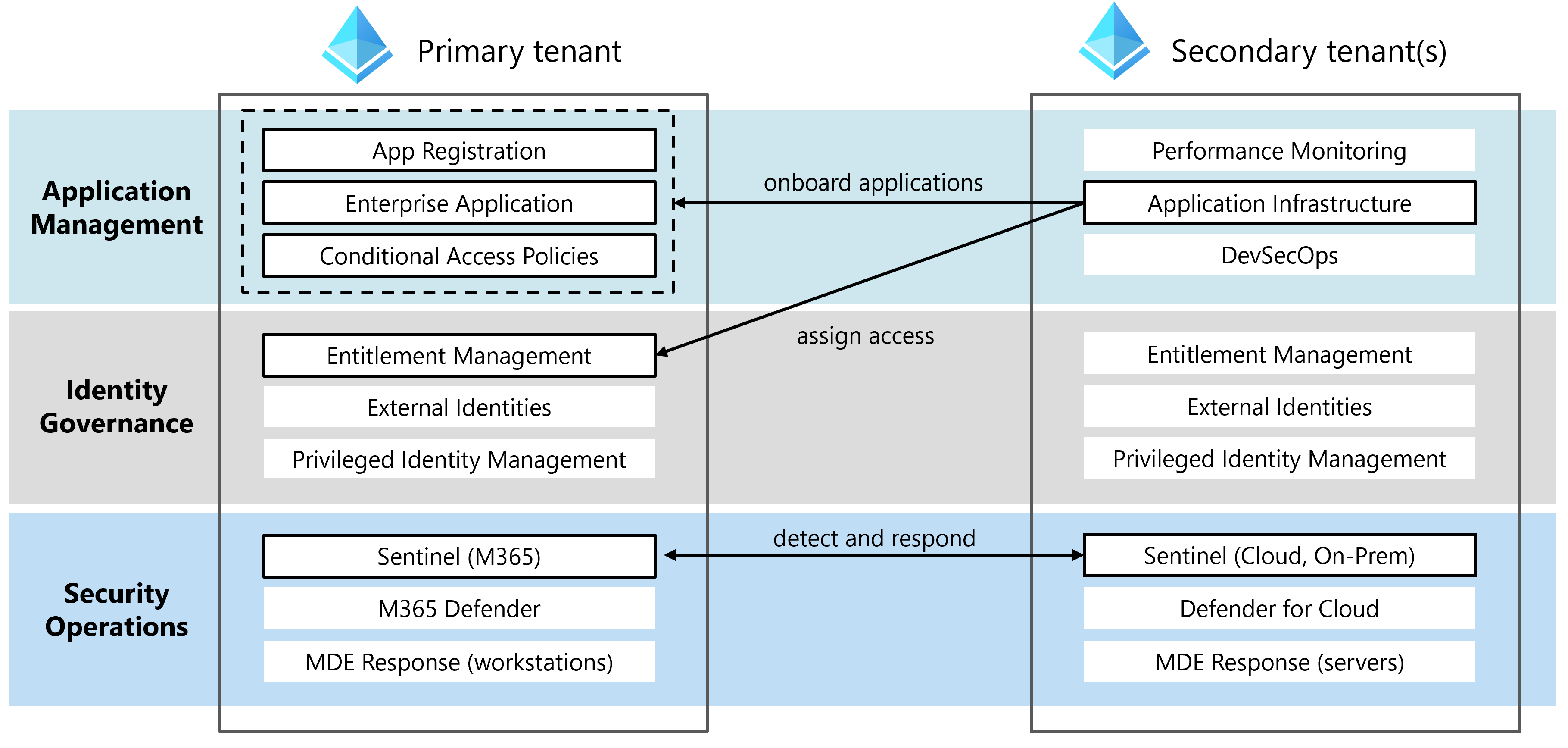 Figure 1. Shared responsibilities by tenant for multitenant defense organizations
Figure 1. Shared responsibilities by tenant for multitenant defense organizations
Application management
The primary Microsoft Entra tenant and the secondary Microsoft Entra tenant(s) share application management responsibilities. The primary tenant is responsible for completing Microsoft Entra tasks like enterprise app management and app registration. The secondary tenant is responsible for Azure platform operations like performance monitoring, resource configuration, scaling, and managing DevSecOps pipelines.
