Events
Microsoft 365 Community Conference
May 6, 2 PM - May 9, 12 AM
Skill up for the era of AI at the ultimate community-led Microsoft 365 event, May 6-8 in Las Vegas.
Learn moreThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
If you're using Basic Mobility and Security, there might be devices that you can't manage with Basic Mobility and Security. If so, you should block Exchange ActiveSync app access to Microsoft 365 email for mobile devices that aren't supported by Basic Mobility and Security. Blocking Exchange ActiveSync app access helps secure your organization information across more devices.
Use these steps:
Sign in to Microsoft 365 with a Compliance administrator account.
In your browser, type: https://compliance.microsoft.com/basicmobilityandsecurity.
Go to Organization Setting tab.
Select Access restriction for unsupported MDM device and make sure Allow access (device enrollment is required) is selected.
To learn what devices Basic Mobility and Security supports, see Capabilities of Basic Mobility and Security.
Additionally, you can use Microsoft Graph PowerShell to get details about the devices in your organization that you set up for Basic Mobility and Security.
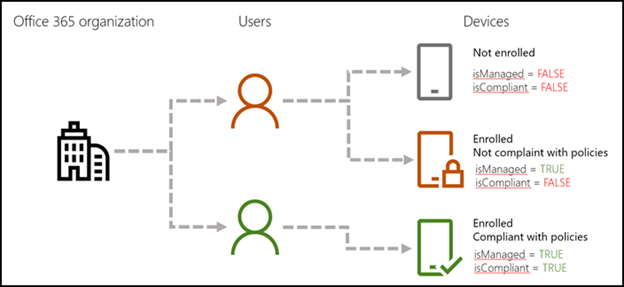
Here's a breakdown for the device details available to you.
| Detail | What to look for in PowerShell |
|---|---|
| Device is enrolled in Basic Mobility and Security. For more info, see Enroll your mobile device using Basic Mobility and Security | The value of the isManaged parameter is: True= device is enrolled. False= device isn't enrolled. |
| Device is compliant with your device security policies. For more info, see Create device security policies | The value of the isCompliant parameter is: True = device is compliant with policies. False = device isn't compliant with policies. |
Note
The commands and scripts that follow also return details about any devices managed by Microsoft Intune.
Here are a few things you need to set up to run the commands and scripts that follow:
For more info on these steps, see Connect to Microsoft 365 with PowerShell.
Install the Microsoft Graph PowerShell SDK for Windows PowerShell with these steps:
Open an administrator-level PowerShell command prompt.
Run the following command:
Install-Module Microsoft.Graph -Scope AllUsers
If prompted to install the NuGet provider, type Y and press ENTER.
If prompted to install the module from PSGallery, type Y and press ENTER.
After installation, close the PowerShell command window.
In Powershell window, run the following command.
Connect-MgGraph -Scopes Device.Read.All, User.Read.All
A popup opens for you to sign in. Provide the credentials of your Administrative Account and log in.
If your account has the necessary permissions, you see "Welcome To Microsoft Graph!" in the Powershell window.
Note
You can skip this step if you're already set up to run PowerShell scripts.
To run the Get-GraphUserDeviceComplianceStatus.ps1 script, you need to enable the running of PowerShell scripts.
From your Windows Desktop, select Start, and then type Windows PowerShell. Right-click Windows PowerShell, and then select Run as administrator.
Run the following command.
Set-ExecutionPolicy RemoteSigned
When prompted, type Y and then press Enter.
Open the Microsoft Azure Active Directory module for Windows PowerShell.
Run the following command.
Get-MgDevice -All -ExpandProperty "registeredOwners" | Where-Object {($_.RegisteredOwners -ne $null) -and ($_.RegisteredOwners.Count -gt 0)}
For more examples, see Get-MgDevice.
First, save the script to your computer.
Copy and paste the following text into Notepad.
