Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The Log Analytics agent, also known as the Microsoft Monitoring Agent (MMA), retired in November 2024. As a result, the Defender for Servers and Defender for SQL on machines plans in Microsoft Defender for Cloud will be updated, and features that rely on the Log Analytics agent will be redesigned.
This article summarizes plans for agent retirement.
Prepare Defender for Servers
The Defender for Servers plan uses the Log Analytics agent in general availability (GA) and in AMA for some features (in preview). Here's what's happening with these features going forward:
To simplify onboarding, all Defender for Servers security features and capabilities will be provided with a single agent (Microsoft Defender for Endpoint), complemented by agentless machine scanning, without any dependency on Log Analytics agent or AMA.
- Defender for Servers features, which are based on AMA, are currently in preview and won’t be released in GA.
- Features in preview that rely on AMA remain supported until an alternate version of the feature is provided, which will rely on the Defender for Endpoint integration or the agentless machine scanning feature.
- By enabling the Defender for Endpoint integration and agentless machine scanning feature before the deprecation takes place, your Defender for Servers deployment will be up to date and supported.
Feature functionality
The following table summarizes how Defender for Servers features will be provided. Most features are already generally available using Defender for Endpoint integration or agentless machine scanning. The rest of the features will either be available in GA by the time the MMA is retired, or will be deprecated.
| Feature | Current support | New support | New experience status |
|---|---|---|---|
| Defender for Endpoint integration for down-level Windows machines (Windows Server 2016/2012 R2) | Legacy Defender for Endpoint sensor, based on the Log Analytics agent | Unified agent integration | - Functionality with the MDE unified agent is GA. - Functionality with the legacy Defender for Endpoint sensor using the Log Analytics agent will be deprecated in August 2024. |
| OS-level threat detection | Log Analytics agent | Defender for Endpoint agent integration | Functionality with the Defender for Endpoint agent is GA. |
| Adaptive application controls | Log Analytics agent (GA), AMA (Preview) | --- | The adaptive application control feature is set to be deprecated in August 2024. |
| Endpoint protection discovery recommendations | Recommendations that are available through the Foundational Cloud Security Posture Management (CSPM) plan and Defender for Servers, using the Log Analytics agent (GA), AMA (Preview) | Agentless machine scanning | - Functionality with agentless machine scanning has been released to preview in early 2024 as part of Defender for Servers Plan 2 and the Defender CSPM plan. - Azure VMs, Google Cloud Platform (GCP) instances, and Amazon Web Services (AWS) instances are supported. On-premises machines are not supported. |
| Missing OS update recommendation | Recommendations available in the Foundational CSPM and Defender for Servers plans using the Log Analytics agent. | Integration with Update Manager, Microsoft | New recommendations based on Azure Update Manager integration are GA, with no agent dependencies. |
| OS misconfigurations (Microsoft Cloud Security Benchmark) | Recommendations that are available through the Foundational CSPM and Defender for Servers plans using the Log Analytics agent, Guest Configuration extension (Preview). | Guest Configuration extension, as part of Defender for Servers Plan 2. | - Functionality based on Guest Configuration extension will be released to GA in September 2024 - For Defender for Cloud customers only: functionality with the Log Analytics agent will be deprecated in November 2024. - Support of this feature for Docker-hub and Azure Virtual Machine Scale Sets will be deprecated in Aug 2024. |
| File integrity monitoring | Log Analytics agent, AMA (Preview) | Defender for Endpoint agent integration | Functionality with the Defender for Endpoint agent will be available in August 2024. - For Defender for Cloud customers only: functionality with the Log Analytics agent will be deprecated in November 2024. - Functionality with AMA will deprecate when the Defender for Endpoint integration is released. |
Log analytics agent autoprovisioning experience - deprecation plan
As part of the MMA agent retirement, the auto provisioning capability that provides the installation and configuration of the agent for MDC customers, will be deprecated as well in 2 stages:
By the end of September 2024 - auto provisioning of MMA will be disabled for customers that are no longer using the capability, as well as for newly created subscriptions:
- Existing subscriptions that switch off MMA auto provisioning after end of September will no longer be able to enable the capability afterwards.