Primary tenant application management
You should onboard all modern applications that need to sign in users as enterprise applications in the primary tenant.
You should register Azure applications running in secondary tenant subscriptions with the primary tenant. The primary tenant is where users and licenses are. Registering applications in the primary tenant allows users to sign in with the same identity they use for Microsoft 365. This configuration offers the most seamless experience and lets you apply the same zero trust policy baseline to all application access.
The location of the application infrastructure (virtual machines, databases, web apps) has not effect on the tenant you can use for user sign-in. The team managing the primary tenant is responsible for app registrations and enterprise applications. They're also responsible for conditional access policies applied to applications hosted in the primary tenant and any secondary tenants.
App registrations. You register web applications and APIs the organization use with the primary tenant. The app registration creates an application object in Microsoft Entra ID. The application object represents the application definition. The application definition includes an application manifest, token claims configuration, app role definitions, and client secrets. Activities involved in primary tenant app registrations include:
- Delegating app registration permissions in Microsoft Entra ID
- Managing the assignment of the Application Developer Microsoft Entra role
- Creating and assigning custom roles for app registration
- Creating App Registrations for applications and APIs
- Exposing web APIs and adding scopes to a registered app
- Creating and managing App Roles for a registered application
- Defining API permissions for an application
Enterprise applications. Enterprise applications are the service principals for a distinct instance of an application in your directory. When you create an app registration in the Azure portal, the enterprise application creates automatically and inherits certain properties from the application object. Activities involved managing enterprise applications in the primary tenant include:
- Creating enterprise applications from the Microsoft Entra Gallery and deploying non-gallery SAML apps
- Delegate enterprise application management by assigning owners
- Managing the name, logo, visibility in My Apps for an enterprise application
- Assigning users and groups for accessing the enterprise application
- Managing signing certificates for SAML apps
- Granting consent for API permissions
- Deploying and managing Microsoft Entra application proxy for on-premises applications
Conditional access policies. Conditional Access policies enforce zero trust policies for accessing resources protected by Microsoft Entra ID. When you register applications in the primary tenant, the primary tenant administrator controls which policies apply during user sign-in.
Secondary tenant application management
Secondary tenants host the infrastructure and platform resources for workloads in Azure. The team managing any secondary tenant is responsible for performance monitoring, resource configuration, scaling, and managing DevSecOps pipelines.
Performance monitoring. Azure includes several tools for monitoring performance of hosted applications, including Azure Monitor and Application Insights. The secondary tenant administrators should set up monitoring to collect performance metrics for application workloads in subscriptions linked to their secondary tenant.
Application infrastructure. The administrators in the Azure environment must manage the infrastructure running the applications. The infrastructure includes networking, platform services, and virtual machines. The requirement applies to applications running on Azure Kubernetes Service, App Service, or virtual machines.
Application owners should use Defender for Cloud to manage the security posture of the environment and view alerts and recommendations for the deployed resources. They should use Azure Policy Initiatives to meet the compliance requirements.
Connecting Defender for Cloud to Microsoft Sentinel allows your security operations center (SOC) to better protect cloud applications. The SOC can still maintain their standard security workflow and automation procedures. Connecting Defender to Sentinel provides visibility to correlate events across the enterprise. It can monitor the cloud and on-premises. To monitor on-premises components, you need to manage them with (1) Azure Arc or (2) connect them via an API, Azure Monitor Agent, or Syslog Forwarder.
DevSecOps pipelines. When you host applications in Azure, a DevSecOps pipeline deploys infrastructure resources and application code to Azure. Secondary tenant administrators are responsible for managing service principals automating code deployment. Microsoft Entra Workload ID premium helps to secure service principals. Microsoft Entra Workload ID also reviews existing access and provides extra protections based on service principal risk.
Identity governance
Multitenant defense organizations need to govern access to applications in the primary Microsoft Entra tenant and manage external guest identities in the secondary tenant for the Azure environment.
