Ask Learn
PreviewPlease sign in to use this experience.
Sign inThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
This unit explores how to access and secure log files in Azure Pipelines and secure them from displaying secrets in plain text.
The job details page provides detailed information about the pipeline run, including the tasks executed, their status, and any output generated.
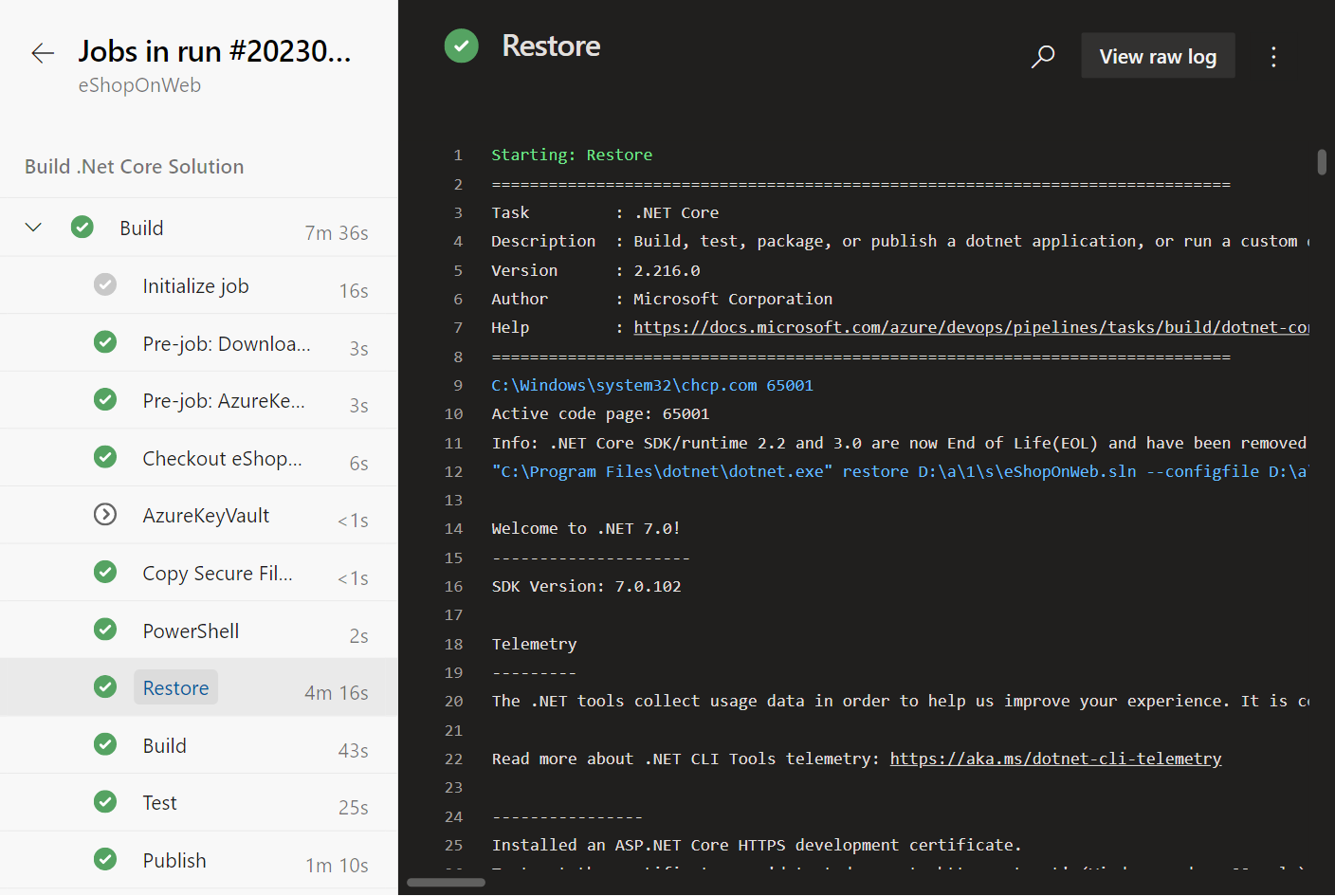
You can access the logs for a specific pipeline run by following these steps:
You can also access the logs for a specific task by clicking on the task name, or download logs for the entire job by clicking on the "Download logs" link.
Securing log files in Azure Pipelines is crucial to ensure that sensitive information, such as secrets and credentials, isn't displayed in plain text. Azure Pipelines attempts to scrub secrets from logs wherever possible. This filtering is on a best-effort basis and can't catch every way that secrets can be leaked. Avoid echoing secrets to the console, using them in command line parameters, or logging them to files.
There are many ways to secure log files in Azure Pipelines, including:
By using the issecret=true command in a script or task, you can ensure that specific values aren't displayed in the logs. When issecret is set to true, the variable's value is saved as secret and masked out from the log. Secret variables aren't passed into tasks as environment variables and must instead be passed as inputs.
Set a variable as a secret in a script or task:
steps:
- pwsh: |
Write-Host "##vso[task.setvariable variable=nonSecretVar;]Now you can see me!"
Write-Host "##vso[task.setvariable variable=secretVar;issecret=true]Now you don't!"
name: SetVariables
Read the variables:
- pwsh: |
Write-Host "The magician says: $env:NONSECRETVAR = Not a secret."
Write-Host "The magician says: $env:SECRETVAR = Yes, it's hidden, can't you see it? =)"
Write-Host "The magician says: $(secretVar) = It's encrypted."
Output:
The magician says: Now you can see me! = Not a secret.
The magician says: = Yes, it's hidden, can't you see it? =)
The magician says: *** = It's encrypted.
By using the isoutput=false command in a script or task, the variable's value is hidden out from the log.
Set a variable as a secret in a script or task:
steps:
- pwsh: |
Write-Host "##vso[task.setvariable variable=outputVarTrue;isoutput=true]No, it's not a secret!"
Write-Host "##vso[task.setvariable variable=outputVarFalse;isoutput=false]Yes, it's a secret!"
name: SetVariables
Read the variables:
- pwsh: |
Write-Host "Hidden out from the log: $env:SETVARIABLES_OUTPUTVARTRUE"
Write-Host "Hidden out from the log: $(SetVariables.outputVarTrue)"
Write-Host "Hidden out from the log: $env:SETVARIABLES_OUTPUTVARFALSE = Yes, it's hidden."
Output:
Hidden out from the log: No, it's not a secret!
Hidden out from the log: No, it's not a secret!
Hidden out from the log: = Yes, it's hidden
A few other ways to secure log files in Azure Pipelines include:
This challenge helps reinforce your understanding of log files in Azure Pipelines and how to secure them from displaying secrets in plain text.
Note
To complete this challenge, you will need access to an Azure subscription and to Azure DevOps. You may need to create an Azure Key Vault and an Azure DevOps project if you do not have these resources available.
For more information about Azure Key Vault and pipeline integration, see:
Please sign in to use this experience.
Sign in