- On newly created subscriptions auto provisioning can no longer be enabled and is automatically turned off.
- End of November 2024 - the capability will be disabled on subscriptions that have not yet switched it off. From that point forward, it can no longer be possible to enable the capability on existing subscriptions.
The 500-MB benefit for data ingestion
To preserve the 500 MB of free data ingestion allowance for the supported data types, you need to migrate from MMA to AMA.
Note
The benefit is granted to every AMA machine that is part of a subscription with Defender for Servers plan 2 enabled.
The benefit is granted to the workspace the machine is reporting to.
The security solution should be installed on the related Workspace. Learn more about how to perform it here.
If the machine is reporting to more than one workspace, the benefit will be granted to only one of them.
Learn more about how to deploy AMA.
For SQL servers on machines, we recommend to migrate to SQL server-targeted Azure Monitoring Agent's (AMA) autoprovisioning process.
Changes to legacy Defender for Servers Plan 2 onboarding via Log Analytics agent
The legacy approach to onboard servers to Defender for Servers Plan 2 based on the Log Analytics agent and using Log analytics workspaces is set for retirement as well:
The onboarding experience for onboarding new non-Azure machines to Defender for Servers using Log Analytics agents and workspaces is removed from the Inventory and Getting started blades in the Defender for Cloud portal.
To avoid losing security coverage on the affected machines connected to a Log Analytics Workspace, with the Agent retirement:
If you onboarded non-Azure servers (both on-premises and multicloud) using the legacy approach, you should now connect these machines via Azure Arc-enabled servers to Defender for Servers Plan 2 Azure subscriptions and connectors. Learn more about deploying Arc machines at scale.
- If you used the legacy approach to enable Defender for Servers Plan 2 on selected Azure VMs, we recommend enabling Defender for Servers Plan 2 on the Azure subscriptions for these machines. You can then exclude individual machines from the Defender for Servers coverage using the Defender for Servers per-resource configuration.
This is a summary of the required action for each of the servers onboarded to Defender for Servers Plan 2 through the legacy approach:
| Machine type | Action required to preserve security coverage |
|---|---|
| On premise servers | Onboarded to Arc and connected to a subscription with Defender for Servers Plan 2 |
| Azure Virtual machines | Connect to subscription with Defender for Servers Plan 2 |
| Multicloud Servers | Connect to multicloud connector with Azure Arc provisioning and Defender for Servers plan 2 |
System update and patches recommendations experience - changes and migration guidance
System updates and patches are crucial for keeping the security and health of your machines. Updates often contain security patches for vulnerabilities that, if left unfixed, are exploitable by attackers.
System updates recommendations were previously provided by the Defender for Cloud Foundational CSPM and the Defender for Servers plans using the Log Analytics agent. This experience has been replaced by security recommendations that are gathered using Azure Update Manager and constructed out of 2 new recommendations:
Machines should be configured to periodically check for missing system updates
System updates should be installed on your machines (powered by Azure Update Manager)
Learn how to Remediate system updates and patches recommendations on your machines.
Which recommendations are being Replaced?
The following table summarizes the timetable for recommendations being deprecated and replaced.
| Recommendation | Agent | Supported resources | Deprecation date | Replacement recommendation |
|---|---|---|---|---|
| System updates should be installed on your machines | MMA | Azure & non-Azure (Windows & Linux) | August 2024 | New recommendation powered by Azure Update Manager |
| System updates on virtual machine scale sets should be installed | MMA | Azure Virtual Machine Scale Sets | August 2024 | No replacement |
How do I prepare for the new recommendations?
Connect your non-Azure machines to Arc
Ensure that periodic assessment update setting is enabled on your machines. You can do it in 2 ways:
- Fix the recommendation: Machines should be configured to periodically check for missing system updates (powered by Azure Update Manager).
- Enable Periodic assessment at scale with Azure Policy.
- Once done, Update Manager can fetch the latest updates to the machines, and you can view the latest machine compliance status.
