Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Defender for Cloud detects anomalous activities indicating unusual and potentially harmful attempts to access or exploit databases for the following services:
And for RDS instances on AWS (Preview):
For Relational Database Service (RDS) instances on AWS (Preview):
- Aurora PostgreSQL
- Aurora MySQL
- PostgreSQL
- MySQL
- MariaDB
To get alerts from the Microsoft Defender plan, you'll first need to enable Defender for open-source relational databases on your Azure or AWS account.
Learn more about this Microsoft Defender plan in Overview of Microsoft Defender for open-source relational databases.
Prerequisites
You need a Microsoft Azure subscription. If you don't have an Azure subscription, you can sign up for a free subscription.
You must enable Defender for Cloud on your Azure subscription.
AWS users only - Connect your AWS account.
Respond to alerts in Defender for Cloud
When Defender for Cloud is enabled on your database, it detects anomalous activities and generates alerts. These alerts are available from multiple locations, including:
In the Azure portal:
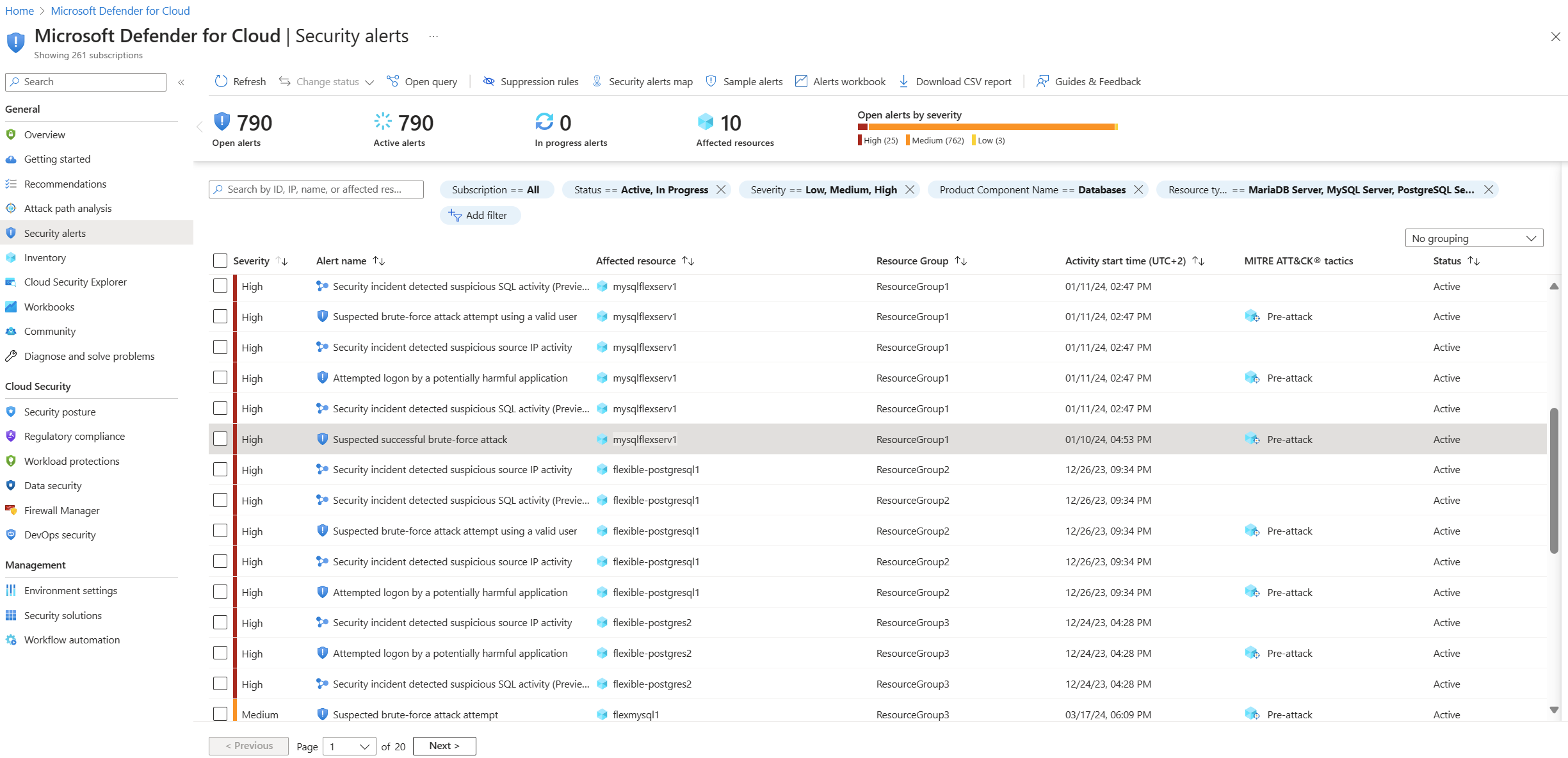
- Defender for Cloud's security alerts page - Shows alerts for all resources protected by Defender for Cloud in the subscriptions you've got permissions to view.
- The resource's Microsoft Defender for Cloud page - Shows alerts and recommendations for one specific resource.
The designated person in your organization receives email alerts in their inbox.