Primary tenant identity governance
When you register applications in the primary tenant, the primary tenant governs application access. The team managing the primary tenant configures entitlement management and conduct access reviews to audit existing access. They also manage external identities and privileged identity management in the primary tenant.
Entitlement management. Microsoft Entra ID entitlement management helps govern access to Microsoft Entra applications, groups, SharePoint Sites, and Teams by bundling entitlement into assignable access packages. The primary tenant administrators manage the Microsoft Entra objects used for application governance. Activities involved in entitlement management in the primary tenant include (see figure 2):
- Creating Microsoft Entra security groups for assigning application roles
- Delegating group ownership for application assignment
- Configuring entitlement management catalogs and access packages
- Delegating roles in entitlement management
- Automating Identity Governance tasks
- Creating access reviews for access packages and Microsoft Entra security groups
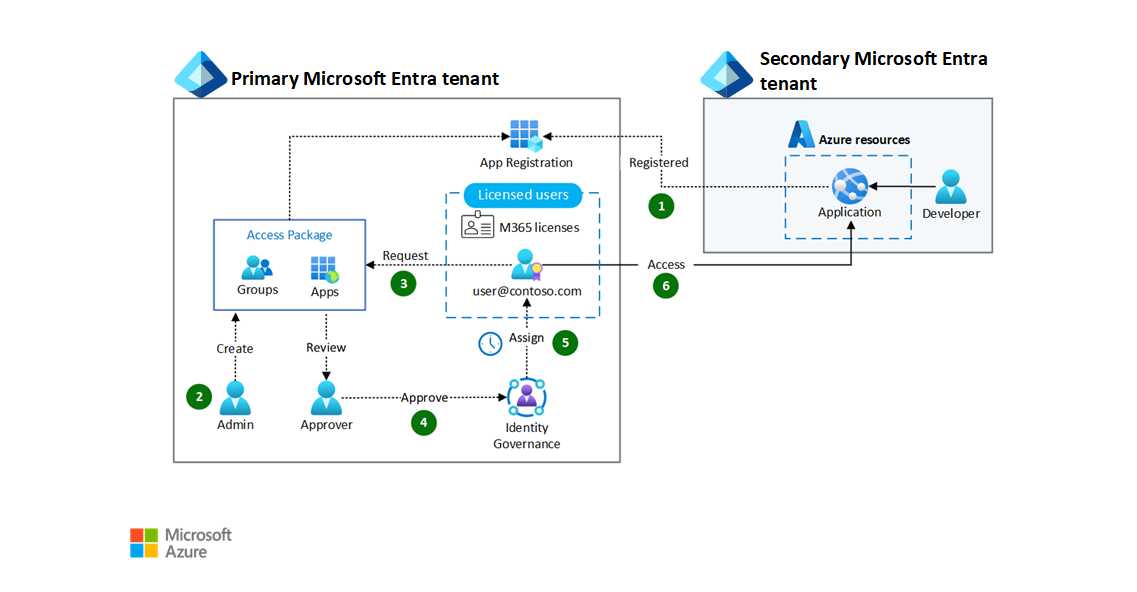 Figure 2. Entitlement management for application assignment, using contoso.com as an example domain name.
Figure 2. Entitlement management for application assignment, using contoso.com as an example domain name.
You should set up application governance using an entitlement management access package and follow this process (see figure 2):
- A primary tenant application administrator must coordinate with the developer to create a new app registration for a web app deployed in a secondary tenant.
- Identity governance administrator needs to create an access package. The administrator adds the application as an entitlement and allows users to request the package. The administrator sets the maximum duration for access before an access review. Optionally, the entitlement management administrator can delegate permissions for others to manage access packages.
- The user requests the access package. They must include the duration of the access request along with justification to help an approver make a decision. They can request any duration up to the maximum duration the administrator set.
- The access package approver approves the request.
- The package assigns the user access to the application in the secondary tenant for the requested duration.
- The user signs in with their primary tenant identity to access the application hosted in a subscription linked to a secondary tenant.
