Tutorial: Microsoft Entra SSO integration with Kemp LoadMaster Microsoft Entra integration
In this tutorial, you'll learn how to integrate Kemp LoadMaster Microsoft Entra integration with Microsoft Entra ID. When you integrate Kemp LoadMaster Microsoft Entra integration with Microsoft Entra ID, you can:
- Control in Microsoft Entra ID who has access to Kemp LoadMaster Microsoft Entra integration.
- Enable your users to be automatically signed-in to Kemp LoadMaster Microsoft Entra integration with their Microsoft Entra accounts.
- Manage your accounts in one central location.
To get started, you need the following items:
- A Microsoft Entra subscription. If you don't have a subscription, you can get a free account.
- Kemp LoadMaster Microsoft Entra integration single sign-on (SSO) enabled subscription.
Note
This integration is also available to use from Microsoft Entra US Government Cloud environment. You can find this application in the Microsoft Entra US Government Cloud Application Gallery and configure it in the same way as you do from public cloud.
In this tutorial, you configure and test Microsoft Entra SSO in a test environment.
- Kemp LoadMaster Microsoft Entra integration supports IDP initiated SSO.
To configure the integration of Kemp LoadMaster Microsoft Entra integration into Microsoft Entra ID, you need to add Kemp LoadMaster Microsoft Entra integration from the gallery to your list of managed SaaS apps.
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Identity > Applications > Enterprise applications > New application.
- In the Add from the gallery section, type Kemp LoadMaster Microsoft Entra integration in the search box.
- Select Kemp LoadMaster Microsoft Entra integration from results panel and then add the app. Wait a few seconds while the app is added to your tenant.
Alternatively, you can also use the Enterprise App Configuration Wizard. In this wizard, you can add an application to your tenant, add users/groups to the app, assign roles, as well as walk through the SSO configuration as well. Learn more about Microsoft 365 wizards.
Configure and test Microsoft Entra SSO with Kemp LoadMaster Microsoft Entra integration using a test user called B.Simon. For SSO to work, you need to establish a link relationship between a Microsoft Entra user and the related user in Kemp LoadMaster Microsoft Entra integration.
To configure and test Microsoft Entra SSO with Kemp LoadMaster Microsoft Entra integration, perform the following steps:
Configure Microsoft Entra SSO - to enable your users to use this feature.
- Create a Microsoft Entra test user - to test Microsoft Entra single sign-on with B.Simon.
- Assign the Microsoft Entra test user - to enable B.Simon to use Microsoft Entra single sign-on.
Configure Kemp LoadMaster Microsoft Entra integration SSO - to configure the single sign-on settings on application side.
Configuring Kerberos Based Authentication
- Create a Kerberos Delegation Account for Kemp LoadMaster Microsoft Entra integration
- Kemp LoadMaster Microsoft Entra integration KCD (Kerberos Delegation Accounts)
- Kemp LoadMaster Microsoft Entra integration ESP
- Create Kemp LoadMaster Microsoft Entra integration test user - to have a counterpart of B.Simon in Kemp LoadMaster Microsoft Entra integration that is linked to the Microsoft Entra representation of user.
Test SSO - to verify whether the configuration works.
Follow these steps to enable Microsoft Entra SSO.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > Kemp LoadMaster Microsoft Entra integration > Single sign-on.
On the Select a single sign-on method page, select SAML.
On the Set up single sign-on with SAML page, click the pencil icon for Basic SAML Configuration to edit the settings.