Tip
A live tile on Defender for Cloud's overview dashboard tracks the status of active threats to your resources including databases. Select the security alerts tile to navigate to the Defender for Cloud security alerts page and get an overview of active threats detected on your databases.
For detailed steps and the recommended method to respond to security alerts, see Respond to a security alert.
Respond to email notifications of security alerts
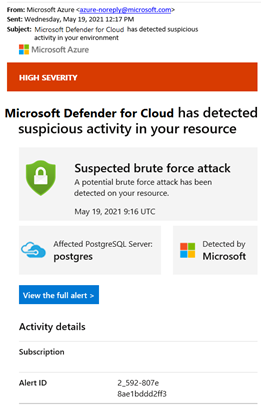
Defender for Cloud sends email notifications when it detects anomalous database activities. The email includes details of the suspicious security event such as the nature of the anomalous activities, database name, server name, application name, and event time. The email also provides information on possible causes and recommended actions to investigate and mitigate any potential threats to the database.
From the email, select the View the full alert link to launch the Azure portal and show the security alerts page, which provides an overview of active threats detected on the database.
View active threats at the subscription level from within the Defender for Cloud portal pages:
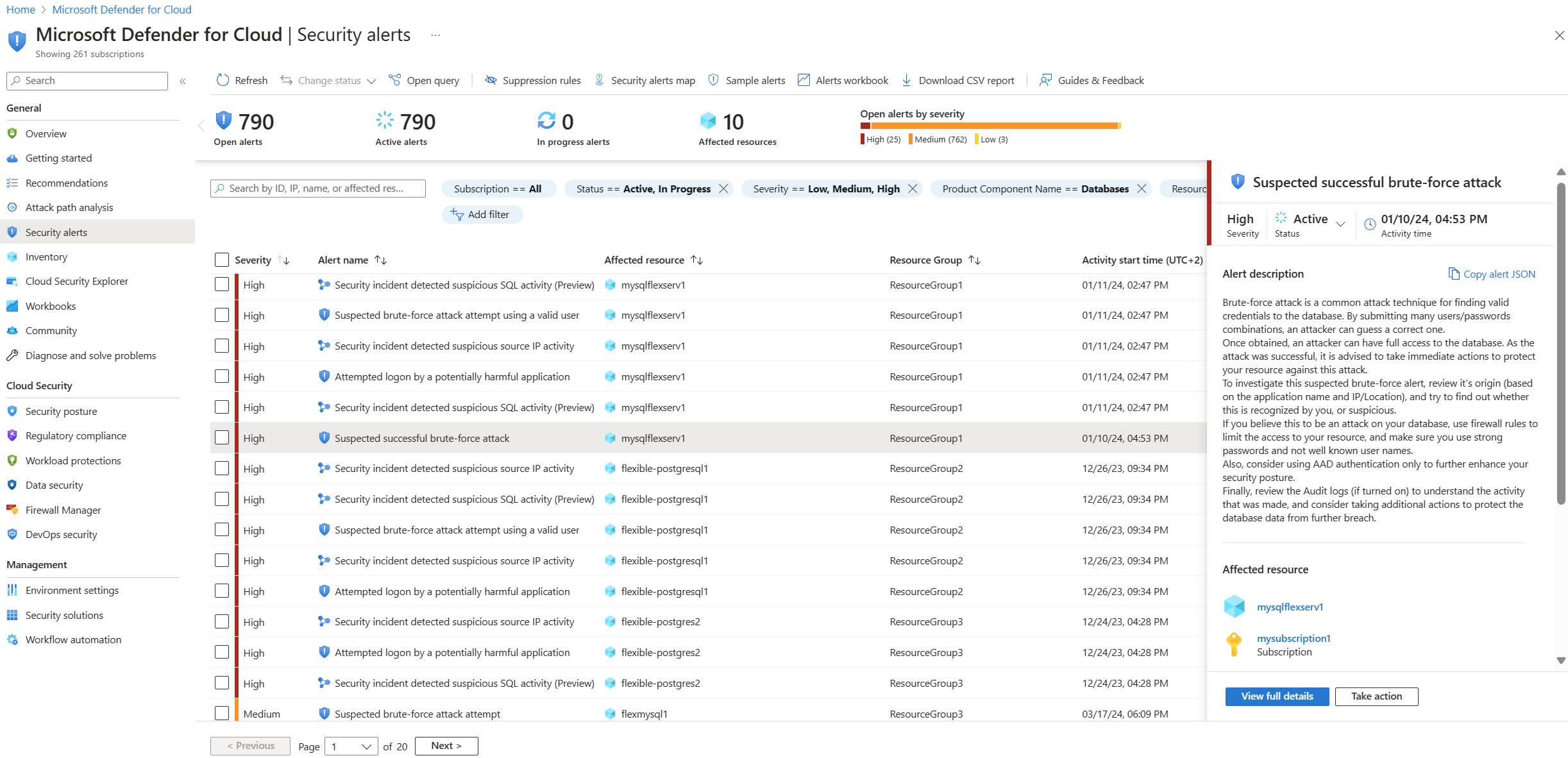
For extra details and recommended actions for investigating the current threat and remediating future threats, select a specific alert.
Tip
For a detailed tutorial on how to handle your alerts, see Manage and respond to alerts.