Configure pipeline access to credential secrets
In this unit, you'll learn how to secure your pipeline secrets using Azure DevOps variables and hidden secrets. It's essential to ensure that your pipeline is secure and your secrets are protected. You'll also learn how to use Azure DevOps variables to store your secrets and how to access them within your pipeline.
Use variables to store values or encrypted secrets
Open your Azure DevOps project and navigate to the Pipelines section.
Click on Pipelines in the left-hand menu.
Open your pipeline (for example "eShopOnWeb"), or create a new one.
Click the Edit button in the right-top corner to edit your pipeline.
Click the Variables button.
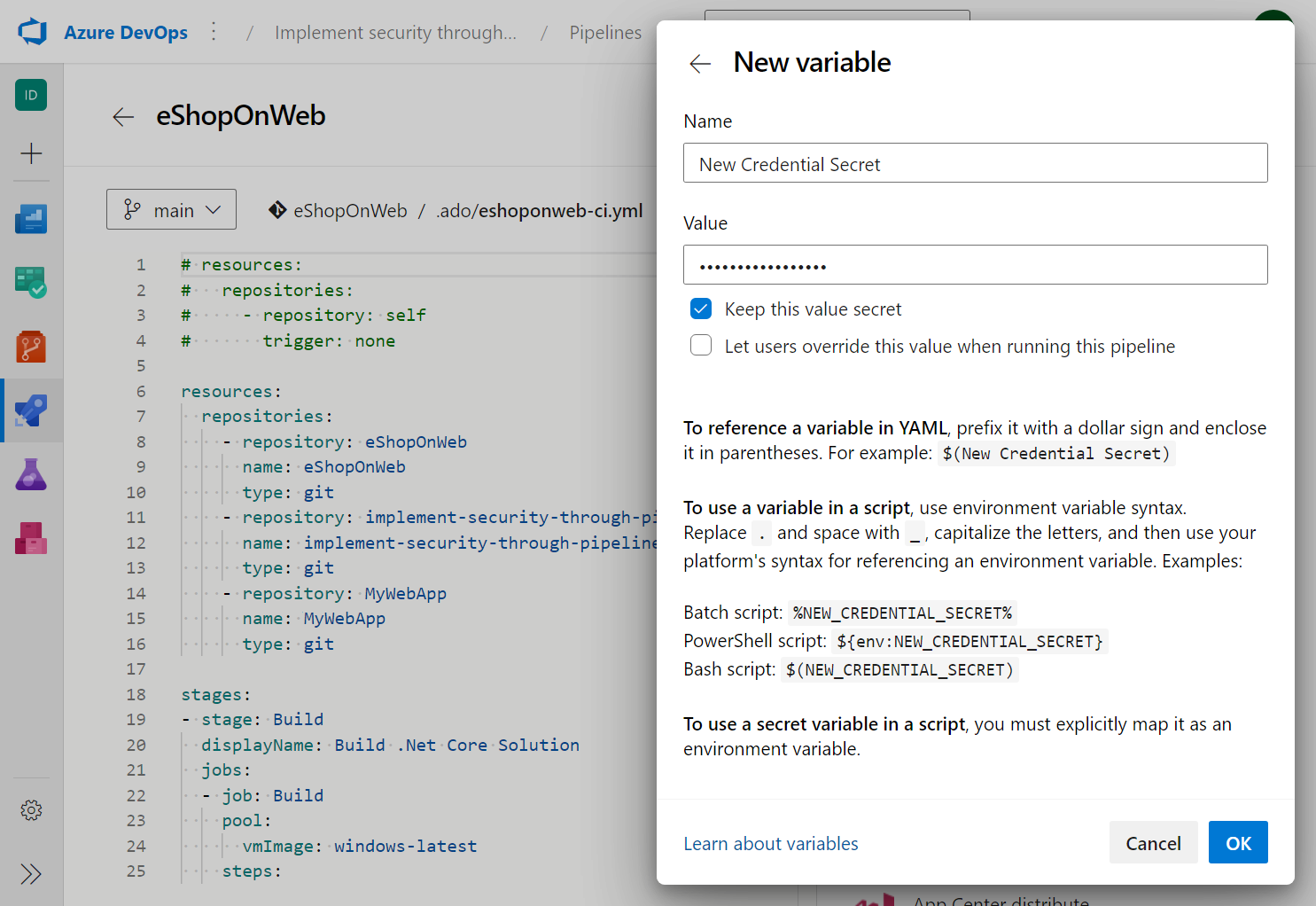
Click the New variable button to create a new variable.
Enter the name and value for your secret.
Check the "Keep this value secret" checkbox to encrypt your secret.
(Optional) Check the "Let users override this value when running this pipeline" checkbox to allow users to override the value of your variable at queue time.
Click the OK button to save your variable.
Click the Save button to save your pipeline.
Create a secret in an Azure DevOps variable group
Open your Azure DevOps project and navigate to the Pipelines section.
Click on Library in the left-hand menu.