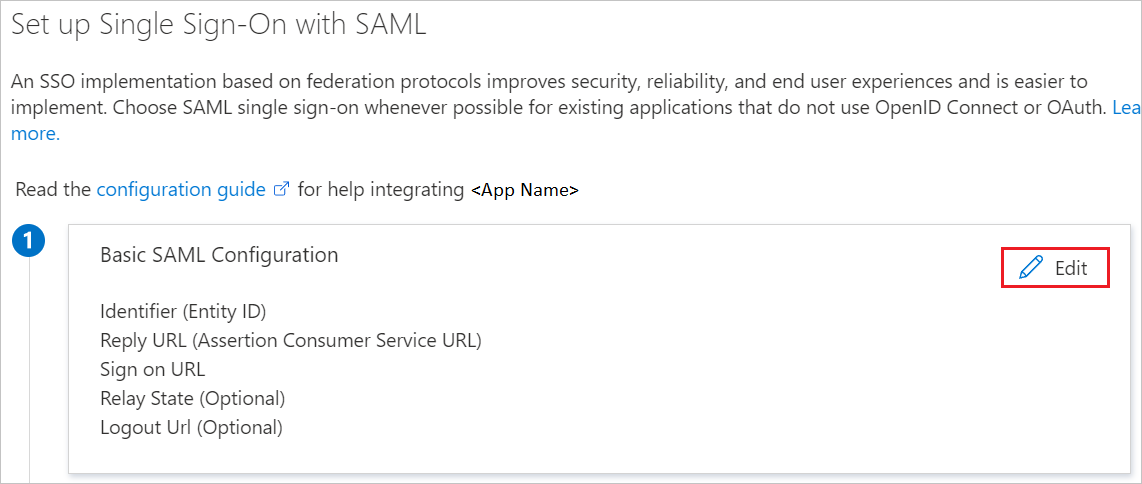
On the Basic SAML Configuration section, enter the values for the following fields:
a. In the Identifier (Entity ID) text box, type a URL:
https://<KEMP-CUSTOMER-DOMAIN>.com/b. In the Reply URL text box, type a URL:
https://<KEMP-CUSTOMER-DOMAIN>.com/Note
These values are not real. Update these values with the actual Identifier and Reply URL. Contact Kemp LoadMaster Microsoft Entra integration Client support team to get these values. You can also refer to the patterns shown in the Basic SAML Configuration section.
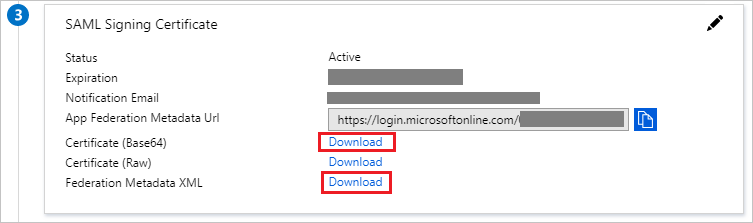
On the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Certificate (Base64) and Federation Metadata XML, select Download to download the certificate and federation metadata XML files and save it on your computer.
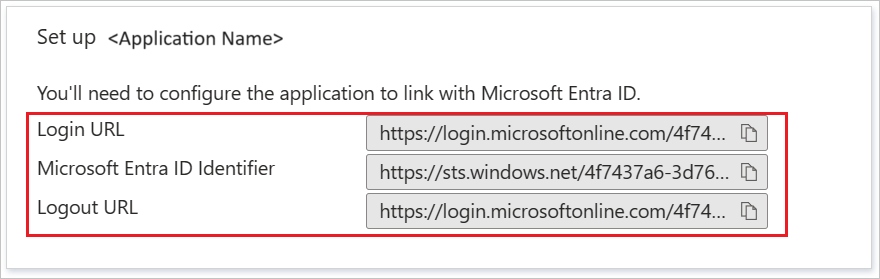
On the Set up Kemp LoadMaster Microsoft Entra integration section, copy the appropriate URL(s) based on your requirement.
In this section, you'll create a test user called B.Simon.
- Sign in to the Microsoft Entra admin center as at least a User Administrator.
- Browse to Identity > Users > All users.
- Select New user > Create new user, at the top of the screen.
- In the User properties, follow these steps:
- In the Display name field, enter
B.Simon. - In the User principal name field, enter the username@companydomain.extension. For example,
B.Simon@contoso.com. - Select the Show password check box, and then write down the value that's displayed in the Password box.
- Select Review + create.
- In the Display name field, enter
- Select Create.
In this section, you'll enable B.Simon to use single sign-on by granting access to Kemp LoadMaster Microsoft Entra integration.
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Identity > Applications > Enterprise applications > Kemp LoadMaster Microsoft Entra integration.
- In the app's overview page, select Users and groups.
- Select Add user/group, then select Users and groups in the Add Assignment dialog.