Note
Enabling periodic assessments for Arc enabled machines that Defender for Servers Plan 2 is not enabled on their related Subscription or Connector, is subject to Azure Update Manager pricing. Arc enabled machines that Defender for Servers Plan 2 is enabled on their related Subscription or Connectors, or any Azure VM, are eligible for this capability with no additional cost.
Endpoint protection recommendations experience - changes and migration guidance
Endpoint discovery and recommendations were previously provided by the Defender for Cloud Foundational CSPM and the Defender for Servers plans using the Log Analytics agent in GA, or in preview via the AMA. These experience have been replaced by security recommendations that are gathered using agentless machine scanning.
Endpoint protection recommendations are constructed in two stages. The first stage is discovery of an endpoint detection and response solution. The second is assessment of the solution’s configuration. The following tables provide details of the current and new experiences for each stage.
Learn how to manage the new endpoint detection and response recommendations (agentless).
Endpoint detection and response solution - discovery
| Area | Current experience (based on AMA/MMA) | New experience (based on agentless machine scanning) |
|---|---|---|
| What's needed to classify a resource as healthy? | An anti-virus is in place. | An endpoint detection and response solution is in place. |
| What's needed to get the recommendation? | Log Analytics agent | Agentless machine scanning |
| What plans are supported? | - Foundational CSPM (free) - Defender for Servers Plan 1 and Plan 2 |
- Defender CSPM - Defender for Servers Plan 2 |
| What fix is available? | Install Microsoft anti-malware. | Install Defender for Endpoint on selected machines/subscriptions. |
Endpoint detection and response solution - configuration assessment
| Area | Current experience (based on AMA/MMA) | New experience (based on agentless machine scanning) |
|---|---|---|
| Resources are classified as unhealthy if one or more of the security checks aren’t healthy. | Three security checks: - Real time protection is off - Signatures are out of date. - Both quick scan and full scan aren't run for seven days. |
Three security checks: - Anti-virus is off or partially configured - Signatures are out of date - Both quick scan and full scan aren't run for seven days. |
| Prerequisites to get the recommendation | An anti-malware solution in place | An endpoint detection and response solution in place. |
Which recommendations are being deprecated?
The following table summarizes the timetable for recommendations being deprecated and replaced.
The new recommendations experience based on agentless machine scanning support both Windows and Linux OS across multicloud machines.
How will the replacement work?
- Current recommendations provided by the Log Analytics Agent or the AMA will be deprecated over time.
- Some of these existing recommendations will be replaced by new recommendations based on agentless machine scanning.
- Recommendations currently in GA remain in place until the Log Analytics agent retires.
- Recommendations that are currently in preview will be replaced when the new recommendation is available in preview.
What's happening with secure score?
- Recommendations that are currently in GA will continue to affect secure score.
- Current and upcoming new recommendations are located under the same Microsoft Cloud Security Benchmark control, ensuring that there’s no duplicate impact on secure score.
How do I prepare for the new recommendations?
- Ensure that agentless machine scanning is enabled as part of Defender for Servers Plan 2 or Defender CSPM.
- If suitable for your environment, for best experience we recommend that you remove deprecated recommendations when the replacement GA recommendation becomes available. To do that, disable the recommendation in the built-in Defender for Cloud initiative in Azure Policy.
File Integrity Monitoring experience - changes and migration guidance
Microsoft Defender for Servers Plan 2 now offers a new File Integrity Monitoring (FIM) solution powered by Microsoft Defender for Endpoint (MDE) integration. Once FIM powered by MDE is public, the FIM powered by AMA experience in the Defender for Cloud portal will be removed. In November, FIM powered by MMA will be deprecated.
Migration from FIM over AMA
If you currently use FIM over AMA:
Onboarding new subscriptions or servers to FIM based on AMA and the change tracking extension, as well as viewing changes, will no longer be available through the Defender for Cloud portal beginning May 30.
If you want to continue consuming FIM events collected by AMA, you can manually connect to the relevant workspace and view changes in the Change Tracking table with the following query:
ConfigurationChange | where TimeGenerated > ago(14d) | where ConfigChangeType in ('Registry', 'Files') | summarize count() by Computer, ConfigChangeTypeIf you want to continue onboarding new scopes or configure monitoring rules, you can manually use Data Connection Rules to configure or customize various aspects of data collection.