param (
[Parameter(Mandatory = $false)]
[PSObject[]]$users = @(),
[Parameter(Mandatory = $false)]
[Switch]$export,
[Parameter(Mandatory = $false)]
[String]$exportFileName = "UserDeviceOwnership_" + (Get-Date -Format "yyMMdd_HHMMss") + ".csv",
[Parameter(Mandatory = $false)]
[String]$exportPath = [Environment]::GetFolderPath("Desktop")
)
#Clearing the screen
Clear-Host
#Preparing the output object
$deviceOwnership = @()
if ($users.Count -eq 0) {
Write-Output "No user has been provided, gathering data for all devices in the tenant"
#Getting all Devices and their registered owners
$devices = Get-MgDevice -All -Property * -ExpandProperty registeredOwners
#For each device which has a registered owner, extract the device data and the registered owner data
foreach ($device in $devices) {
$DeviceOwners = $device | Select-Object -ExpandProperty 'RegisteredOwners'
#Checking if the DeviceOwners Object is empty
if ($DeviceOwners -ne $null) {
foreach ($DeviceOwner in $DeviceOwners) {
$OwnerDictionary = $DeviceOwner.AdditionalProperties
$OwnerDisplayName = $OwnerDictionary.Item('displayName')
$OwnerUPN = $OwnerDictionary.Item('userPrincipalName')
$OwnerID = $deviceOwner.Id
$deviceOwnership += [PSCustomObject]@{
DeviceDisplayName = $device.DisplayName
DeviceId = $device.DeviceId
DeviceOSType = $device.OperatingSystem
DeviceOSVersion = $device.OperatingSystemVersion
DeviceTrustLevel = $device.TrustType
DeviceIsCompliant = $device.IsCompliant
DeviceIsManaged = $device.IsManaged
DeviceObjectId = $device.Id
DeviceOwnerID = $OwnerID
DeviceOwnerDisplayName = $OwnerDisplayName
DeviceOwnerUPN = $OwnerUPN
ApproximateLastLogonTimestamp = $device.ApproximateLastSignInDateTime
}
}
}
}
}
else {
#Checking that userid is present in the users object
Write-Output "List of users has been provided, gathering data for all devices owned by the provided users"
foreach ($user in $users) {
$devices = Get-MgUserOwnedDevice -UserId $user.Id -Property *
foreach ($device in $devices) {
$DeviceHashTable = $device.AdditionalProperties
$deviceOwnership += [PSCustomObject]@{
DeviceId = $DeviceHashTable.Item('deviceId')
DeviceOSType = $DeviceHashTable.Item('operatingSystem')
DeviceOSVersion = $DeviceHashTable.Item('operatingSystemVersion')
DeviceTrustLevel = $DeviceHashTable.Item('trustType')
DeviceDisplayName = $DeviceHashTable.Item('displayName')
DeviceIsCompliant = $DeviceHashTable.Item('isCompliant')
DeviceIsManaged = $DeviceHashTable.Item('isManaged')
DeviceObjectId = $device.Id
DeviceOwnerUPN = $user.UserPrincipalName
DeviceOwnerID = $user.Id
DeviceOwnerDisplayName = $user.DisplayName
ApproximateLastLogonTimestamp = $DeviceHashTable.Item('approximateLastSignInDateTime')
}
}
}
}
$deviceOwnership
if ($export) {
$exportFile = Join-Path -Path $exportPath -ChildPath $exportFileName
$deviceOwnership | Export-Csv -Path $exportFile -NoTypeInformation
Write-Output "Data has been exported to $exportFile"
}
Save it as a Windows PowerShell script file by using the file extension ".ps1". For example, Get-MgGraphDeviceOwnership.ps1.
Note
The script is also available for download on Github.
Open Powershell.
Go to the folder where you saved the script. For example, if you saved it to C:\PS-Scripts, run the following command.
cd C:\PS-Scripts
Run the following command to identify the user you want to get device details for. This example gets details for user@contoso.com.
$user = Get-MgUser -UserId "user@contoso.com"
Run the following command.
.\Get-GraphUserDeviceComplianceStatus.ps1 -users $user -Export
The information is exported to your Windows Desktop as a CSV file. You can specify the file name and path of the CSV.
Open Powershell.
Go to the folder where you saved the script. For example, if you saved it to C:\PS-Scripts, run the following command.
cd C:\PS-Scripts
Run the following command to identify the group you want to get device details for. This example gets details for users in the FinanceStaff group.
$groupId = Get-MgGroup -Filter "displayName eq 'FinanceStaff'" | Select-Object -ExpandProperty Id
$Users = Get-MgGroupMember -GroupId $groupId | Select-Object -ExpandProperty Id | % { Get-MgUser -UserId $_ }
Run the following command to initiate the script.
.\Get-GraphUserDeviceComplianceStatus.ps1 -User $Users -Export
The information is exported to your Windows Desktop as a CSV file. You can use more parameters to specify the file name and path of the CSV.
Overview of Basic Mobility and Security
Events
Microsoft 365 Community Conference
May 6, 2 PM - May 9, 12 AM
Skill up for the era of AI at the ultimate community-led Microsoft 365 event, May 6-8 in Las Vegas.
Learn more