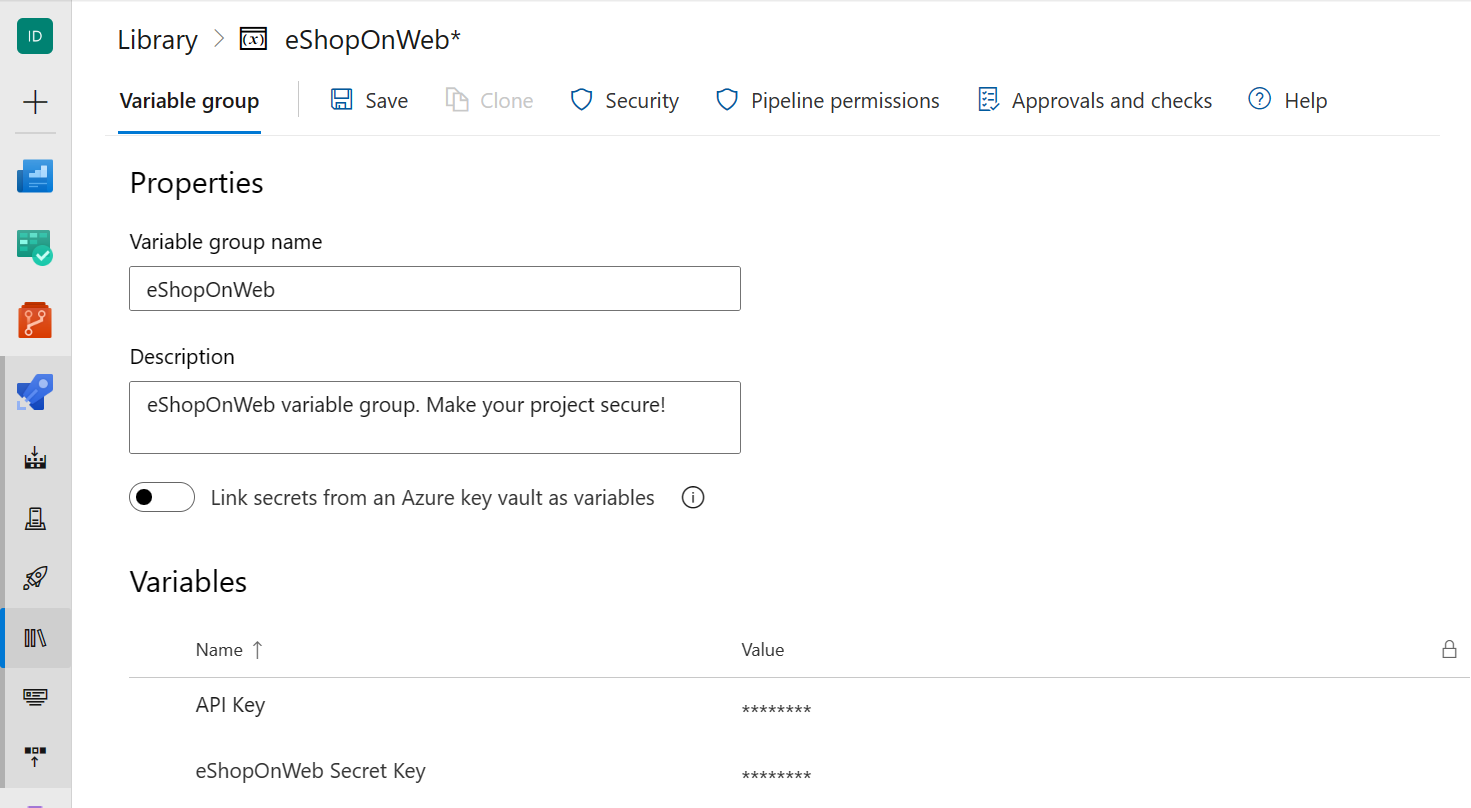
Open your variable group (for example "eShopOnWeb"), or create a new one.
Click the Add button to add a new variable.
Give your variable a name (for example "eShopOnWeb Secret Key").
Enter the value for your secret in the Value field.
Click the Save button to save your variable group.
