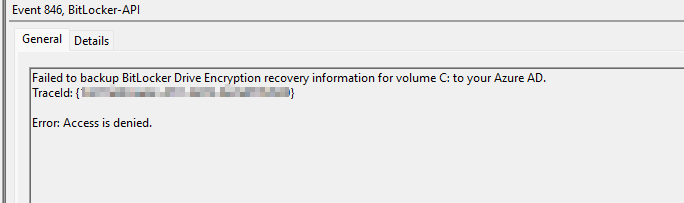
@Matt Pollock , Thanks for posting in our Q&A. From your description, I know that you have deployed encryption policy via Intune and successfully encrypted the device, but when backing up the recovery key, you get an error of access is denied was received. You try to run cmdlet using PowerShell as and admin and it worked, you want to know if there is any way to back up the recovery key automatically and not require admin rights. If there's any misunderstanding, feel free to let us know.
Based on my experience, recovery key can also be saved to Azure AD when we silently enable BitLocker which is for standard user (non-admin user) For our issue, could you firstly confirm if we have configured silently enable BitLocker in the following link?
https://learn.microsoft.com/en-us/mem/intune/protect/encrypt-devices#manage-bitlocker
Meanwhile, when a TPM startup PIN or startup key is required on a device, BitLocker can't silently enable on the device and instead requires interaction from the end user. Please ensure it is not set. And also check if the device meets the prerequisites.
After researching, I find there’s a known issue with the similar error as yours. Please check if you have other errors existing as well. If yes, try to install the latest update to see if the issue is fixed.
https://learn.microsoft.com/en-us/windows/security/information-protection/bitlocker/ts-bitlocker-intune-issues#issue-7
Please check the above information and if there’s any update, feel free to let us know.
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.