Microsoft Defender for Cloud recommends disabling FIM over AMA, and onboarding your environment to the new FIM version based on Defender for Endpoint upon release.
Disable FIM over AMA
To disable FIM over AMA, remove the Azure Change Tracking solution. For more information, see Remove ChangeTracking solution.
Alternatively, you can remove the related file change tracking Data collection rules (DCR). For more information, see Remove-AzDataCollectionRuleAssociation or Remove-AzDataCollectionRule.
After you disable the file events collection using one of the methods above:
- New events will stop being collected on the selected scope.
- The historical events that already were collected remain stored in the relevant workspace under the ConfigurationChange table in the Change Tracking section. These events will remain available in the relevant workspace according to the retention period defined in this workspace. For more information, see How retention and archiving work.
Migrate from FIM over Log Analytics Agent (MMA)
If you currently use FIM over the Log Analytics Agent (MMA):
File Integrity Monitoring based on Log Analytics Agent (MMA) will be deprecated at the end of November 2024.
Microsoft Defender for Cloud recommends disabling FIM over MMA, and onboarding your environment to the new FIM version based on Defender for Endpoint upon release.
Disable FIM over MMA
To disable FIM over MMA, remove the Azure Change Tracking solution. For more information, see Remove ChangeTracking solution.
After you disable the file events collection:
- New events will stop being collected on the selected scope.
- The historical events that already were collected remain stored in the relevant workspace under the ConfigurationChange table in the Change Tracking section. These events will remain available in the relevant workspace according to the retention period defined in this workspace. For more information, see How retention and archiving work.
Baseline experience
The baselines misconfiguration feature on VMs is designed to ensure that your VMs adhere to security best practices and organizational policies. Baselines misconfiguration evaluates the configuration of your VMs against the predefined security baselines, and identifies any deviations, or misconfigurations that could pose a risk to your environment.
Machine information is collected for assessment using the Log Analytics agent (also known as the Microsoft Monitoring agent (MMA)). The MMA is set to be deprecated in November 2024, and the following changes will occur:
Machine information will be collected using the Azure Policy guest configuration.
The following Azure policies are enabled with Azure Policy guest configuration:
"Windows machines should meet requirements of the Azure compute security baseline"
"Linux machines should meet requirements for the Azure compute security baseline"
Note
If you remove these policies you won't be able to access the benefits of the Azure Policy guest configuration extension.
OS recommendations based on compute security baselines will no longer be included in Defender for Cloud foundational CSPM. These recommendations will be available when you enable the Defender for Servers Plan 2.
Review the Defender for Cloud pricing page to learn about Defender Servers Plan 2 pricing information. You can also estimate costs with the Defender for Cloud cost calculator.
Important
Be aware that additional features provided by Azure Policy guest configuration that exist outside of the Defender for Cloud portal aren't included with Defender for Cloud, and are subject to Azure Policy guest configurations pricing policies. For example remediation and custom policies. For more information, see the Azure Policy guest configuration pricing page.
Recommendations that are provided by the MCSB that aren't part of Windows and Linux compute security baselines, will continue to be part of free foundational CSPM.
Install Azure Policy guest configuration
In order to continue receiving the baseline experience, you need to enable the Defender for Servers Plan 2 and install the Azure Policy guest configuration. This will ensure that you continue to receive the same recommendations and hardening guidance that you have been receiving through the baseline experience.
Depending on your environment, you may need to take the following steps:
Review the support matrix for the Azure Policy guest configuration.
Install the Azure Policy guest configuration on your machines.
Azure machines: In the Defender for Cloud portal, on the recommendations page, search for and select Guest Configuration extension should be installed on machines, and remediate the recommendation.
(Azure VMs only) You must Assign managed Identity.
- In the Defender for Cloud portal, on the recommendations page, search for and select Virtual machines' Guest Configuration extension should be deployed with system-assigned managed identity, and remediate the recommendation.
(Azure VMs only) Optional: To autoprovision the Azure Policy guest configuration across your entire subscription, you can enable the Guest Configuration agent (preview).
- To enable the Guest Configuration agent:
- Sign in to the Azure portal.
- Navigate to Environment settings > Your subscription > Settings & Monitoring.
- Select Guest Configuration.

- Toggle the Guest Configuration agent (preview) to On.
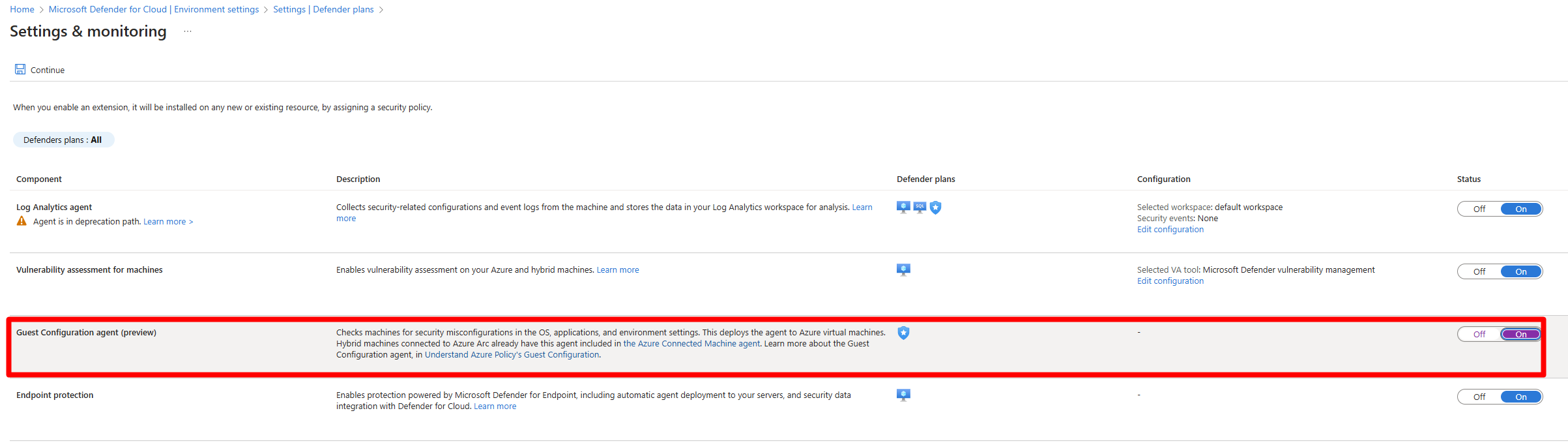
- Select Continue.
- To enable the Guest Configuration agent:
GCP and AWS: Azure Policy guest configuration is automatically installed when you connect your GCP project, or you connect your AWS accounts with Azure Arc autoprovisioning enabled, to Defender for Cloud.
On-premises machines: The Azure Policy guest configuration is enabled by default when you onboard on-premises machines as Azure Arc enabled machine or VMs.
Once you have completed the necessary steps to install the Azure Policy guest configuration, you will automatically gain access to the baseline features based on the Azure Policy guest configuration. This will ensure that you continue to receive the same recommendations and hardening guidance that you have been receiving through the baseline experience.
Changes to recommendations
With the deprecation of the MMA, the following MMA based recommendations are set to be deprecated:
- Machines should be configured securely
- Auto provisioning of the Log Analytics agent should be enabled on subscriptions
The deprecated recommendations will be replaced by the following Azure Policy guest configuration base recommendations:
- Vulnerabilities in security configuration on your Windows machines should be remediated (powered by Guest Configuration)
- Vulnerabilities in security configuration on your Linux machines should be remediated (powered by Guest Configuration)
- Guest Configuration extension should be installed on machines
Duplicate recommendations
When you enable Defender for Cloud on an Azure subscription, the Microsoft cloud security benchmark (MCSB), including compute security baselines that assess machine OS compliance, is enabled as a default compliance standard. Free foundational cloud security posture management (CSPM) in Defender for Cloud makes security recommendations based on the MCSB.