Allow variable groups use in your pipeline
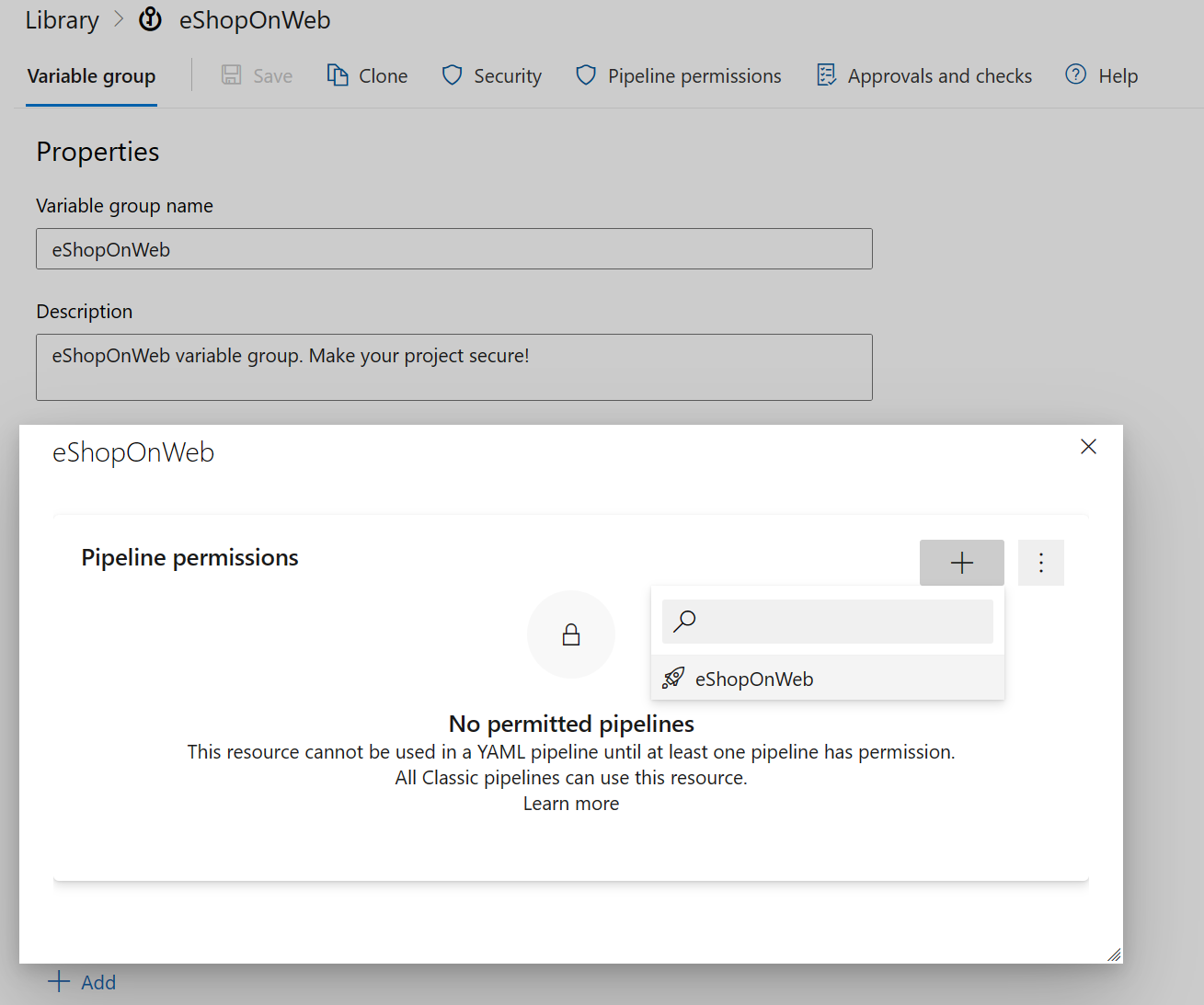
Open your Variable Group.
Click on the Pipeline permissions button.
Add the pipelines that will use this Variable Group.
Click the Save button to save your Variable Group.
Access secrets within your pipeline
Open your pipeline YAML file.
Add the following code to the top of your YAML file:
variables: - group: eShopOnWebReplace "eShopOnWeb" with the name of your variable group.
Use the following syntax to access your secrets within your pipeline:
$(eShopOnWeb Secret Key)Replace "eShopOnWeb Secret Key" with the name of your secret.
If you want to use your pipeline variables, you can use the following:
$(New Credential Secret)Note
The variable use will be the same, but one is coming from Variable Groups, and others from Variables from your pipeline UI.
Save your YAML file.
Secret variables are encrypted at rest with a 2048-bit RSA key. Secrets are available on the agent for tasks and scripts to use. Be careful about who has access to alter your pipeline.
You must decide whether to use the Variable Groups or the pipeline UI variables. The advantage of using the Variable Groups is that you can use the same variables in multiple pipelines. The advantage of using the pipeline UI variables is that you can override the variable's value at queue time.
Important
We try to mask secrets from appearing in Azure Pipelines output, but you still need to take precautions. Never echo secrets as output. Some operating systems log command line arguments. Never pass secrets on the command line. Instead, we suggest that you map your secrets into environment variables. We never mask the substrings of secrets. If, for example, "abc123" is set as a secret, "ABC" isn't masked from the logs. This is to avoid masking secrets at too granular of a level, making the logs unreadable. For this reason, secrets should not contain structured data. If, for example, "{ "foo": "bar" }" is set as a secret, "bar" isn't masked from the logs.
Challenge yourself
- Create a pipeline that retrieves a password from Azure DevOps Variable Group.
- Store a variable using a secret variable and use it in your pipeline.
- Override the variable of your variable in your pipeline with the secret variable at queue time.
For more information about secret variables, see: