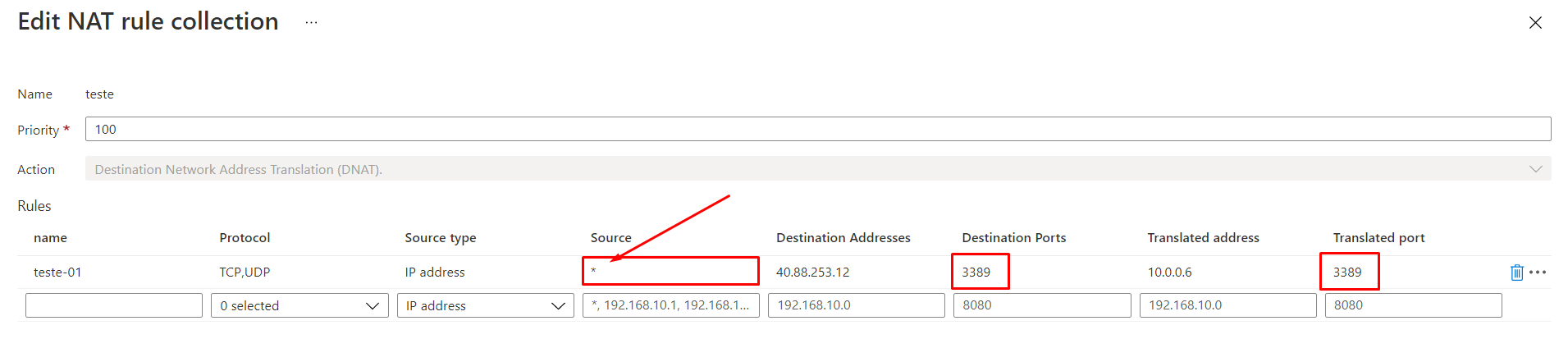
<< Resurfacing the information from comments here for broader community usage>>
@VolginRnB - Currently below are service-specific logs which are available via diagnostic logging for Azure Firewall. Please review here for additional details.
- AzureFirewallApplicationRule
- AzureFirewallNetworkRule
- AzureFirewallDnsProxy
However for your requirement to alert on specific NAT rule collection , I don't think we have out of box ingestion to Log analytics and probably a custom solution of getting the firewall NAT rule collection and ingesting into Log Analytics workspace and then alerting on top of it, should help.
You can leverage get-azfirewallpolicyrulecollectiongroup to get the rule collection , below snippet might help you to scope it down to the source you are looking for.
$ruleCollection = Get-AzFirewallPolicyRuleCollectionGroup -AzureFirewallPolicyName MyfirewallPolicy -Name DefaultNetworkRuleCollectionGroup -ResourceGroupName Networking-Resources
$ruleCollection[0].Properties.RuleCollection.RulesText | select-string -SimpleMatch "*"
Hope the above information helps. Please revert back if you have any further queries.