If a machine is running both the MMA and the Azure Policy guest configuration, you will see duplicate recommendations. The duplication of recommendations occurs because both methods are running at the same time and producing the same recommendations. These duplicates will affect your Compliance and Secure Score.
As a work-around, you can disable the MMA recommendations, "Machines should be configured securely", and "Auto provisioning of the Log Analytics agent should be enabled on subscriptions", by navigating to the Regulatory compliance page in Defender for Cloud.
Once you have located the recommendation, you should select the relevant machines and exempt them.
Some of the baseline configuration rules powered by the Azure Policy guest configuration tool are more current and offer broader coverage. As a result, transition to Baselines feature power by Azure Policy guest configuration can affect your compliance status since they include checks that might not have been performed previously.
Query recommendations
With the retirement of the MMA, Defender for Cloud no longer queries recommendations through the Log Analytic workspace information. Instead, Defender for Cloud now uses Azure Resource Graph for API, and portal queries, to query recommendation information.
Here are 2 sample queries you can use:
Query all unhealthy rules for a specific resource
Securityresources | where type == "microsoft.security/assessments/subassessments" | extend assessmentKey=extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id) | where assessmentKey == '1f655fb7-63ca-4980-91a3-56dbc2b715c6' or assessmentKey == '8c3d9ad0-3639-4686-9cd2-2b2ab2609bda' | parse-where id with machineId:string '/providers/Microsoft.Security/' * | where machineId == '{machineId}'All Unhealthy Rules and the amount if Unhealthy machines for each
securityresources | where type == "microsoft.security/assessments/subassessments" | extend assessmentKey=extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id) | where assessmentKey == '1f655fb7-63ca-4980-91a3-56dbc2b715c6' or assessmentKey == '8c3d9ad0-3639-4686-9cd2-2b2ab2609bda' | parse-where id with * '/subassessments/' subAssessmentId:string | parse-where id with machineId:string '/providers/Microsoft.Security/' * | extend status = tostring(properties.status.code) | summarize count() by subAssessmentId, status
Migration planning
We recommend you plan agent migration in accordance with your business requirements. The table summarizes our guidance.
| Are you using Defender for Servers? | Are these Defender for Servers features required in GA: file integrity monitoring, endpoint protection recommendations, security baseline recommendations? | Are you using Defender for SQL servers on machines or AMA log collection? | Migration plan |
|---|---|---|---|
| Yes | Yes | No | 1. Enable Defender for Endpoint integration and agentless machine scanning. 2. Wait for GA of all features with the alternative's platform (you can use preview version earlier). 3. Once features are GA, disable the Log Analytics agent. |
| No | --- | No | You can remove the Log Analytics agent now. |
| No | --- | Yes | 1. You can migrate to SQL autoprovisioning for AMA now. 2. Disable Log Analytics/Azure Monitor Agent. |
| Yes | Yes | Yes | 1. Enable Defender for Endpoint integration and agentless machine scanning. 2. You can use the Log Analytics agent and AMA side-by-side to get all features in GA. Learn more about running agents side-by-side. 3. Migrate to SQL autoprovisioning for AMA in Defender for SQL on machines. Alternatively, start the migration from Log Analytics agent to AMA in April 2024. 4. Once the migration is finished, disable the Log Analytics agent. |
| Yes | No | Yes | 1. Enable Defender for Endpoint integration and agentless machine scanning. 2. You can migrate to SQL autoprovisioning for AMA in Defender for SQL on machines now. 3. Disable the Log Analytics agent. |
MMA migration experience
The MMA migration experience is a tool that helps you migrate from the MMA to the AMA. The experience provides a step-by-step guide to help you migrate your machines from the MMA to the AMA.
With this tool, you can:
- Migrate servers from the legacy onboarding through the Log analytic workspace.
- Ensure subscriptions meet all of the prerequisites to receive all of Defender for Servers Plan 2's benefits.
- Migrate to FIM's new version over MDE.
Sign in to the Azure portal.
Navigate to the Microsoft Defender for Cloud > Environment settings.
Select MMA migration.
Select Take action for one of the available actions:
Allow the experience to load and follow the steps to complete the migration.



