Based on the details so far, this sounds like the peering was added after your VPN was created and your local site has no route to the peered VNET. Your quickest route to resolution is to delete and recreate the VPN Connection resource.
VM in Vnet peered to a Vnet with Virtual Gateway can't access on prem resources
Hi!
I'm facing connectivity issues with a Vnet peered to a Vnet with a gateway and a S2S connection to my on prem resources:
Vnet-test is peered to Vnet-hub
Vnet-hub has a Virtual Gateway deployed
Virtual Gateway is linked to my on prem gateway
The flow from on prem (or p2s connections) is working.
The flow from a VM in the Vnet-hub to on-prem resources is working.
The flow from a VM in Vnet-test to Vnet-hub is working.
The flow from a VM in Vnet-test to on-prem is blocked, but I don't know where.
The peering options are set like the following:
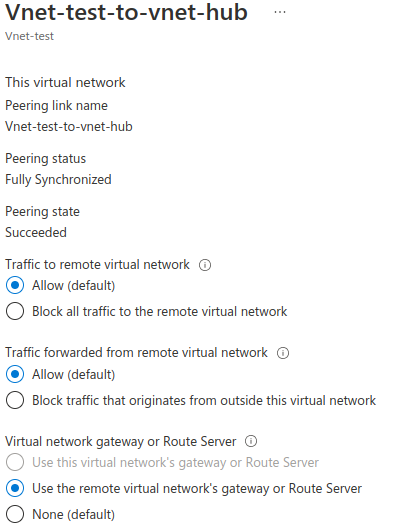
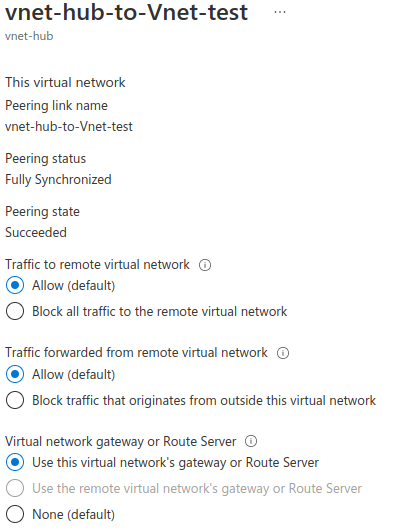
What did I miss? How to define the proper routing to make my resources in Vnet-test able to reach on-prem instances through the Virtual Gateway?
Thanks a lot!
Azure VPN Gateway
Azure Virtual Network
-
 GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft Employee
GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft EmployeeOct 18, 2022, 12:32 PM Hello @Nicolas ESPIAU ,
Welcome to Microsoft Q&A Platform. Thank you for reaching out & hope you are doing well.
I understand that you have enabled gateway transit in your peered Vnet to use the VPN gateway in the hub Vnet but are unable to access the on-prem resources from the peered vnet.
Could you please help with the below details?
1) Are there any UDRs associated to the subnets in your peered Vnet (Vnet-test)?
2) Could you check the effective routes for the VM in peered Vnet (Vnet-test) and validate if you are getting the on-premises routes?
Refer : https://learn.microsoft.com/en-us/azure/virtual-network/diagnose-network-routing-problem#diagnose-using-azure-portalRegards,
Gita -
Nicolas ESPIAU • 51 Reputation points
Oct 18, 2022, 2:34 PM Hi @GitaraniSharma-MSFT ,
First of all, thank you for answering.
I've checked what you asked:
- I have multiple subnets in my peered Vnet (vnet-test), one of them has a route table attached with custom routes added by AKS, but system routes haven't been overwritten. The other subnets have no route table associated. The issue I mentioned is present on all subnets.
- I've checked the effective routes of the 2 vms I use for my tests (one in the same subnet as AKS, lets call it subnet-priv1, and the other in an empty subnet, lets call it subnet-priv2).
In both of them I can validate that the routes to on-prem are present, and point to Virtual Network Gateway as next hop, and IP is the public ip of the Virtual Gateway.
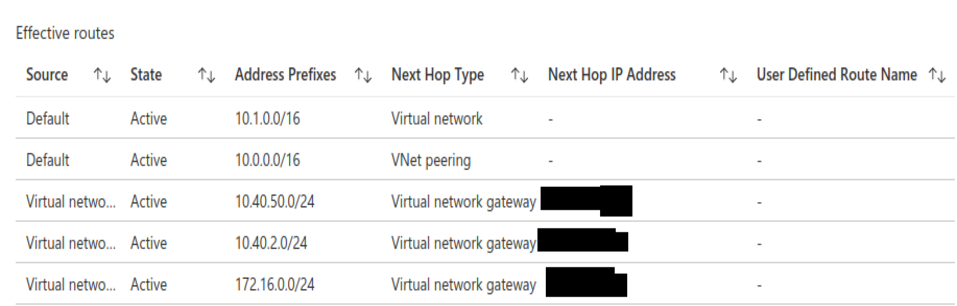
Tell me if I'm wrong but it's exactly what's expected here?
On the vm side, when I try
route -nI don't see all these routes. I guess it's normal since it's been handling on the Vnet side. -
Nicolas ESPIAU • 51 Reputation points
Oct 18, 2022, 4:04 PM I've ran some diagnostics with Network Watcher.
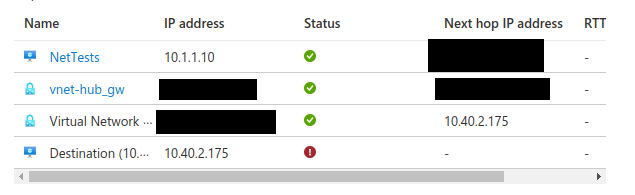
Our Network Security Officer opened the flow from 10.1.0.0/16 but told me that they didn't detect any traffic.
I tried the same from a VM in the Vnet-hub and this time the test was ok (on prem resource was reachable) but they saw the traffic from the monitoring tools.
-
 GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft Employee
GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft EmployeeOct 19, 2022, 4:59 PM Hello @Nicolas ESPIAU ,
Is there any address space overlapping between your on-premises network and peered Vnet?
Also, I see the network watcher test above shows that it reaches the VPN gateway but then it fails.
Are there any NSGs on your GatewaySubnet?Is this traffic allowed on your on-premises Firewall?
And the Site to Site VPN configuration on your on-premises should have both your hub Vnet and peered Vnet address spaces added, is it configured correctly?Regards,
Gita -
Nicolas ESPIAU • 51 Reputation points
Oct 20, 2022, 10:00 AM There is no overlapping between on-prem and any Vnet in Azure.
There is no NSG attached to the GatewaySubnet.
The traffic is allowed on our on-prem Firewall.
For the last part, I'll have to double check with our Network Engineer, he told me that everything was configured properly but I'll make him check once again. -
 GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft Employee
GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft EmployeeOct 26, 2022, 1:13 PM Hello @Nicolas ESPIAU ,
Could you please provide an update on this post?
Is the issue still persisting?Regards,
Gita -
 GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft Employee
GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft EmployeeOct 31, 2022, 1:13 PM Hello @Nicolas ESPIAU , do you have any new updates on this issue?
-
 GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft Employee
GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft EmployeeNov 3, 2022, 1:48 PM Hello @Nicolas ESPIAU , Could you please provide an update on this post?
-
Nicolas ESPIAU • 51 Reputation points
Nov 3, 2022, 1:51 PM Sorry for the late answer, I had no "reply" button so far.
We are still facing the same issue.
We tried to recreate the tunnel using the VTI and following the docs but it did not work, so to bypass this issue we had to mount 3 tunnels, for each VNet IP range.
Which is very annoying and we would like to make it work with only one tunnel and VTI conf. -
 GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft Employee
GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft EmployeeNov 3, 2022, 1:57 PM Hello @Nicolas ESPIAU ,
Thank you for the update.
Could you please let me know what is the make and model of your on-prem VPN device?
Regards,
Gita -
Nicolas ESPIAU • 51 Reputation points
Nov 3, 2022, 2:08 PM We're working with a Stormshield instance
-
 GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft Employee
GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft EmployeeNov 3, 2022, 3:06 PM Hello @Nicolas ESPIAU ,
Stormshield VPN is not an Azure validated VPN device.
If your device is not listed in the Validated VPN devices table, your device still may work with a Site-to-Site connection. The recommendation is to contact your device manufacturer for additional support and configuration instructions.
Refer : https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-devicesBut I would advise you to collect packet captures from your VPN gateway to see what is causing this issue.
Refer : https://learn.microsoft.com/en-us/azure/vpn-gateway/packet-capture#start-packet-capture---portalIf that doesn't help, we may need to raise a support ticket to get further assistance on this issue. So if you have a support plan, I request you file a support ticket, else please do let us know, we will try and help you get a one-time free technical support.
Regards,
Gita -
Ho, Eddie • 25 Reputation points
Nov 28, 2023, 11:41 AM Hi I am having exactly the same problem, the peered VNET2 cannot communicate with the S2S vpn (peered Vnet1).
Effective route for the Virtual network gateway (transit gateway enabled) exist and correct, NSG with same cidr has been added also to inbound allow, just traffic doesnt seem to flow.
It looks like the VNet peering is not passing the traffic through, how to check vnet peering logs?
-
 GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft Employee
GitaraniSharma-MSFT • 49,811 Reputation points • Microsoft EmployeeNov 28, 2023, 12:54 PM Hello @Ho, Eddie ,
Please check the below:
- Check if there are any UDRs associated to the spoke subnets with "Propagate gateway routes" option (previously referred to as Disable BGP route propagation) set to NO. Refer: https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-peering-gateway-transit
- Check your on-premises device to verify that it has the remote/spoke virtual network address space added. Refer: https://learn.microsoft.com/en-us/azure/virtual-network/virtual-network-troubleshoot-peering-issues#both-the-hub-virtual-network-and-the-spoke-virtual-network-do-not-have-a-vpn-gateway
- Check if there is any address space overlapping between your on-premises network and peered Vnet.
Regards,
Gita
Sign in to comment
1 answer
Sort by: Most helpful
-
 Joe Carlyle • 661 Reputation points • MVP
Joe Carlyle • 661 Reputation points • MVPOct 19, 2022, 1:06 PM -
Nicolas ESPIAU • 51 Reputation points
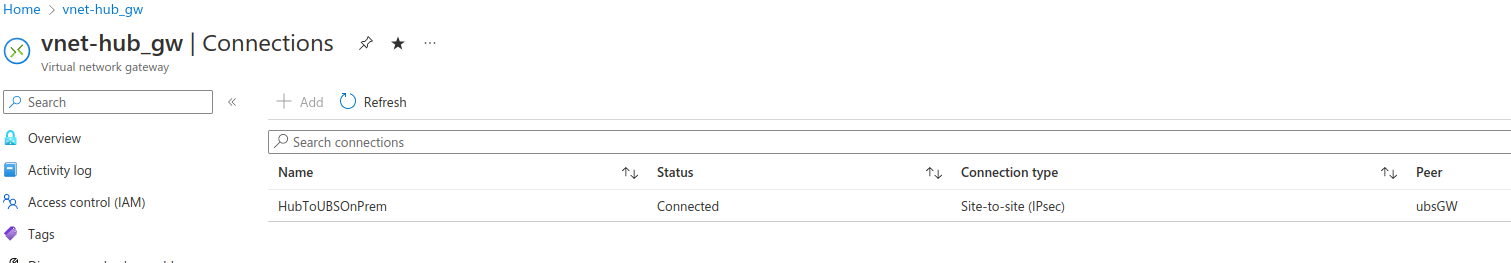
Oct 20, 2022, 9:57 AM That may be a lead.
You mean delete the whole Virtual Gateway ? The Local Gateway ? Or just the Connection between the Virtual Gateway and the Local Gateway ?
-
 Joe Carlyle • 661 Reputation points • MVP
Joe Carlyle • 661 Reputation points • MVPOct 20, 2022, 11:00 AM Don't delete either gateway resource, just delete and recreate the Connection resource you have screenshotted. Ensure you have captured details like PSK and IPsec custom settings so you can recreate identically.
-
Nicolas ESPIAU • 51 Reputation points
Oct 21, 2022, 8:21 AM That's what I've done and it did change anything. I'm still investigating.
-
 Joe Carlyle • 661 Reputation points • MVP
Joe Carlyle • 661 Reputation points • MVPOct 21, 2022, 12:05 PM This would indicate an issue with the tunnel itself on-prem then. Check encapsulation settings and ensure any NAT settings are correct relative to spoke VNET
-
carlintveld • 26 Reputation points
Aug 15, 2023, 12:55 PM We experience a comparable issue. What was ultimately the solution?
-
Ho, Eddie • 25 Reputation points
Nov 28, 2023, 11:44 AM Hi I am having exactly the same problem, the peered VNET2 cannot communicate with the S2S vpn (peered Vnet1).
Effective route for the Virtual network gateway (transit gateway enabled) exist and correct, NSG with same cidr has been added also to inbound allow, just traffic doesnt seem to flow.
It looks like the VNet peering is not passing the traffic through, how to check vnet peering logs?
I also have a vm on VNet1 and it can talk to remote side of the VPN no problem, its the spoke side of the VNet (2) is the problem
Running a "connection troubleshoot", the next hop is for the public ip of the Azure VNG (see image)
-
Sven Bracke • 0 Reputation points
Aug 9, 2024, 2:46 PM Would like to add that i experience a similar issue with the difference that i have a Fortigate NVA deployed in the HUB VNET where all traffic is passing through.
So the Virtual network gateway has a tunnel with an on-prem firewall and then has a UDR route for the spoke address range pointing to the NVA as next-hop.
When performing a ping from an on-prem server to a VM in a spoke (peered) VNET i see traffic going back and forth over the fortigate (TCPDUMP), so the VPN from on-prem to the HUB VNET works, and from HUB to Spoke, the VM in the Spoke answers and sends the traffic back to the NVA who sends it towards the virtual network gateway and thats where the traffic seems to drop dead cause we do not see it arrive at the on-prem firewall (VPN).
Sign in to comment -