- In the Users and groups dialog, select B.Simon from the Users list, then click the Select button at the bottom of the screen.
- If you are expecting a role to be assigned to the users, you can select it from the Select a role dropdown. If no role has been set up for this app, you see "Default Access" role selected.
- In the Add Assignment dialog, click the Assign button.
Go to Kemp LoadMaster Microsoft Entra integration LoadMaster Web UI > Virtual Services > Add New.
Click Add New.
Specify the Parameters for the Virtual Service.
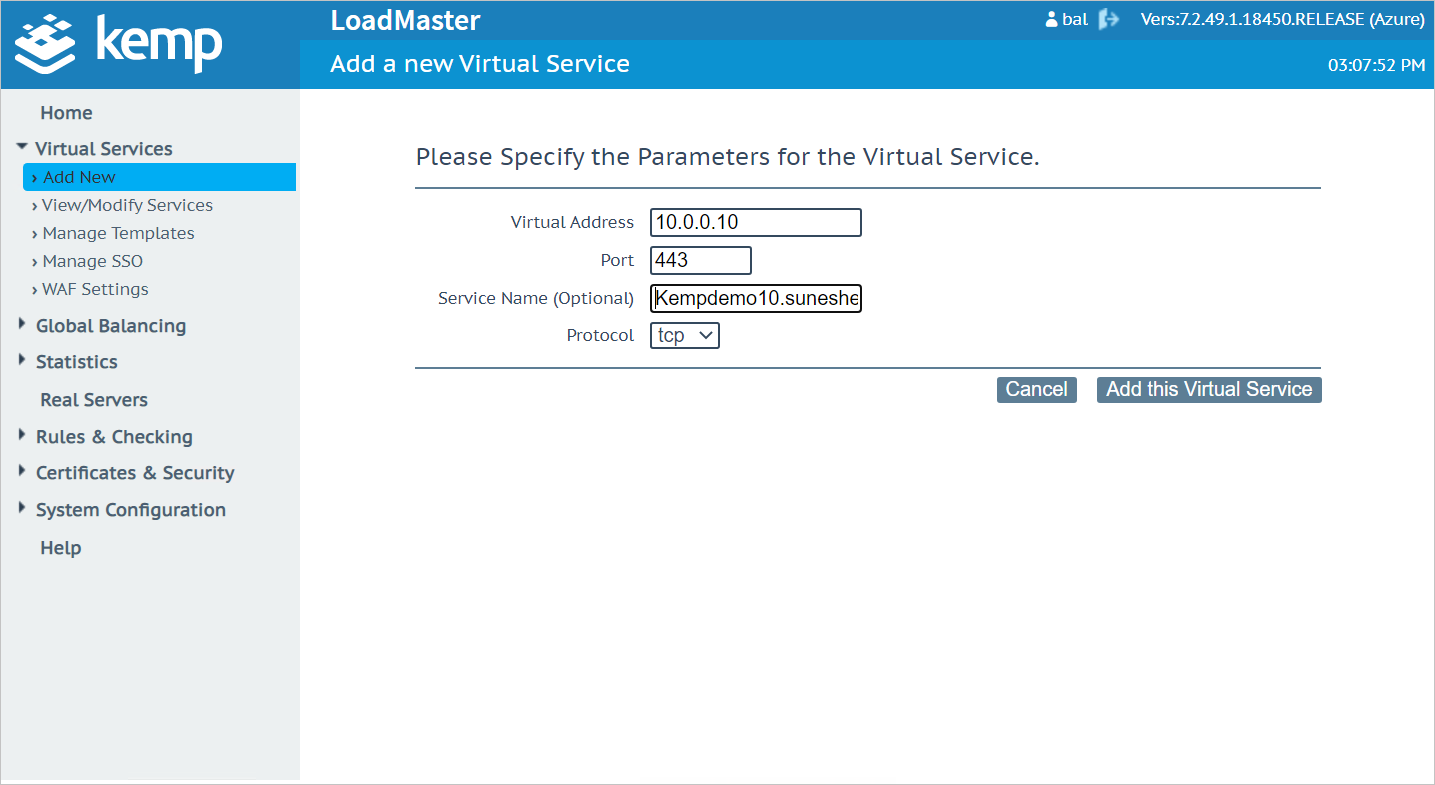
a. Virtual Address
b. Port
c. Service Name (Optional)
d. Protocol
Navigate to Real Servers section.
Click on Add New.
Specify the Parameters for the Real Server.

a. Select Allow Remote Addresses
b. Type in Real Server Address
c. Port
d. Forwarding method
e. Weight
f. Connection Limit
g. Click on Add This Real Server
Go to Kemp LoadMaster Microsoft Entra integration Web Portal > Certificates & Security > SSL Certificates.
Under Manage Certificates > Certificate Configuration.
Click Import Certificate.
Specify the name of the file that contains the certificate. The file can also hold the private key. If the file does not contain the private key, then the file containing the private key must also be specified. The certificate can be in either .PEM or .PFX (IIS) format.
Click on Choose file on Certificate File.
Click on Key File (optional).
Click on Save.
Go to Kemp LoadMaster Web UI > Virtual Services > View/Modify Services.
Click in Modify under Operation.
Click on SSL Properties, (which operates at Layer 7).
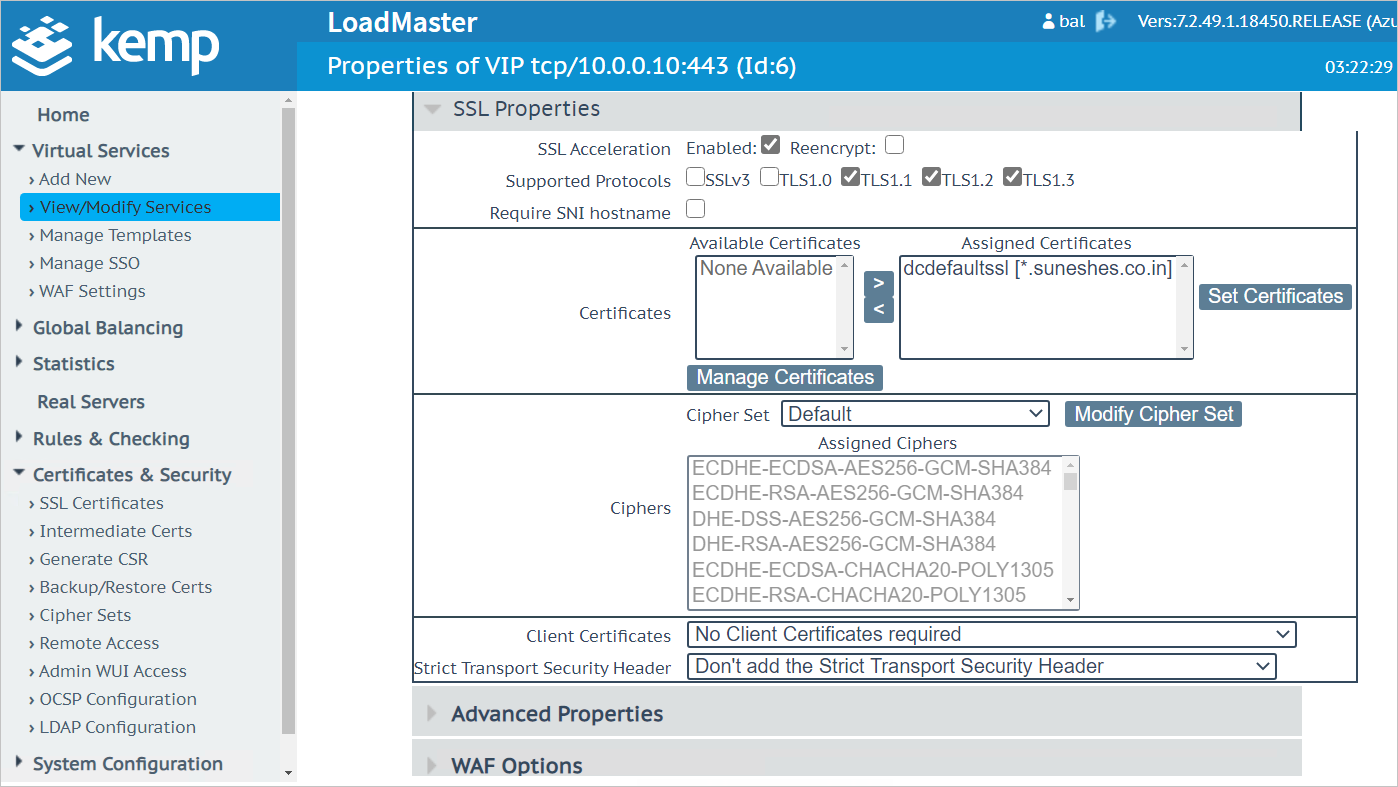
a. Click on Enabled in SSL Acceleration.
b. Under Available Certificates, select the imported certificate and click on
>symbol.c. Once the desired SSL certificate appears in Assigned Certificates, click on Set Certificates.
Note
Make sure you click on the Set Certificates.
Go to Kemp LoadMaster Microsoft Entra integration Web Console.
Click Intermediate Certificates under Certificates and Authority.

a. Click choose file in Add a new Intermediate Certificate.
b. Navigate to certificate file previously downloaded from Microsoft Entra Enterprise Application.
c. Click on Open.
d. Provide a Name in Certificate Name.
e. Click on Add Certificate.
Go to Manage SSO under Virtual Services.
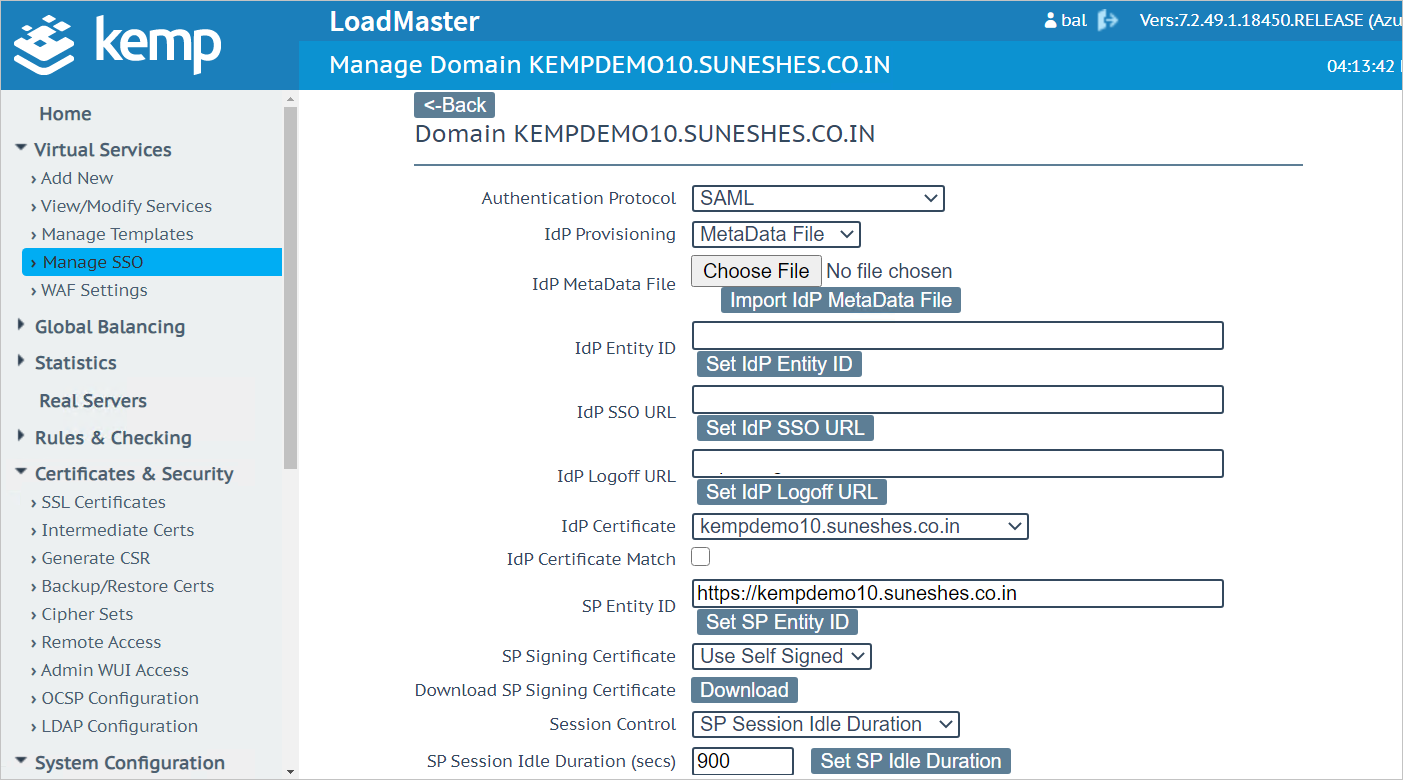
a. Click Add under Add new Client Side Configuration after giving it a name.
b. Select SAML under Authentication Protocol.
c. Select MetaData File under IdP Provisioning.
d. Click on Choose File.
e. Navigate to previously downloaded XML from Azure portal.
f. Click on Open and click on Import IdP MetaData file.
g. Select the intermediate certificate from IdP Certificate.
h. Set the SP Entity ID which should match the identity created in Azure portal.
i. Click on Set SP Entity ID.
On Kemp LoadMaster Microsoft Entra integration Web Console.
Click on Virtual Services.
Click on View/Modify Services.
Click on Modify and navigate to ESP Options.

a. Click on Enable ESP.
b. Select SAML in Client Authentication Mode.
c. Select previously created Client Side Authentication in SSO Domain.
d. Type in host name in Allowed Virtual Hosts and click on Set Allowed Virtual Hosts.
e. Type /* in Allowed Virtual Directories (based on access requirements) and click on Set Allowed Directories.
Browse to the application URL.
You should see your tenanted login page instead of unauthenticated access previously.
Create a user Account (in this example AppDelegation).
a. Select the Attribute Editor tab.
b. Navigate to servicePrincipalName.
c. Select servicePrincipalName and click Edit.
d. Type http/kcduser in the Value to add field and click Add.
e. Click Apply and OK. The window must close before you open it again (to see the new Delegation tab).
Open the user properties window again and the Delegation tab becomes available.
Select the Delegation tab.

a. Select Trust this user for delegation to specified services only.
b. Select Use any authentication protocol.
c. Add the Real Servers and add http as the service.
d. Select the Expanded check box.
e. You can see all servers with both the host name and the FQDN.
f. Click on OK.
Note
Set the SPN on the Application / Website as applicable. To access application when the application pool identity has been set. To access the IIS application by using the FQDN name, go to Real Server command prompt and type SetSpn with required parameters. For example, Setspn –S HTTP/sescoindc.sunehes.co.in suneshes\kdcuser.
Go to Kemp LoadMaster Microsoft Entra integration Web Console > Virtual Services > Manage SSO.
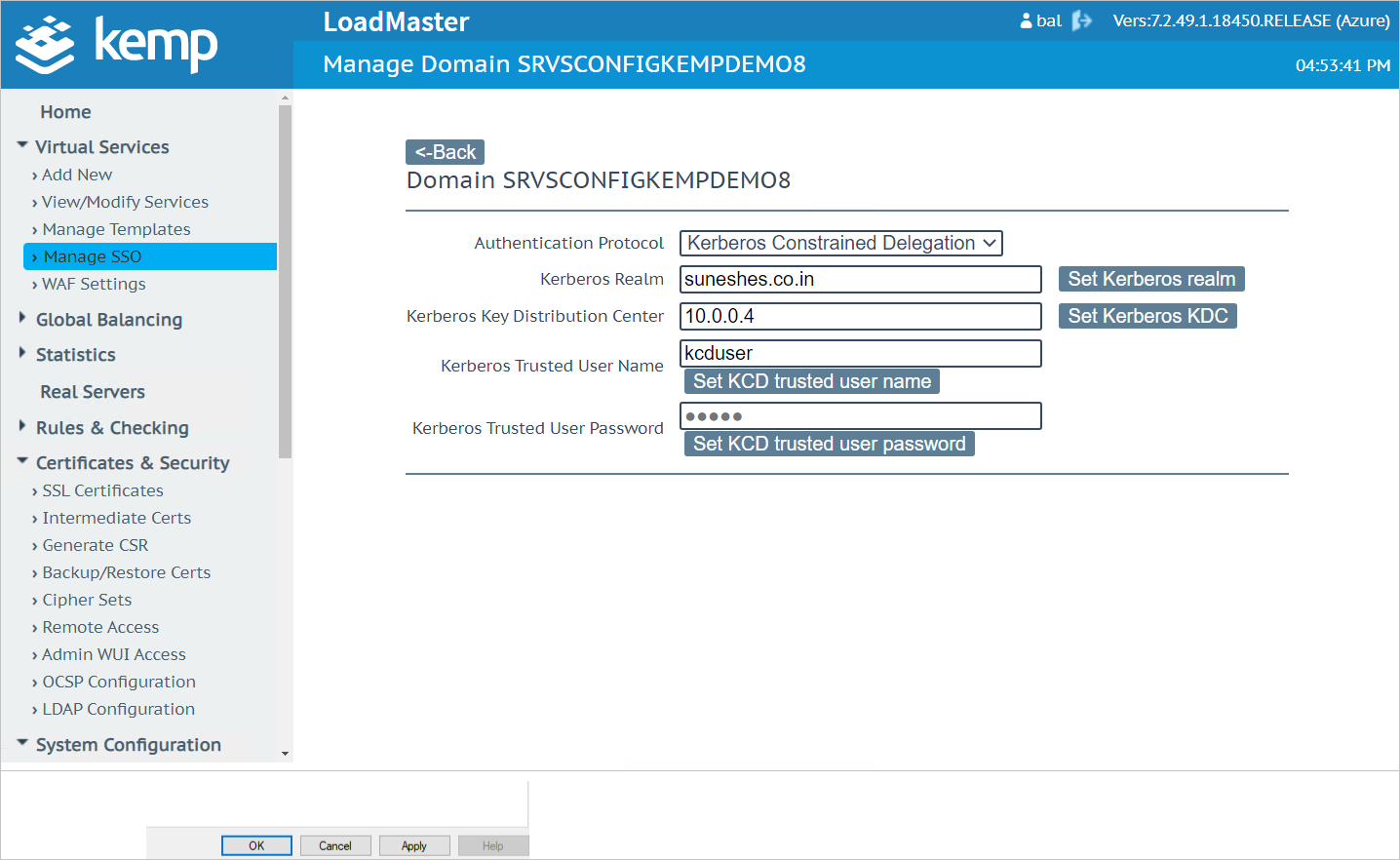
a. Navigate to Server Side Single Sign On Configurations.
b. Type Name in Add new Server-Side Configuration and click on Add.
c. Select Kerberos Constrained Delegation in Authentication Protocol.
d. Type Domain Name in Kerberos Realm.
e. Click on Set Kerberos realm.
f. Type Domain Controller IP Address in Kerberos Key Distribution Center.
g. Click on Set Kerberos KDC.
h. Type KCD user name in Kerberos Trusted User Name.
i. Click on Set KDC trusted user name.
j. Type password in Kerberos Trusted User Password.
k. Click on Set KCD trusted user password.
Go to Virtual Services > View/Modify Services.
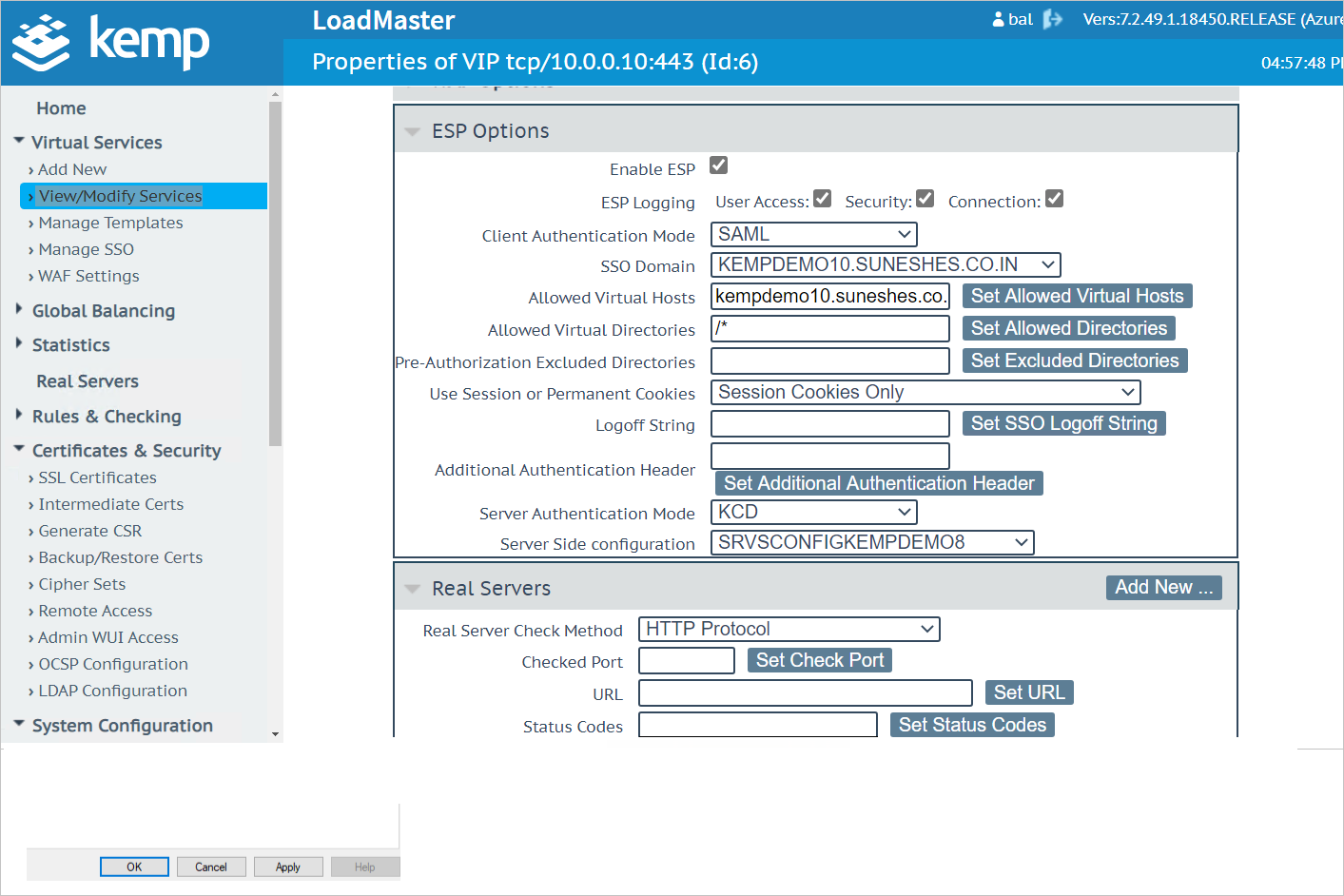
a. Click on Modify on the Nick Name of the Virtual Service.
b. Click on ESP Options.
c. Under Server Authentication Mode, select KCD.
d. Under Server-Side configuration, select the previously created server-side profile.
In this section, you create a user called B.Simon in Kemp LoadMaster Microsoft Entra integration. Work with Kemp LoadMaster Microsoft Entra integration Client support team to add the users in the Kemp LoadMaster Microsoft Entra integration platform. Users must be created and activated before you use single sign-on.
In this section, you test your Microsoft Entra single sign-on configuration with following options.
Click on Test this application, and you should be automatically signed in to the Kemp LoadMaster Microsoft Entra integration for which you set up the SSO.
You can use Microsoft My Apps. When you click the Kemp LoadMaster Microsoft Entra integration tile in the My Apps, you should be automatically signed in to the Kemp LoadMaster Microsoft Entra integration for which you set up the SSO. For more information about the My Apps, see Introduction to the My Apps.
Once you configure Kemp LoadMaster Microsoft Entra integration you can enforce session control, which protects exfiltration and infiltration of your organization’s sensitive data in real time. Session control extends from Conditional Access. Learn how to enforce session control with Microsoft Defender for Cloud Apps.