External identities. Microsoft Entra External ID enables secure interaction with users outside of your organization. The primary tenant administrators have several configuration responsibilities for applications registered in the primary tenant. They must configure external (B2B) collaboration and cross-tenant access policies with their partner organizations. They must also configure any lifecycle workflows for the guest users and their access. Activities involved in managing external identities in the primary tenant include:
- Governing access for users outside your organization
- Managing B2B collaboration settings and cross-tenant access policies (XTAP) for partner organizations
- Configuring Microsoft Entra ID Governance to review and remove external users who no longer have resource access
Privileged Identity Management. Microsoft Entra Privileged Identity Management (PIM) enables just-in-time administration of Microsoft Entra roles, Azure roles, and Microsoft Entra security groups. Primary tenant administrators are responsible for configuring and managing Microsoft Entra PIM in the primary tenant.
Secondary tenant identity governance
You should use primary tenant identities to manage secondary tenants. This management model reduces the number of separate accounts and credentials administrators need to maintain. Configuring identity governance features in secondary tenants simplifies management even more. You can use a self-service model to onboard external users (B2B guests) from the primary tenant.
The team managing a secondary tenant has several responsibilities in their secondary tenant. They configure entitlement management. They conduct access reviews to audit existing access. They manage external identities and configuring privileged identity management.
Entitlement management. You need to configure external user governance for Azure management. You should onboard external identities (B2B guests) from the primary tenant to manage Azure resources using an end user-initiated scenario using entitlement management (see figure 3).
 Figure 3. Entitlement management for external (B2B) guest access, using contoso.com as an example domain name.
Figure 3. Entitlement management for external (B2B) guest access, using contoso.com as an example domain name.
You should set up external (B2B) guest access using an entitlement management access package and follow this process (see figure 3):
- An administrator in the secondary tenant adds the primary tenant as a connected organization and creates an access package for primary tenant users to request.
- Primary tenant user requests the access package in the secondary tenant.
- Optionally, an approver completes the request.
- An external guest object is created for the user in the secondary tenant.
- Access package is assigned granting eligibility for an Azure role.
- The user manages Azure resources using their external identity.
For more information, see Govern access for external users in entitlement management.
External identities. Microsoft Entra External ID enables users in the primary tenant to interact with resources in the secondary tenant. The process outlined in figure 3 uses external identities from the primary tenant to manage Azure subscriptions attached to the secondary tenant. Activities involved in managing external identities in the secondary tenant include:
- Managing B2B collaboration settings and cross-tenant access policies (XTAP) for the primary tenant and other partner organizations
- Using Identity Governance to review and remove external users who no longer have resource access
Privileged Identity Management. Microsoft Entra PIM enables just-in-time administration for Microsoft Entra roles, Azure roles, and privileged security groups. Secondary tenant administrators are responsible for configuring and managing Microsoft Entra PIM for administrative roles used to manage the secondary Microsoft Entra tenant and Azure environment.
Security operations
The security operations team for a defense organization must protect, detect, and respond to threats across on-premises, hybrid, and multicloud environments. They need to protect their users, control sensitive data, investigate threats on user devices and servers. They also need to remediate insecure configuration of cloud and on-premises resources. Security operators in multitenant defense organizations usually operate from the primary tenant but might pivot between tenants for certain actions.
Primary tenant security operations
Security operators in the primary tenant need to monitor and manage alerts from Microsoft 365 in the primary tenant. This work involves managing Microsoft Sentinel and Microsoft Defender XDR services like Microsoft Defender for Endpoint (MDE).
Sentinel and Microsoft 365. You deploy a Microsoft Sentinel instance to a subscription attached to the primary tenant. You should configure data connectors for this Sentinel instance. The data connectors allow the Sentinel instance to ingest security logs from various sources. These sources include Office 365, Microsoft Defender XDR, Microsoft Entra ID, Entra Identity Protection, and other workloads in the primary tenant. Security operators monitoring incidents and alerts for Microsoft 365 should use the primary tenant. Activities involved in managing Sentinel for Microsoft 365 in the primary tenant include:
- Monitoring and remediating risky users and service principals in the primary tenant
- Configuring data connectors for Microsoft 365 and other available primary tenant data sources to Microsoft Sentinel
- Building workbooks, notebooks, analytics rules, and security orchestration and response (SOAR) within the Microsoft 365 environment
Microsoft Defender XDR. You manage Microsoft Defender XDR in the primary tenant. The primary tenant is where you use Microsoft 365 services. Microsoft Defender XDR helps you monitor alerts and remediate attacks against users, devices, and service principals. Activities include managing components of Microsoft Defender XDR. These components include Defender for Endpoint, Defender for Identity, Defender for Cloud Apps, Defender for Office.
Microsoft Defender for Endpoint (MDE) response (workstations). You need to join end-user workstations to the primary tenant and use Microsoft Intune to manage them. Security operators need to use MDE to respond to detected attacks. The response can be isolating workstations or collecting an investigating package. Defender for Endpoint response actions for user devices takes place in the primary tenant MDE service. Activities involved in managing MDE response in the primary tenant include managing device groups and roles.
Secondary tenant security operations
This section describes how you should monitor and protect Azure resources in subscriptions in secondary tenants. You need to Defender for Cloud, Microsoft Sentinel, and Microsoft Defender for Endpoint (MDE). You need to use Azure Lighthouse and external identities to assign permissions to security operators in the primary tenant. This setup allows security operators to use one account and privileged access device to manage security across tenants.
Sentinel (cloud, on-premises). You need to assign permissions and configure Sentinel to ingest security signals from Azure resources deployed in subscriptions linked to the secondary tenant.
Assign permissions. For security operators in the primary tenant to use Microsoft Sentinel, you have to assign permissions using Azure Resource Manager roles. You can use Azure Lighthouse to assign these roles to users and security groups in the primary tenant. This configuration lets security operators operate across Sentinel workspaces in different tenants. Without Lighthouse, security operators would need guest accounts or separate credentials to manage Sentinel in the secondary tenants.
Configure Sentinel. You should configure Microsoft Sentinel in a secondary tenant to ingest security logs from several sources. These sources include logs from Azure resources in the secondary tenant, on-premises servers, and network appliances owned and managed in the secondary tenant. Activities involved in managing Sentinel and on-premises in the secondary tenant include:
- Assigning Sentinel roles and configuring Azure Lighthouse to grant access to primary tenant security operators
- Configuring data connectors for Azure Resource Manager, Defender for Cloud, and other available secondary tenant data sources to Microsoft Sentinel
- Building workbooks, notebooks, analytics rules, and security orchestration and response (SOAR) within the secondary tenant Azure environment
Microsoft Defender for Cloud. Defender for Cloud surfaces security recommendations and alerts for resources in Azure, on-premises, or other cloud providers. You need to assign permissions to configure and manage Defender for Cloud.
Assign permissions. You need to assign permissions to security operators in the primary tenant. Like Sentinel, Defender for Cloud also uses Azure roles. You can assign Azure roles to primary tenant security operators using Azure Lighthouse. This configuration allows security operators in the primary tenant see recommendations and alerts from the Defender for Cloud without switching directories or signing in with a separate account in the secondary tenant.
Configure Defender for Cloud. You need to enable Defender for Cloud and manage recommendations and alerts. Turn on enhanced workload protections for resources in subscriptions linked to secondary tenants.
Microsoft Defender for Endpoint (MDE) response (servers). Defender for Servers is a Defender for Cloud enhanced protection for servers that includes MDE.
Assign permissions. When you enable a Defender for Server plan in a secondary tenant, the MDE extension automatically deploys to your VMs. This MDE extension onboards the server to the MDE service for the secondary tenant.
MDE uses the Microsoft Defender portal and permissions model. You must use external identities (B2B guests) to give security operators in the primary tenant access to MDE. Assign MDE roles to Microsoft Entra security groups and add the guests as group members so they can take response actions on servers.
Configure MDE. You need to configure and manage device groups and roles in Microsoft Defender for Endpoint for the secondary tenant.